Chapter 4 Wireless LANs Scaling Networks PresentationID 2008

















- Slides: 33

Chapter 4: Wireless LANs Scaling Networks Presentation_ID © 2008 Cisco Systems, Inc. All rights reserved. Cisco Confidential 1

Chapter 4 4. 0 Introduction 4. 1 Wireless LAN Concepts 4. 2 Wireless LAN Operations 4. 3 Wireless LAN Security 4. 4 Wireless LAN Configuration 4. 5 Summary Presentation_ID © 2008 Cisco Systems, Inc. All rights reserved. Cisco Confidential 2

4. 1 Wireless Concepts Presentation_ID © 2008 Cisco Systems, Inc. All rights reserved. Cisco Confidential 3

WLAN Components Supporting Mobility § Productivity is no longer restricted to a fixed work location or a defined time period. § People now expect to be connected at any time and place, from the office to the airport or the home. § Users now expect to be able to roam wirelessly. § Roaming enables a wireless device to maintain Internet access without losing a connection. Presentation_ID © 2008 Cisco Systems, Inc. All rights reserved. Cisco Confidential 4

WLAN Components Benefits of Wireless § Increased flexibility § Increased productivity § Reduced costs § Ability to grow and adapt to changing requirements Presentation_ID © 2008 Cisco Systems, Inc. All rights reserved. Cisco Confidential 5

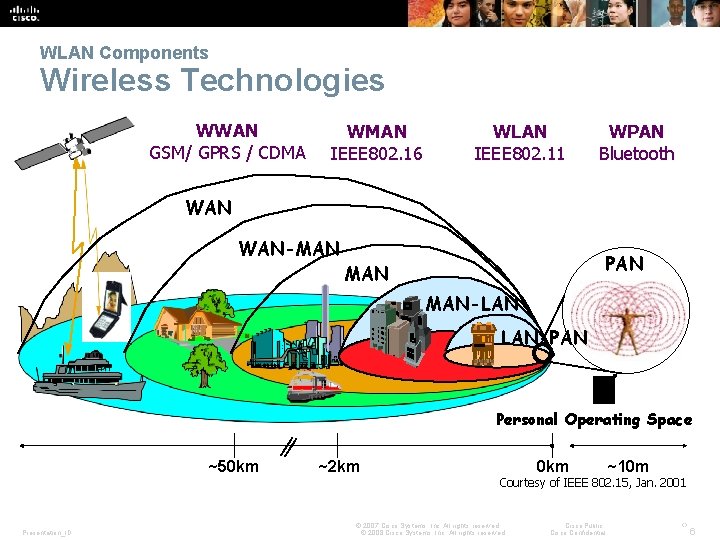
WLAN Components Wireless Technologies WWAN GSM/ GPRS / CDMA WMAN IEEE 802. 16 WLAN IEEE 802. 11 WPAN Bluetooth WAN-MAN PAN MAN-LAN LAN-PAN Pico-Cell Personal Operating Space ~50 km Presentation_ID ~2 km 0 km ~10 m Courtesy of IEEE 802. 15, Jan. 2001 © 2007 Cisco Systems, Inc. All rights reserved. © 2008 Cisco Systems, Inc. All rights reserved. Cisco Public Cisco Confidential ‹› 6

WLAN Components Wireless Technologies (cont. ) § Worldwide Interoperability for Microwave Access (Wi. MAX) – An IEEE 802. 16 WWAN standard that provides wireless broadband access of up to 30 mi (50 km). § Cellular broadband – Consists of various corporate, national, and international organizations using service provider cellular access to provide mobile broadband network connectivity. § Satellite Broadband – Provides network access to remote sites through the use of a directional satellite dish. Presentation_ID © 2008 Cisco Systems, Inc. All rights reserved. Cisco Confidential 7

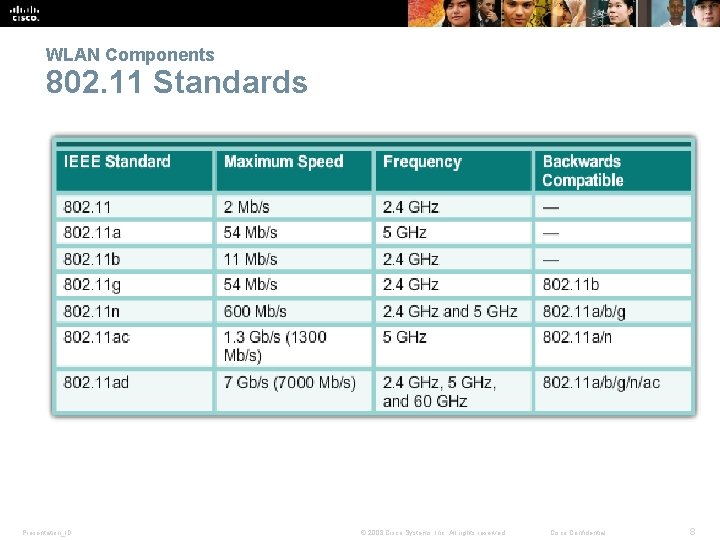
WLAN Components 802. 11 Standards Presentation_ID © 2008 Cisco Systems, Inc. All rights reserved. Cisco Confidential 8

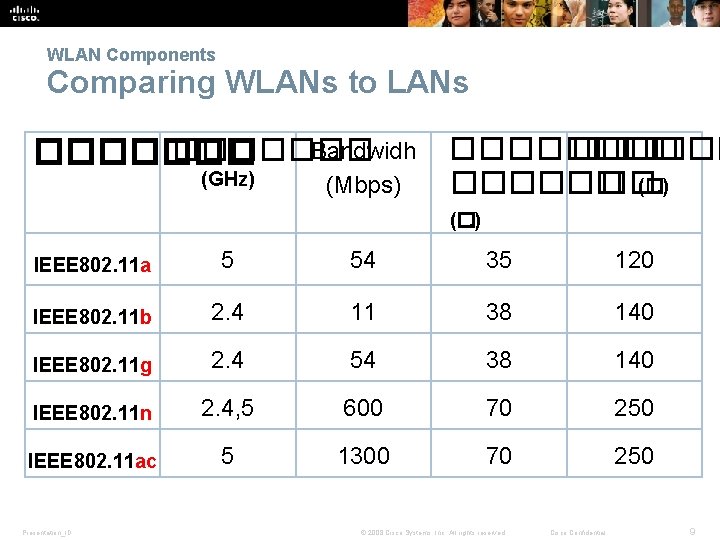
WLAN Components Comparing WLANs to LANs Bandwidh ������� (GHz) (Mbps) ������ �� (�. ) IEEE 802. 11 a 5 54 35 120 IEEE 802. 11 b 2. 4 11 38 140 IEEE 802. 11 g 2. 4 54 38 140 IEEE 802. 11 n 2. 4, 5 600 70 250 IEEE 802. 11 ac 5 1300 70 250 Presentation_ID © 2008 Cisco Systems, Inc. All rights reserved. Cisco Confidential 9

Components of WLANs Wireless NICs Wireless deployment requires: § End devices with wireless NICs § Infrastructure device, such as a wireless router or wireless AP Presentation_ID © 2008 Cisco Systems, Inc. All rights reserved. Cisco Confidential 10

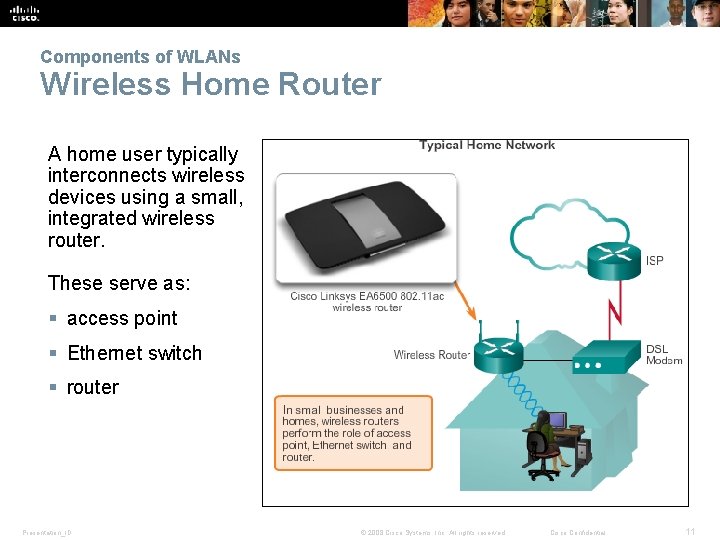
Components of WLANs Wireless Home Router A home user typically interconnects wireless devices using a small, integrated wireless router. These serve as: § access point § Ethernet switch § router Presentation_ID © 2008 Cisco Systems, Inc. All rights reserved. Cisco Confidential 11

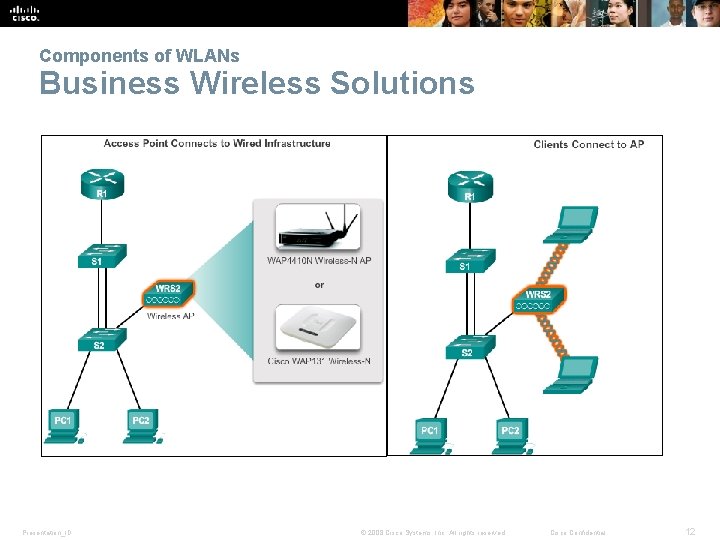
Components of WLANs Business Wireless Solutions Presentation_ID © 2008 Cisco Systems, Inc. All rights reserved. Cisco Confidential 12

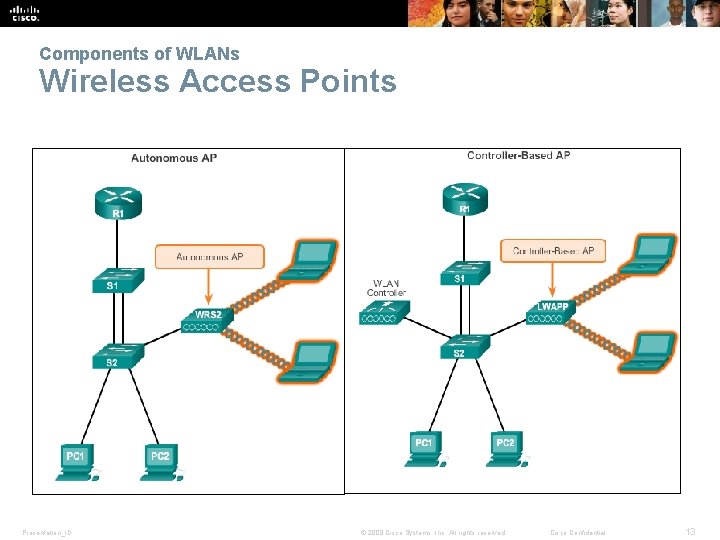
Components of WLANs Wireless Access Points Presentation_ID © 2008 Cisco Systems, Inc. All rights reserved. Cisco Confidential 13

Components of WLANs Large Wireless Deployment Solutions § For larger organizations with many APs, Cisco provides controller-based managed solutions, including the Cisco Meraki Cloud Managed Architecture and the Cisco Unified Wireless Network Architecture. § Cisco Meraki cloud architecture is a management solution used to simplify the wireless deployment. Using this architecture, APs are centrally managed from a controller in the cloud. Presentation_ID © 2008 Cisco Systems, Inc. All rights reserved. Cisco Confidential 14

Components of WLANs Large Wireless Deployment Solutions (cont. ) Presentation_ID © 2008 Cisco Systems, Inc. All rights reserved. Cisco Confidential 15

Components of WLANs Wireless Antennas Cisco Aironet APs can use: § Omni Directional Wi-Fi Antennas (��������� ) § Directional Wi-Fi Antennas • Sector Antenna • Yagi Antenna • Solid Dish Anterna Presentation_ID © 2008 Cisco Systems, Inc. All rights reserved. Cisco Confidential 16

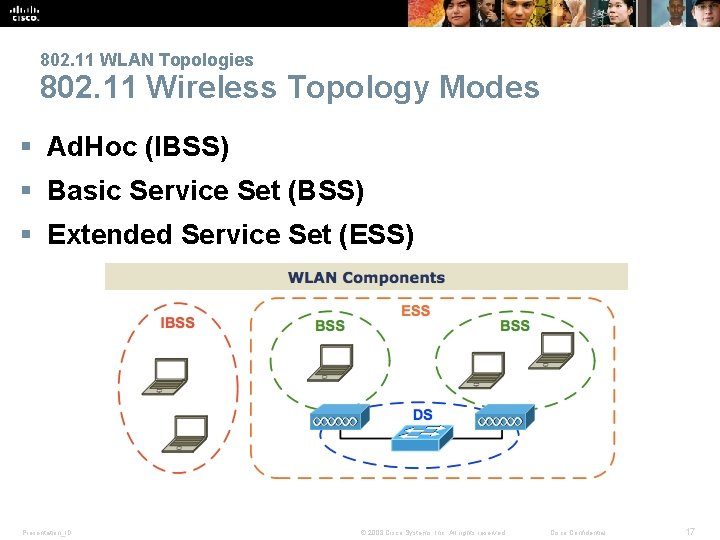
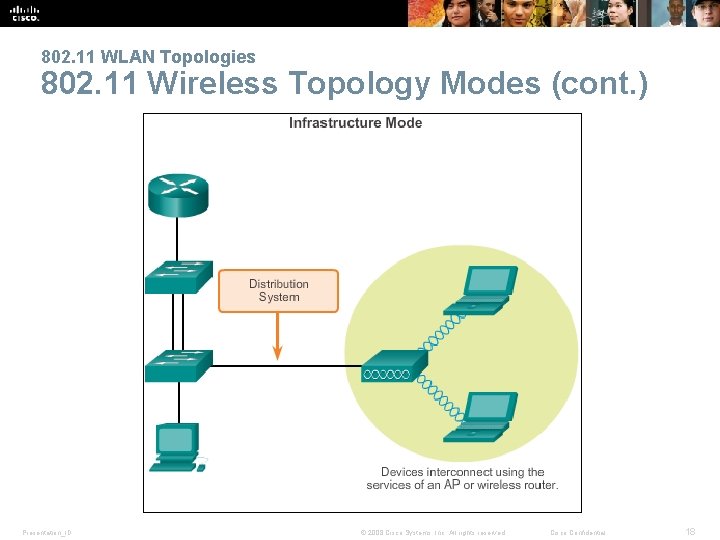
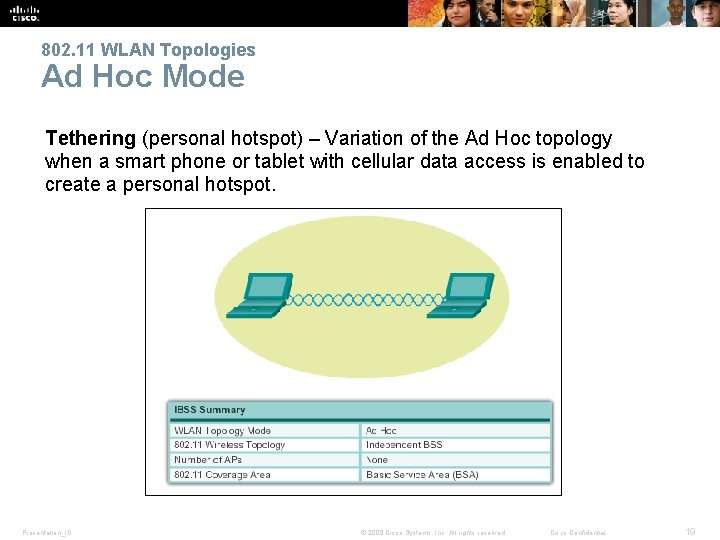
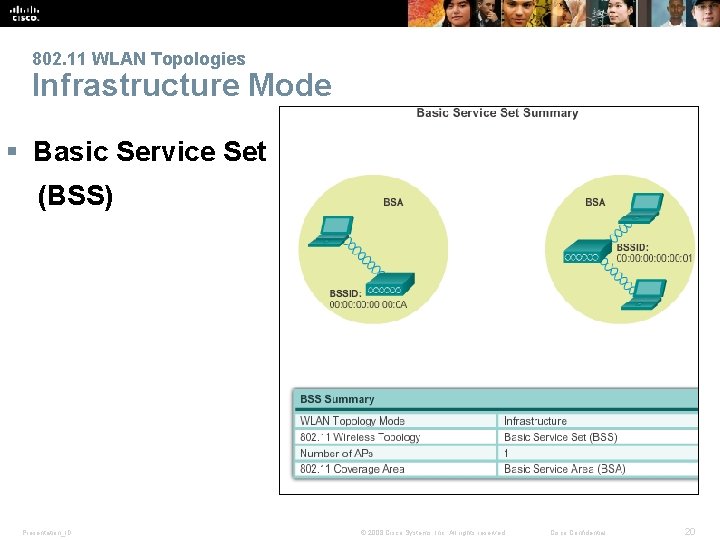
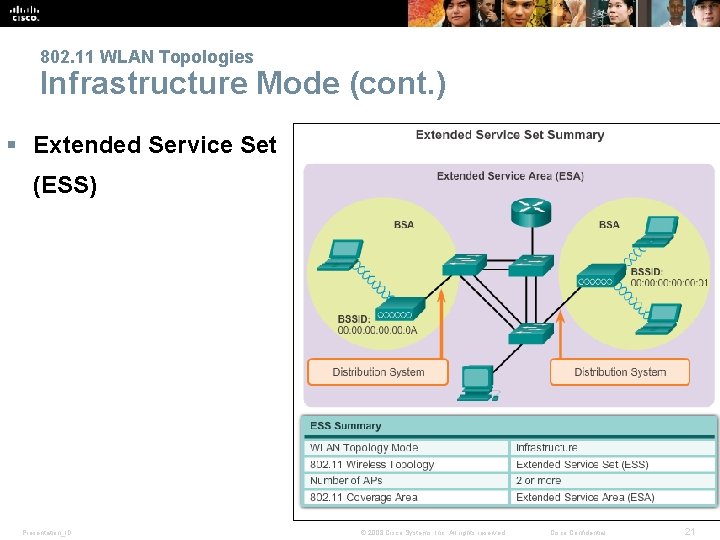
802. 11 WLAN Topologies 802. 11 Wireless Topology Modes § Ad. Hoc (IBSS) § Basic Service Set (BSS) § Extended Service Set (ESS) Presentation_ID © 2008 Cisco Systems, Inc. All rights reserved. Cisco Confidential 17

802. 11 WLAN Topologies 802. 11 Wireless Topology Modes (cont. ) Presentation_ID © 2008 Cisco Systems, Inc. All rights reserved. Cisco Confidential 18

802. 11 WLAN Topologies Ad Hoc Mode Tethering (personal hotspot) – Variation of the Ad Hoc topology when a smart phone or tablet with cellular data access is enabled to create a personal hotspot. Presentation_ID © 2008 Cisco Systems, Inc. All rights reserved. Cisco Confidential 19

802. 11 WLAN Topologies Infrastructure Mode § Basic Service Set (BSS) Presentation_ID © 2008 Cisco Systems, Inc. All rights reserved. Cisco Confidential 20

802. 11 WLAN Topologies Infrastructure Mode (cont. ) § Extended Service Set (ESS) Presentation_ID © 2008 Cisco Systems, Inc. All rights reserved. Cisco Confidential 21

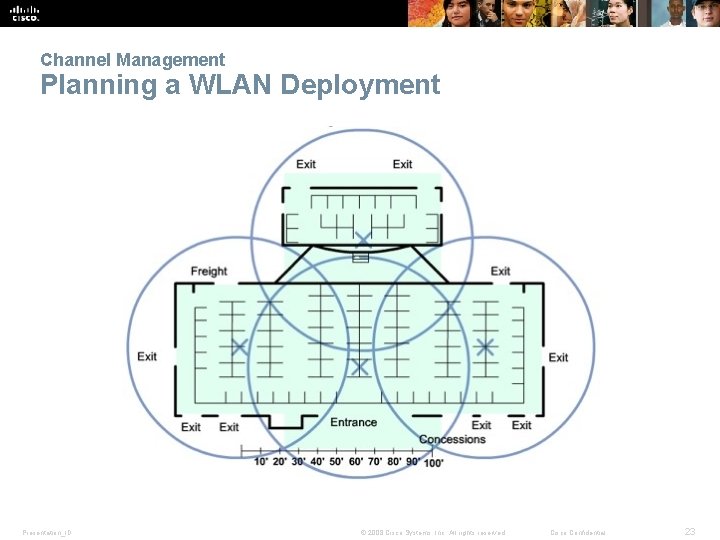
Wireless Operation Association Parameters § SSID – Unique identifier that wireless clients use to distinguish between multiple wireless networks in the same vicinity. § Password – Required from the wireless client to authenticate to the AP. Sometimes called the security key. § Network mode – Refers to the 802. 11 a/b/g/n/ac/ad WLAN standards. APs and wireless routers can operate in a mixed mode; i. e. , it can simultaneously use multiple standards. § Security mode – Refers to the security parameter settings, such as WEP, WPA, or WPA 2. § Channel settings – Refers to the frequency bands used to transmit wireless data. Wireless routers and AP can choose the channel setting or it can be manually set. Presentation_ID © 2008 Cisco Systems, Inc. All rights reserved. Cisco Confidential 22

Channel Management Planning a WLAN Deployment Presentation_ID © 2008 Cisco Systems, Inc. All rights reserved. Cisco Confidential 23

4. 3 Wireless LAN Security Presentation_ID © 2008 Cisco Systems, Inc. All rights reserved. Cisco Confidential 24

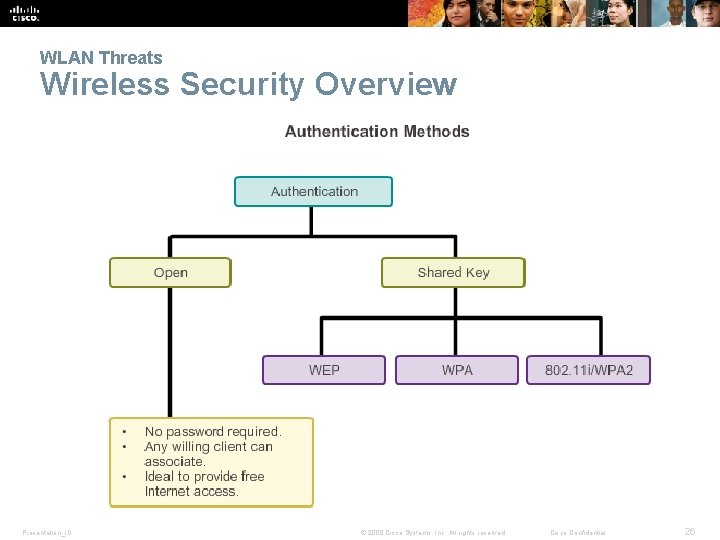
WLAN Threats Securing Wireless § Bruteforce Base Station SSID § Man-in-middle Presentation_ID © 2008 Cisco Systems, Inc. All rights reserved. Cisco Confidential 25

WLAN Threats Wireless Security Overview Presentation_ID © 2008 Cisco Systems, Inc. All rights reserved. Cisco Confidential 26

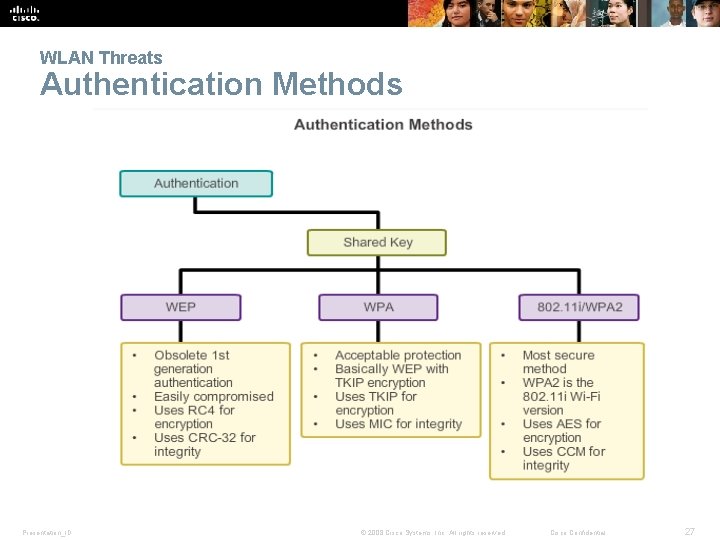
WLAN Threats Authentication Methods Presentation_ID © 2008 Cisco Systems, Inc. All rights reserved. Cisco Confidential 27

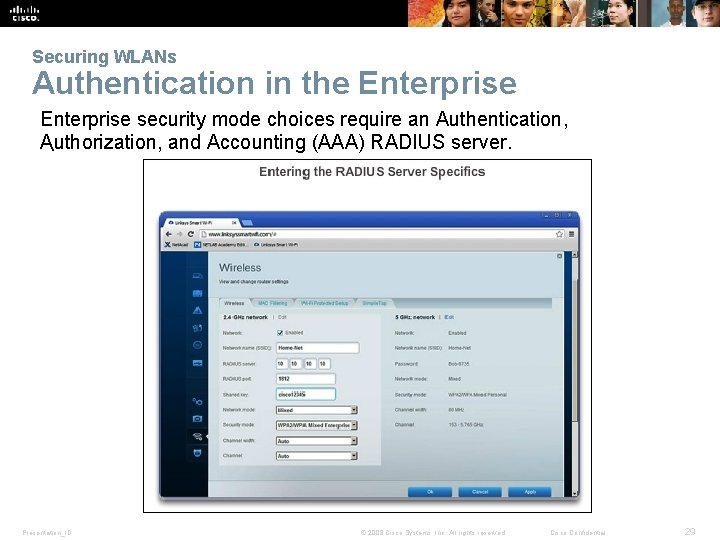
Securing WLANs Authenticating a Home User WPA and WPA 2 support two types of authentication: § Personal § Intended for home or small office networks, or authenticated users who use a pre-shared key (PSK). § No special authentication server is required. § Enterprise § Requires a Remote Authentication Dial-In User Service (RADIUS) authentication server. § Provides additional security. § Users must authenticate using 802. 1 X standard, which uses the Extensible Authentication Protocol (EAP) for authentication. Presentation_ID © 2008 Cisco Systems, Inc. All rights reserved. Cisco Confidential 28

Securing WLANs Authentication in the Enterprise security mode choices require an Authentication, Authorization, and Accounting (AAA) RADIUS server. . Presentation_ID © 2008 Cisco Systems, Inc. All rights reserved. Cisco Confidential 29

8. 4 Wireless LAN Configuration Presentation_ID © 2008 Cisco Systems, Inc. All rights reserved. Cisco Confidential 30

Configure a Wireless Router Configuring a Wireless Router Before installing a wireless router, consider the following settings: Presentation_ID © 2008 Cisco Systems, Inc. All rights reserved. Cisco Confidential 31

Configure a Wireless Router Configuring a Wireless Router ���������� �� Wireless LAN § Disable SSID Broadcast § Mac Address Filtering § WEP, WPA 2, 802. 1 x Presentation_ID © 2008 Cisco Systems, Inc. All rights reserved. Cisco Confidential 32

Presentation_ID © 2008 Cisco Systems, Inc. All rights reserved. Cisco Confidential 33