WHOAMI IT SECURITY ANALYST JOHNDEERE CORPORATE COMPUTER SECURITY






- Slides: 15

WHOAMI • IT SECURITY ANALYST @JOHNDEERE CORPORATE COMPUTER SECURITY • RED/BLUE TEAM MEMBER FOR NORTH EAST CYBERPROTECTION CENTER (NECPC) ARMY RESERVES @ US

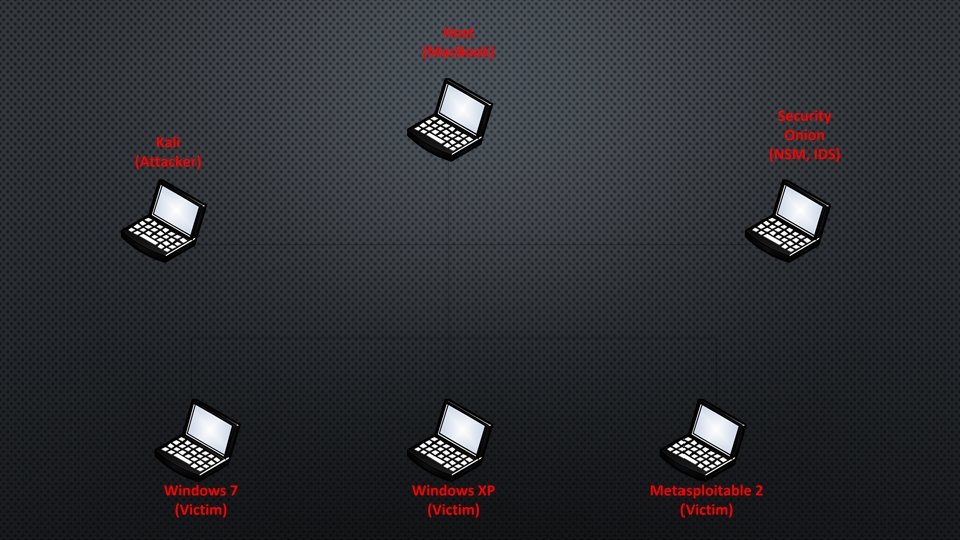
SETTING UP SECURITY LAB FOR PERSONAL USE VIRTUALBOX KALI 2. 0 METASPLOITABLE 2 WINDOWS XP (SERVICE PACK 1) WINDOWS 7 64 BIT

DISCLAIMER FOR EDUCATIONS PURPOSES ONLY. NEVER ATTEMPT TO GAIN ACCESS TO OR PENTEST A NETWORK THAT YOU DO NOT HAVE WRITTEN PERMISSION TO DO SO. YOU CAN FACE LEGAL ACTION AND COULD SERVE JAIL TIMEA. NY ACTIVITIES DONE OUTSIDE THIS TRAINING ENVIRONMENT ARE THE RESPONSIBILITY OF THE INDIVIDUAL PERFORMINGTHEM

INSTALL VIRTUALBOX HTTPS: //WWW. VIRTUALBOX. ORG

INSTALL KALI 2. 0 PREBUILT IMAGE HTTP: //IMAGES. KALI. ORGK / ALI-LINUX-2. 0. 0 -VBOX-AMD 64. 7 Z ISO HTTPS: //WWW. KALI. ORG/DOWNLOADS/

INSTALL METASPLOITABLE 2 HTTP: //SOURCEFORGE. NET/PROJECTS/METASPLOITABLE/FILES/LATEST/DOWNLOAD? SOURCE=FILES

INSTALL WINDOWS XP SP-1 90 DAY TRIAL VERSION HTTPS: //DEV. WINDOWS. COM/EN-US/MICROSOFT-EDGE/TOOLS/VMS/WINDOWS

INSTALL WINDOWS 7 90 DAY TRIAL VERSION HTTPS: //DEV. WINDOWS. COM/EN-US/MICROSOFT-EDGE/TOOLS/VMS/WINDOWS


WHAT IS METASPLOIT? • • •

WINDOWS 7 WEB_DELIVERY • QUICKLY FIRES UP A WEB SERVER THAT SERVES A PAYLOADT. HE PROVIDED COMMAND WILL START THE SPECIFIED SCRIPTING LANGUAGE INTERPRETER AND THEN DOWNLOAD AND EXECUTE THE PAYLOAD. • DOES NOT WRITE TO DISK SO ITIS LESS LIKELY TO TRIGGERAV SOLUTIONS AND WILL ALLOW PRIVILEGE ESCALATIONS SUPPLIED BY METERPRETER • REFERENCES: • HTTP: //SECURITYPADAWAN. BLOGSPOT. COM/2014/02/PHP-METERPRETER-WEB-DELIVERY. HTML • HTTP: //WWW. PENTESTGEEK. COM/2013/07/19/INVOKE-SHELLCODE/ • HTTP: //WWW. POWERSHELLMAGAZINE. COM/2013/04/19/PSTIP-POWERSHELL-COMMAND-LINE-SWITCHES-SHORTCUTS/ • HTTP: //WWW. DARKOPERATOR. COM/BLOG/2013/3/21/POWERSHELL-BASICS-EXECUTION-POLICY-AND-CODE-SIGNING-PART- 2. HTML

WINDOWS 7 BYPASSUAC_INJECTION • WILL BYPASS WINDOWS UAC BY UTILIZING THETRUSTED PUBLISHER CERTIFICATE THROUGH PROCESS INJECTION. • SPAWN A SECOND SHELL THAT HAS THE UAC FLAG TURNED OFF

WINDOWS XP MS 08_067_NETAPI • EXPLOITS A PARSING FLAW IN THE PATH CANONICALIZATIONCODE OF NETAPI 32. DLL THROUGH THE SERVER SERVICE. REFERENCES: HTTP: //CVEDETAILS. COM/CVE/2008 -4250/ HTTP: //WWW. OSVDB. ORG/49243 HTTP: //TECHNET. MICROSOFT. COM/EN-US/SECURITY/BULLETIN MS 08 -067 / HTTP: //WWW. RAPID 7. COM/VULNDB/LOOKUP/DCERPC-MS-NETAPI-NETPATHCANONICALIZE-DOS

METASPLOITABLE 2 VSFTP 2. 3. 4 BACKDOOR • EXPLOITS A MALICIOUS BACKDOOR THAT WAS ADDED TO THEVSFTPD DOWNLOAD ARCHIVE. • INTRODUCED INTO THE VSFTPD-2. 3. 4. TAR. GZ ARCHIVE BETWEEN JUNE 30 TH 2011 AND JULY 1 ST 2011 • REFERENCES: • OSVDB-73573 • URL: HTTP: //PASTEBIN. COMA/ ETT 9 SS 5 • URL: HTTP: //SCARYBEASTSECURITY. BLOGSPOT. COM/2011/07/ALERT-VSFTPD-DOWNLOADBACKDOORED. HTML

CONTACT INFO ROY. ARGUILEZ@GMAIL. COM ARGUILEZROY@JOHNDEERE. COM