Email Worm Modeling and Defense Cliff C Zou



- Slides: 14

Email Worm Modeling and Defense Cliff C. Zou, Don Towsley, Weibo Gong Univ. Massachusetts, Amherst 1

Internet Worm Introduction n Scan-based worms: u n Email worms: Example: Code Red, Slammer, u No human interaction u Blaster, Sasser, … u Example: Melissa, Love letter, Sircam, So. Big, My. Doom, … Human activation § Fast (automatic defense) u Need vulnerability § Slower u § Fewer incidents § Network-based blocking u Modeling: no (week) topological issue u Epidemic models Need no vulnerability § More incidents § Defense on email servers u Modeling: email address logical topology u No math model yet Nimda: mixed infection My. Doom: search engine 2

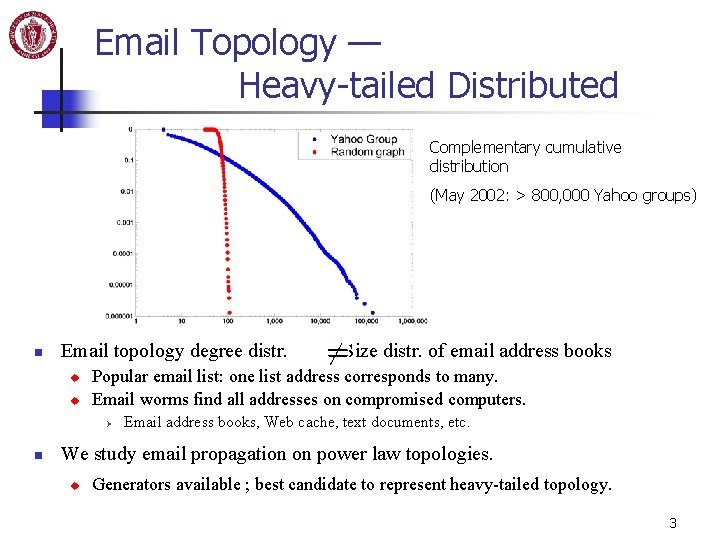
Email Topology — Heavy-tailed Distributed Complementary cumulative distribution (May 2002: > 800, 000 Yahoo groups) n Email topology degree distr. u u Popular email list: one list address corresponds to many. Email worms find all addresses on compromised computers. Ø n Size distr. of email address books Email address books, Web cache, text documents, etc. We study email propagation on power law topologies. u Generators available ; best candidate to represent heavy-tailed topology. 3

Email Worm Simulation Model n Discrete time simulation n Topology: undirected graph u n Power law, small world, random graph Modeling behavior of individual user u u Worm email attachment opening prob. Email checking time interval Ø n Following any distribution: Exponential, Erlang, Constant. Modeling the entire user population u u normal distr. 4

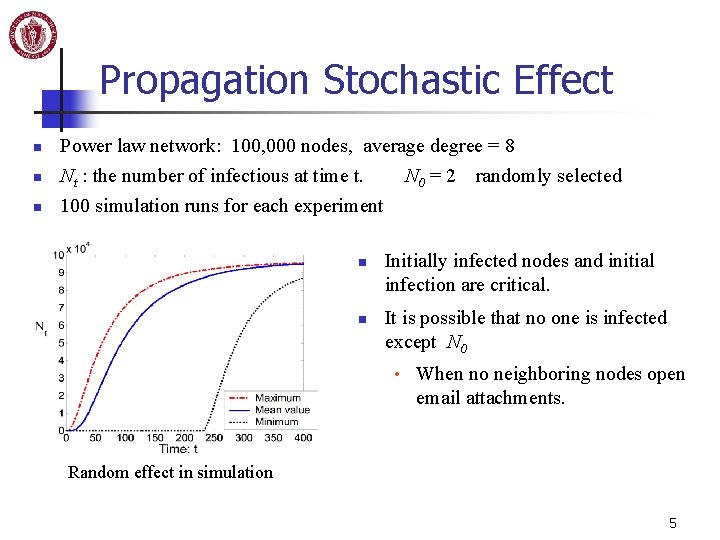
Propagation Stochastic Effect n n n Power law network: 100, 000 nodes, average degree = 8 Nt : the number of infectious at time t. N 0 = 2 randomly selected 100 simulation runs for each experiment n n Initially infected nodes and initial infection are critical. It is possible that no one is infected except N 0 • When no neighboring nodes open email attachments. Random effect in simulation 5

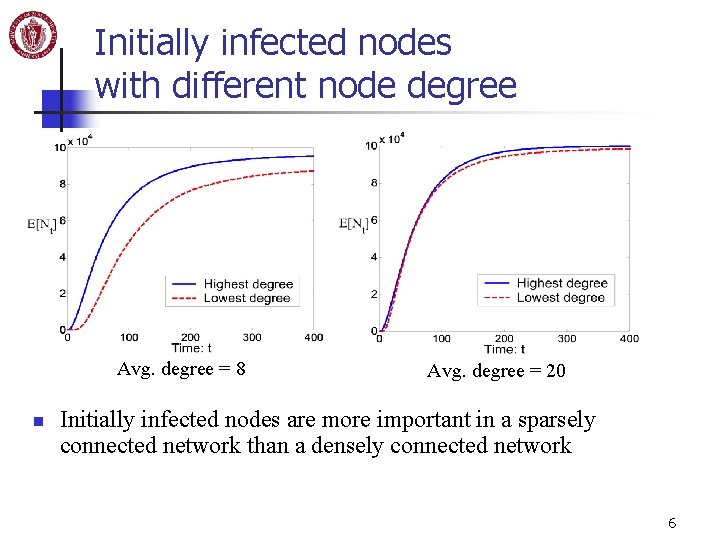
Initially infected nodes with different node degree Avg. degree = 8 n Avg. degree = 20 Initially infected nodes are more important in a sparsely connected network than a densely connected network 6

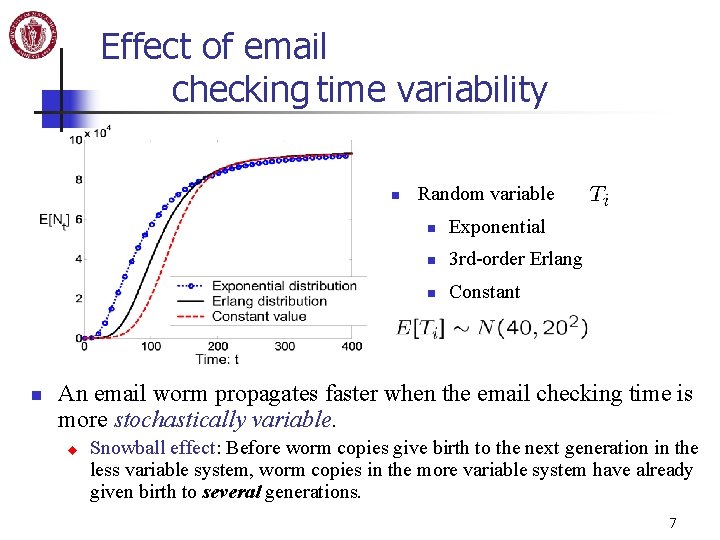
Effect of email checking time variability n n Random variable n Exponential n 3 rd-order Erlang n Constant An email worm propagates faster when the email checking time is more stochastically variable. u Snowball effect: Before worm copies give birth to the next generation in the less variable system, worm copies in the more variable system have already given birth to several generations. 7

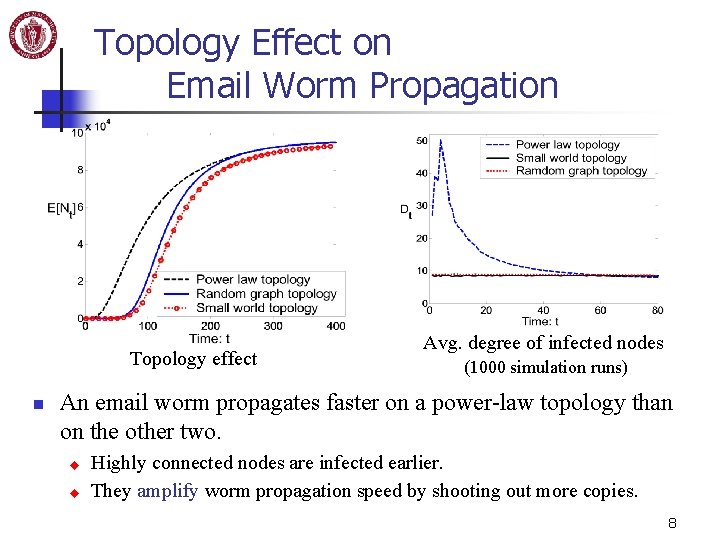
Topology Effect on Email Worm Propagation Topology effect n Avg. degree of infected nodes (1000 simulation runs) An email worm propagates faster on a power-law topology than on the other two. u u Highly connected nodes are infected earlier. They amplify worm propagation speed by shooting out more copies. 8

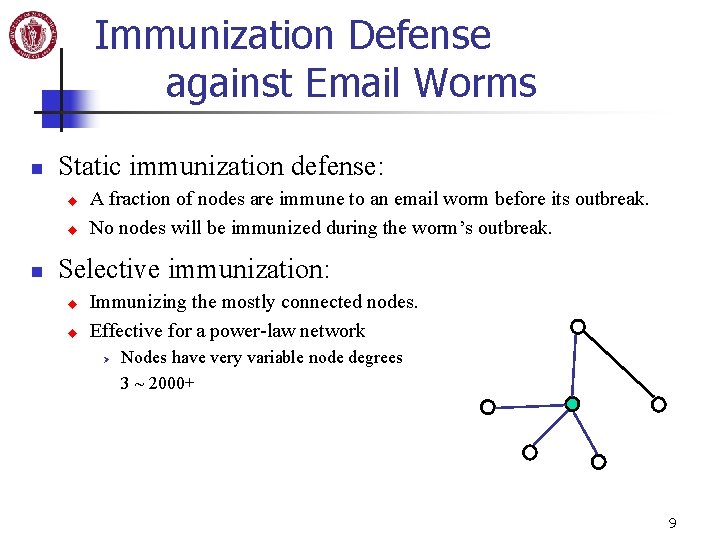
Immunization Defense against Email Worms n Static immunization defense: u u n A fraction of nodes are immune to an email worm before its outbreak. No nodes will be immunized during the worm’s outbreak. Selective immunization: u u Immunizing the mostly connected nodes. Effective for a power-law network Ø Nodes have very variable node degrees 3 ~ 2000+ 9

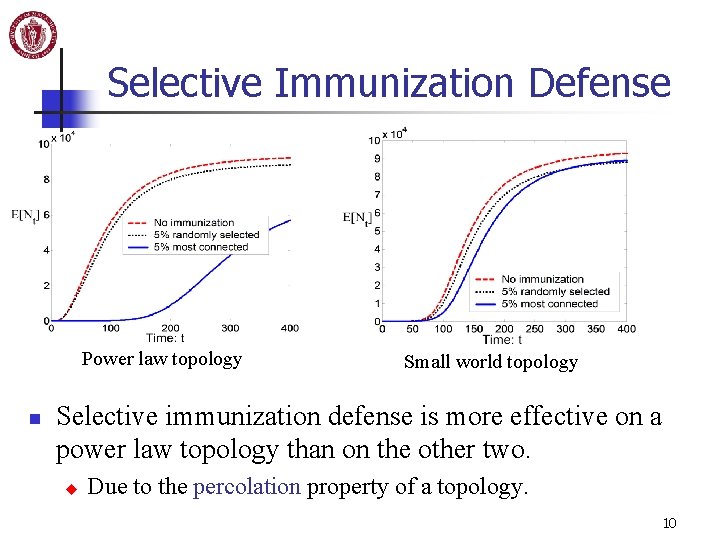
Selective Immunization Defense Power law topology n Small world topology Selective immunization defense is more effective on a power law topology than on the other two. u Due to the percolation property of a topology. 10

Percolation and Phase Transition n Selective percolation with p: u u Removing top p percent of mostly connected nodes. Corresponding to selective immunization. Ø n Newman et al. studied uniform percolation. Selective percolation property: u Connection ratio: Ø u Remaining link ratio: Ø u fraction of remained nodes that are connected. fraction of remained links. Phase transition selective percolation threshold Ø Disjoint the remaining network when 11

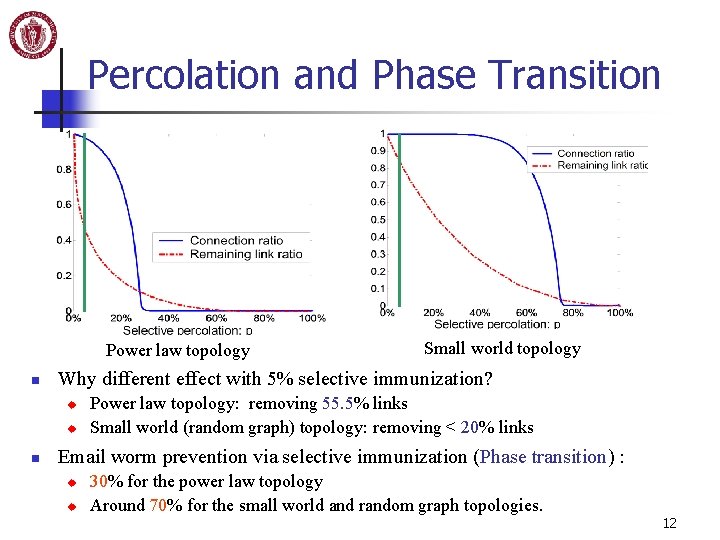
Percolation and Phase Transition Power law topology n Why different effect with 5% selective immunization? u u n Small world topology Power law topology: removing 55. 5% links Small world (random graph) topology: removing < 20% links Email worm prevention via selective immunization (Phase transition) : u u 30% for the power law topology Around 70% for the small world and random graph topologies. 12

Summary n n Email topology is a heavy-tailed distributed topology. The impact of a power law topology on email worm propagation is mixed: u u Cons: an email worm spreads faster than on a small world or a random graph topology. Pros: static selective immunization defense is more effective. 13

Future Work n Mathematical modeling u n Difficulty: considering an arbitrary topology Directed graph for email topology u u One-way email address relationship Heavy tailed distr. definition? Topology generator? n Dynamic immunization defense n Short-term focus: Enterprise network defense 14