Revealing Stealth Malware UMD CMSC 389 M Xeno




- Slides: 11

Revealing Stealth Malware UMD CMSC 389 M Xeno Kovah – Jan. 2013 xkovah at gmail Subject line starting with "UMD: " 1

All materials is licensed under a Creative Commons “Share Alike” license. • http: //creativecommons. org/licenses/by-sa/3. 0/ 2

Outline • Patch. Guard • Review 3

"Patch. Guard" aka Kernel Patch Protection • Meant to stop 3 rd party software from patching the kernel • Has gone through a number of iterations, but can still be defeated – http: //fyyre. ivory-tower. de/ • Specifically disable_pg_ds_v 3. rar 4

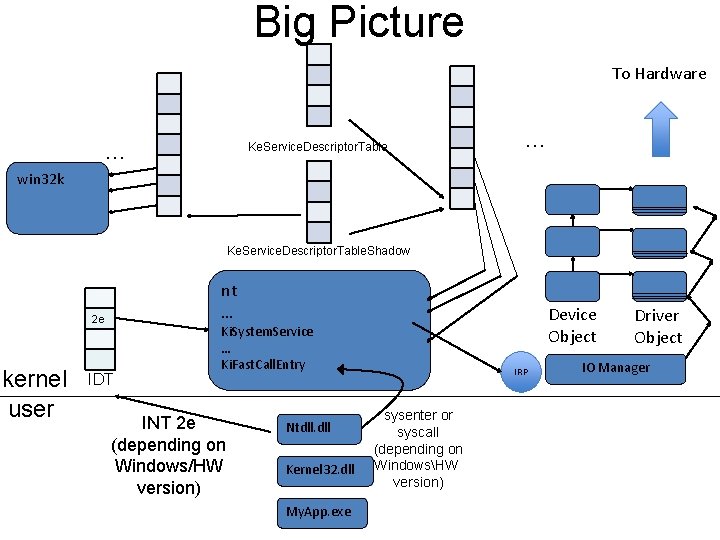
Big Picture To Hardware … Ke. Service. Descriptor. Table … win 32 k Ke. Service. Descriptor. Table. Shadow nt … 2 e kernel user IDT Device Object Ki. System. Service … Ki. Fast. Call. Entry INT 2 e (depending on Windows/HW version) Ntdll. dll Kernel 32. dll My. App. exe IRP sysenter or syscall (depending on WindowsHW version) Driver Object IO Manager

Tool Time 6

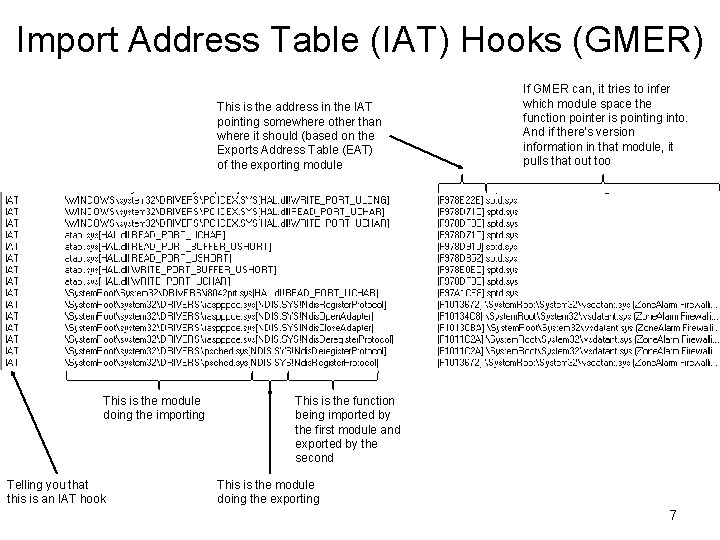
Import Address Table (IAT) Hooks (GMER) This is the address in the IAT pointing somewhere other than where it should (based on the Exports Address Table (EAT) of the exporting module This is the module doing the importing Telling you that this is an IAT hook If GMER can, it tries to infer which module space the function pointer is pointing into. And if there's version information in that module, it pulls that out too This is the function being imported by the first module and exported by the second This is the module doing the exporting 7

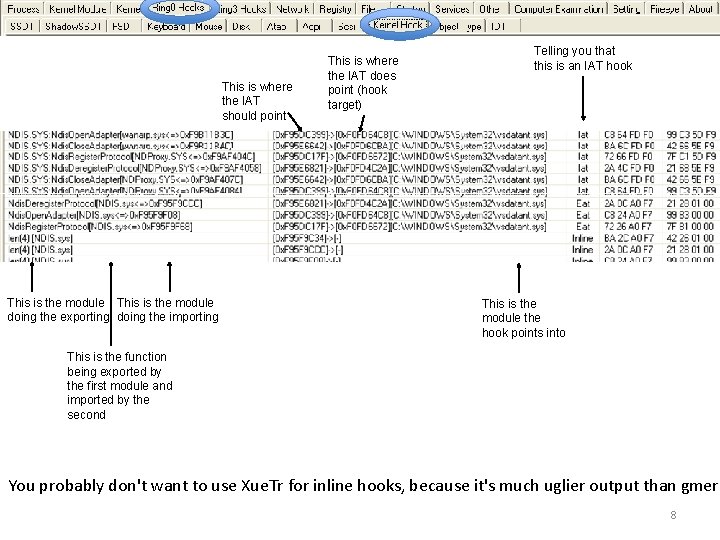
This is where the IAT should point This is the module doing the exporting doing the importing This is where the IAT does point (hook target) Telling you that this is an IAT hook This is the module the hook points into This is the function being exported by the first module and imported by the second You probably don't want to use Xue. Tr for inline hooks, because it's much uglier output than gmer 8

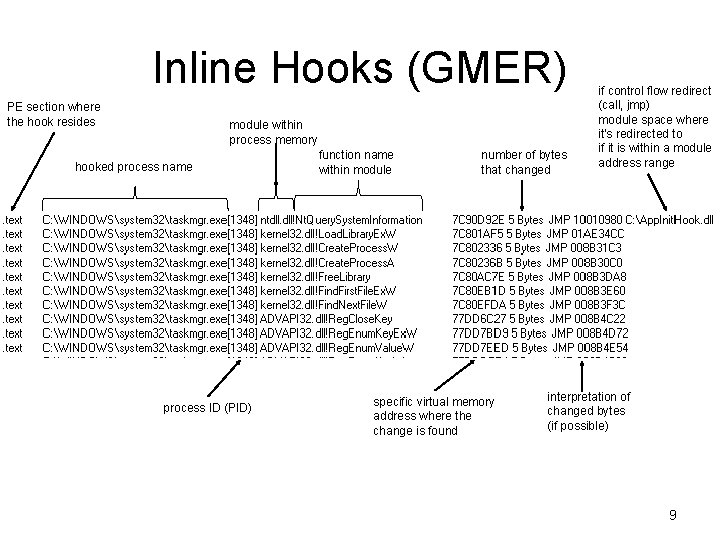
Inline Hooks (GMER) PE section where the hook resides module within process memory hooked process name process ID (PID) function name within module number of bytes that changed specific virtual memory address where the change is found if control flow redirect (call, jmp) module space where it's redirected to if it is within a module address range interpretation of changed bytes (if possible) 9

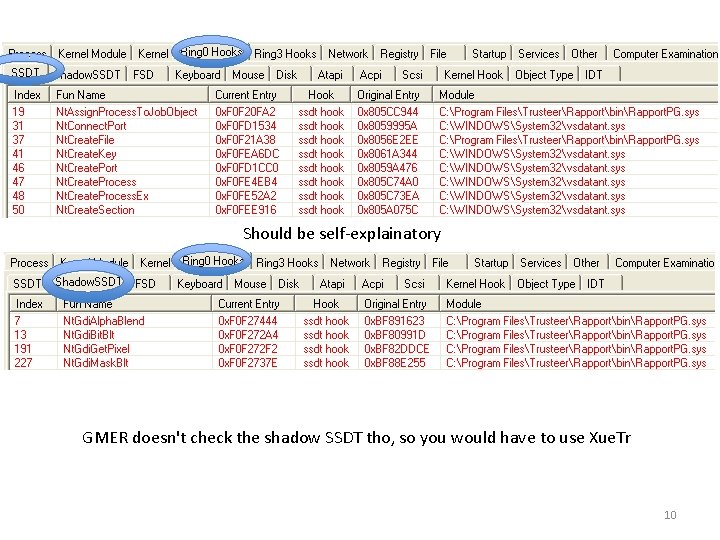
Should be self-explainatory GMER doesn't check the shadow SSDT tho, so you would have to use Xue. Tr 10

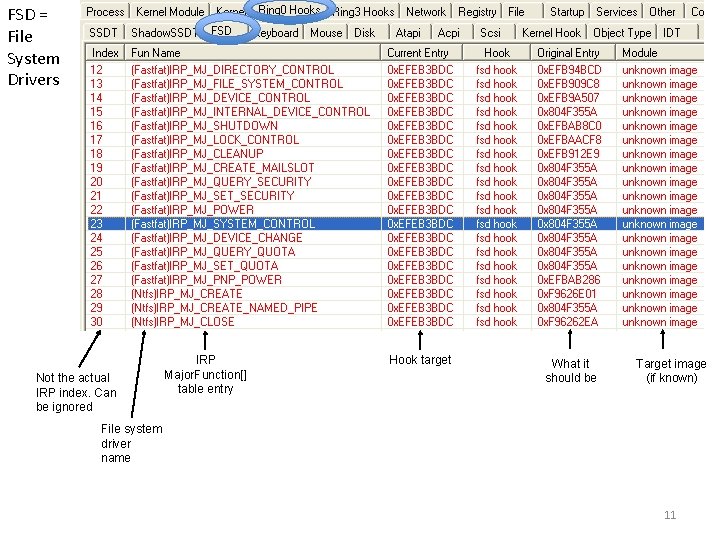
FSD = File System Drivers Not the actual IRP index. Can be ignored IRP Major. Function[] table entry Hook target What it should be Target image (if known) File system driver name 11