chown Io T Secure Handling of Smart Home

- Slides: 16

chown. Io. T Secure Handling of Smart Home Io. T Devices Ownership Change Samuel Marchal, Md Sakib Nizam Khan, N. Asokan Aalto University samuel. marchal@aalto. fi

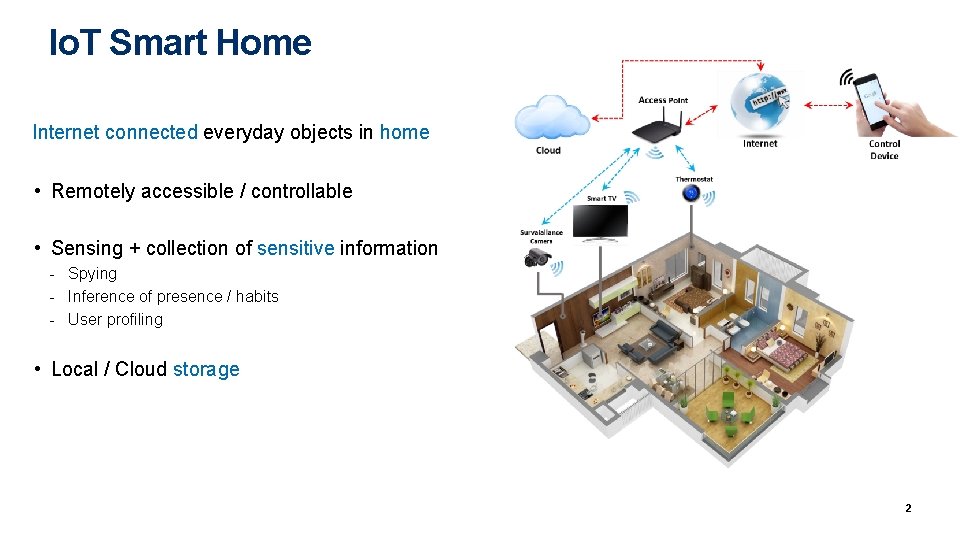
Io. T Smart Home Internet connected everyday objects in home • Remotely accessible / controllable • Sensing + collection of sensitive information - Spying - Inference of presence / habits - User profiling • Local / Cloud storage 2

Ownership change • Ownership of Smart Home (SH) device can change during lifetime - Lend - Resell / stealing - Change of tenant (rental places) • May introduce unauthorized access to privacy sensitive data - Historical / personal data not wiped (threat to previous owner) Authentication credentials for cloud / network access saved (threat to previous owner) Old authentication credentials still valid (threat to new owner) Etc. 3

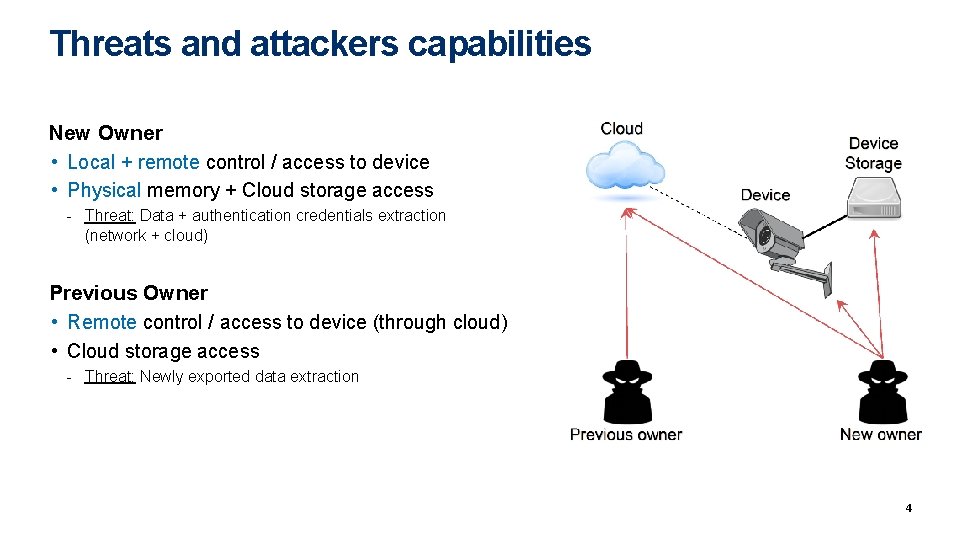
Threats and attackers capabilities New Owner • Local + remote control / access to device • Physical memory + Cloud storage access - Threat: Data + authentication credentials extraction (network + cloud) Previous Owner • Remote control / access to device (through cloud) • Cloud storage access - Threat: Newly exported data extraction 4

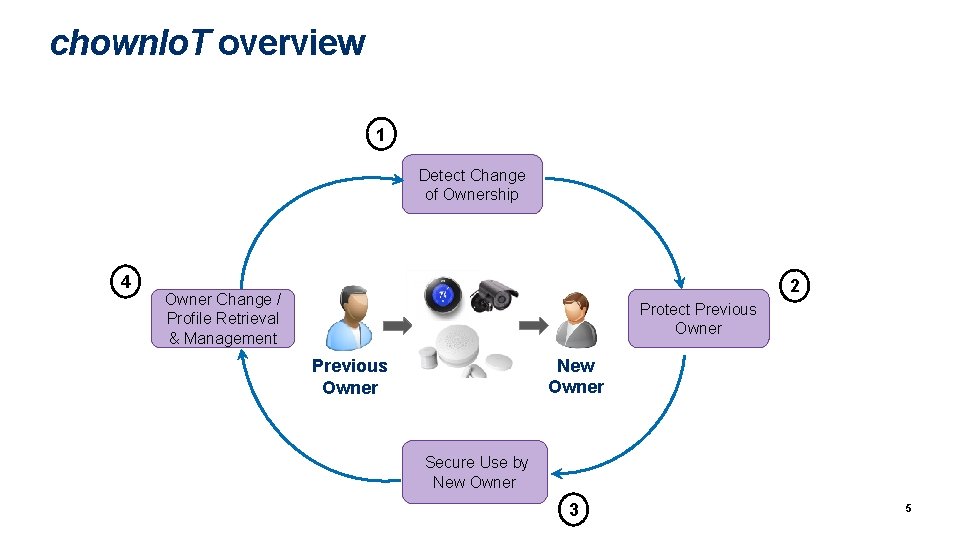
chown. Io. T overview 1 Detect Change of Ownership 4 2 Owner Change / Profile Retrieval & Management Protect Previous Owner New Owner Previous Owner Secure Use by New Owner 3 5

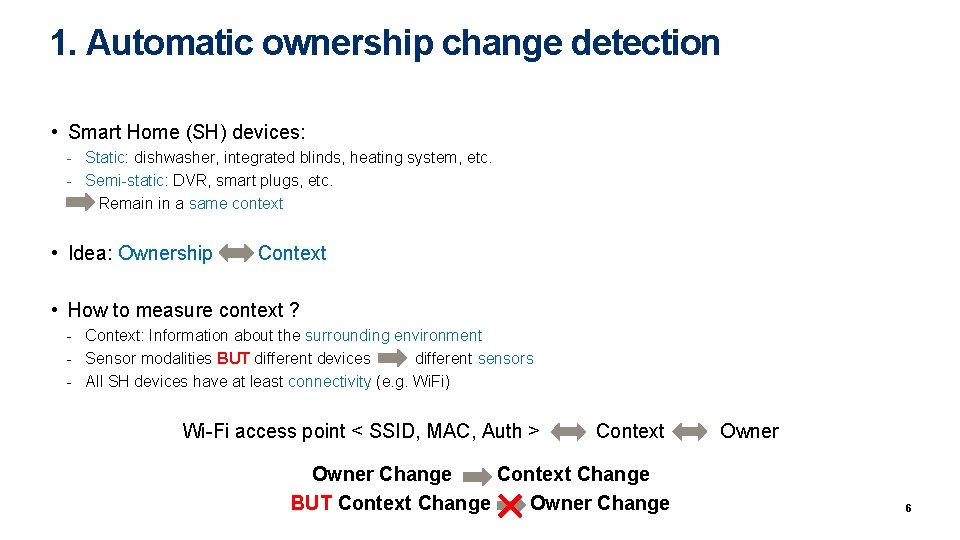
1. Automatic ownership change detection • Smart Home (SH) devices: - Static: dishwasher, integrated blinds, heating system, etc. - Semi-static: DVR, smart plugs, etc. - Remain in a same context • Idea: Ownership Context • How to measure context ? - Context: Information about the surrounding environment - Sensor modalities BUT different devices different sensors - All SH devices have at least connectivity (e. g. Wi. Fi) Wi-Fi access point < SSID, MAC, Auth > Context Owner Change Context Change BUT Context Change Owner Change 6

1. 1 Verification of ownership change • SH devices setup and controlled using a control device (e. g. smartphone) - Assumption: in vicinity if same owner change the context of SH device • Verification: - Challenge-response between control device and SH device (Bluetooth) Add new context to owner profile • SH device setup overhead - Security association with control device (e. g. DH key exchange) trusted device 7

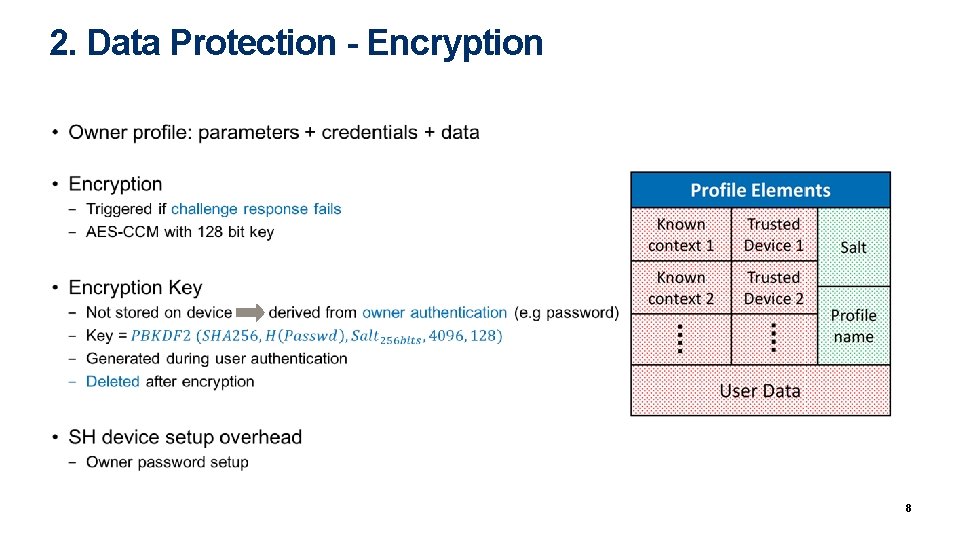
2. Data Protection - Encryption • 8

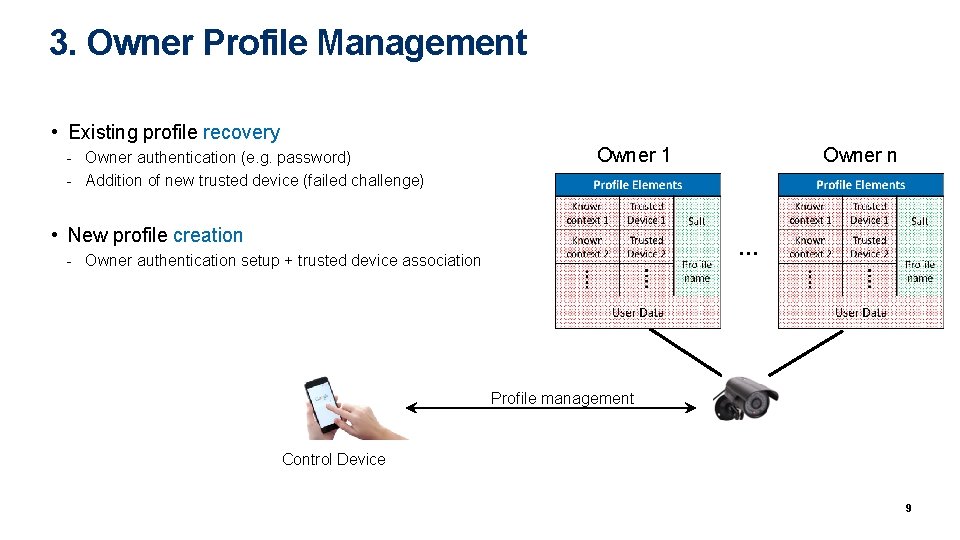
3. Owner Profile Management • Existing profile recovery - Owner authentication (e. g. password) - Addition of new trusted device (failed challenge) Owner 1 • New profile creation Owner n … - Owner authentication setup + trusted device association Profile management Control Device 9

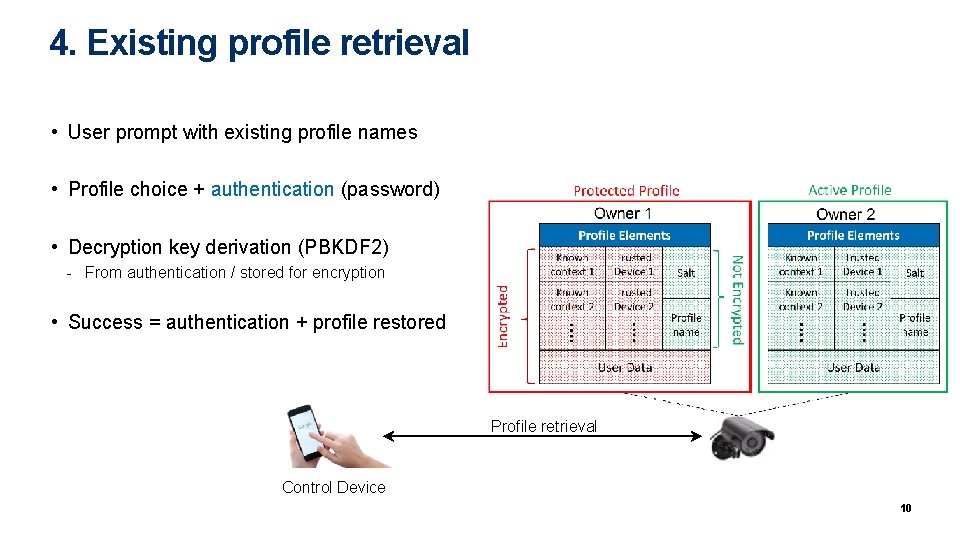
4. Existing profile retrieval • User prompt with existing profile names • Profile choice + authentication (password) • Decryption key derivation (PBKDF 2) - From authentication / stored for encryption • Success = authentication + profile restored Profile retrieval Control Device 10

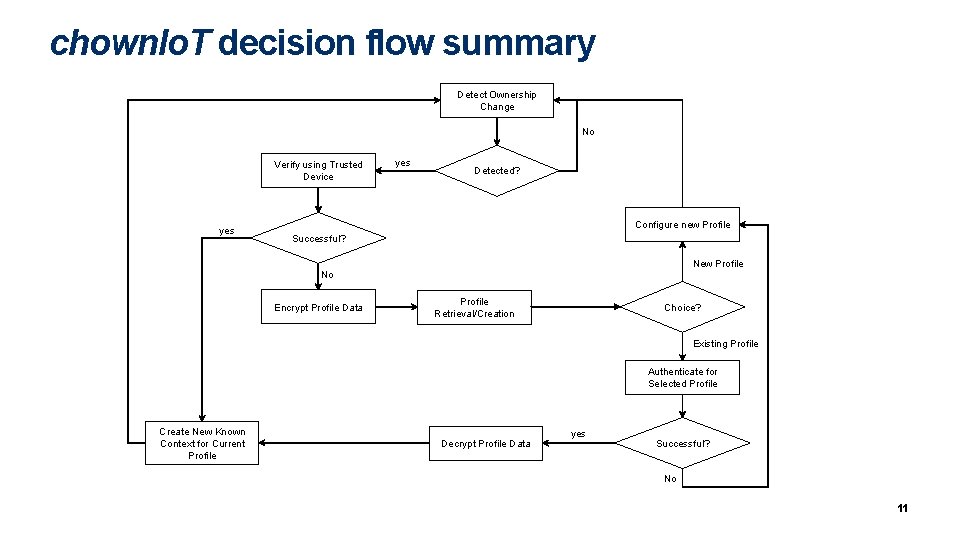
chown. Io. T decision flow summary Detect Ownership Change No Verify using Trusted Device yes Detected? Configure new Profile Successful? New Profile No Encrypt Profile Data Profile Retrieval/Creation Choice? Existing Profile Authenticate for Selected Profile Create New Known Context for Current Profile Decrypt Profile Data yes Successful? No 11

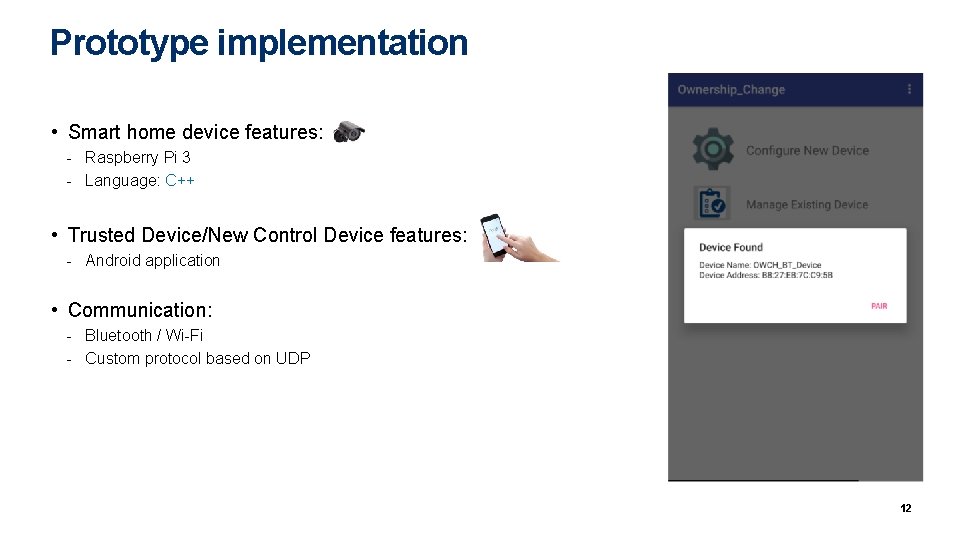
Prototype implementation • Smart home device features: - Raspberry Pi 3 - Language: C++ • Trusted Device/New Control Device features: - Android application • Communication: - Bluetooth / Wi-Fi - Custom protocol based on UDP 12

Summary • Privacy enhancement protocol for ownership change of SH devices - Automatic: ownership change detection based on Wi. Fi AP - Secure: owner authentication / device association / data encryption - Usable: profile management + limited annoyance • Prototype implementation - Android management application - C++ code for smart home device - UDP based communication protocol 13

Future Work • Improvements: - Abnormal power off • Ownership change not detected • Data remains unencrypted • Potential solution: Always encrypt but costly / unrealistic - Password based key derivation • Brute force attack • More robust key generation • Ownership change detection - Reduce false positives - Other sensor modalities • Profile management - Cloud-based management (no storage on device) 14

chown. Io. T Secure Handling of Smart Home Io. T Devices Ownership Change Samuel Marchal, Md Sakib Nizam Khan, N. Asokan Aalto University samuel. marchal@aalto. fi

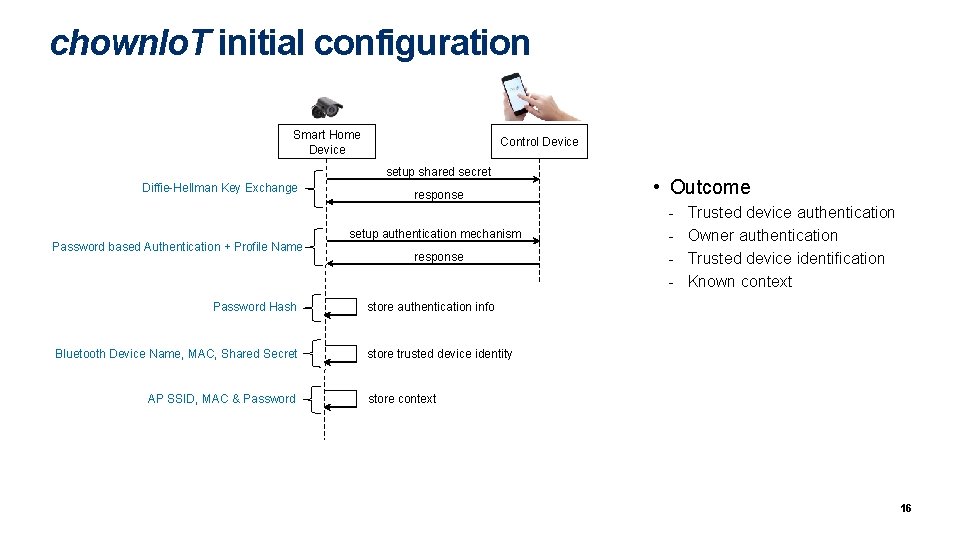
chown. Io. T initial configuration Smart Home Device Control Device setup shared secret Diffie-Hellman Key Exchange Password based Authentication + Profile Name Password Hash Bluetooth Device Name, MAC, Shared Secret AP SSID, MAC & Password response setup authentication mechanism response • Outcome - Trusted device authentication Owner authentication Trusted device identification Known context store authentication info store trusted device identity store context 16
 Hadoop chown
Hadoop chown One smart man he felt smart
One smart man he felt smart Street knowledge vs book knowledge
Street knowledge vs book knowledge It's not how smart you are it's how you are smart
It's not how smart you are it's how you are smart One smart man he felt smart
One smart man he felt smart Street smart vs book smart quotes
Street smart vs book smart quotes It's not how smart you are it's how you are smart
It's not how smart you are it's how you are smart Street smart vs book smart quotes
Street smart vs book smart quotes Future smart answers module 2
Future smart answers module 2 Easyfiks smart home
Easyfiks smart home Conclusion of home automation system
Conclusion of home automation system Philio smart home
Philio smart home Conclusion of smart grid
Conclusion of smart grid Smart home device
Smart home device What did you say
What did you say Plurals of flower
Plurals of flower John heartfield
John heartfield































