Code Red Worm Propagation Modeling and Analysis Zou




![Two-Factor Model Math • d. I(t)/dt = β(t)[N - R(t) - I(t) - Q(t)]I(t) Two-Factor Model Math • d. I(t)/dt = β(t)[N - R(t) - I(t) - Q(t)]I(t)](https://slidetodoc.com/presentation_image_h2/9304c433d9f3ad87e0967de6020ea22e/image-13.jpg)

- Slides: 17

Code Red Worm Propagation Modeling and Analysis Zou, Gong, & Towsley Michael E. Locasto March 21, 2003

Overview • Code Red incident data & impact • epidemiology models – traditional (biological) infection models – two-factor worm model • related work & questions – (Weaver & Sapphire)

Motivation • Internet great medium for spreading malicious code – Code Red & Co. renew interest in worm studies • Issues: – How to explain worm propagation curves? – What factors affect spreading behavior? – Can we generate a more accurate model?

Background: Code Red • Three versions: – CRv 1. 1 (bad rng) July 13, 2001 – CRv 1. 2 July 19, 2001 – CRv 2 August, 2001 • 100 threads, 300 k victims • “maliciously crafted URL” (default. ida vulnerability)

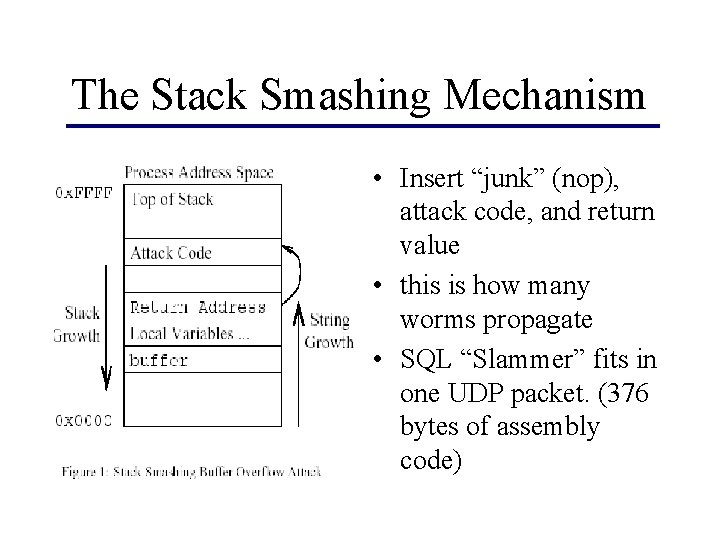
Background: The Stack Smash • Buffer overflows in C functions – gets(), etc – home-grown functions • code injection & modify return pointer – both parts are critical: overflow alone does not allow you to execute code

The Stack Smashing Mechanism • Insert “junk” (nop), attack code, and return value • this is how many worms propagate • SQL “Slammer” fits in one UDP packet. (376 bytes of assembly code)

Epidemic Models • Deterministic vs. Stochastic – Simple epidemic model (previous paper) – general epidemic model (Kermack-Mckendrick add notion of removed hosts) • good baseline, need to be adjusted to explain Internet worm data • any model must be deterministic (b/c of scale)

Two-Factor Worm Model • Two major factors affect worm spread: – dynamic human countermeasures • • anti-virus software cleaning patching firewall updates disconnect/shutdown – interference due to aggressive scanning • Rate of infection (ß) is not constant

Two-Factor Worm Model (con) • Two important restrictions: – consider only “continuously activated” worms – consider worms that propagate w/ort topology

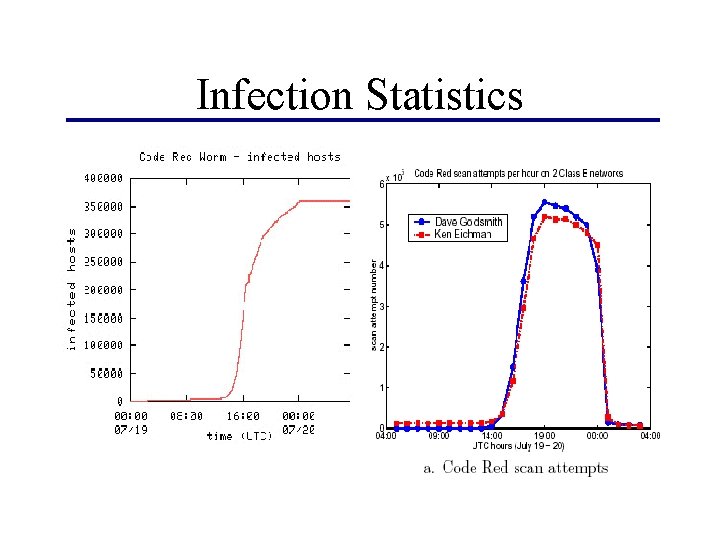
Infection Statistics

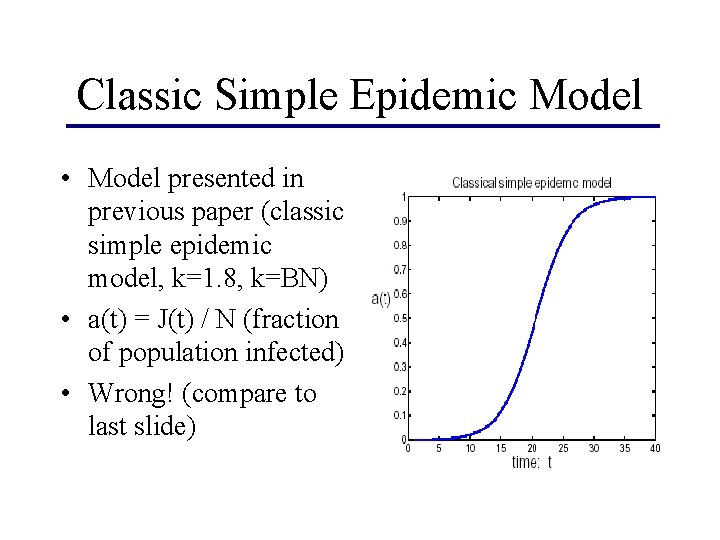
Classic Simple Epidemic Model • Model presented in previous paper (classic simple epidemic model, k=1. 8, k=BN) • a(t) = J(t) / N (fraction of population infected) • Wrong! (compare to last slide)

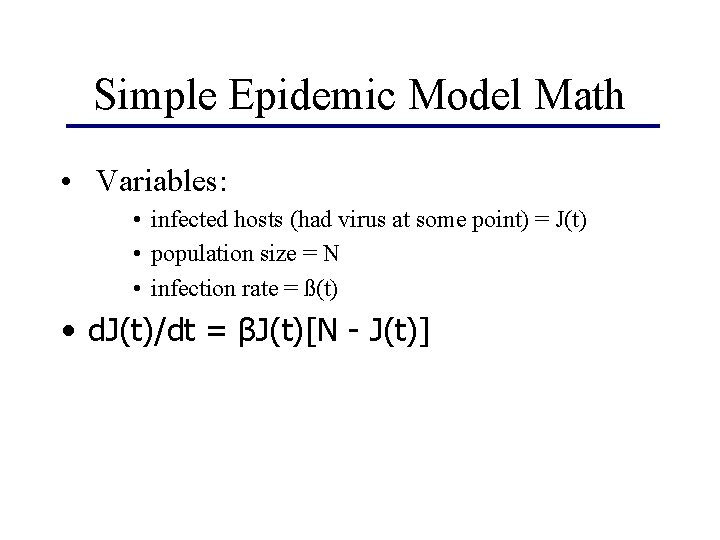
Simple Epidemic Model Math • Variables: • infected hosts (had virus at some point) = J(t) • population size = N • infection rate = ß(t) • d. J(t)/dt = βJ(t)[N - J(t)]
![TwoFactor Model Math d Itdt βtN Rt It QtIt Two-Factor Model Math • d. I(t)/dt = β(t)[N - R(t) - I(t) - Q(t)]I(t)](https://slidetodoc.com/presentation_image_h2/9304c433d9f3ad87e0967de6020ea22e/image-13.jpg)
Two-Factor Model Math • d. I(t)/dt = β(t)[N - R(t) - I(t) - Q(t)]I(t) d. R(t)/dt – – – – S(t) = susceptible hosts I(t) = infectious hosts R(t) = removed hosts from I population Q(t) = removed hosts from S population J(t) = I(t) + R(t) C(t) = R(t) + Q(t) J(t) = I(t) + R(t) N = population (I+R+Q+S)

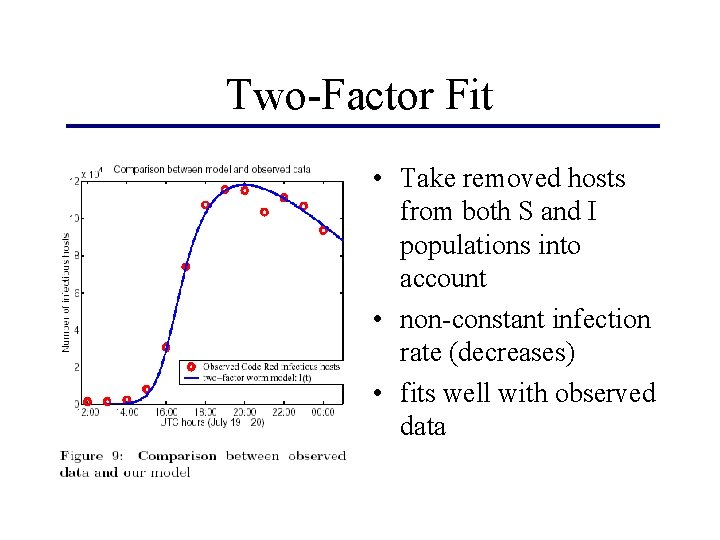
Two-Factor Fit • Take removed hosts from both S and I populations into account • non-constant infection rate (decreases) • fits well with observed data

Results • Two-factor worm model – accurate model without topology constraints – explains exponential start & end drop off – identifies 2 critical factors in worm propagation • Only 60% of CR targets infected

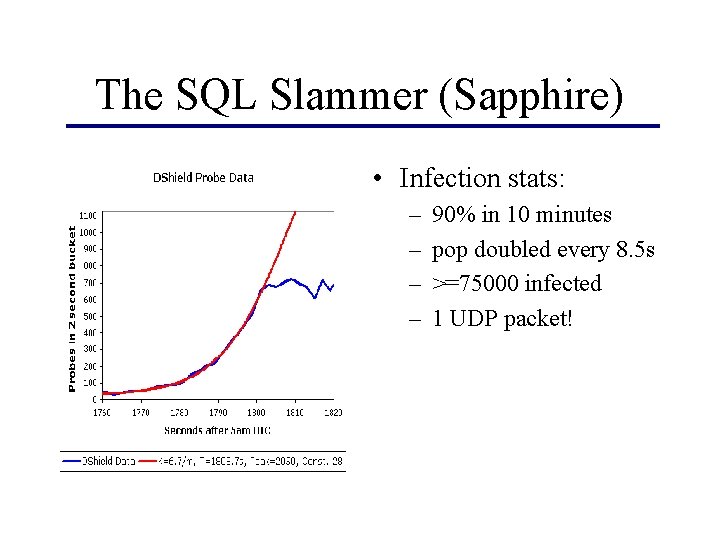
The SQL Slammer (Sapphire) • Infection stats: – – 90% in 10 minutes pop doubled every 8. 5 s >=75000 infected 1 UDP packet!

Questions • Sapphire paper: – http: //www. caida. org/outreach/papers/2003/sapphire. html • “Previous” Code Red paper: – http: //www. icir. org/vern/papers/cdc-usenix-sec 02/