APOD Network Mechanisms and the APOD Redteam Experiments








- Slides: 21

APOD Network Mechanisms and the APOD Red-team Experiments Chris Jones Michael Atighetchi, Partha Pal, Franklin Webber BBN Technologies Qu. O & APOD 1 APOD 9/11/2021 NCA 2003 Christopher Jones

Outline • Motivating Scenario and APOD Overview • Qu. O Overview • APOD Description – Example APOD Strategies – Example APOD Tactics – Example APOD Mechanisms • Red-team Experiments • Concluding Remarks 2 APOD 9/11/2021 NCA 2003 Christopher Jones

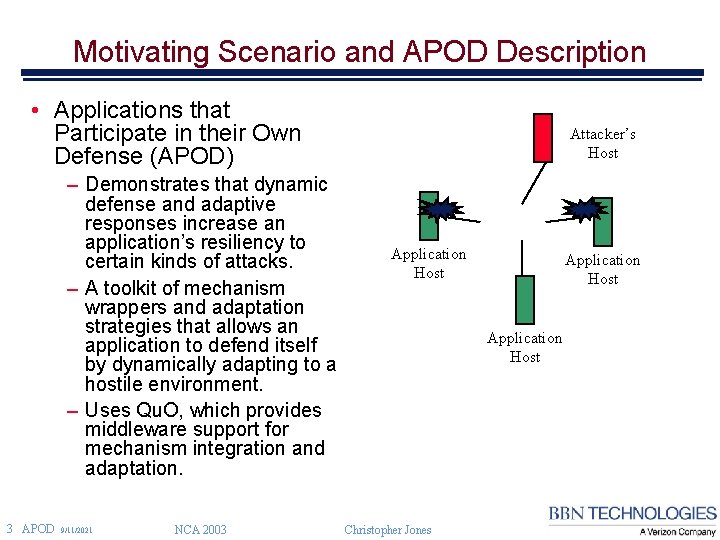
Motivating Scenario and APOD Description • Applications that Participate in their Own Defense (APOD) – Demonstrates that dynamic defense and adaptive responses increase an application’s resiliency to certain kinds of attacks. – A toolkit of mechanism wrappers and adaptation strategies that allows an application to defend itself by dynamically adapting to a hostile environment. – Uses Qu. O, which provides middleware support for mechanism integration and adaptation. 3 APOD 9/11/2021 NCA 2003 Attacker’s Host Application Host Christopher Jones

Outline • Motivating Scenario and APOD Overview • Qu. O Overview • APOD Description – Example APOD Strategies – Example APOD Tactics – Example APOD Mechanisms • Red-team Experiments • Concluding Remarks 4 APOD 9/11/2021 NCA 2003 Christopher Jones

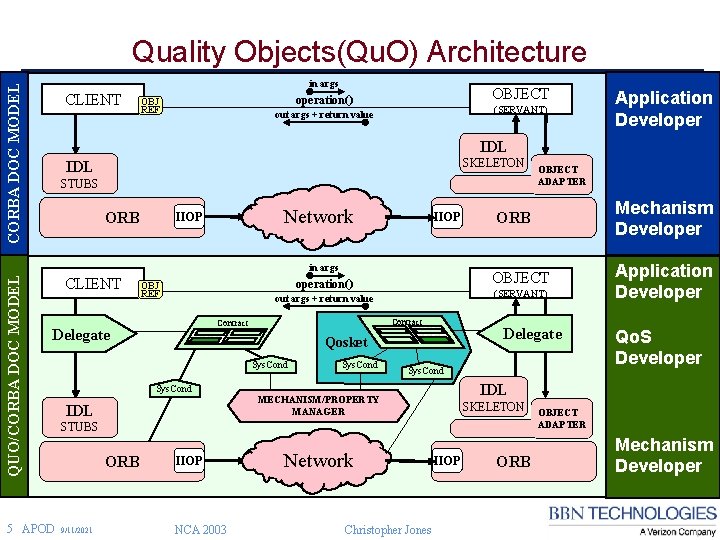
Quality Objects(Qu. O) Architecture CORBA DOC MODEL in args CLIENT OBJECT operation() OBJ REF (SERVANT) out args + return value IDL SKELETON IDL STUBS ORB Network IIOP in args QUO/CORBA DOC MODEL Application Developer CLIENT 5 APOD (SERVANT) out args + return value Contract Delegate Qosket Sys. Cond MECHANISM/PROPERTY MANAGER SKELETON STUBS ORB 9/11/2021 IIOP NCA 2003 Network Christopher Jones Application Developer Qo. S Developer IDL Sys. Cond IDL Mechanism Developer ORB OBJECT operation() OBJ REF OBJECT ADAPTER IIOP ORB OBJECT ADAPTER Mechanism Developer

Qu. O Overview • Qu. O is a middleware framework that supports the development and execution of adaptation and adding it to an application. • Adaptation can be driven by changes in an application’s operating environment. – Host resources (CPU and memory) usage. – Network resource availability. – Host and Network Intrusion status. • The adaptive code is encapsulated in a middleware component called “qosket”. – A qosket is a set of specifications and implementations that defines a reusable module of specific adaptive behavior. • It can be added into a distributed object application with minimum impact on the application. 6 APOD 9/11/2021 NCA 2003 Christopher Jones

Qu. O Overview (cont. ) • Quality Description Languages (QDL) – Contract description language, adaptive behavior description language. – Code generators that generate Java and C++ code for contracts, delegates, creation, and initialization. • System Condition Objects – Provide interfaces to resources, managers, and mechanisms. • Qu. O Runtime Kernel – Contract evaluator. – Factory object which instantiates contract and system condition objects. 7 APOD 9/11/2021 NCA 2003 Christopher Jones

Outline • Motivating Scenario and APOD Overview • Qu. O Overview • APOD Description – Example APOD Strategies – Example APOD Tactics – Example APOD Mechanisms • Red-team Experiments • Concluding Remarks 8 APOD 9/11/2021 NCA 2003 Christopher Jones

APOD Description • Key Idea: by adapting to and trying to control its environment, an application can increase its chances of survival under attack. – Use Qu. O to integrate multiple security mechanisms into a coherent strategy for adaptive defense. – This is complementary to the usual hardening or protection of applications, resources, or services where available and practical. • Ties security information to the adaptation of an application through the Qu. O system condition objects. • APOD has sensor mechanisms that feed defense tactics and strategies. – Actuator mechanisms implement tactic and strategy reactions. • APOD tactics integrate sensors and actuator mechanisms to mount a local defensive response. • Combining individual mechanisms and tactics into higher-level defense strategies helps applications meet survivability requirements. • The following slides are examples, not an exhaustive list of the possibilities or the mechanisms, tactics, and strategies that we are using. 9 APOD 9/11/2021 NCA 2003 Christopher Jones

APOD Strategies • Use Qu. O middleware to coordinate all available defense mechanisms in a coherent strategy. • Examples of APOD strategies have been created: – “outrun”: move application components off corrupted hosts and on to good ones at a rate faster than the hosts go bad. » Slow down the attacker’s ability to corrupt host by quarantine. – “contain”: quarantine bad hosts and bad LANs by limiting or blocking network traffic from them and, within limits, shutting them down. » Respond quickly with locally gathered information. » Can only quarantine so many hosts or LANs before application performance becomes affected. » In follow on projects we are looking at having backup hosts to replenish application capabilities depleted by quarantining bad application hosts. 10 APOD 9/11/2021 NCA 2003 Christopher Jones

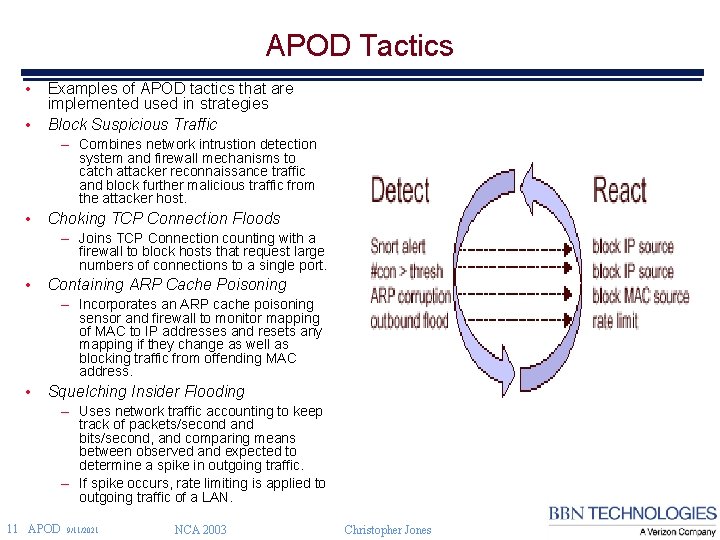
APOD Tactics • • Examples of APOD tactics that are implemented used in strategies Block Suspicious Traffic – Combines network intrustion detection system and firewall mechanisms to catch attacker reconnaissance traffic and block further malicious traffic from the attacker host. • Choking TCP Connection Floods – Joins TCP Connection counting with a firewall to block hosts that request large numbers of connections to a single port. • Containing ARP Cache Poisoning – Incorporates an ARP cache poisoning sensor and firewall to monitor mapping of MAC to IP addresses and resets any mapping if they change as well as blocking traffic from offending MAC address. • Squelching Insider Flooding – Uses network traffic accounting to keep track of packets/second and bits/second, and comparing means between observed and expected to determine a spike in outgoing traffic. – If spike occurs, rate limiting is applied to outgoing traffic of a LAN. 11 APOD 9/11/2021 NCA 2003 Christopher Jones

APOD Network Sensor Mechanisms • Network Intrusion Detection – Attacker can run live attacks and known scripted network attacks on hosts. – Use Snort, a lightweight network intrusion detection system. – Extract the offending host addresses to pass to an APOD strategy. • TCP Connection Flood sensor – Attacker can flood port with many connections making it very difficult or impossible for legitimate clients to connect. – Have a mechanism using netstat to determine number of connections to a given port. – Mechanism monitors application ports for “too many” connections and will warn an APOD strategy of any host that has gone over the connection threshold. • ARP cache poisoning detection – Attacker with access to a subnet can use ARP cache poisoning to disrupt or intercept network traffic. – Tool to detect changes in MAC/IP pairings and notify an APOD tactic or strategy of changes. – Uses ping and arp commands to get pairings and compares previously collected pairing for changes. 12 APOD 9/11/2021 NCA 2003 Christopher Jones

APOD Network Actuator Mechanisms • Network traffic filters – Uses iptables for blocking and rate-limiting traffic from hosts believed to be malicious. • Bandwidth Management – Intserv (RSVP, Secure. RSVP) » Uses an enhanced RSVP version of Darmstadt’s RSVP implementation. » Enhanced version done at North Carolina State University. – Bandwidth Broker » Tool using tc command to make changes in queuing policies of routers. • Secure network traffic – Uses Free. S/WAN IPSec for protecting network traffic. – Dynamically bring up IPSec between two hosts. • Dynamic endpoint mechanism – Uses a NAT gateway to hide the real endpoints, address and port, of application. – The “fake” endpoints are chosen randomly and changed periodically. 13 APOD 9/11/2021 NCA 2003 Christopher Jones

Outline • Motivating Scenario and APOD Overview • Qu. O Overview • APOD Description – Example APOD Strategies – Example APOD Tactics – Example APOD Mechanisms • Red-team Experiments • Concluding Remarks 14 APOD 9/11/2021 NCA 2003 Christopher Jones

APOD Red-teaming Experimentation • Reasons for experiments. – Validate APOD idea that dynamic adaptation defenses can prolong an applications usefulness in a hostile environment. – Also, analyzing the overhead of APOD. • Sandia Labs red-team tasked with validating APOD. – Outside, independent team. – Given full knowledge of application, APOD defenses added, and test network. • Red-teaming happened in two distinct experiments. – Each experiment consisted of multiple runs of the defended application. – During each run, the red-team would try different attacks. » Started with single attacks per run to multiple attacks per run. 15 APOD 9/11/2021 NCA 2003 Christopher Jones

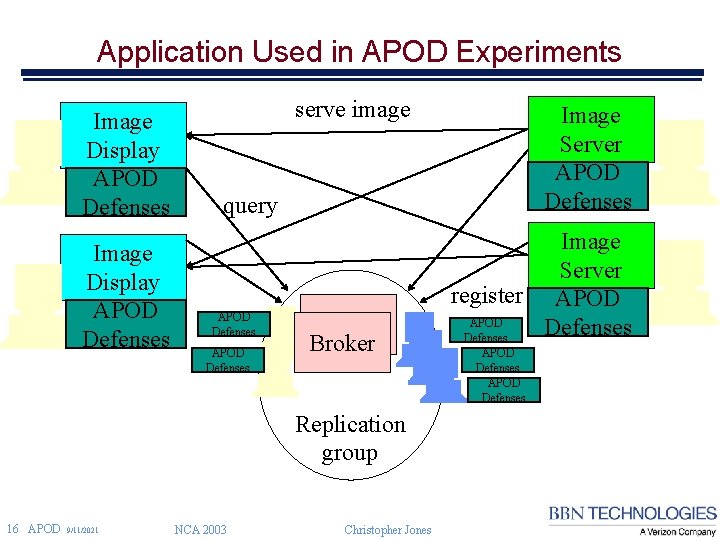
Application Used in APOD Experiments Image Display APOD Defenses serve image query APOD Defenses Broker Replication group 16 APOD 9/11/2021 Image Server APOD Defenses NCA 2003 Christopher Jones Image Server register APOD Defenses

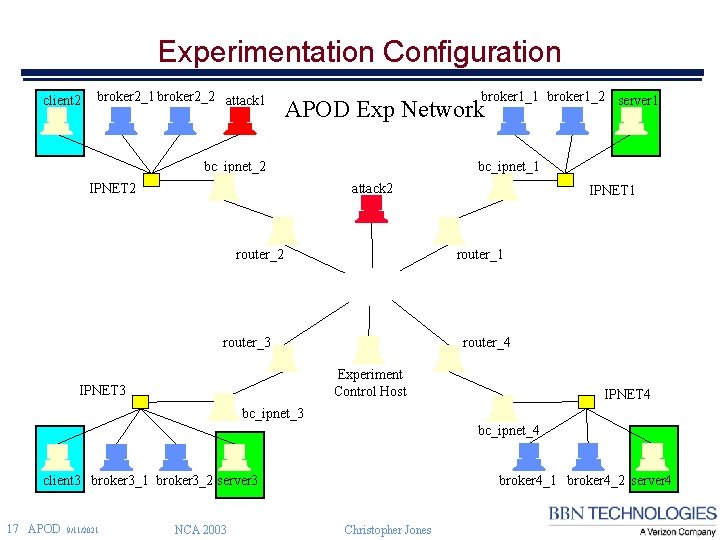
Experimentation Configuration client 2 broker 2_1 broker 2_2 attack 1 broker 1_2 server 1 APOD Exp Network bc_ipnet_2 IPNET 2 bc_ipnet_1 attack 2 router_2 IPNET 1 router_3 router_4 Experiment Control Host IPNET 3 IPNET 4 bc_ipnet_3 bc_ipnet_4 client 3 broker 3_1 broker 3_2 server 3 17 APOD 9/11/2021 NCA 2003 broker 4_1 broker 4_2 server 4 Christopher Jones

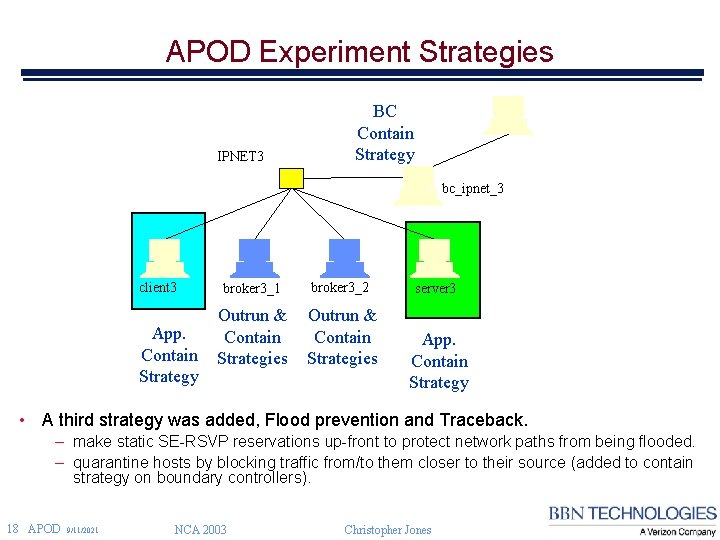
APOD Experiment Strategies IPNET 3 BC Contain Strategy bc_ipnet_3 client 3 App. Contain Strategy broker 3_1 broker 3_2 Outrun & Contain Strategies server 3 App. Contain Strategy • A third strategy was added, Flood prevention and Traceback. – make static SE-RSVP reservations up-front to protect network paths from being flooded. – quarantine hosts by blocking traffic from/to them closer to their source (added to contain strategy on boundary controllers). 18 APOD 9/11/2021 NCA 2003 Christopher Jones

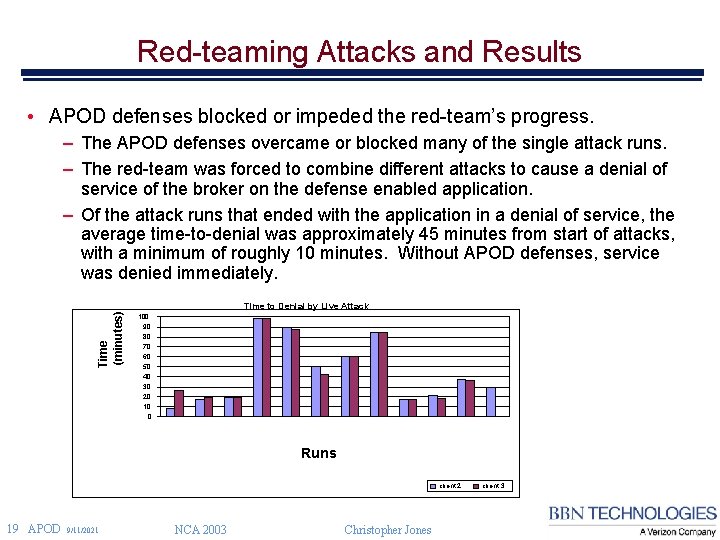
Red-teaming Attacks and Results • APOD defenses blocked or impeded the red-team’s progress. – The APOD defenses overcame or blocked many of the single attack runs. – The red-team was forced to combine different attacks to cause a denial of service of the broker on the defense enabled application. – Of the attack runs that ended with the application in a denial of service, the average time-to-denial was approximately 45 minutes from start of attacks, with a minimum of roughly 10 minutes. Without APOD defenses, service was denied immediately. Time (minutes) Time to Denial by Live Attack 100 90 80 70 60 50 40 30 20 10 0 Runs client 2 19 APOD 9/11/2021 NCA 2003 Christopher Jones client 3

Results • The cost of adding the APOD defenses to image latency was approximately 5% to 20% depending which tactics and strategies were in place. – We concluded that most of the latency increase was caused by the containment strategy and accompanying mechanisms that ran on the boundary control routers. 20 APOD 9/11/2021 NCA 2003 Christopher Jones

Concluding Remarks • Conclusion. – Dynamic adaptation has added value for an application by giving it the ability to prolong its usefulness in the presents of attacks. – This prolonged usefulness has a reasonable cost. – Red-team experiments are beneficial for validating and “stress testing” our defenses. • APOD is being used in other survivability projects. – Using and expanding of APOD mechanisms, tactics, and strategies. – Other projects include ITUA, DPASA, and Dynamic Quarantine. • Websites: – Qu. O: quo. bbn. com – APOD: apod. bbn. com – ITUA: itua. bbn. com 21 APOD 9/11/2021 NCA 2003 Christopher Jones