Secure Shell SSH into Amazon EC 2 Instance








- Slides: 14

Secure Shell (SSH) into Amazon EC 2 Instance (Mac) README BEFORE GETTING STARTED Here's some important information to know before starting this hands-on activity. Bit. Beat is a new startup that is planning to take the record industry and the world by storm with its new product Bit. Banger, a web-based music mixer app. As a new member of the Bit. Beat infrastructure team, you will need a variety of skills to assist in the growth of the startup. As the startup grows, they will be creating a larger web presence. They originally launched a static web page using Amazon Simple Storage Service (Amazon S 3). They want to launch a dynamic website that will provide customers with product information, an ecommerce shopping site, and a blog. This means that you will need to launch and configure a webserver. Then, you will need to connect to the Amazon Elastic Compute Cloud (Amazon EC 2) instances that you launched and transfer files between your local computer and your instance. Activity time: 60 minutes Requirements: You must have an AWS Educate account. Getting help: If you experience any issues as you complete this activity, please ask your instructor for assistance. Academic Gateway to the Hearts and Minds of the Next Generation of IT Professionals © 2020, Amazon Web Services, Inc. or its affiliates. All rights reserved.

Secure Shell (SSH) into Amazon EC 2 Instance (Mac) Task overview In this hands-on activity, you are going to build a cloud-based webserver using a Linux machine image on an Amazon EC 2 instance. A key pair, consisting of a private key and a public key, is a set of security credentials that you use to prove your identity when connecting to an instance. Amazon EC 2 stores the public key, and you store the private key. You use the private key, instead of a password, to securely access your instances. Anyone who possesses your private key can connect to your instances, so it's important that you store your private keys in a secure place. Task objectives: Build a practice cloud-based webserver Create a key pair Secure Shell (SSH) into the Amazon EC 2 instance Modify an AWS security group Troubleshoot issues Learning outcomes Once you’ve completed this activity you should be able to: Build an Amazon EC 2 cloud webserver Create an Amazon EC 2 key pair Know how to Secure Shell (SSH) into the Amazon EC 2 instance using terminal Let’s get started! Academic Gateway to the Hearts and Minds of the Next Generation of IT Professionals © 2020, Amazon Web Services, Inc. or its affiliates. All rights reserved.

Secure Shell (SSH) into Amazon EC 2 Instance (Mac) Launch an Amazon EC 2 instance Follow these steps to launch an Amazon EC 2 instance: 1. In the AWS Management Console find and select the Amazon EC 2 Dashboard. 2. From the Amazon EC 2 Dashboard, click Launch Instances. 3. Notice the variety of AMIs located on the AMI page. These are different templates for different types of machines. Select the Amazon Linux 2 AMI (HVM). 4. Notice the variety of instance types available. Select the t 2. micro instance. 5. Select Next: Configure Instance Details. 6. Accept the default settings for the Step 3: Configure Instance Details page and scroll down to the bottom to see the Advanced Details section. a. Expand the Advanced Details. A field for User data will appear. b. Copy the following commands and paste them into the User data field: #!/bin/bash yum - y i n s t a l l h t t p d systemctl enable h t t p d systemctl s t a r t h t t p d echo '<html><h 1>Hey Guru, You have mad Cloud s k i l l s ! </h 1></html>' > /var/www/html/index. html Here’s what this bash script does; see if you can identify which actions each line of script executes: Installs, enables, and starts the Apache HTTP Server Creates an index. html page with a message Important info This is “bootstrapping” or providing code that runs when a computer starts up. Make sure you don’t insert additional characters or spaces at the end of you code. Academic Gateway to the Hearts and Minds of the Next Generation of IT Professionals © 2020, Amazon Web Services, Inc. or its affiliates. All rights reserved.

Secure Shell (SSH) into Amazon EC 2 Instance (Mac) Let’s add some storage to our instance, tags and security groups: 1. Click Next: Add Storage You will not need another Amazon Elastic Block Store volume. 2. Click Next: Add Tags 3. Click Add tag then configure: Key: Name Value: SSH Practice Server Key: Department Value: Development 4. Click Next: Configure Security Group 5. Configure a new security group as follows: Security Group name: SSH Practice SG Description: This security group is for SSH practice. By default, the Type SSH with Port 22 has been added Click Review and Launch 6. Review the details, scroll down, and click Launch. 7. The key pair modal displays. In the dropdown, select Create a new key pair, name your Key Pair my_ssh_key, then click Download Key Pair and save the it to your desktop. Download your key to your desktop. The SSH instructions provided later in this activity assume your key pair has been downloaded to your desktop. 8. After you have downloaded your key pair to your desktop, click Launch Instances. 9. On the Launch Status page, scroll to the bottom and click View Instances. Wait for your new Amazon EC 2 Instance State to display as. Academic Gateway to the Hearts and Minds of the Next Generation of IT Professionals © 2020, Amazon Web Services, Inc. or its affiliates. All rights reserved.

Secure Shell (SSH) into Amazon EC 2 Instance (Mac) Now that your Amazon EC 2 instance is running: 1. Select your SSH Practice Server Instance and Copy the IPV 4 Public IP address located near the bottom of your screen to your clipboard. 2. Paste the IPv 4 Public IP address into a new browser window and observe the results. Did your webpage load properly? If not, what might be the reason why? Important info AWS Security Groups (SGs) are associated with Amazon EC 2 instances and provide security at the protocol and port access level. A security group works very much the same way as a firewall, as it contains a set of rules that filter traffic coming into and out of an Amazon EC 2 instance. By default, all non-local traffic is blocked. Example: Webservers typically allow public traffic access on port 80 (HTTP) and/or port 443 (HTTPS). Troubleshooting Amazon EC 2 You successfully launched your SSH practice server, but when you tried to access the Public IP address, there was an error: This site cannot be reached. You won’t be able to access the application if you can’t reach the webserver. You need to figure out how to fix this issue. Review the previous steps and read about security groups. Academic Gateway to the Hearts and Minds of the Next Generation of IT Professionals © 2020, Amazon Web Services, Inc. or its affiliates. All rights reserved.

Secure Shell (SSH) into Amazon EC 2 Instance (Mac) Are you allowing normal web traffic (Port 80) to access your webserver? Did you configure this properly? Update your security group Keep the web browser open and go back to the Amazon EC 2 Management Console tab. In the left navigation pane, under Network and Security, click Security Groups. Select the SSH Practice SG or the security group you created when launching your Amazon EC 2 instance. Expand the Security Group info pane at the bottom of the screen and click the Inbound rules tab. Notice the Security Group currently has no HTTP rules. Important info When you add or remove a security group rule, these changes are automatically applied to all instances to which you have assigned the security group. These updates/changes are immediate. Create a rule in the Inbound tab. 1. Click Edit inbound rules 2. Click Add Rule and then configure the following settings: Type: HTTP Source: Anywhere Click Save rules The new Inbound HTTP rule will create an entry for both IPV 4 IP address (0. 0/0) as well as IPV 6 IP address (: : /0). Academic Gateway to the Hearts and Minds of the Next Generation of IT Professionals © 2020, Amazon Web Services, Inc. or its affiliates. All rights reserved.

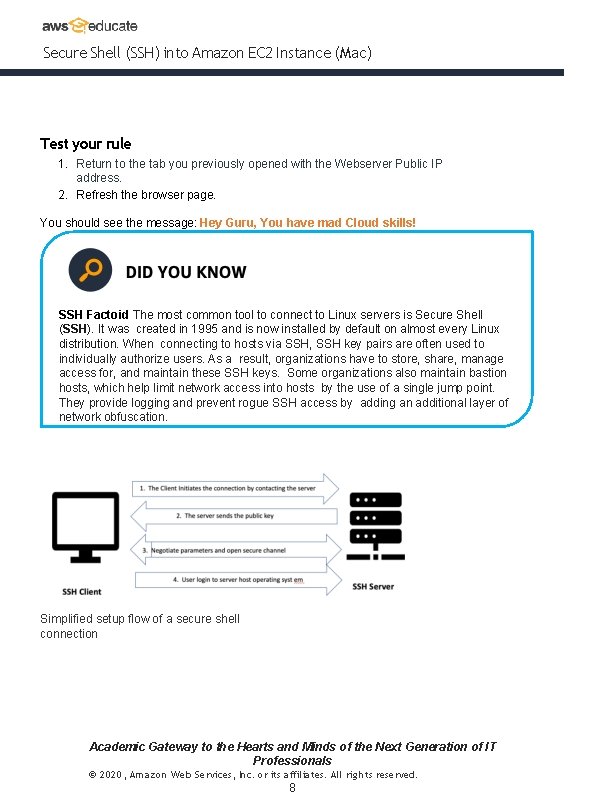
Secure Shell (SSH) into Amazon EC 2 Instance (Mac) Test your rule 1. Return to the tab you previously opened with the Webserver Public IP address. 2. Refresh the browser page. You should see the message: Hey Guru, You have mad Cloud skills! SSH Factoid The most common tool to connect to Linux servers is Secure Shell (SSH). It was created in 1995 and is now installed by default on almost every Linux distribution. When connecting to hosts via SSH, SSH key pairs are often used to individually authorize users. As a result, organizations have to store, share, manage access for, and maintain these SSH keys. Some organizations also maintain bastion hosts, which help limit network access into hosts by the use of a single jump point. They provide logging and prevent rogue SSH access by adding an additional layer of network obfuscation. Simplified setup flow of a secure shell connection Academic Gateway to the Hearts and Minds of the Next Generation of IT Professionals © 2020, Amazon Web Services, Inc. or its affiliates. All rights reserved.

Secure Shell (SSH) into Amazon EC 2 Instance (Mac) SSH enables two computers to establish a secure and direct connection within a potentially unsecure network, such as the internet. This is necessary so that third parties cannot access the data stream, which would result in sensitive data falling into the wrong hands. SSH encrypts the connection between two computers and enables a second one to be operated from one computer. SSH not only provides an encrypted connection but also makes sure that connections are only established between the designated computers and that the corresponding data cannot be manipulated on its way to the recipient. SSH has many different areas of application including: Managing servers that cannot be accessed locally Securing transmission of files Securing creation of backups Connecting between two computers with end-to-end encryption Remote maintenance from other computers Connect to the webserver using SSH When you launch an instance, created a key pair. When your instance boots for the first time, the public key content is copied to the Linux instance in an entry within ~/. ssh/authorized_keys. When you connect to your Linux instance using SSH, you must specify the private key that corresponds to the public key content to log in. Now, let’s make sure that you can connect to the webserver using SSH from you Mac. 1. Navigate to the Amazon EC 2 dashboard and click on Running Instances. 2. Click the checkbox to select the SSH Practice Server. 3. Locate the Public DNS (IPV 4) name. Hover offer the name and select Copy to Clipboard. Tip: When you select your instance, you can click the Connect button at the top of the screen to view the SSH information for your instance. Academic Gateway to the Hearts and Minds of the Next Generation of IT Professionals © 2020, Amazon Web Services, Inc. or its affiliates. All rights reserved.

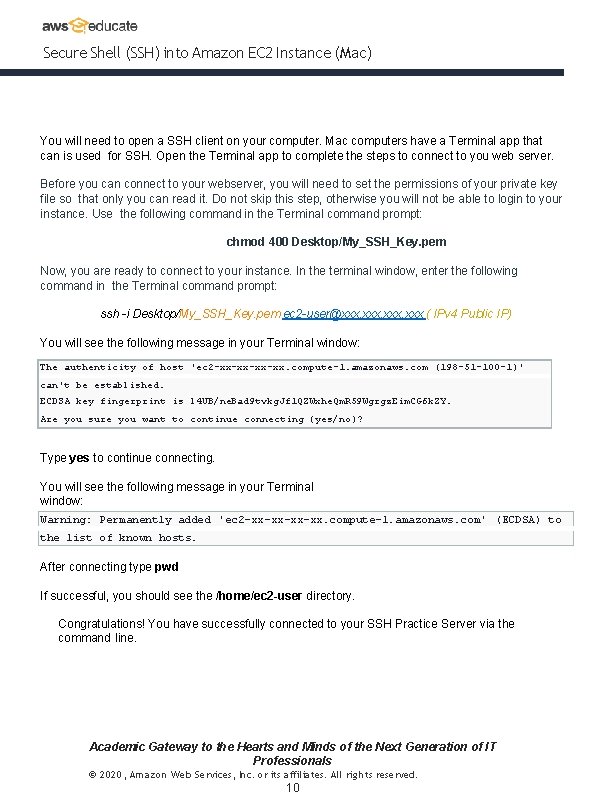
Secure Shell (SSH) into Amazon EC 2 Instance (Mac) You will need to open a SSH client on your computer. Mac computers have a Terminal app that can is used for SSH. Open the Terminal app to complete the steps to connect to you web server. Before you can connect to your webserver, you will need to set the permissions of your private key file so that only you can read it. Do not skip this step, otherwise you will not be able to login to your instance. Use the following command in the Terminal command prompt: chmod 400 Desktop/My_SSH_Key. pem Now, you are ready to connect to your instance. In the terminal window, enter the following command in the Terminal command prompt: ssh -i Desktop/My_SSH_Key. pem ec 2 -user@xxx. xxx ( IPv 4 Public IP) You will see the following message in your Terminal window: The authenticity of host 'ec 2 -xx-xx. compute-1. amazonaws. com (198 -51 -100 -1)' can't be established. ECDSA key fingerprint is l 4 UB/ne. Bad 9 tvkg. Jf 1 QZWxhe. Qm. R 59 Wgrgz. Eim. CG 6 k. ZY. Are you sure you want to continue connecting (yes/no)? Type yes to continue connecting. You will see the following message in your Terminal window: Warning: Permanently added 'ec 2 -xx-xx. compute-1. amazonaws. com' (ECDSA) to the list of known hosts. After connecting type pwd If successful, you should see the /home/ec 2 -user directory. Congratulations! You have successfully connected to your SSH Practice Server via the command line. Academic Gateway to the Hearts and Minds of the Next Generation of IT Professionals © 2020, Amazon Web Services, Inc. or its affiliates. All rights reserved.

Secure Shell (SSH) into Amazon EC 2 Instance (Mac) Fun Fact You’ve launched your Amazon EC 2 instance using a script inserted into your User data field in the Advanced Details section. You can retrieve and view the user data information from within a running instance using the following URL: http: //169. 254/latest/user-data. To retrieve user data from within a running instance, type curl http: //169. 254/latest/user-data after you’ve used SSH to gain access to your instance. (Hint: If you have to elevate your privileges, don’t forget the sudo su command). Cost effectiveness Stop your Amazon EC 2 instance You used a t 2. micro Instance but what are some other ways that you can save on cost for the startup? Cloud computing services use a utility-based pricing model. Basically, if you leave your light on, there is an associated cost that will show up in your electricity bill. If the product team only works on Mondays through Fridays between the hours of 6: 00 AM and 6: 00 PM, how can you minimize cost by turning off the SSH Practice Server when you aren’t using it? 1. In the Amazon EC 2 Management Console, click Instances in the left navigation. 2. Select your running instance and then at the top of the screen click Actions > Instance State > Stop. 3. Your instance will do a normal shutdown and then will stop running. You may want to refresh your screen. You can do that by clicking on the two circular arrows (refresh) in the top right portion of your screen: . Resize your instance 1. In the Actions menu, select Instance Settings > Change Instance Type 2. Then configure the following: 1. Instance Type: t 2. small 2. Click Apply Academic Gateway to the Hearts and Minds of the Next Generation of IT Professionals © 2020, Amazon Web Services, Inc. or its affiliates. All rights reserved.

Secure Shell (SSH) into Amazon EC 2 Instance (Mac) Start the resized instance 1. 2. 3. 4. In the left navigation pain, click Instances. In the Actions menu, select Instance State > Start. Click Yes, Start in the modal. You can click the refresh arrows if preferred. Copy and paste the new Amazon EC 2 Public IP address from the Amazon EC 2 Details. 5. Open up a browser tab and enter the address. Can you SSH into your new t 2: small instance using the same key pair and SSH commands you used before? Hints: You don’t need to repeat the chmod 400 Test Desktop/My_SSH_Key. pem command; remember to use the new t 2: small IPv 4 Public IP address. 1. 2. [your text here] Academic Gateway to the Hearts and Minds of the Next Generation of IT Professionals © 2020, Amazon Web Services, Inc. or its affiliates. All rights reserved.

Secure Shell (SSH) into Amazon EC 2 Instance (Mac) Great job! Let’s review You have completed the activity by successfully launching and configuring an Amazon EC 2 and connecting to the instance via SSH in support of your remote employee. Looking forward, think about how you might do this on a PC using Pu. TTY or on a Windows server using RDP. In this activity you: Launched an Amazon EC 2 Instance Created User-Data (bootstrapping) instructions for your Amazon EC 2 Instance Configured security group settings Created a key pair Connected to your instance via SSH Resized an existing Amazon EC 2 instance Demonstrated ways to minimize cost Test your knowledge A key pair consists of two keys. What are these two keys called? Which key does the Amazon EC 2 instance store? You use the instead of a password, to securely access your instances. What is an AWS tag? What are tags used for? A security group works like a firewall because it contains a set of rules that filter traffic coming into and out of an Amazon EC 2 instance. By default, all non-local traffic is. (Choose: Allowed, blocked, or neither) From which URL, can you retrieve and view the user data information from within a running instance? When you add or remove a security group rule, how long does it take for the changes to take place? When you make a change to a security group rule, does the change affect only the instance you’re currently working on or other instances, too? Explain. Academic Gateway to the Hearts and Minds of the Next Generation of IT Professionals © 2020, Amazon Web Services, Inc. or its affiliates. All rights reserved.

Secure Shell (SSH) into Amazon EC 2 Instance (Mac) Bonus activity Let’s explore a few more things before you practice good cloud hygiene and clean up your environment. Do not change any of your configurations or modify your current settings. 1. In the Amazon EC 2 Management Console, click Instances in the left navigation and highlight your SSH Practice Server. 2. Click the Actions button and review all the options that are available. 3. Under each of the options where there is an additional drop-down options menu, take a moment to review the additional options that are available. Take note how you can do many things under the Instance Settings options. Clean up your environment The development team has fully deployed and tested their software in a development setting. They asked you to terminate the testing machine you created. 1. Find and select your SSH Practice Server. 2. Select Actions>Instance State>Terminate. 3. Delete your SSH Practice SG security group by navigating to the Security Groups option in the left- hand navigation within the Network and Security category. Simply check there is a check mark in the box next to your Security group name > Actions > Delete security group. 4. You may also want to delete your My_SSH_Key by navigating to the key pairs option in the left-hand navigation within the Network and Security category. Make sure there is a checkmark in the box next to your Key pair name > Click the actions dropdown box > Click delete > Confirm deletion by typing Delete in the field > Click delete. Academic Gateway to the Hearts and Minds of the Next Generation of IT Professionals © 2020, Amazon Web Services, Inc. or its affiliates. All rights reserved.

Secure Shell (SSH) into Amazon EC 2 Instance (Mac) Resources https: //docs. aws. amazon. com/AWSEC 2/latest/User. Guide/ec 2 -key-pairs. html https: //docs. aws. amazon. com/AWSEC 2/latest/User. Guide/Accessing. Instances. Lin ux. html https: //docs. aws. amazon. com/AWSEC 2/latest/User. Guide/connectionprereqs. html https: //www. ssh. com/ssh/ https: //aws. amazon. com/blogs/compute/new-using-amazon-ec 2 -instance-connect-for-ssh-accessto-your- ec 2 -instances/ Academic Gateway to the Hearts and Minds of the Next Generation of IT Professionals © 2020, Amazon Web Services, Inc. or its affiliates. All rights reserved.