Random Access Carrier Sense Multiple Access with Collision





- Slides: 30

Random Access • • • Carrier Sense Multiple Access with Collision Detection(CSMA/CD) The CSMA method does not specify the procedure following a collision Includes an algorithm to handle the collision. Here a station monitor the medium after sends a frame Till transmission successful If there is a collision then station send again Ajith G. S: poposir. orgfree. com

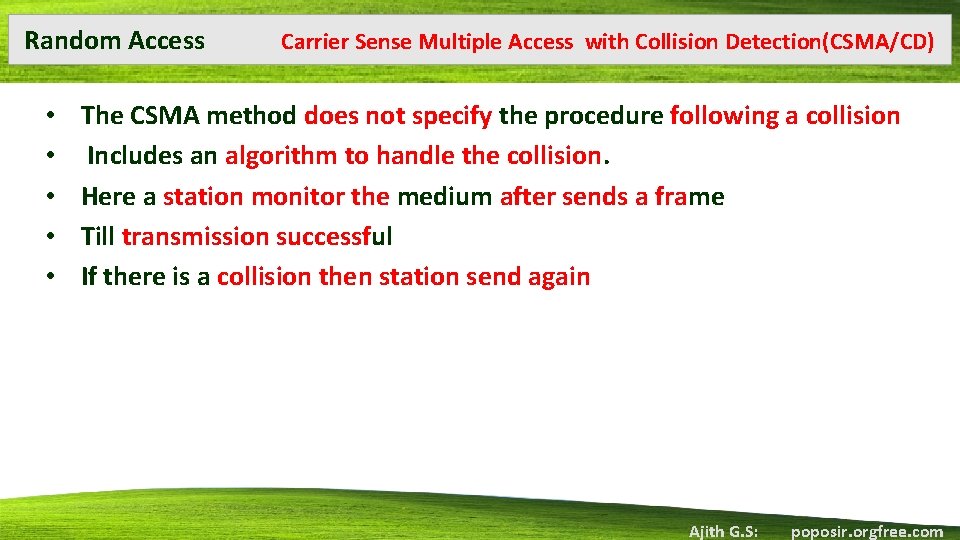
Random Access Carrier Sense Multiple Access with Collision Detection(CSMA/CD) • Collision of CSMA/CD Ajith G. S: poposir. orgfree. com

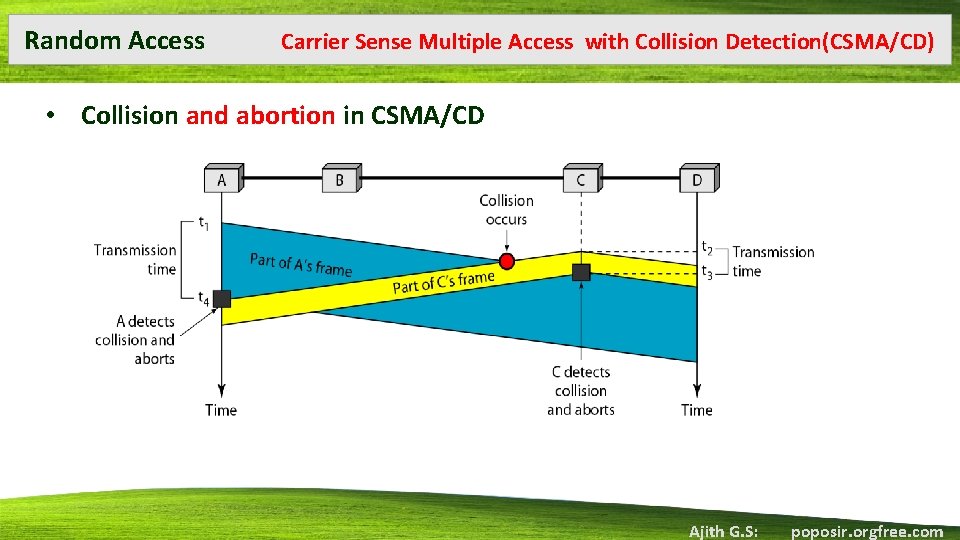
Random Access • • Carrier Sense Multiple Access with Collision Detection(CSMA/CD) From the above fig Station A and C involved in collision At time t 1 station A start sending bits of frame At time t 2 station C has not yet sensed the first bit sent by A Station C start sending the frame in both left and right some time after t 2 collision occur Station C detect a collision at time t 3 when first bit of A’s frame collide Station C immediately abort transmission Ajith G. S: poposir. orgfree. com

Random Access Carrier Sense Multiple Access with Collision Detection(CSMA/CD) • Collision and abortion in CSMA/CD Ajith G. S: poposir. orgfree. com

Random Access • • (CSMA/CD) Minimum Frame Size There is some restriction on the frame size in CSMA/CD Before sending the last bit of frame the sending station must detect a collision, if any and abort the transmission This is because once the entire frame is sent the station does not keep a copy of the frame and does not monitor the line for transmission There fore the frame transmission time must be at least 2 times the max propagation time Tp(Worst Case Scenario- 2 stations are at maximum distance) Worst case if 2 station involved in collision at maximum distance The signal from first takes time TP to reach the second station and effect the collision Takes another Tp time needed for the jamming signal to inform collision so total time is 2 Tp Ajith G. S: poposir. orgfree. com

Random Access (CSMA/CD) Comparison with pure ALOHA • Use of a persistence method • The frame transmission and collision detection is a continuous process • After a collision is detected a jamming signal is send by the station. Ajith G. S: poposir. orgfree. com

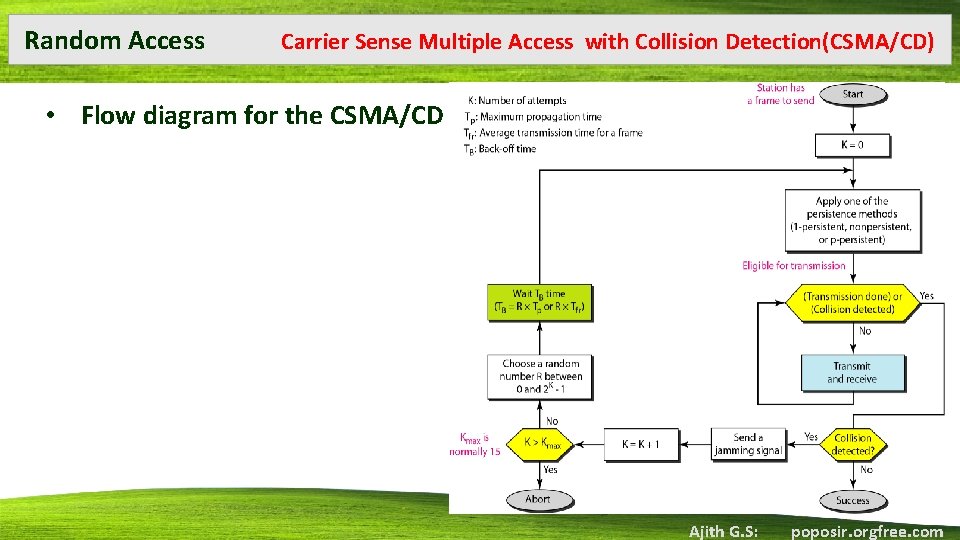
Random Access Carrier Sense Multiple Access with Collision Detection(CSMA/CD) • Flow diagram for the CSMA/CD Ajith G. S: poposir. orgfree. com

Random Access (CSMA/CD) Exponential back-off algorithm Algorithm used by the transmitting station to determine the waiting time following a collision before attempting to retransmit a frame • Following a collision each station generates a random number • It then waits the number of slot time before attempting retransmission • The range of values increases exponentially after each failed transmission • Ajith G. S: poposir. orgfree. com

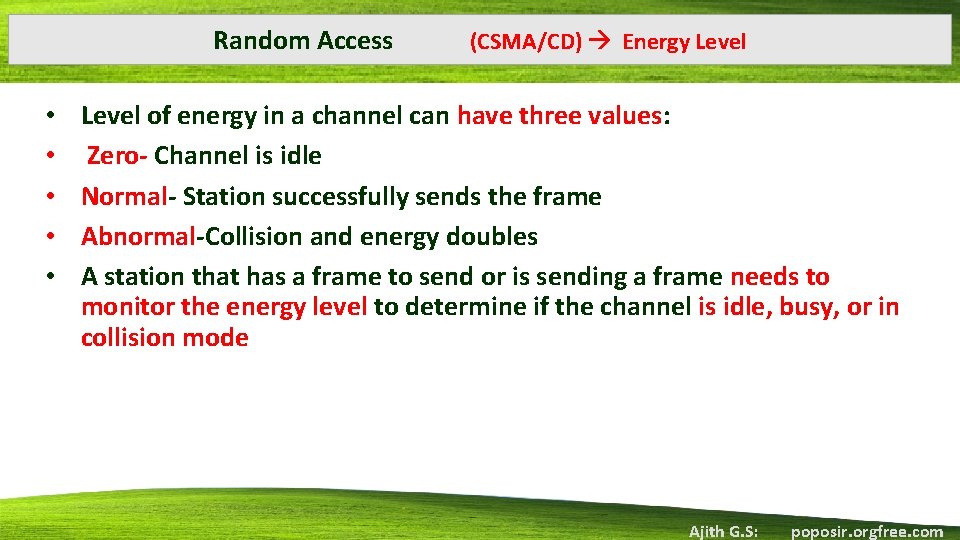
Random Access • • • (CSMA/CD) Energy Level of energy in a channel can have three values: Zero- Channel is idle Normal- Station successfully sends the frame Abnormal-Collision and energy doubles A station that has a frame to send or is sending a frame needs to monitor the energy level to determine if the channel is idle, busy, or in collision mode Ajith G. S: poposir. orgfree. com

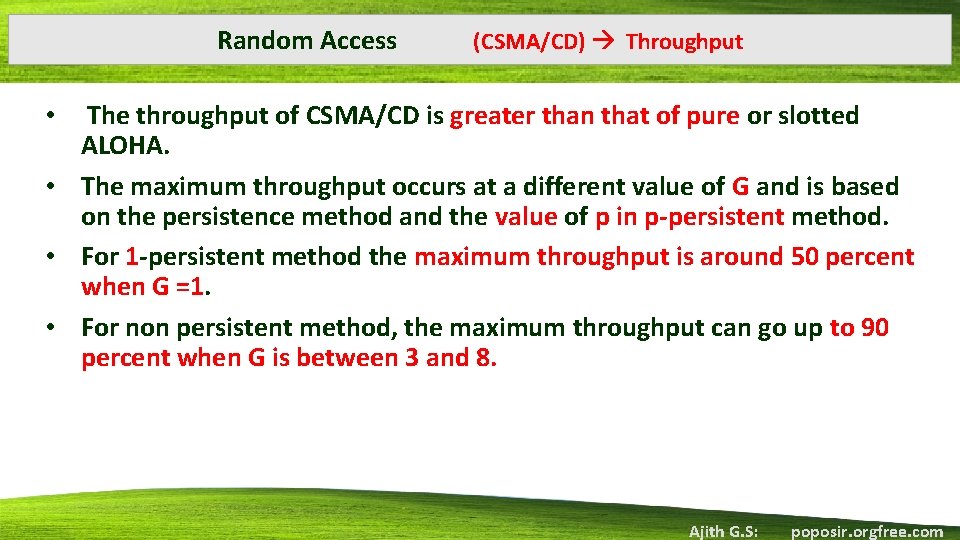
Random Access (CSMA/CD) Throughput The throughput of CSMA/CD is greater than that of pure or slotted ALOHA. • The maximum throughput occurs at a different value of G and is based on the persistence method and the value of p in p-persistent method. • For 1 -persistent method the maximum throughput is around 50 percent when G =1. • For non persistent method, the maximum throughput can go up to 90 percent when G is between 3 and 8. • Ajith G. S: poposir. orgfree. com

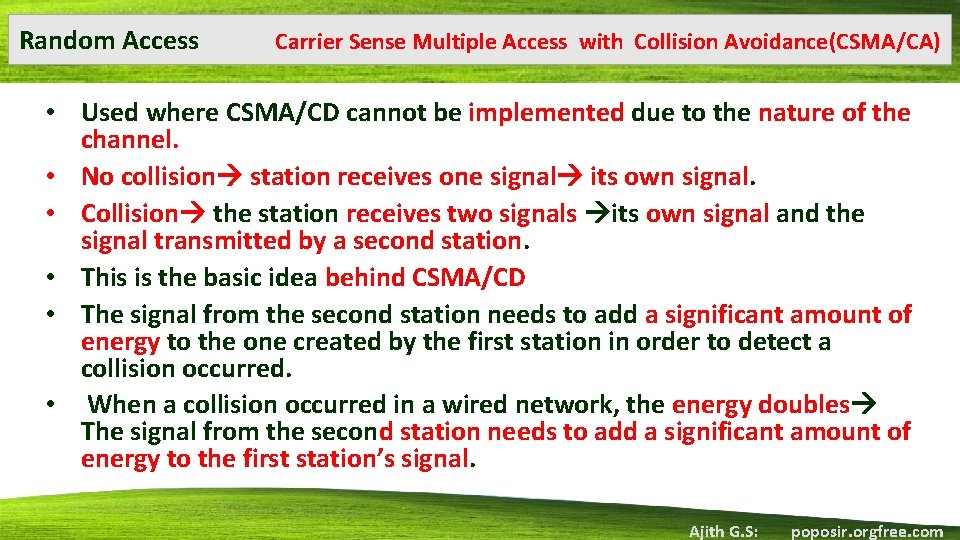
Random Access Carrier Sense Multiple Access with Collision Avoidance(CSMA/CA) • Used where CSMA/CD cannot be implemented due to the nature of the channel. • No collision station receives one signal its own signal. • Collision the station receives two signals its own signal and the signal transmitted by a second station. • This is the basic idea behind CSMA/CD • The signal from the second station needs to add a significant amount of energy to the one created by the first station in order to detect a collision occurred. • When a collision occurred in a wired network, the energy doubles The signal from the second station needs to add a significant amount of energy to the first station’s signal. Ajith G. S: poposir. orgfree. com

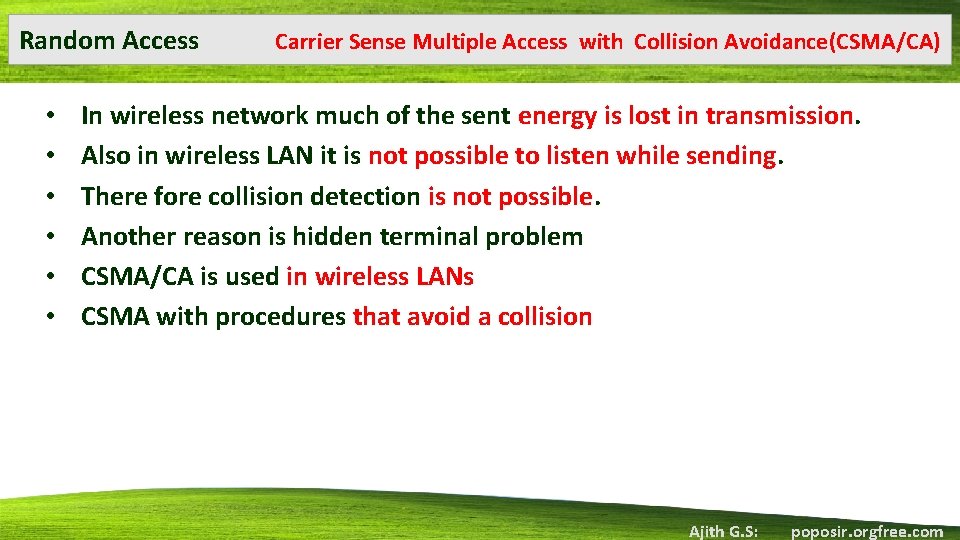
Random Access • • • Carrier Sense Multiple Access with Collision Avoidance(CSMA/CA) In wireless network much of the sent energy is lost in transmission. Also in wireless LAN it is not possible to listen while sending. There fore collision detection is not possible. Another reason is hidden terminal problem CSMA/CA is used in wireless LANs CSMA with procedures that avoid a collision Ajith G. S: poposir. orgfree. com

Random Access Carrier Sense Multiple Access with Collision Avoidance(CSMA/CA) • Collisions are avoided through the use of CSMA/CA's three strategies: • inter frame space • contention window • acknowledgments Ajith G. S: poposir. orgfree. com

Random Access (CSMA/CA) inter frame space • When an channel is found idle , the station does not send immediately. • It waits for a period of time , this time is called inter frame space or IFS. • Even though the channel may appear idle when it is sensed, other station can started transmitting and. • So avoid collision • If the station is still idle After IFS time, also wait for a time =contention window • Using this can set priority of stations: if a station with smaller IFS has higher priority Ajith G. S: poposir. orgfree. com

Random Access (CSMA/CA) Contention Window • Amount of time divided into slots. • A station chooses a random number of slots as its wait time. • The number of slots in the window changes according to the binary exponential back-off strategy • First time- 1 slot • Doubles each time • Station senses the channel after each time slot If the station finds the medium is idle, it will transmit otherwise it halts the process and transmit when the medium is idle Ajith G. S: poposir. orgfree. com

Random Access (CSMA/CA) Acknowledgment • With all these precautions, there still may be a collision resulting in destroyed data. • In addition, the data may be corrupted during the transmission. • The positive acknowledgment and the time-out timer can help guarantee that the receiver has received the frame. Ajith G. S: poposir. orgfree. com

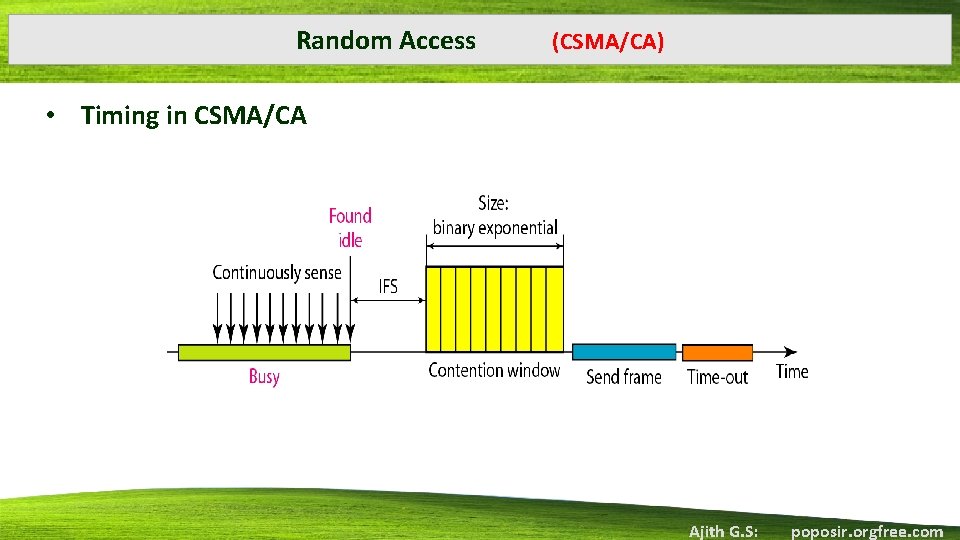
Random Access (CSMA/CA) • Timing in CSMA/CA Ajith G. S: poposir. orgfree. com

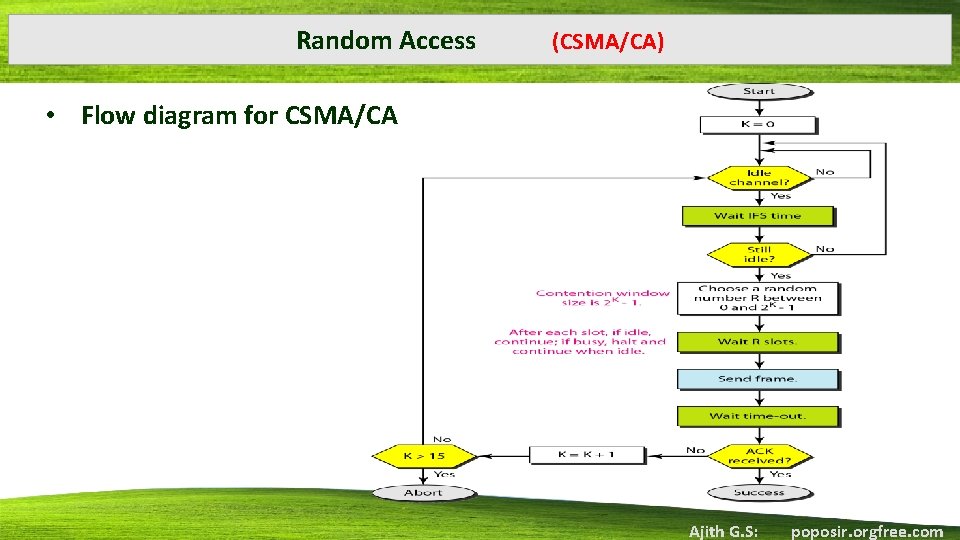
Random Access (CSMA/CA) • Flow diagram for CSMA/CA Ajith G. S: poposir. orgfree. com

Controlled Access • • • Stations consult one another to find which station has the right to send. A station cannot send unless it has been authorized by other stations. Three popular methods include: Reservation Polling Token Passing Ajith G. S: poposir. orgfree. com

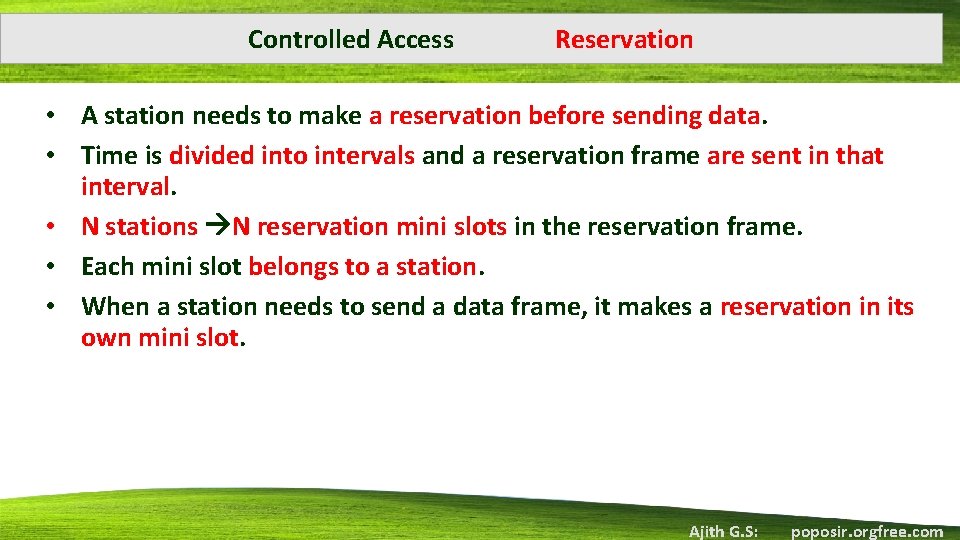
Controlled Access Reservation • A station needs to make a reservation before sending data. • Time is divided into intervals and a reservation frame are sent in that interval. • N stations N reservation mini slots in the reservation frame. • Each mini slot belongs to a station. • When a station needs to send a data frame, it makes a reservation in its own mini slot. Ajith G. S: poposir. orgfree. com

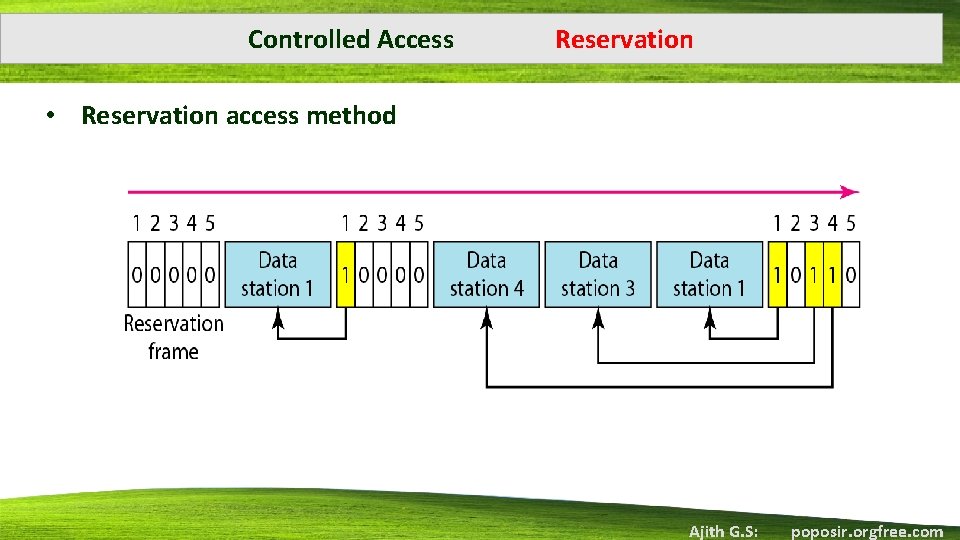
Controlled Access Reservation • Reservation access method Ajith G. S: poposir. orgfree. com

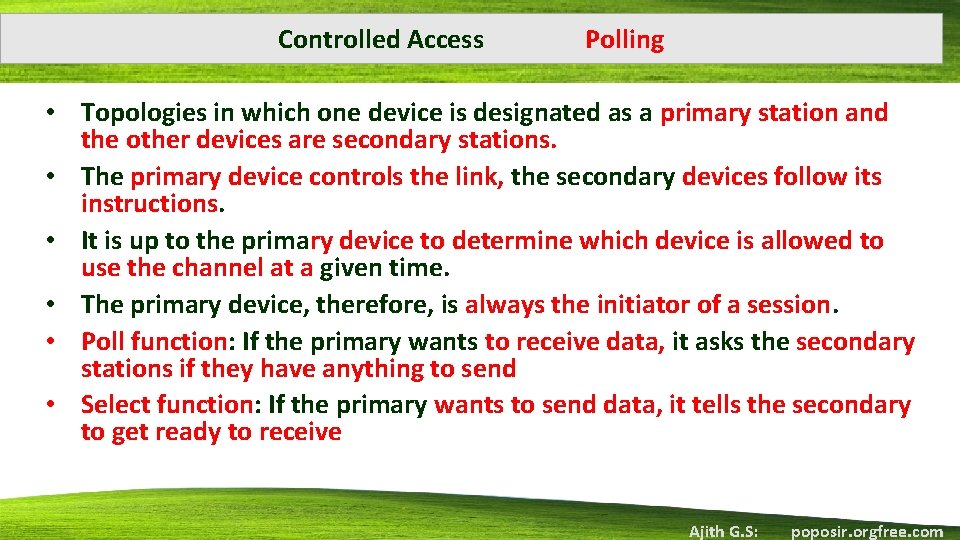
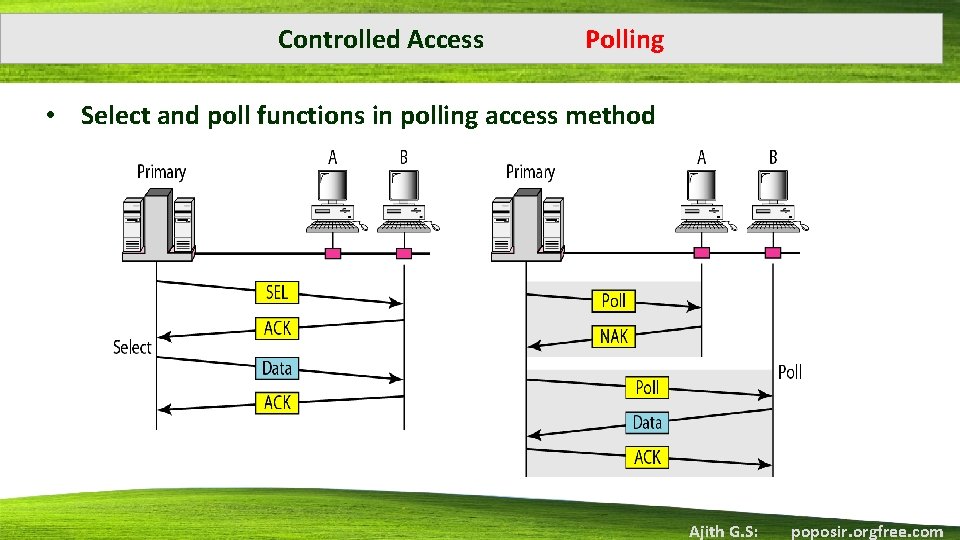
Controlled Access Polling • Topologies in which one device is designated as a primary station and the other devices are secondary stations. • The primary device controls the link, the secondary devices follow its instructions. • It is up to the primary device to determine which device is allowed to use the channel at a given time. • The primary device, therefore, is always the initiator of a session. • Poll function: If the primary wants to receive data, it asks the secondary stations if they have anything to send • Select function: If the primary wants to send data, it tells the secondary to get ready to receive Ajith G. S: poposir. orgfree. com

Controlled Access Polling • There are two general polling policies: • Round robin order • Round-robin means each station has an equal opportunity to transmit packets • Priority order means some stations will have more opportunity to send Ajith G. S: poposir. orgfree. com

Controlled Access Polling • Select and poll functions in polling access method Ajith G. S: poposir. orgfree. com

Controlled Access Token passing • Token passing is a channel access method where a signal called a token is passed between nodes that authorizes the node to communicate • The stations in a network are organized in a ring (physically or logically) for each station, there is a predecessor and a successor. • Token circulates through the ring and possession of the token gives the station the right to access Ajith G. S: poposir. orgfree. com

Controlled Access Token passing • When a station has some data to send, it waits until it receives the token • It then holds the token and sends its data and releases the token when it has no data to send. • The station cannot send data until it receives the token again in the next round. • When a station receives the token and has no data to send, it just passes the data to the next station. Ajith G. S: poposir. orgfree. com

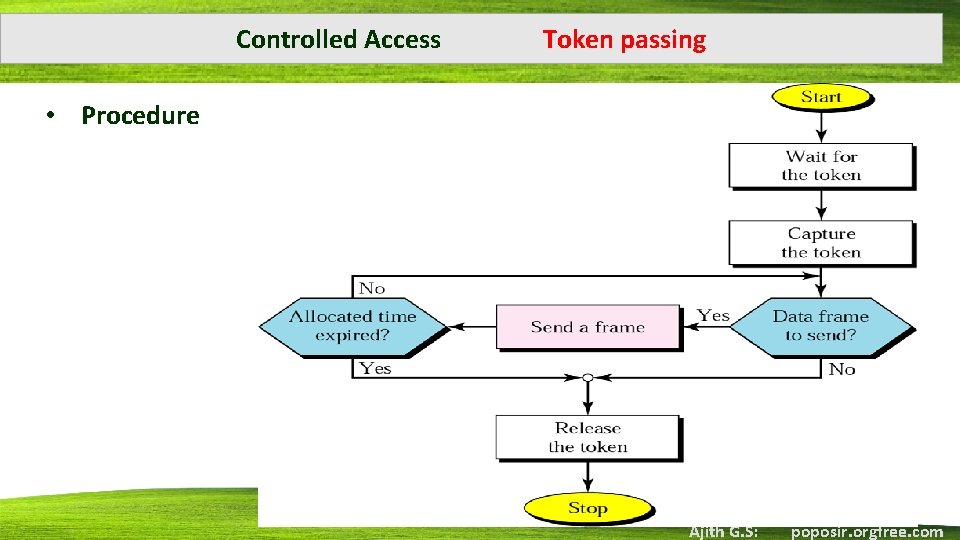
Controlled Access Token passing • Procedure Ajith G. S: poposir. orgfree. com

Controlled Access Token passing • Token management • To limit the time stations can have possession of the token. • The token must be monitored to ensure it has not been lost or destroyed. • Example: if a station that is holding the token fails, the token will disappear from the network. • To assign priorities to the stations and to the types of data being transmitted. • To make low-priority stations release the token to high priority stations. Ajith G. S: poposir. orgfree. com

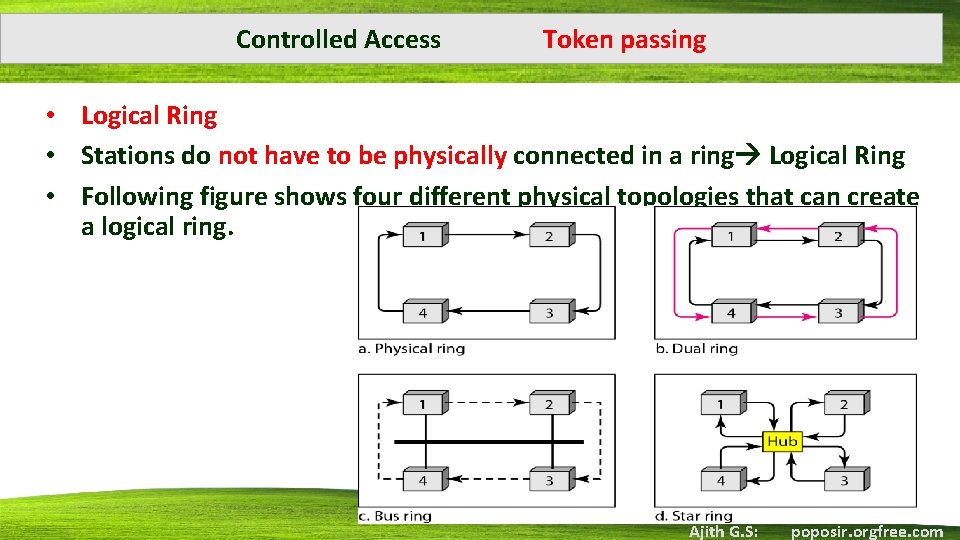
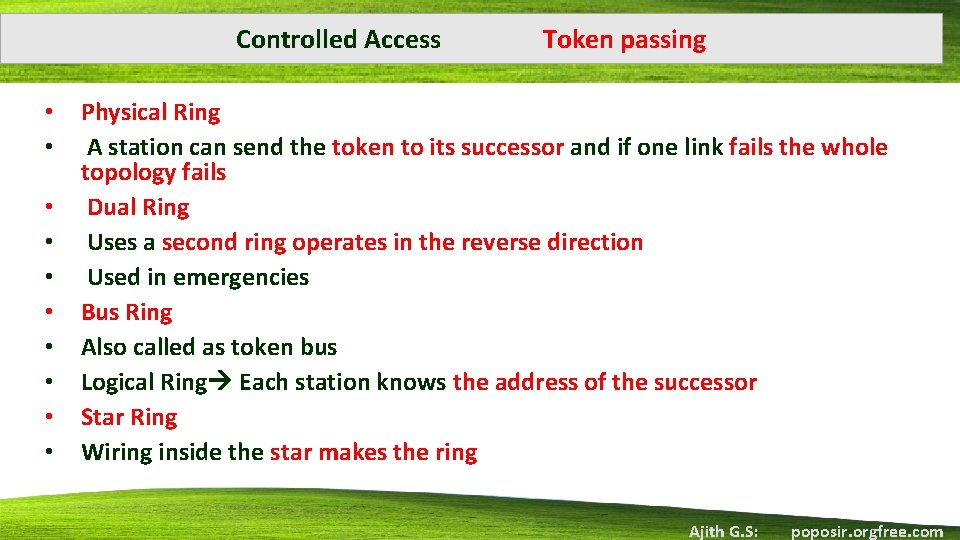
Controlled Access Token passing • Logical Ring • Stations do not have to be physically connected in a ring Logical Ring • Following figure shows four different physical topologies that can create a logical ring. Ajith G. S: poposir. orgfree. com

Controlled Access • • • Token passing Physical Ring A station can send the token to its successor and if one link fails the whole topology fails Dual Ring Uses a second ring operates in the reverse direction Used in emergencies Bus Ring Also called as token bus Logical Ring Each station knows the address of the successor Star Ring Wiring inside the star makes the ring Ajith G. S: poposir. orgfree. com