DDo S Vulnerability Analysis of Bit Torrent Protocol
DDo. S Vulnerability Analysis of Bit. Torrent Protocol CS 239 project Spring 2006

Background n Bit. Torrent (BT) q q q n P 2 P file sharing protocol 30% of Internet traffic 6881 - top 10 scanned port in the Internet DDo. S q q q Distributed – hard to guard against by simply filtering at upstream routers Application level (resources) Network level (bandwidth)
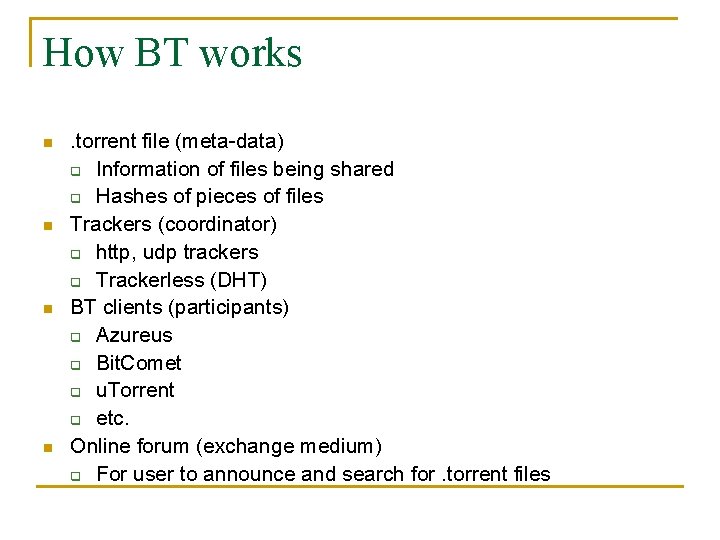
How BT works n n . torrent file (meta-data) q Information of files being shared q Hashes of pieces of files Trackers (coordinator) q http, udp trackers q Trackerless (DHT) BT clients (participants) q Azureus q Bit. Comet q u. Torrent q etc. Online forum (exchange medium) q For user to announce and search for. torrent files

Communication with trackers seeder. torrent I have the file! Who has the file? Tracker clients Discussion forum Who has the file? . torrent client
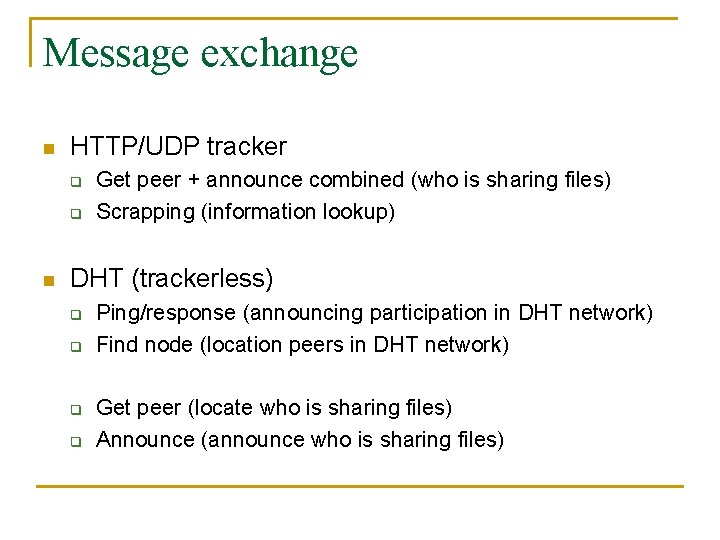
Message exchange n HTTP/UDP tracker q q n Get peer + announce combined (who is sharing files) Scrapping (information lookup) DHT (trackerless) q q Ping/response (announcing participation in DHT network) Find node (location peers in DHT network) Get peer (locate who is sharing files) Announce (announce who is sharing files)

Vulnerabilities n Spoofed information q q n * Both http and udp trackers allow specified IP in announce DHT does not allow specified IP in announce n Allow spoofed information on who is participating in DHT network n Possible to redirect a lot of DHT query to a victim Compromised tracker
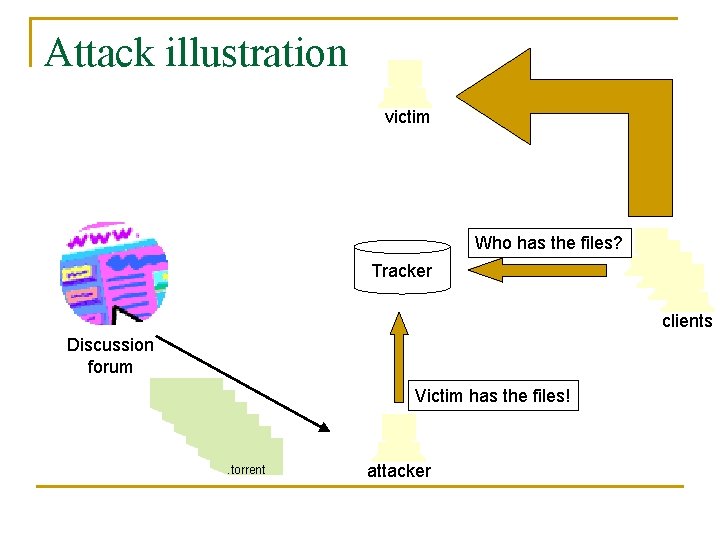
Attack illustration victim Who has the files? Tracker clients Discussion forum. torrent Victim has the files! attacker

Experiments n Discussion forum (http: //www. mininova. org) q 1191 newly uploaded. torrent files in 2 days n Victim (131. 179. 187. 205) q Apache web server (configured to serve 400 clients) q tcpdump, netstat n Attacker q Python script to process. torrent files and contact trackers n Zombies q Computers running Bit. Torrent clients in the Internet
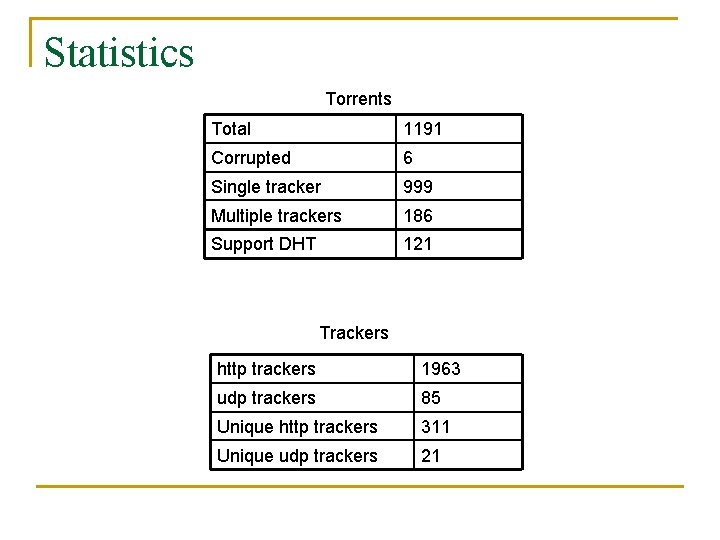
Statistics Torrents Total 1191 Corrupted 6 Single tracker 999 Multiple trackers 186 Support DHT 121 Trackers http trackers 1963 udp trackers 85 Unique http trackers 311 Unique udp trackers 21
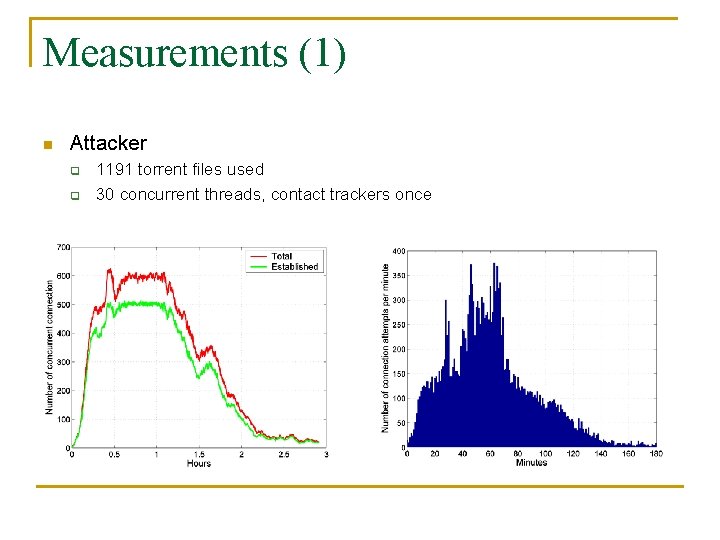
Measurements (1) n Attacker q q 1191 torrent files used 30 concurrent threads, contact trackers once

Measurements (2) n Attacker q 1191 torrent files used q 40 concurrent threads, contact trackers 10 times q Attack ends after 8 hours
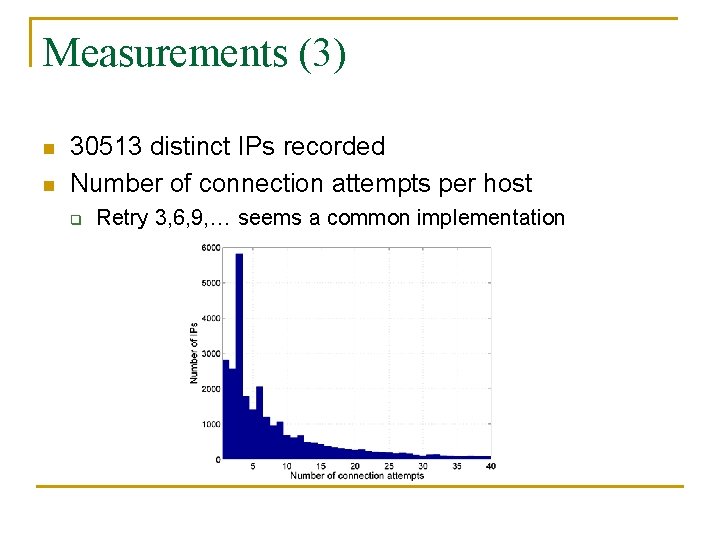
Measurements (3) n n 30513 distinct IPs recorded Number of connection attempts per host q Retry 3, 6, 9, … seems a common implementation
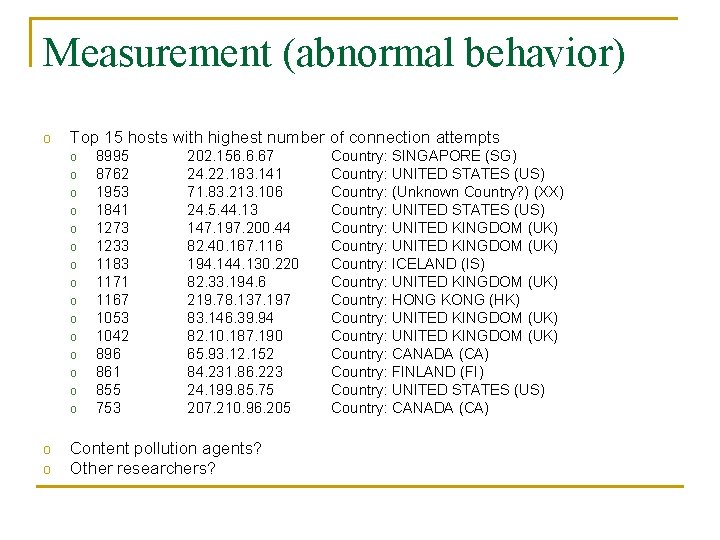
Measurement (abnormal behavior) o Top 15 hosts with highest number of connection attempts o o o o o 8995 8762 1953 1841 1273 1233 1183 1171 1167 1053 1042 896 861 855 753 202. 156. 6. 67 24. 22. 183. 141 71. 83. 213. 106 24. 5. 44. 13 147. 197. 200. 44 82. 40. 167. 116 194. 144. 130. 220 82. 33. 194. 6 219. 78. 137. 197 83. 146. 39. 94 82. 10. 187. 190 65. 93. 12. 152 84. 231. 86. 223 24. 199. 85. 75 207. 210. 96. 205 Content pollution agents? Other researchers? Country: SINGAPORE (SG) Country: UNITED STATES (US) Country: (Unknown Country? ) (XX) Country: UNITED STATES (US) Country: UNITED KINGDOM (UK) Country: ICELAND (IS) Country: UNITED KINGDOM (UK) Country: HONG KONG (HK) Country: UNITED KINGDOM (UK) Country: CANADA (CA) Country: FINLAND (FI) Country: UNITED STATES (US) Country: CANADA (CA)
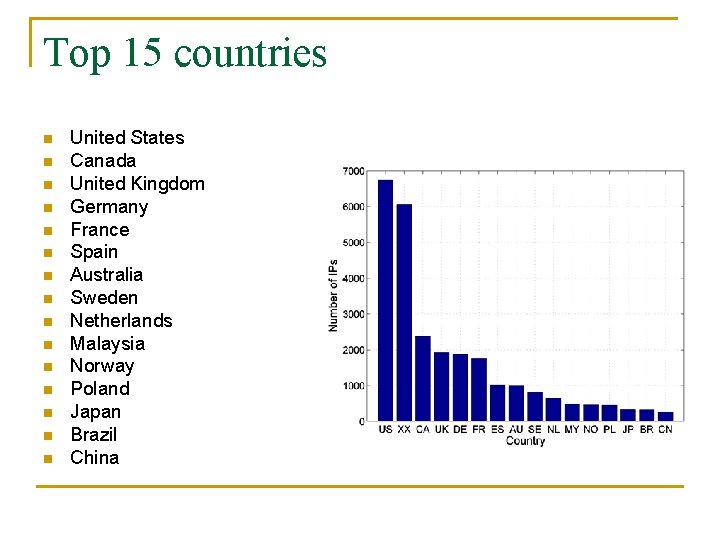
Top 15 countries n n n n United States Canada United Kingdom Germany France Spain Australia Sweden Netherlands Malaysia Norway Poland Japan Brazil China

Countries with less BT clients running n n n n Albania Bermuda Bolivia Georgia Ghana Kenya Lao Lebanon Monaco Mongolia Nicaragua Nigeria Qatar Tanzania Uganda Zimbabwe
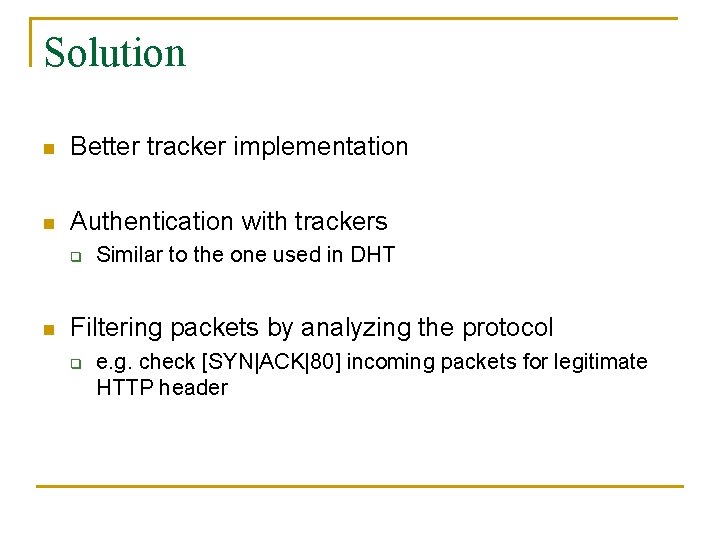
Solution n Better tracker implementation n Authentication with trackers q n Similar to the one used in DHT Filtering packets by analyzing the protocol q e. g. check [SYN|ACK|80] incoming packets for legitimate HTTP header

End Q and A

seeder. torrent I have the file! Tracker Discussion forum Who has the file? . torrent client
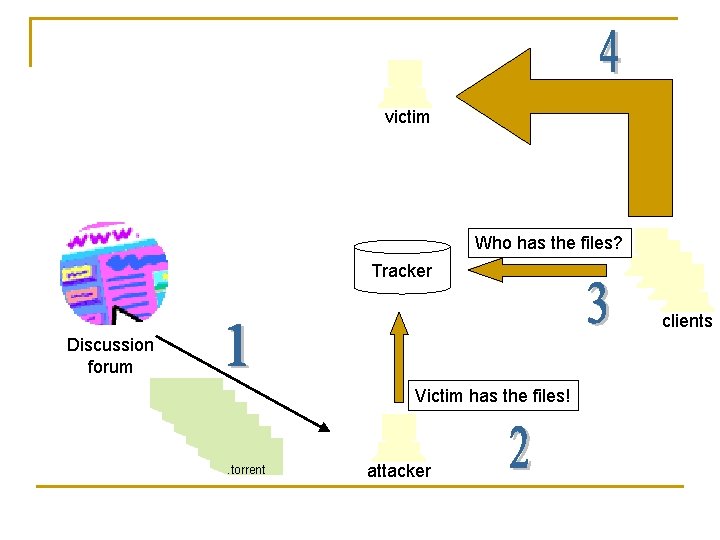
victim Who has the files? Tracker clients Discussion forum. torrent Victim has the files! attacker
- Slides: 19