Code Red Worm Propagation Modeling and Analysis Cliff




- Slides: 17

Code Red Worm Propagation Modeling and Analysis Cliff Changchun Zou, Weibo Gong, Don Towsley Univ. Massachusetts, Amherst

Motivation n Code Red worm incident of July 19 th, 2001: n Showed how fast a worm can spread. n n A friendly worm? n n n more than 350, 000 infected in less than one day. No real damage to compromised computers. Did not send out flooding traffic. A good model can: n n n Predict worm propagation and damage. Understand the worm spreading characteristics. Help to find effective mitigation technique.

Code Red worm background n n Sent HTTP Get request to buffer overflow Win IIS server. It generated 100 threads to scan simultaneously n n n One reason for its fast spreading. Huge scan traffic might have caused congestion. Characteristics: n Uniformly picked IP addresses to send scan packets.

Epidemic modeling introduction infectious susceptible removed n “infectious” hosts: continuously infect others. n “removed” hosts in epidemic area: Ø Ø n Recover and immune to the virus. Dead because of the disease. “removed” hosts in computer area: Ø Ø Patched computers that are clean and immune to the worm. Computers that are shut down or cut off from worm’s circulation.

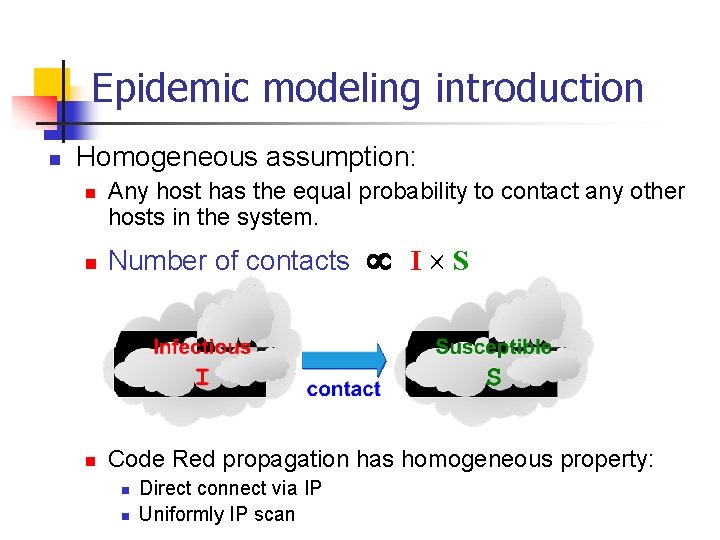
Epidemic modeling introduction n Homogeneous assumption: n Any host has the equal probability to contact any other hosts in the system. I S n Number of contacts n Code Red propagation has homogeneous property: n n Direct connect via IP Uniformly IP scan

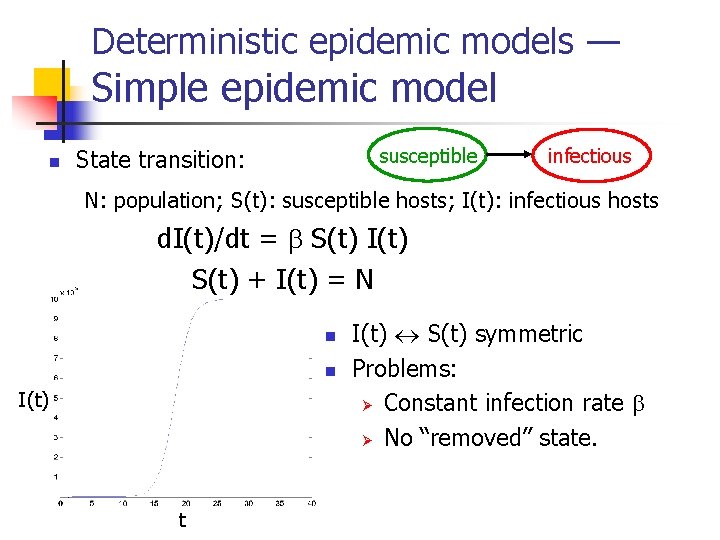
Deterministic epidemic models — Simple epidemic model n susceptible State transition: infectious N: population; S(t): susceptible hosts; I(t): infectious hosts d. I(t)/dt = S(t) I(t) S(t) + I(t) = N n n I(t) t I(t) S(t) symmetric Problems: Ø Constant infection rate Ø No “removed” state.

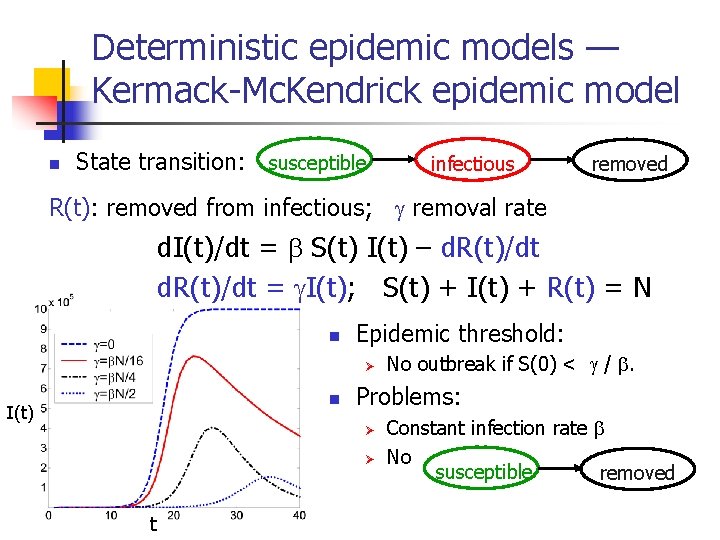
Deterministic epidemic models — Kermack-Mc. Kendrick epidemic model n State transition: susceptible infectious removed R(t): removed from infectious; removal rate d. I(t)/dt = S(t) I(t) – d. R(t)/dt = I(t); S(t) + I(t) + R(t) = N n Epidemic threshold: Ø n I(t) Problems: Ø Ø t No outbreak if S(0) < / . Constant infection rate No susceptible removed

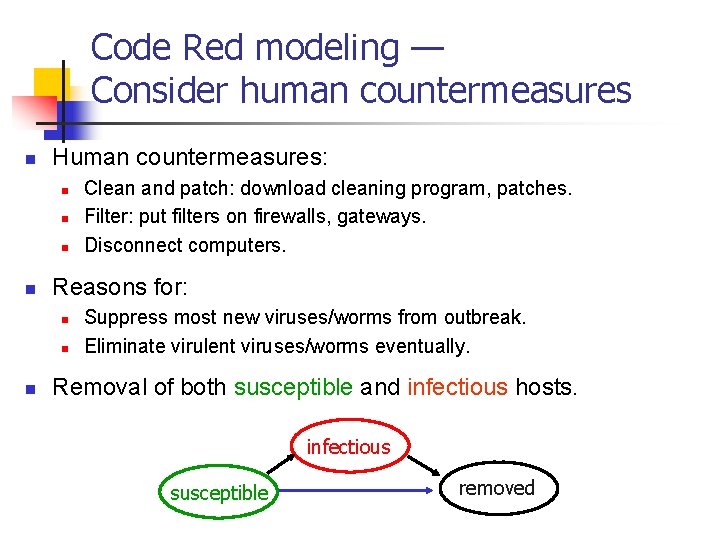
Code Red modeling — Consider human countermeasures n Human countermeasures: n n Reasons for: n n n Clean and patch: download cleaning program, patches. Filter: put filters on firewalls, gateways. Disconnect computers. Suppress most new viruses/worms from outbreak. Eliminate virulent viruses/worms eventually. Removal of both susceptible and infectious hosts. infectious susceptible removed

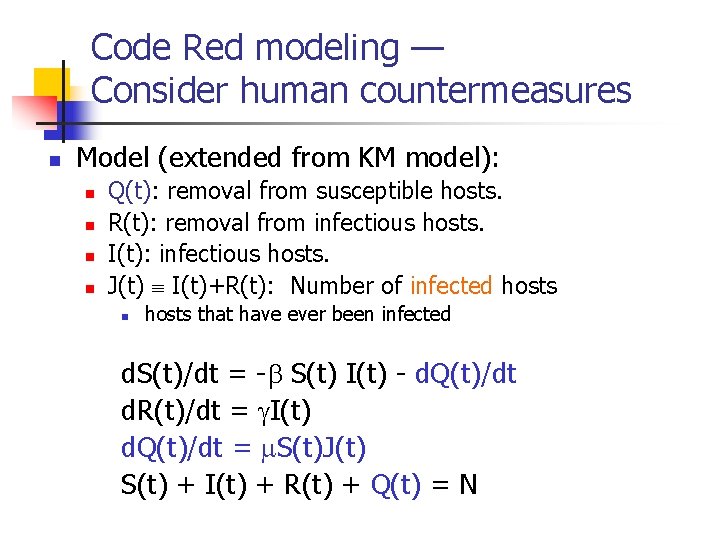
Code Red modeling — Consider human countermeasures n Model (extended from KM model): n n Q(t): removal from susceptible hosts. R(t): removal from infectious hosts. I(t): infectious hosts. J(t) I(t)+R(t): Number of infected hosts n hosts that have ever been infected d. S(t)/dt = - S(t) I(t) - d. Q(t)/dt d. R(t)/dt = I(t) d. Q(t)/dt = S(t)J(t) S(t) + I(t) + R(t) + Q(t) = N

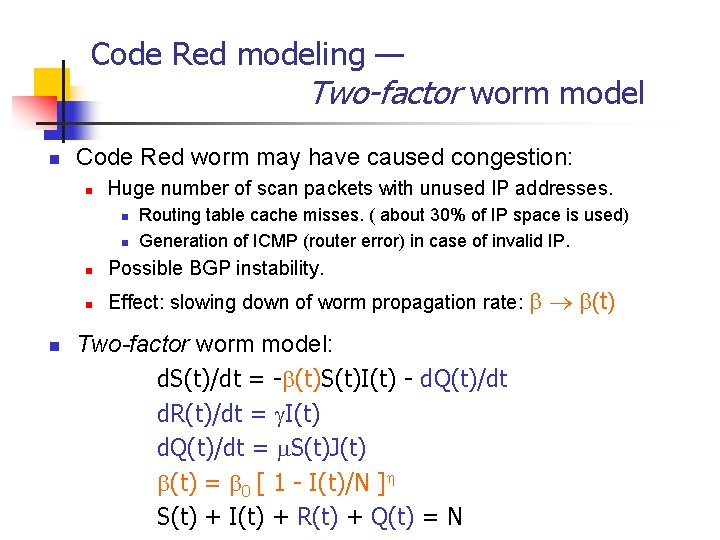
Code Red modeling — Two-factor worm model n Code Red worm may have caused congestion: n Huge number of scan packets with unused IP addresses. n n n Routing table cache misses. ( about 30% of IP space is used) Generation of ICMP (router error) in case of invalid IP. n Possible BGP instability. n Effect: slowing down of worm propagation rate: Two-factor worm model: d. S(t)/dt = - (t)S(t)I(t) - d. Q(t)/dt d. R(t)/dt = I(t) d. Q(t)/dt = S(t)J(t) = 0 [ 1 - I(t)/N ] S(t) + I(t) + R(t) + Q(t) = N (t)

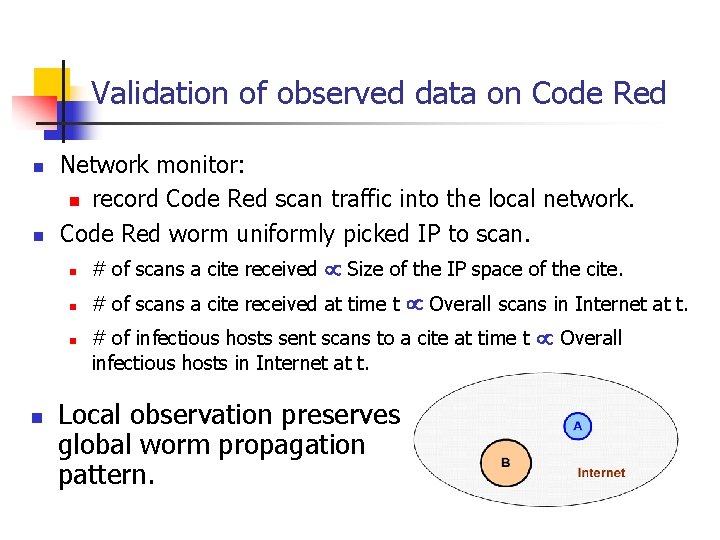
Validation of observed data on Code Red n n Network monitor: n record Code Red scan traffic into the local network. Code Red worm uniformly picked IP to scan. n # of scans a cite received Size of the IP space of the cite. n # of scans a cite received at time t Overall scans in Internet at t. n # of infectious hosts sent scans to a cite at time t Overall infectious hosts in Internet at t. n Local observation preserves global worm propagation pattern.

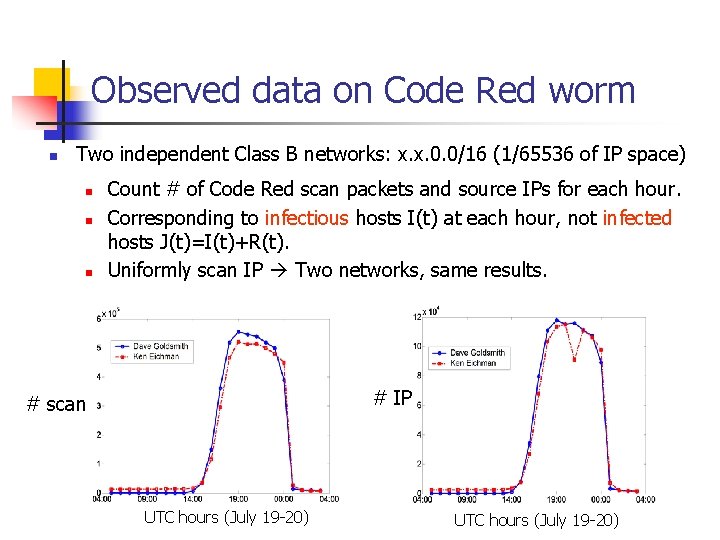
Observed data on Code Red worm n Two independent Class B networks: x. x. 0. 0/16 (1/65536 of IP space) n n n Count # of Code Red scan packets and source IPs for each hour. Corresponding to infectious hosts I(t) at each hour, not infected hosts J(t)=I(t)+R(t). Uniformly scan IP Two networks, same results. # IP # scan UTC hours (July 19 -20)

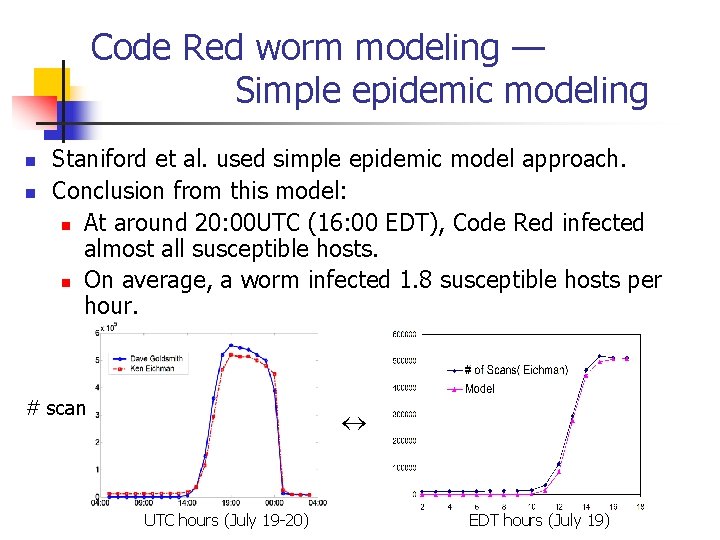
Code Red worm modeling — Simple epidemic modeling n n Staniford et al. used simple epidemic model approach. Conclusion from this model: n At around 20: 00 UTC (16: 00 EDT), Code Red infected almost all susceptible hosts. n On average, a worm infected 1. 8 susceptible hosts per hour. # scan UTC hours (July 19 -20) EDT hours (July 19)

Code Red worm modeling — Simple epidemic modeling n n Possible overestimation? Issues on using simple epidemic for Code Red: n Constant infection rate — No considering of the impact of worm traffic n n No recovery — removal from infectious hosts No patching before infection — removal from susceptible hosts

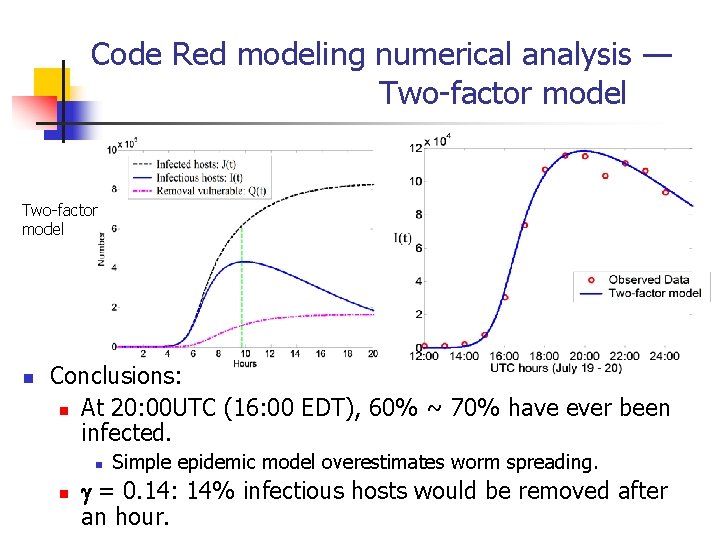
Code Red modeling numerical analysis — Two-factor model n Conclusions: n At 20: 00 UTC (16: 00 EDT), 60% ~ 70% have ever been infected. n n Simple epidemic model overestimates worm spreading. = 0. 14: 14% infectious hosts would be removed after an hour.

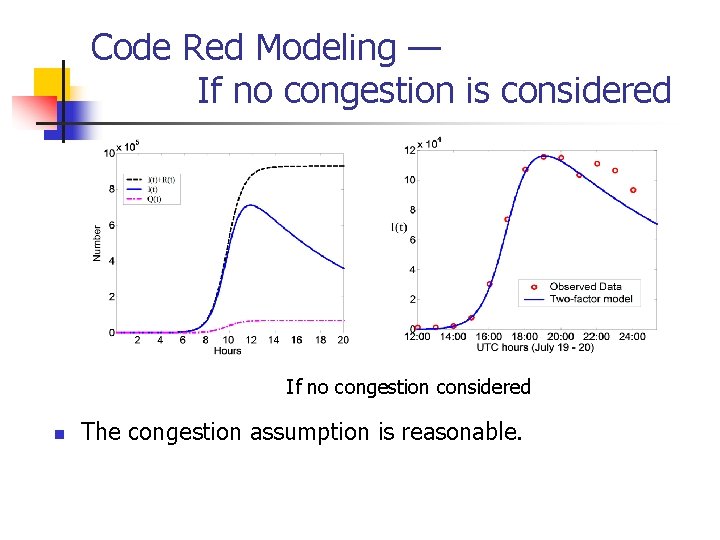
Code Red Modeling — If no congestion is considered If no congestion considered n The congestion assumption is reasonable.

Summary n We must consider the changing environment when we model virus/worm propagation. n n n Worm modeling limitation: n n n Human countermeasures/changing of behaviors. Virus/worm impact on Internet infrastructure. Modeling worm continuously spreading part. Homogeneous systems. Future work: how to predict before worm’s outbreak? n Determine parameters of a virus/worm model.