26 of 1 Compliance With the Red Flags
















- Slides: 19

26 of 1… Compliance With the Red Flags Rule in Higher Education Sarah Morrow, MBA-ISM, CIPP/US, GISP Chief Privacy Officer The Pennsylvania State University Maura Johnston, JD, CIPP/US University Privacy Officer University of Pennsylvania

Compliance with financial regulations in higher education, especially the Red Flags Rule, is as complex as it gets; it is a regulation with elusive requirements. Join two university privacy officers to hear about how compliance was achieved at their respective institutions. Abstract

• This presentation will provide an overview of the Red Flags Rule; • How IT is an integral part of university compliance in this area; and • Answer questions you may have about where, when, and why this law applies to institutions of higher learning. Objectives


Red Flags Rule Was Adopted by FTC to require: • financial institutions and creditors that maintain certain accounts to have an identity theft prevention program; • users of consumer reports to implement procedures for handling notices of address discrepancy from credit bureaus; and • credit/debit card issuers to have procedures to assess validity of change of address notices. Who has to comply with the Red Flags Rule? • Financial institutions • “Creditors” who have “covered accounts”

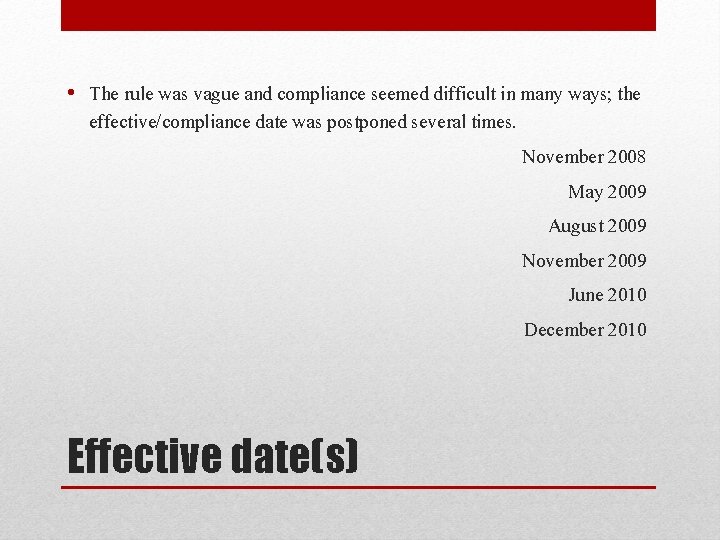
• The rule was vague and compliance seemed difficult in many ways; the effective/compliance date was postponed several times. November 2008 May 2009 August 2009 November 2009 June 2010 December 2010 Effective date(s)

• Under Red Flags Program Clarification Act of 2010, a “creditor” is an entity that regularly, in the ordinary course of business: • Obtains or uses credit reports in connection with a credit transaction; • Provides information to credit bureaus, in connection with a credit transaction; or • Advances funds that must be repaid in the future. • Interpreted by FTC to cover higher education institutions. “Creditor”

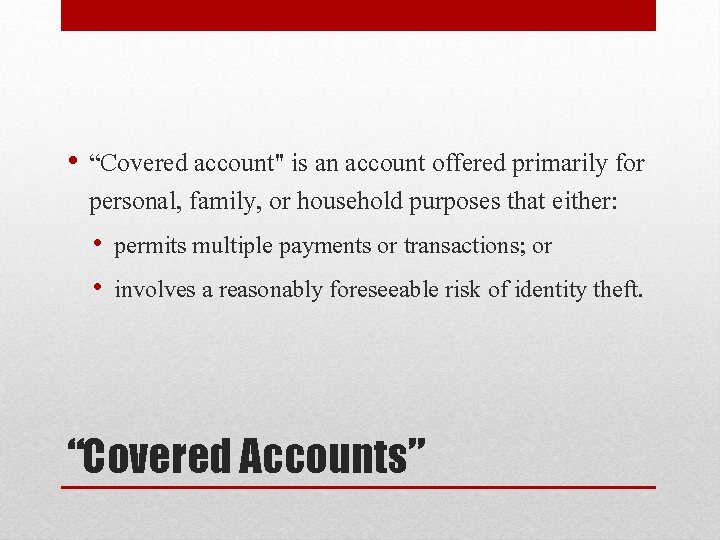
• “Covered account" is an account offered primarily for personal, family, or household purposes that either: • permits multiple payments or transactions; or • involves a reasonably foreseeable risk of identity theft. “Covered Accounts”

Identify Relevant Red Flags • Identify the red flags of identity theft you’re likely to come across Detect Red Flags • Set up procedures to detect those red flags in your day-to-day operations Prevent and Mitigate Identity Theft • If you spot the red flags you’ve identified, respond appropriately to prevent and/or mitigate harm Design program appropriate to organization’s size and complexity, and nature of operations Update program periodically • Risks of identity theft can change rapidly, so keep program current and educate staff Identity Theft Prevention Program

• Federal Trade Commission identifies 26, in five categories: • alerts, notifications, or warnings from a consumer reporting agency • suspicious documents • suspicious identifying information, such as a suspicious address • unusual use of – or suspicious activity relating to – a covered account • notices from customers, victims of identity theft, law enforcement authorities, or other businesses about possible identity theft in connection with “covered accounts” Some Potential Red Flags

• Committee formed to create and vet the required training. • Bursar (leader) • Corporate Controller Office • Privacy • Financial Officers • IT and Security Offices • CPO had final approval sign off • Implemented prior to actual effective date • Annual training Penn State’s Approach

• At Penn State • Financial Officers • Student Aid • Bursar • Credit Card Transaction locations…. (all around us) • Milton S. Hershey Medical Center • University Health Services • ID+ Lion. Cash • Security Operations and Services • PCI Penn State’s Approach

• Security Operation and Services • Watches my back • PCI-DSS may find more than simple credit card fraud • Teaching moments • Technological advances make identity theft more common and easier to achieve • Keep APT on the radar • Devise more accurate methods to assess risk Penn State’s Approach

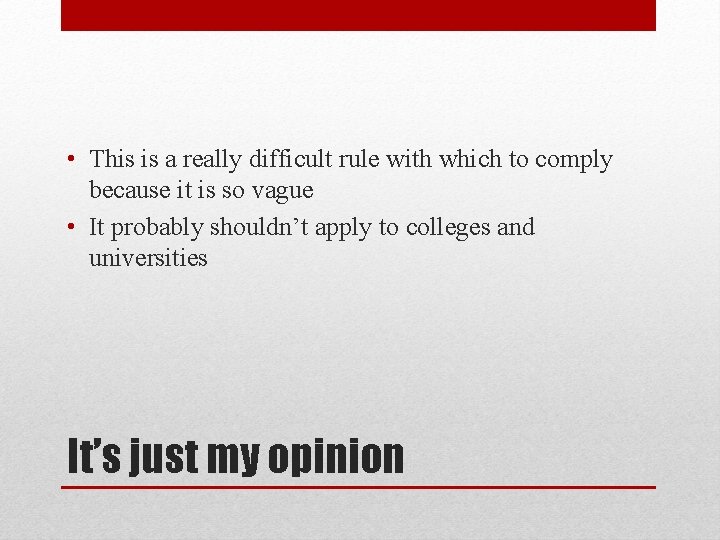
• This is a really difficult rule with which to comply because it is so vague • It probably shouldn’t apply to colleges and universities It’s just my opinion

• Formed Red Flags Task Force • Representatives from potentially covered areas • Narrowed group to areas we concluded were covered • Central policy developed • Simplified content of Rule • Specific to Penn • Procedures and training developed by each covered area Penn’s Approach

• Covered areas: • Student Financial Services • Tuition refunds • Collections • Student Health • Dental Medicine • Veterinary Medicine • Home Ownership Services • Penn. Card • Health System Penn’s Approach

IT’s role in preventing identity theft Example: Health System - Medical Office Visit • If Red Flags present (such as ID that looks altered or forged) Incident Report is created • Incident Report is forwarded to team that reviews and, if appropriate, posts Red Flags Alert • Alert interfaces with all core registration databases • Incident Report is scanned into electronic health record system Penn’s Approach

• Review/update Red Flags program periodically • Experienced incidents of identity theft in the past year? • Experienced changes in methods of identity theft in the past year? • Amended Red Flags procedures since they were first adopted? • Any changes that might present new potential opportunities for identity theft? • Staff received training on Red Flags procedures? • Suggestions for changes to Red Flags program? Penn’s Approach

• Sarah Morrow sdm 24@psu. edu (814)863 -3049 • Maura Johnston mauraa@upenn. edu (215)898 -1934 Questions?
 Red flags for developmental delays
Red flags for developmental delays Red flags alarmsymptome der medizin
Red flags alarmsymptome der medizin Red flags checklist
Red flags checklist Red flags cefaleia
Red flags cefaleia Vertigo central vs peripheral
Vertigo central vs peripheral Food red flags
Food red flags Red flags of junk science
Red flags of junk science Iap developmental milestones
Iap developmental milestones Bis know your customer
Bis know your customer Red flags lombalgia
Red flags lombalgia Occupancy fraud red flags
Occupancy fraud red flags Red flags nyeri kepala
Red flags nyeri kepala Headache red flags
Headache red flags Financial statement red flags
Financial statement red flags Red flags of junk science
Red flags of junk science Pediatric headache red flags
Pediatric headache red flags Black market peso exchange diagram
Black market peso exchange diagram Windump examples
Windump examples The intoif int1if and int2if bits function as flags
The intoif int1if and int2if bits function as flags Globe theatre flags
Globe theatre flags