Toysmart Key Concepts William J Frey College of





























- Slides: 35

Toysmart: Key Concepts William J. Frey College of Business Administration UPRM

Acknowledgment • Much of this material is taken from a summary of intermediate moral concepts provided by Dr. Chuck Huff, St. Olaf College.

Intermediate Moral/Non-Moral Concepts in Toysmart Privacy Property Dot. coms

There are different kinds of privacy • Accessibility Privacy – Access to your person – Camera • Decision Privacy – Some decisions (certainly not all) are private – Roe vs Wade: government cannot interfere in your right to decide whether or not to have an abortion • Information Privacy – Control over information about the person – Genetic/Health

Privacy: Associated Concepts • Normative vs. Natural – Whether you in fact have exclusive control over your information (=natural) – Whether you ought to have exclusive control over your information (=normative) • Reasonable Expectation – Relationship between normative and natural privacy – If there is a reasonable expectation of privacy, then violating this is prima facie wrong – Planning a crime in a phone booth; growing marijuana in your house; as opposed to leaving your door open. • First two imply a reasonable expectation. But first was defensible privacy, the second not.

Privacy Distinctions • Non-Public-Private Information – Non-public: what happens in the privacy of your home • Public-Private Information – What you buy at the supermarket is public, but we have some expectation of privacy about it • Why are we concerned about public private information? – Broadcasting picture of you across the internet? – Marketing specialists assembling publically available data about you to develop a profile and target specific advertising toward you. (Data Mining) • The computer instruments human action – Digitalizing your public private information allows it to be copied (easily), disseminated (worldwide), and compiled (combined with other data)

Is Privacy a Right • Moral Right = an essential (to autonomy) capacity of action others are obliged to recognize and respect. • Legal Right – Privacy is legal right that is based on an agreement among people. It can be revoked only when those people decide to change the terms of that agreement. • Respect Based – Privacy is essential to recognizing and respecting the autonomy of the individual. It is a capacity of action essential to the exercise of individual autonomy.

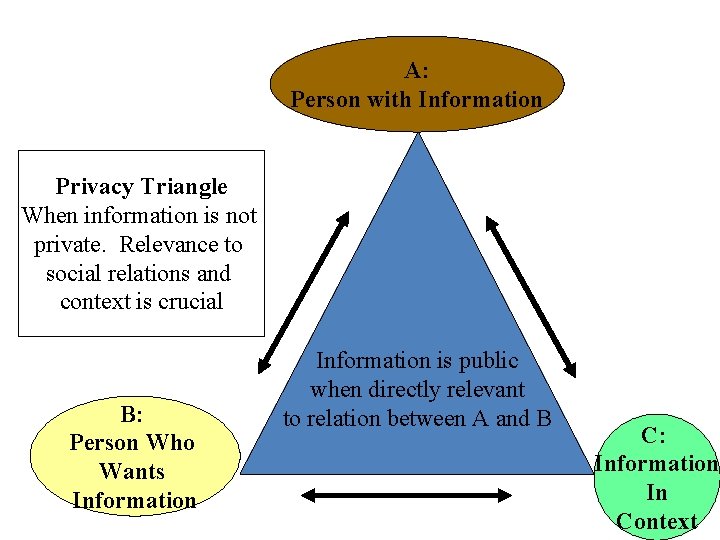
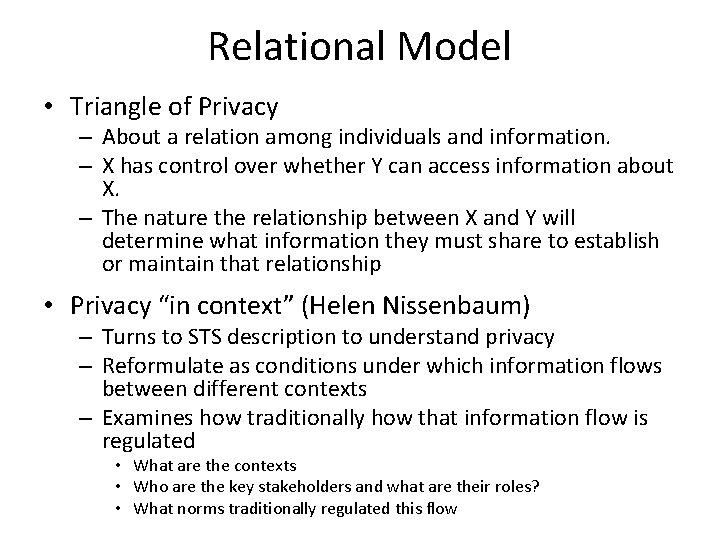
Privacy may not a right but still protected • Property Model – Privacy is a transferable product. Commercial entitles want to treat information you give them as a product with first sale rights. But they want to license that information to others • Relational Model (See Triangle of Privacy) – Privacy is about a relation among individuals and information. X has control over whether Y can access information about X. The nature the relationship between X and Y will determine what information they must share to establish or maintain that relationship – Reformulate privacy “in context” by identifying the context(s) in which information flows, the key stakeholders and their roles in this context(s), and the norms that have traditionally regulated this flow • Public Good – The consequential argument that privacy is a public good that should be protected – Privacy implies control over sharing information. Sharing information both builds trust and differentiates relationships.

A: Person with Information Privacy Triangle When information is not private. Relevance to social relations and context is crucial B: Person Who Wants Information is public when directly relevant to relation between A and B C: Information In Context

Relational Model • Triangle of Privacy – About a relation among individuals and information. – X has control over whether Y can access information about X. – The nature the relationship between X and Y will determine what information they must share to establish or maintain that relationship • Privacy “in context” (Helen Nissenbaum) – Turns to STS description to understand privacy – Reformulate as conditions under which information flows between different contexts – Examines how traditionally how that information flow is regulated • What are the contexts • Who are the key stakeholders and what are their roles? • What norms traditionally regulated this flow

Property With Emphasis on Intellectual Property, Its Legal Protections, and “Propertizing” Information

Labor Theory of Property • John Locke. Second Treatise on Civil Government. • Property is a natural extension of the body and the body is the paradigm of ownership – “ 1. A person has exclusive rights over, ‘owns, ’ his own body and its labor. – 2. Land, in its natural state is unowned; that is, no one individual can rightfully claim exclusive control of it. – 3. Therefore, when someone’s labor, which is owned, comes to be ‘mixed’ with land that is unowned, the exclusive rights over his or her labor are transferred to the land. That person comes to own the land. ” • I own that with which I mix my labor. Or I own that which I transform through my labor or work. (I take a stretch of unoccupied land, clear it off, and plant corn. I tend the corn and when it ripens I am entitled to harvest and eat the food. ) • Center argument for labor theory of property quoted from Des Jardins, (1993) Environmental Ethics: An Introduction to Environmental Philosophy 1 st Edition, Wadsworth, 36

Not everybody is happy with this • Rousseau: Discourse on the Origin of Inequality (Hackett edition, 60) – “The first person who, having enclosed a plot of land, took it into his head to say this is mine and found people simple enough to believe him was the true founder of civil society. ” • He goes on to say… – “What crimes, wars, murders, what miseries and horrors would the human race have been spared, had someone pulled up the stakes or filled in the ditch and cried out to his fellow men: ‘Do not listen to this imposter. You are lost if you forget that the fruits of the earth belong to all and the earth to on one!’” • Rousseau doesn’t like property—it is not natural to humankind. But, as he emphasizes in this and other things, we can’t go back, we have to go forward. • Or Proudhon: property = theft – What do you think this means?

Locke’s theory is criticized • Problematic in many ways (Huff). – If we assume property, it helps us to understand our intuition about it. – But this argument fails to establish property as a necessary natural right. • Consider Nozick’s argument: – When we mix our labor with X we could be said to own X because we own our labor – But isn’t this also compatible with the position that we dissipate our labor just as a drop of blue dye is dispersed, diluted, and lost when dropped in to the ocean?

Bundle “Theory” of Property • Des Jardins characterizes property, not as a single right, but as a “bundle of associated rights. ” These include the right to… – “possess, control, use, benefit from, dispose of, and exclude others” from one’s property – This gets a bit tricky when the property in question is intellectual property such as an idea or even music that has been digitalized on a CD. • The bundle is assembled according to the context in question. – We possess DVDs. But this ownership is limited. There are limits to how we can use them and how much we control them. (Can’t collect money for a public showing and can’t copy them. ) – Joseph Des Jardins. (1993) Environmental Ethics: An Introduction to Environmental Philosophy , 1 st edition. Wadsworth: 37

Consequentialist Theory of Property • Found in the U. S. Constitution • Negative Argument: not protecting property results in undesirable consequences. (No incentive to invent and innovate) • Positive Argument: protecting property results in desirable consequences (With incentives, talented individuals invent and innovate) • Constitution seeks balance by protecting property to maximize positive consequences and minimize bad consequences. • It protects intellectual property as… – Copyright – Patents – Trade Secrets

Social Role Theory of (Intellectual) Property • Lessig, Benkler, and “Copy Left” • Information wants to be shared. • It is in the nature of information that it is shared. • Control over sharing is essential as is provision for sharing • Sharing leads to an “intellectual commons. ”

Support from Jefferson • Thomas Jefferson – If nature has made any one thing less susceptible than all others of exclusive property, it is the action of the thinking power called an idea, which an individual may exclusively possess as long as he keeps it to himself; – but the moment it is divulged, it forces itself into the possession of every one, and the receiver cannot dispossess himself of it. • Ideas are non-rivalrous. – He who receives an idea from me, receives instruction himself without lessening mine; as he who lites his taper at mine, receives light without darkening me. • Ideas are non-exclusive – when she [nature] made them, like fire, expansible over all space, without lessening their density at any point, – and like the aire in which we breathe, move, and have our physical being, incapable of confinement or exclusive appropriation. Inventions then cannot, in nature, be a subject of property. (Quoted by Lessig in Code, 132)

Unpacking Jefferson’s Metaphor • Intellectual Property is non-rivalrous – My having an idea does not prevent you from having the same idea – Lighting your candle from my candle, extends the flame but does not diminish mine. • Intellectual property is non-excludable – Like the air it expands and cannot be contained in a limited, controlled region. • These two characteristics make intellectual property both essential to and useful for developing an intellectual commons – Intellectual commons = a repository of the collected ideas of our culture and civilization – we all have access to these ideas which we use as raw material to build new culture

Copyright, Patents, and Trade Secrets Next three slides are quoted from "Glossary" Online Ethics Center for Engineering 1/31/2006 6: 57: 46 PM National Academy of Engineering Accessed: Thursday, December 13, 2007 www. onlineethics. org/CMS/glossary. aspx”

Copyright • Legal right (usually of the author or composer or publisher of a work) to the exclusive publication, production, sale, or distribution of some work for a specified period. • What is protected by the copyright is the “expression, ” not the idea. • Notice that taking another’s idea without attribution may be plagiarism, so copyrights are not the equivalent of legal prohibition of plagiarism. – Most acts of plagiarism violate copyright but not all copyright violations are plagiarisms. Copyright is the broader category.

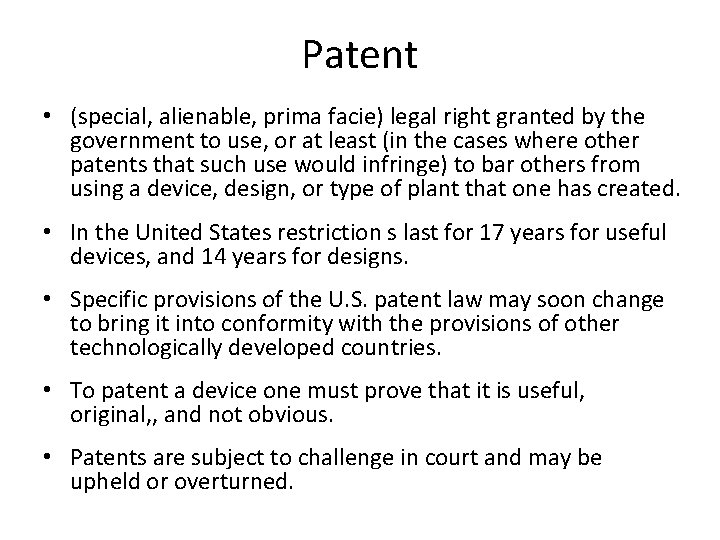
Patent • (special, alienable, prima facie) legal right granted by the government to use, or at least (in the cases where other patents that such use would infringe) to bar others from using a device, design, or type of plant that one has created. • In the United States restriction s last for 17 years for useful devices, and 14 years for designs. • Specific provisions of the U. S. patent law may soon change to bring it into conformity with the provisions of other technologically developed countries. • To patent a device one must prove that it is useful, original, , and not obvious. • Patents are subject to challenge in court and may be upheld or overturned.

Trade Secret • Device, method, or formula that gives one an advantage over the competition, and which must therefore be kept secret if it is to be of special value • It is legal to use reverse engineering to learn a competitor’s secret. • “Know how” concerning research procedures may function as something like a trade secret.

The Shrinking Intellectual Commons • There is a social value in having a common “space” where information is shared. • Unrestricted exercise of intellectual property rights may cause damage to the intellectual commons. – Extension of copyright terms prevents material from entering the commons. (Turns off the tap) • Commons = repository of ideas and source of creativity – We need it to continually “reinvent” our culture • Extension of metaphor of mixing. – As with Locke, I mix my thought and work with existing content. – This value added builds new culture and transforms the existing culture – But this source of creativity is stopped if we overly exercise the rights of copyright, patent, and trade secrets

The shrinking intellectual commons • 1998 was a watershed year for the intellectual commons with the commercialization of the net, DMCA, SBCTA, the NET act, were all passed. – Digital Millennium Copyright Act – Sonny Bono Copyright Term Extension Act • The NSF turned domain naming over to ICANN (Internet Corporation for Assigned Names and Numbers)

Exchanging Information on the Internet • What is needed, that is, is a machine-to-machine protocol for negotiating privacy protections. The user sets her preferences once—specifies how she would negotiate privacy and what she is willing to give up—and from that moment on, when she enters a site, the site and her machine negotiate. Only if the machines can agree will the site be able to obtain her personal data. • The kernel to this architecture is a project sponsored by the World Wide Web Consortium. Dubbed P 3 P, the project’s aim is to facilitate an architecture within which users can express their preferences and negotiate the use of data about them. • Quoted from Lessig, Code, 160 (Schwartz calls this “Cyber Jeeves”)

Can we develop an information market? • Convert privacy (as control over self-generated information) into property • Information Exchange Market – People who want information and are willing to pay for it – People who have information and are willing to sell it • All of this can be handled through code – P 3 P, W 3 C, XML – Cyber Jeeves • Paul M. Schwartz, “Beyond Lessig’s Code for Internet Privacy: Cyberspace Filters, Privacy-Control, and Fair Information Practices” Wisconsin Law Review 2000 Wis. L. Rev. 743

Why information markets may not work • Criticism of Privacy Market – Information asymmetries (Blinking Twelve) – Collective action (leaves individuals out) – Bounded rationality (leaves out important considerations) – Limits on exits (What if I don’t want to sell my information and have no exit? ) • Constitutive view of privacy (Advocated by Schwartz) – Not control view • Paul M. Schwartz, “Beyond Lessig’s Code for Internet Privacy: Cyberspace Filters, Privacy. Control, and Fair Information Practices” Wisconsin Law Review 2000 Wis. L. Rev. 743

Non-market Reasons for Privacy • Intrusion upon one´s seclusion • Public disclosure of private facts • Publicity that places one in a false light before the public (Defamation—Biomatrix) • Appropriation of one’s name or likeness without permission • Paul M. Schwartz, “Beyond Lessig’s Code for Internet Privacy: Cyberspace Filters, Privacy-Control, and Fair Information Practices” Wisconsin Law Review 2000 Wis. L. Rev. 743

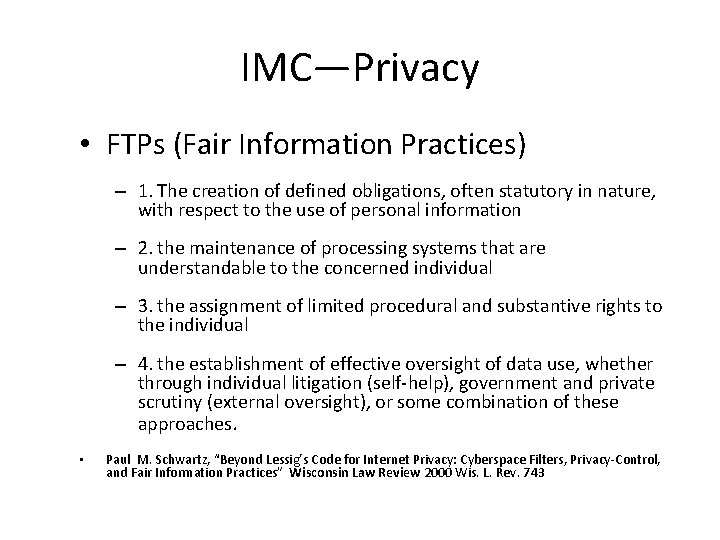
IMC—Privacy • FTPs (Fair Information Practices) – 1. The creation of defined obligations, often statutory in nature, with respect to the use of personal information – 2. the maintenance of processing systems that are understandable to the concerned individual – 3. the assignment of limited procedural and substantive rights to the individual – 4. the establishment of effective oversight of data use, whether through individual litigation (self-help), government and private scrutiny (external oversight), or some combination of these approaches. • Paul M. Schwartz, “Beyond Lessig’s Code for Internet Privacy: Cyberspace Filters, Privacy-Control, and Fair Information Practices” Wisconsin Law Review 2000 Wis. L. Rev. 743

Privacy and Property Issues Raised in Toysmart • Toysmart creditors wish to sell customer data base. – Does this violate their privacy? • Toysmart customers shared PII only under strict privacy promises. – Do Toysmart promises pass over to the creditors after bankruptcy? • Is PII convertible into property? • If so, who owns it? – The individual who generates it? – The individual who adds value to it? (The one who transforms it into something useful and important. )

Pivots to the Present Other Privacy and Property Cases

Recent Decision Concerning Facebook • http: //www. npr. org/templates/story. php? story. Id=133575667 – Associated Press story accessed through National Public Radio – See also Steve Greenhouse, “Company Accused of Firing Over Facebook Post”, New York Times, February 8, 2010 http: //www. nytimes. com/2010/11/09/business/09 facebook. html? _r=1&scp =2&sq=Facebook+Connecticut+ambulance+company&st=nyt • Employee fired for criticizing her boss on Facebook • National Labor Relations Board successfully sues Connecticut ambulance company – Workers can discuss with co-workers issues such as wages, hours, and working conditions – Compared to a conversation next to the water cooler – Is it a “concerted protected activity” (See Greenhouse article)

Related Privacy Cases • Wire tapping phone booth used by mob figure • Using infra-red detectors to determine if suspect is growing marijuana inside house • Major corporation secretly installs cameras in bathrooms to find who is damaging them • Facebook: Supervisor finds negative comments about him posted by employee in Facebook. Fires employee • Carnivore: FBI tries to force OSPs to install packet filter to identify terrorists who are using Internet

Related Property Cases • Disney works to extend copyright term limits yet makes use of fairy tales that are part of public domain • Are aggressive RIAA measures to stop pirating CDs and DVDs justified? – Recently, choose universities, send students letter telling to confess or face legal action • Lawrence Lessig discusses Eric Eldred case in Free Culture – Eldred wanted to develop online library to post classical authors and works – But Sony Bono Copyright Term Extension Act blocked this in the case of poems by Robert Frost as well as others – Sued unsuccessfully to get permission to include these works in library
 Dr william frey
Dr william frey Dr william frey
Dr william frey Apush college board key concepts
Apush college board key concepts Canciones belgas más famosas
Canciones belgas más famosas Leeftijd jimmy frey
Leeftijd jimmy frey Frey syndrome symptoms
Frey syndrome symptoms Airbnb mehrwertsteuer
Airbnb mehrwertsteuer Klaus dieter frey
Klaus dieter frey Frey’s syndrome
Frey’s syndrome Theory of bureaucratic caring
Theory of bureaucratic caring Magalie frey
Magalie frey Regina frey
Regina frey Coeficiente de inbreeding
Coeficiente de inbreeding Ariane frey
Ariane frey Iris frey attac
Iris frey attac Oliver kohl-frey
Oliver kohl-frey Frey gebäudereinigung
Frey gebäudereinigung Samina saleem
Samina saleem Sindrome de frey
Sindrome de frey Hans dieter frey
Hans dieter frey Frey gebäudereinigung
Frey gebäudereinigung David frey 12 step sales letter
David frey 12 step sales letter Alan frey
Alan frey Example of business model canvas
Example of business model canvas Key partners
Key partners William jewell college
William jewell college William zinsser college pressures
William zinsser college pressures Russian formalism theory
Russian formalism theory Key concepts examples
Key concepts examples Period 6 key concepts
Period 6 key concepts Period 5 key concepts apush
Period 5 key concepts apush Apush period 3 review
Apush period 3 review Apush key concepts period 2
Apush key concepts period 2 Key concepts of quantitative research
Key concepts of quantitative research Feminist therapy
Feminist therapy Reviewing key concepts reproductive barriers
Reviewing key concepts reproductive barriers