Security of Wireless Sensor Networks Security Risks in





- Slides: 12

Security of Wireless Sensor Networks

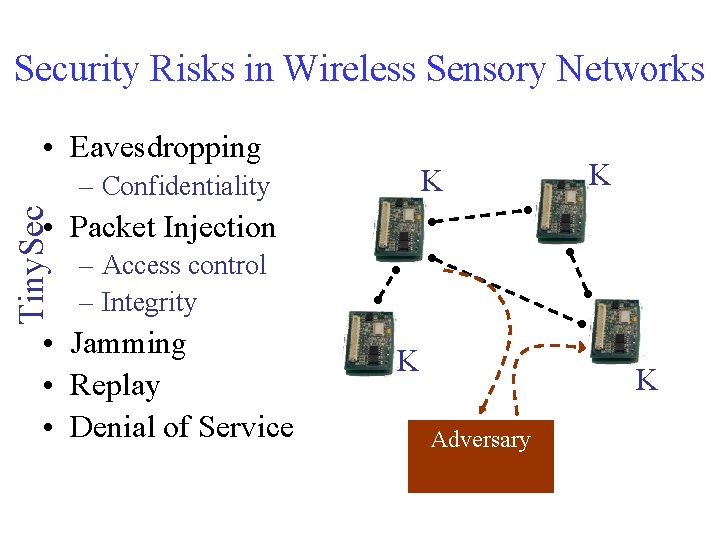
Security Risks in Wireless Sensory Networks • Eavesdropping K Tiny. Sec – Confidentiality K • Packet Injection – Access control – Integrity • Jamming • Replay • Denial of Service K K Adversary

Security Goals • Access Control – Link layer protocol should prevent unauthorized parties from participating in the network • Message Integrity – Receiver should be able to detect the malicious modification of transmitted messages • Confidentiality – Keep transmitted messages secret from unauthorized parties • Replay Protection – Attacker can replay a legitimate message at some later time

Security Goals • Performance – Using cryptography will incur increased overhead in extra demands on the processor and RAM – Increased message length decreases the throughput and increased latency. It will also increase the power consumption • Ease of use – Higher level security protocols will rely on the link -layer security as a primitive – Transparent to applications

Security Primitives • Message Authentication Codes (MACs) – A common solution to achieve authenticity and integrity – MAC can be viewed as “Cryptographically secure checksum” • Generated with a key shared by both sender and receiver • Difficult to forge without the key • Initialization Vectors (IV) – To achieve semantic security – An input to the algorithm to add variation to the encryption process

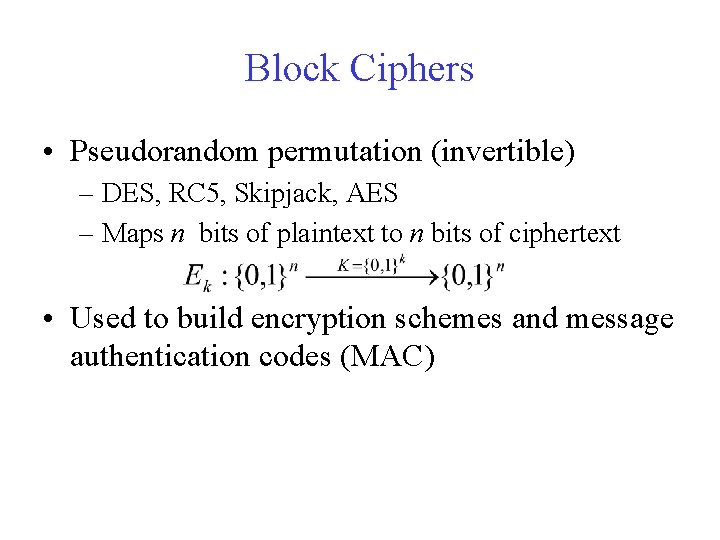
Block Ciphers • Pseudorandom permutation (invertible) – DES, RC 5, Skipjack, AES – Maps n bits of plaintext to n bits of ciphertext • Used to build encryption schemes and message authentication codes (MAC)

Mode of Operation • Block ciphers operate on blocks of plaintext and ciphertext – For example 64 bits – A cryptographic mode combines the basic ciphers, some sort of feedback, and some simple operations • Example Block Cipher modes – ECB, CBC, CFB, CTR, OFB

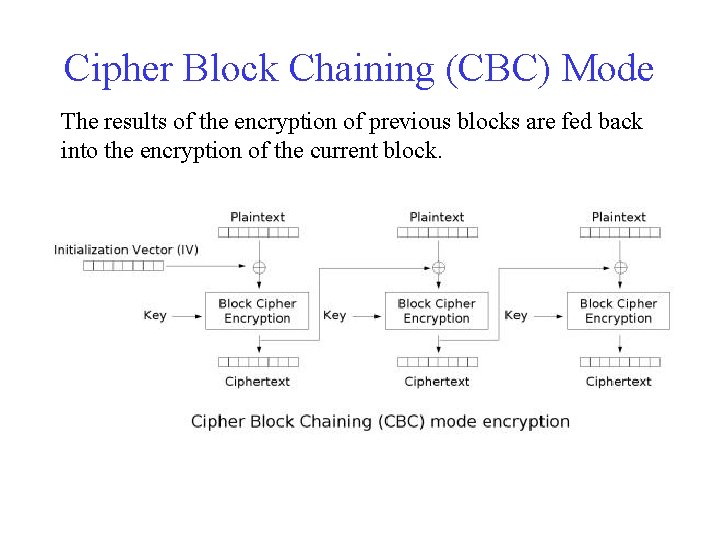
Cipher Block Chaining (CBC) Mode The results of the encryption of previous blocks are fed back into the encryption of the current block.

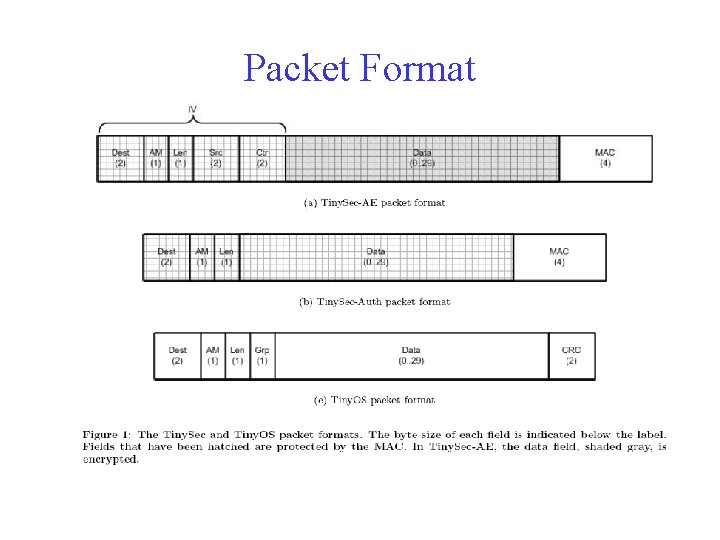
Two Security Options • Authenticated Encryption (Tiny. Sec-AE) – Data payload encrypted – Packets authenticated with a MAC • MAC computed over the encrypted data and the packet header • Authentication Only (Tiny. Sec-Auth) – Data payload is not encrypted

Encryption • Tiny. Sec IV format – Tradeoff between long and short IV – How long is long enough? • The structure of IV is dst||AM||l||src||ctr • Encryption schemes – Stream cipher has a devastating failure mode: if the same IV is ever used, it is often possible to recover both plaintext – Block cipher is preferred • It is as robust as possible in the presence of repeated IV • MAC algorithms use a block cipher

Packet Format

Keying Mechanisms • Determines how cryptographic keys are distributed and shared throughout the network • Mechanisms – A single network-wide Tiny. Sec key among the authorized nodes – Nodes share a key for communication only if they need to communicate with each other (pair-wise) – Neighboring nodes to share a Tiny. Sec key