Stream Ciphers CSCI 284 162 Spring 2009 GWU






- Slides: 13

Stream Ciphers CSCI 284 -162 Spring 2009 GWU CS 284 -162/Spring 09/GWU/Vora/ Stream Ciphers

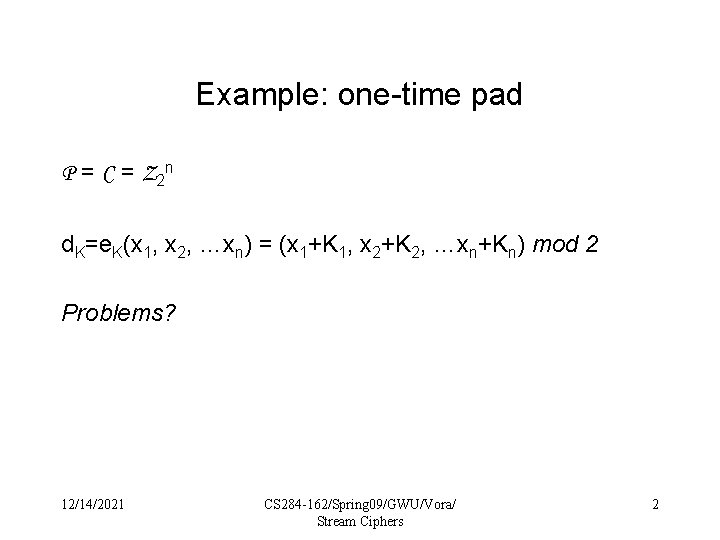
Example: one-time pad P = C = Z 2 n d. K=e. K(x 1, x 2, …xn) = (x 1+K 1, x 2+K 2, …xn+Kn) mod 2 Problems? 12/14/2021 CS 284 -162/Spring 09/GWU/Vora/ Stream Ciphers 2

One-time pad is best • But key too long to be practical • Can we use a pseudo-random key then, which would be generated from a short truly random string? 12/14/2021 CS 284 -162/Spring 09/GWU/Vora/ Stream Ciphers 3

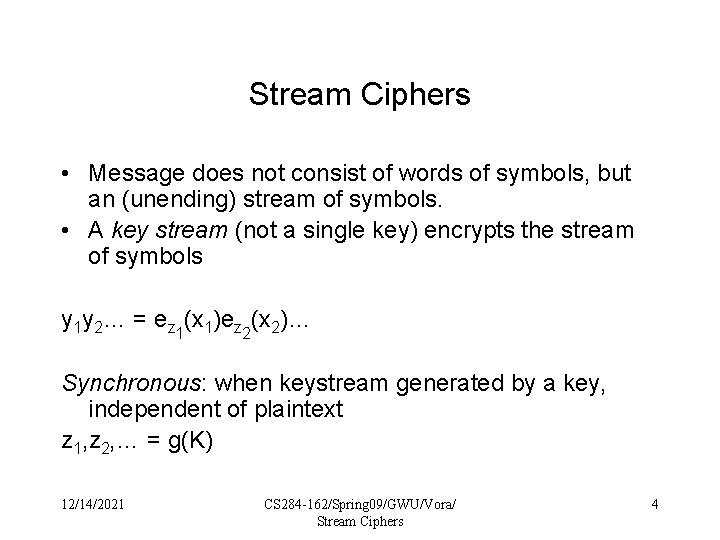
Stream Ciphers • Message does not consist of words of symbols, but an (unending) stream of symbols. • A key stream (not a single key) encrypts the stream of symbols y 1 y 2… = ez 1(x 1)ez 2(x 2)… Synchronous: when keystream generated by a key, independent of plaintext z 1, z 2, … = g(K) 12/14/2021 CS 284 -162/Spring 09/GWU/Vora/ Stream Ciphers 4

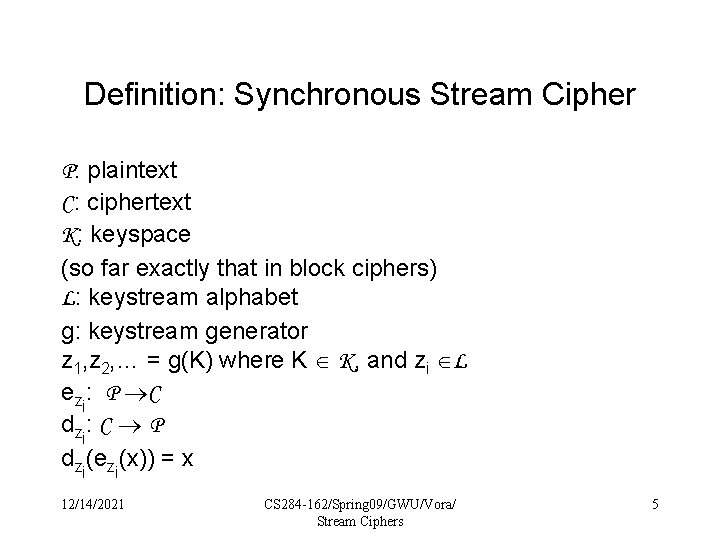
Definition: Synchronous Stream Cipher P: plaintext C: ciphertext K: keyspace (so far exactly that in block ciphers) L: keystream alphabet g: keystream generator z 1, z 2, … = g(K) where K K, and zi L ezi: P C d zi : C P dzi(ezi(x)) = x 12/14/2021 CS 284 -162/Spring 09/GWU/Vora/ Stream Ciphers 5

Examples from ciphers we have already seen? • Shift? Affine? Substitution? Vigenère? Permutation? 12/14/2021 CS 284 -162/Spring 09/GWU/Vora/ Stream Ciphers 6

Periodic Stream Cipher? • Security? • Binary addition as XOR, easy to implement in hardware. • Encryption and decryption are the same operations: addition of the bit 12/14/2021 CS 284 -162/Spring 09/GWU/Vora/ Stream Ciphers 7

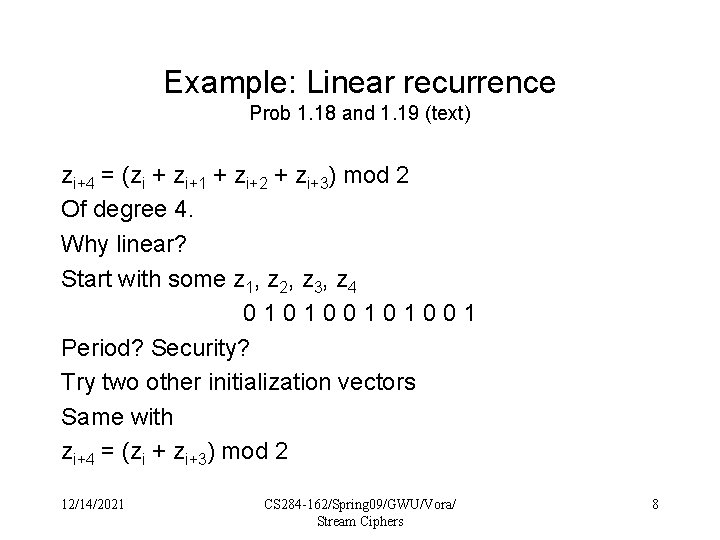
Example: Linear recurrence Prob 1. 18 and 1. 19 (text) zi+4 = (zi + zi+1 + zi+2 + zi+3) mod 2 Of degree 4. Why linear? Start with some z 1, z 2, z 3, z 4 0101001 Period? Security? Try two other initialization vectors Same with zi+4 = (zi + zi+3) mod 2 12/14/2021 CS 284 -162/Spring 09/GWU/Vora/ Stream Ciphers 8

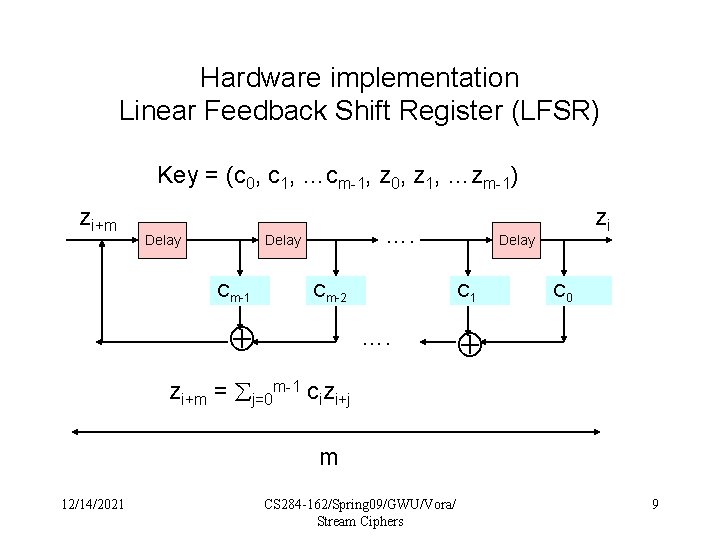
Hardware implementation Linear Feedback Shift Register (LFSR) Key = (c 0, c 1, …cm-1, z 0, z 1, …zm-1) zi+m Delay …. Delay Cm-1 Cm-2 Delay C 1 …. zi C 0 zi+m = j=0 m-1 cizi+j m 12/14/2021 CS 284 -162/Spring 09/GWU/Vora/ Stream Ciphers 9

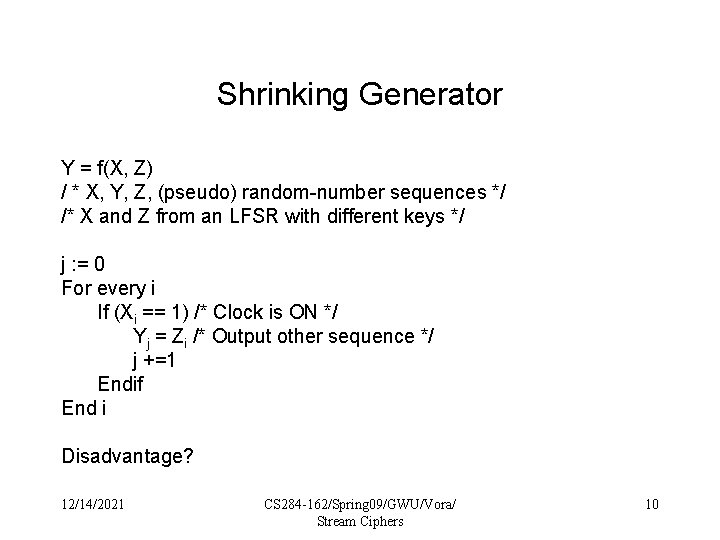
Shrinking Generator Y = f(X, Z) / * X, Y, Z, (pseudo) random-number sequences */ /* X and Z from an LFSR with different keys */ j : = 0 For every i If (Xi == 1) /* Clock is ON */ Yj = Zi /* Output other sequence */ j +=1 Endif End i Disadvantage? 12/14/2021 CS 284 -162/Spring 09/GWU/Vora/ Stream Ciphers 10

Shrinking Generator: Examples 12/14/2021 CS 284 -162/Spring 09/GWU/Vora/ Stream Ciphers 11

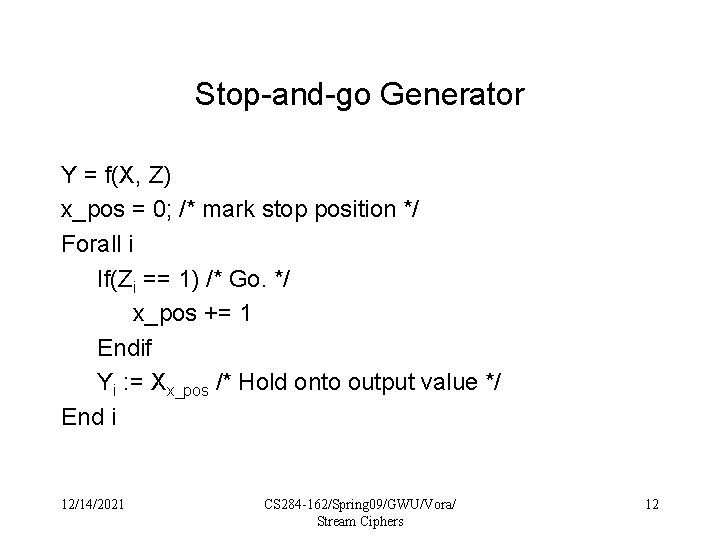
Stop-and-go Generator Y = f(X, Z) x_pos = 0; /* mark stop position */ Forall i If(Zi == 1) /* Go. */ x_pos += 1 Endif Yi : = Xx_pos /* Hold onto output value */ End i 12/14/2021 CS 284 -162/Spring 09/GWU/Vora/ Stream Ciphers 12

Examples 12/14/2021 CS 284 -162/Spring 09/GWU/Vora/ Stream Ciphers 13