Appropriate Use of Technology Technology can help us






















- Slides: 23

Appropriate Use of Technology

Technology can help us: Communicate with others Gather information Share ideas Be entertained Technology has improved our quality of life!

But technology must be used appropriately

Cell Phone Safety Cell phones have helped us to: Communicate with others quickly Communicate with others while away from home Take pictures Access the internet without a computer

But cell phones can also be misused: Cyberbullying Sharing inappropriate pictures Predators targeting young people

Cell Phone Safety Tips

1. Protect Your Privacy Only give phone numbers to people you know and trust Never reply to text messages from people you don’t know Make sure you know how to block others from calling your phone

2. Respect others Think about how a text message might be read before you send it Never give anyone else’s phone number out without asking them if it is OK first Never take pictures of anyone with your phone without their permission

3. Use Common Sense Never meet anyone in real life who you only know through text messaging. Why?

Consequences of inappropriate cell phone use Why is cell phone use regulated at school? What are the rules for cell phone use at our school? What are the consequences for breaking these rules?

Sexting What is it? The sending of sexual messages or sexually explicit photos via cell phone. What are the short term and long term personal consequences of sexting : For the victim? For the perpetrator? What are the school and legal consequences for sexting? Are there consequences for viewing an inappropriate text? What about sharing an inappropriate message or picture with others?

Internet Safety The internet can be a great place to learn, be entertained and share ideas.

But the internet can be misused: Predators targeting young people Identity theft Inappropriate web sites Cyberbullying Internet addiction

Internet Safety Tips

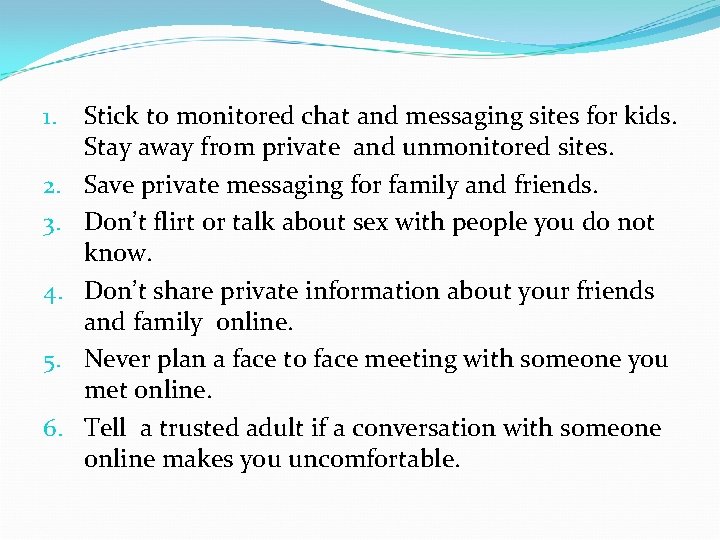
1. 2. 3. 4. 5. 6. Stick to monitored chat and messaging sites for kids. Stay away from private and unmonitored sites. Save private messaging for family and friends. Don’t flirt or talk about sex with people you do not know. Don’t share private information about your friends and family online. Never plan a face to face meeting with someone you met online. Tell a trusted adult if a conversation with someone online makes you uncomfortable.

Never share private information with someone you do not know Personal Information Private Information Age Gender Favorite music, color, food Pets Opinions • • Is this information you can share online? Full name Street address Email address Phone numbers Passwords Credit card numbers Social Security numbers Mother’s maiden name What about this information? Why not?

Identity Theft is when someone uses someone else’s private information to pretend to be them. They may use the information to buy things, apply for loans, credit cards or a driver’s license. Protect your private information!

Cyberbullying When someone uses technology (cell phones, instant messaging, chat rooms or social networking sites) to intimidate, threaten or harass another person, this is cyberbullying. Students sometimes don’t realize that a comment or picture that is put on the internet, may quickly be seen by hundreds of others.

The consequences for cyberbullying are severe, both for the victim and the bully. The victim may feel embarrassed, humiliated or ostracized, and may seek revenge. The perpetrator may face school and legal sanctions.

How can you prevent cyberbullying? • Don’t pass on hurtful text or instant messages. • Before you send or pass on a message, ask yourself these three questions: Is it true? Is it kind? Does it really need to be shared? • Don’t take photos of others without their permission • Don’t allow others to take your photo with their cell phone

If you find yourself a victim of cyberbullying: Leave the chat room or website immediately Sign off your computer Never reply to an inappropriate question from someone Make a copy of all inappropriate emails, text messages or instant messages Learn how to block messages from others Talk to a trusted friend adult

Keep it Safe! How are students protected from inappropriate use of technology: At home? At school? What might be the consequences of inappropriate use of technology: At home? At school? By law?

Material used for this presentation was gathered in part from www. cybersmartcurriculum. org