Product Tampering and Counterfeiting PTC Awareness for Acquisition











- Slides: 21

Product Tampering and Counterfeiting (PTC) Awareness for Acquisition Professionals Training, Awareness, and Strategies for Privacy and Security Cybersecurity Acquisition Training Overview (CATO) Information Technology Category (ITC) IT Security Subcategory 08 Nov 2017

CATO Roadmap Introduction to Cybersecurity in Acquisitions Risk Management Framework (RMF) Internet of Things (Io. T) Product Tampering and Counterfeiting (PTC)

Intended Audience Who should take this training? Acquisition Professionals that support the Federal Agencies in procuring Information and Communications Technology (ICT). 01 Contracting Officers (COs) 02 Contracting Officer’s Representatives (CORs) 03 04 Contracting Officer’s Technical Representatives (COTRs) Responsible for managing contracts and overseeing their implementation. In regard to Cybersecurity, COs in collaboration with the Chief Information Security Officer (CISO) and COTRs ensure agency’s contracting policies and contracts adequately address the information security requirements. Responsible for performing contract management activities and functions to ensure contractors meet the commitment of their contracts, proper development of requirements, and assist Contracting Officers in managing their contracts. Responsible for monitoring the contractor's performance in fulfilling the technical requirements specified. Program and Project Managers (P/PMs) Responsible for performing program and project management activities and functions in developing accurate government requirements, defining measurable performance standards, and managing life cycle activities to ensure that intended outcomes are achieved.

Introduction Background and Purpose Definitions Key Definitions and Terminology Threats and Impacts to the ICT Supply Chain Examples Recent PTC Headlines in the News Countermeasures Acquisition Strategies to Prevent PTC Agenda

Introduction Background and Purpose Product counterfeiting is rampant with ICT, costing billions of dollars, while tampering is even more damaging, resulting in unauthorized access and the loss of sensitive information. § Statistics from the last few years show a clear increase in the number of counterfeit products, affecting almost every industry. The International Chamber of Commerce (ICC) estimates that the total global economic value of counterfeit goods was $1. 77 trillion in 2015 alone. In 2008, this value was just $650 billion – an alarming increase. § Meanwhile, cases of product tampering remain infamous. Few can forget how the National Security Agency (NSA) tampered with an American multinational technology conglomerate’s routers prior to export, and more recently, how an Asian global manufacturer of memory chips received reports from their return center regarding memory chips that were either missing, tampered with, or counterfeited. The purpose of this training is to improve the awareness of Acquisition Professionals regarding the potential threats, impacts, and countermeasures of PTC.

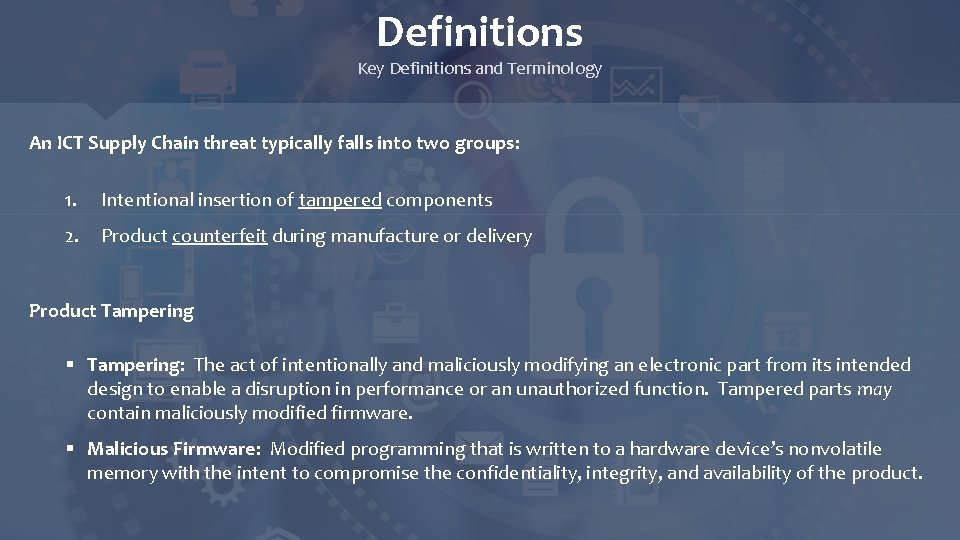
Definitions Key Definitions and Terminology An ICT Supply Chain threat typically falls into two groups: 1. Intentional insertion of tampered components 2. Product counterfeit during manufacture or delivery Product Tampering § Tampering: The act of intentionally and maliciously modifying an electronic part from its intended design to enable a disruption in performance or an unauthorized function. Tampered parts may contain maliciously modified firmware. § Malicious Firmware: Modified programming that is written to a hardware device’s nonvolatile memory with the intent to compromise the confidentiality, integrity, and availability of the product.

Definitions Key Definitions and Terminology (continued) Product Counterfeiting § Counterfeiting: The act of an unlawful or unauthorized reproduction, substitution or alteration that has been knowingly mismarked, misidentified or otherwise misrepresented to be an authentic, unmodified electronic part from the original manufacturer, or a source with the express written authority of the original manufacturer or current design activity, including an authorized aftermarket manufacturer. Unlawful or unauthorized substitution includes used electronic parts represented as new, or the false identification of grade, serial number, lot number, date code or performance characteristics (Defense Federal Acquisition Regulation Supplement [DFARS], Subpart 202. 1– Definitions). Such acts are motivated by profit or malice. • Counterfeits for Profit: Up-screened, re-marked or reused parts sold as new/authentic which is avoidable through Original Equipment Manufacturer (OEM) procurement. • Counterfeits for Malice: “Perfect” parts that also perform additional, unwanted functions, which are designed to pass inspection.

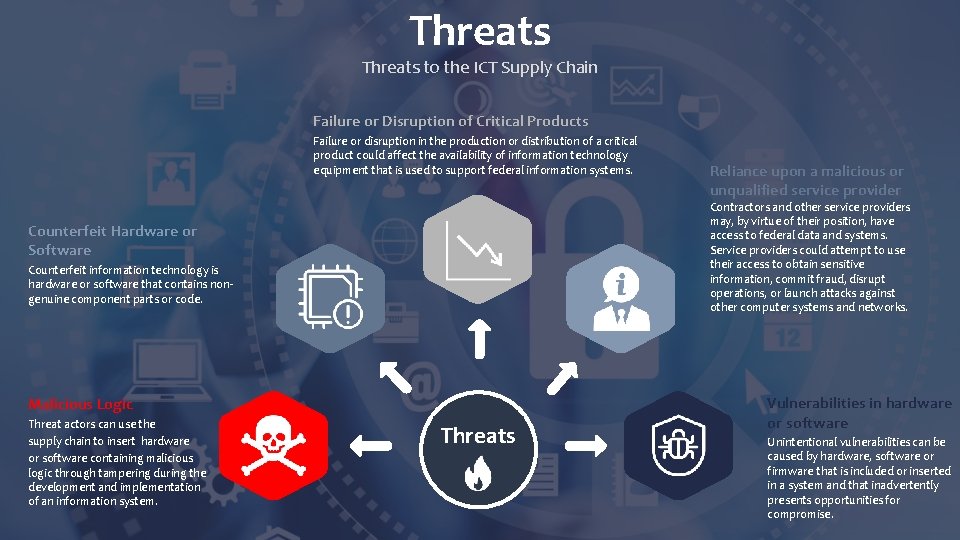
Threats to the ICT Supply Chain Failure or Disruption of Critical Products Failure or disruption in the production or distribution of a critical product could affect the availability of information technology equipment that is used to support federal information systems. Contractors and other service providers may, by virtue of their position, have access to federal data and systems. Service providers could attempt to use their access to obtain sensitive information, commit fraud, disrupt operations, or launch attacks against other computer systems and networks. Counterfeit Hardware or Software Counterfeit information technology is hardware or software that contains nongenuine component parts or code. Malicious Logic Threat actors can use the supply chain to insert hardware or software containing malicious logic through tampering during the development and implementation of an information system. Reliance upon a malicious or unqualified service provider Threats Vulnerabilities in hardware or software Unintentional vulnerabilities can be caused by hardware, software or firmware that is included or inserted in a system and that inadvertently presents opportunities for compromise.

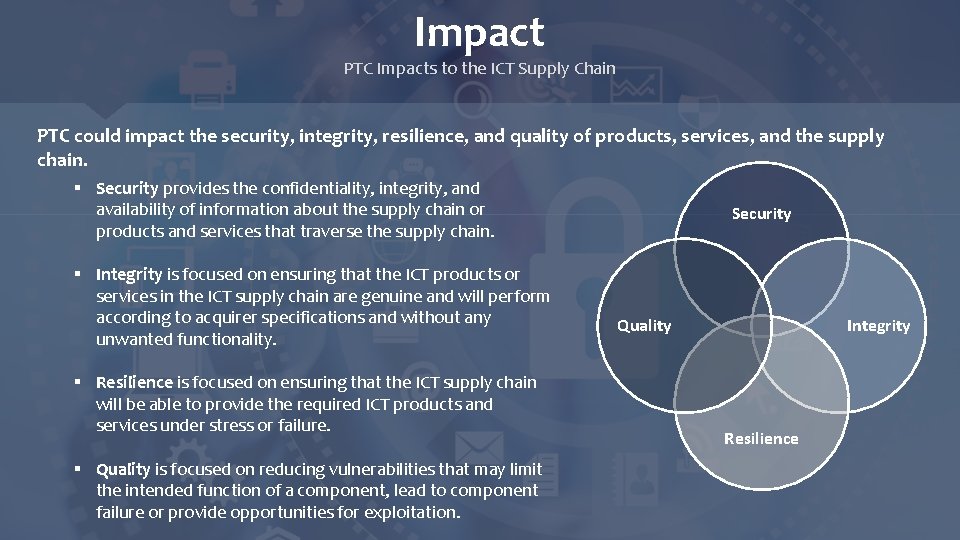
Impact PTC Impacts to the ICT Supply Chain PTC could impact the security, integrity, resilience, and quality of products, services, and the supply chain. § Security provides the confidentiality, integrity, and availability of information about the supply chain or products and services that traverse the supply chain. § Integrity is focused on ensuring that the ICT products or services in the ICT supply chain are genuine and will perform according to acquirer specifications and without any unwanted functionality. § Resilience is focused on ensuring that the ICT supply chain will be able to provide the required ICT products and services under stress or failure. § Quality is focused on reducing vulnerabilities that may limit the intended function of a component, lead to component failure or provide opportunities for exploitation. Security Quality Integrity Resilience

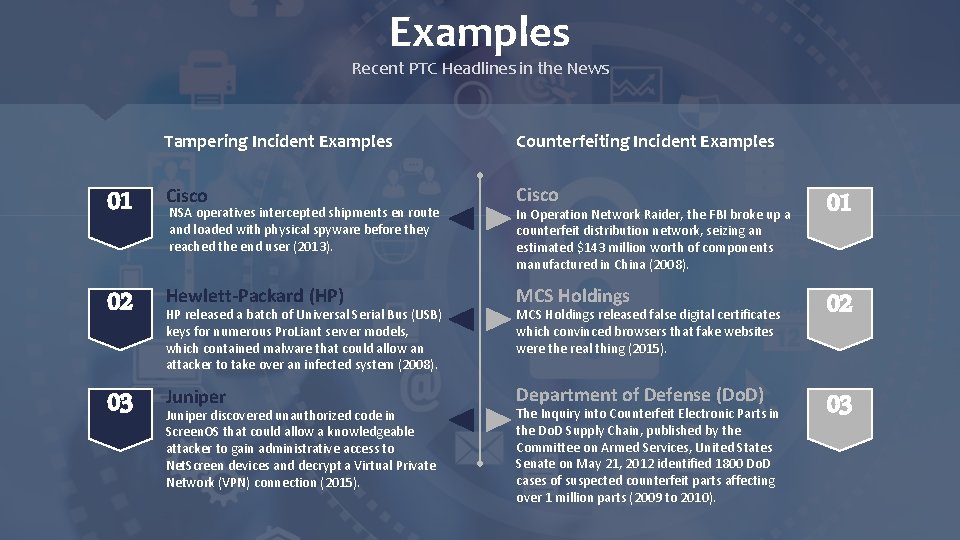
Examples Recent PTC Headlines in the News Tampering Incident Examples Counterfeiting Incident Examples 01 Cisco 01 02 Hewlett-Packard (HP) MCS Holdings 02 03 Juniper Department of Defense (Do. D) 03 NSA operatives intercepted shipments en route and loaded with physical spyware before they reached the end user (2013). HP released a batch of Universal Serial Bus (USB) keys for numerous Pro. Liant server models, which contained malware that could allow an attacker to take over an infected system (2008). Juniper discovered unauthorized code in Screen. OS that could allow a knowledgeable attacker to gain administrative access to Net. Screen devices and decrypt a Virtual Private Network (VPN) connection (2015). In Operation Network Raider, the FBI broke up a counterfeit distribution network, seizing an estimated $143 million worth of components manufactured in China (2008). MCS Holdings released false digital certificates which convinced browsers that fake websites were the real thing (2015). The Inquiry into Counterfeit Electronic Parts in the Do. D Supply Chain, published by the Committee on Armed Services, United States Senate on May 21, 2012 identified 1800 Do. D cases of suspected counterfeit parts affecting over 1 million parts (2009 to 2010).

Countermeasures Acquisition Strategies to Prevent PTC An effective mitigation strategy begins with GSA’s understanding of its supply chain and its vulnerabilities. ICT PTC risk mitigations are mechanisms to research, identify, and assess the security, integrity, quality, and resilience of the procured products and services. These mitigation strategies encompass the following focus areas within the acquisition life cycle: 1. Providers of Products and Services (CO, COR, and COTR) 2. Distribution and Transportation (CO, COR, and COTR) 3. Installation, Integration, and Maintenance (P/PM) 4. Disposal and Retirement (P/PM) 5. Anti-PTC Technologies (CO, COR, COTR, and P/PM)

Acquisition Mitigation Strategies 1. Providers of Products and Services Mitigation strategies that could be considered for implementation by the CO, COR, and COTR during the acquisition life cycle to reduce the PTC risk relating to the providers of ICT products and services may include the following: Identify the location of a service provider. Identify if the provider employs foreign nationals. Review publicly available information (and classified where applicable) regarding a provider’s history of intellectual property theft. Identify and review the provider’s processes and procedures to verify the quality of its products or third-party products and services. Consider the provider’s current financial state and their capability to meet requirements with current and increased demand.

Acquisition Mitigation Strategies 2. Distribution and Transportation Mitigation strategies that could be implemented by the CO, COR, and COTR during the acquisition life cycle to reduce the PTC risk during the distribution and transportation of ICT products may include the following: Identify how products are transported from the producer, manufacturer or service. Determine if products are transported overseas for both imports and exports. Ascertain the transshipment points. Identify where the products are to be warehoused during transportation. Determine who owns or has access to warehouse properties. Ascertain what transportation carriers would be used for product transport.

Acquisition Mitigation Strategies 3. Installation, Integration, and Maintenance Mitigation strategies that could be implemented by the P/PM during the acquisition life cycle to reduce the PTC risk of installation, integration, and maintenance of ICT products may include the following: Identify names and addresses of individuals with access to the products before and after installation. Determine if any foreign nationals have access to the products and their level of access to product information. Ascertain how products and services are incorporated or installed into existing systems, assuring compliance with the organization’s configuration management plan.

Acquisition Mitigation Strategies 4. Disposal and Retirement Mitigation strategies that could be implemented by the P/PM during the acquisition life cycle to reduce the PTC risk of the disposal and retirement of the ICT products may include the following: Identify if products are refurbished or resold, and the names and addresses of companies who could purchase or otherwise acquire such equipment. Require compliance with electronic media sanitization methodologies for wiping hard drives and other media as defined in National Institute for Standards and Technology (NIST) Special Publication 800 -88 Rev. 1, Guidelines for Media Sanitization.

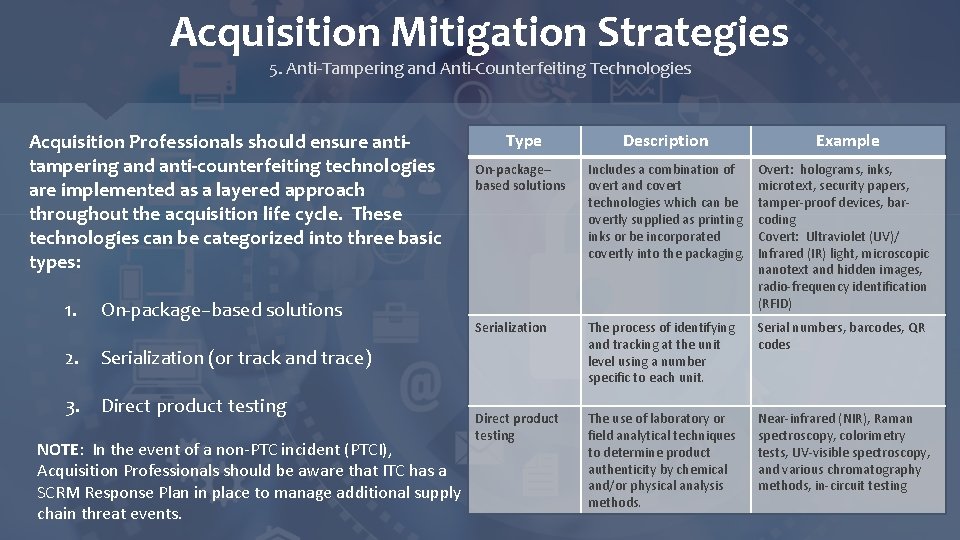
Acquisition Mitigation Strategies 5. Anti-Tampering and Anti-Counterfeiting Technologies Acquisition Professionals should ensure antitampering and anti-counterfeiting technologies are implemented as a layered approach throughout the acquisition life cycle. These technologies can be categorized into three basic types: 1. On-package–based solutions 2. Serialization (or track and trace) 3. Direct product testing NOTE: In the event of a non-PTC incident (PTCI), Acquisition Professionals should be aware that ITC has a SCRM Response Plan in place to manage additional supply chain threat events. Type Description Example On-package– based solutions Includes a combination of overt and covert technologies which can be overtly supplied as printing inks or be incorporated covertly into the packaging. Overt: holograms, inks, microtext, security papers, tamper-proof devices, barcoding Covert: Ultraviolet (UV)/ Infrared (IR) light, microscopic nanotext and hidden images, radio-frequency identification (RFID) Serialization The process of identifying and tracking at the unit level using a number specific to each unit. Serial numbers, barcodes, QR codes Direct product testing The use of laboratory or field analytical techniques to determine product authenticity by chemical and/or physical analysis methods. Near-infrared (NIR), Raman spectroscopy, colorimetry tests, UV-visible spectroscopy, and various chromatography methods, in-circuit testing

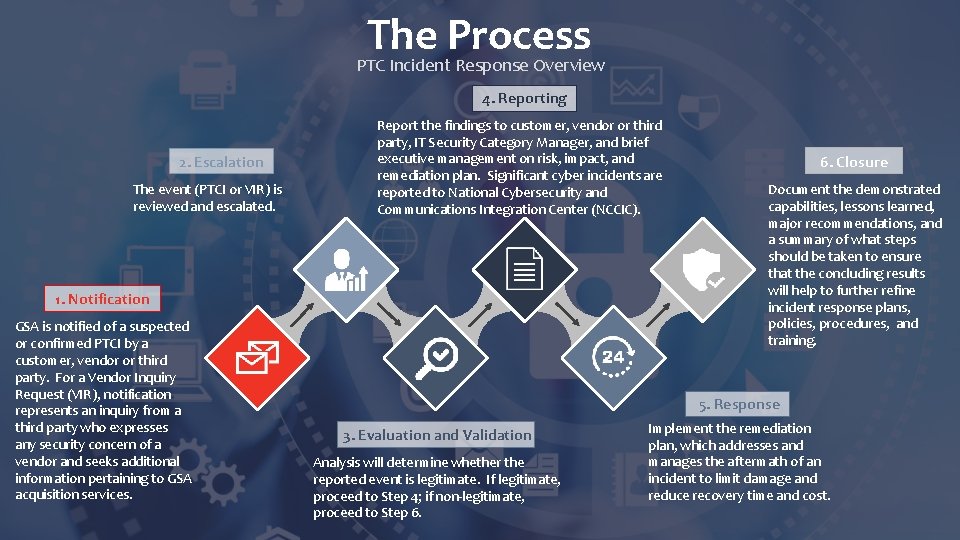
The Process PTC Incident Response Overview 4. Reporting 2. Escalation The event (PTCI or VIR) is reviewed and escalated. Report the findings to customer, vendor or third party, IT Security Category Manager, and brief executive management on risk, impact, and remediation plan. Significant cyber incidents are reported to National Cybersecurity and Communications Integration Center (NCCIC). 1. Notification GSA is notified of a suspected or confirmed PTCI by a customer, vendor or third party. For a Vendor Inquiry Request (VIR), notification represents an inquiry from a third party who expresses any security concern of a vendor and seeks additional information pertaining to GSA acquisition services. 6. Closure Document the demonstrated capabilities, lessons learned, major recommendations, and a summary of what steps should be taken to ensure that the concluding results will help to further refine incident response plans, policies, procedures, and training. 5. Response 3. Evaluation and Validation Analysis will determine whether the reported event is legitimate. If legitimate, proceed to Step 4; if non-legitimate, proceed to Step 6. Implement the remediation plan, which addresses and manages the aftermath of an incident to limit damage and reduce recovery time and cost.

Summary Key Takeaways Sophisticated and targeted tampering and counterfeiting attempts against ICT products continue to increase. Therefore, Acquisition Professionals must be proactive to ensure the ICT supply chain is protected from these threats by integrating relevant cybersecurity requirements throughout the acquisition life cycle. Specifically, it is imperative that special considerations be untaken to implement some or all of the countermeasures documented in this training. Key Takeaways: � Acquisition Professionals must be aware of the different PTC threats. � Implementation of the Acquisition Mitigation Strategies will help protect the security, integrity, resilience, and quality of the ITC products, services, and its supply chain. � Anti-tampering and anti-counterfeiting technologies must be integrated into contract requirements.

Questions & Answers What would you like clarification on?

THANK YOU Thank you for attending this training session. Going forward, we hope you are able to utilize aspects of the program which were of particular benefit to your day-to-day work. We look forward to seeing you at our next session. Please feel free to share any comments you may wish to make about this or any future programs.

Contact Information For more information regarding PTCI response activities or to learn more about the recommended security practices for ITC, contact Shon Lyublanovits (shondrea. lyublanovits@gsa. gov).
 Gangguan pesan
Gangguan pesan Chapter 10 handwriting analysis forgery and counterfeiting
Chapter 10 handwriting analysis forgery and counterfeiting Handwriting characteristics
Handwriting characteristics Flourishes and embellishments in handwriting
Flourishes and embellishments in handwriting Handwriting analysis forgery and counterfeiting
Handwriting analysis forgery and counterfeiting Chapter 10 handwriting analysis forgery and counterfeiting
Chapter 10 handwriting analysis forgery and counterfeiting Privacy awareness and hipaa awareness training cvs
Privacy awareness and hipaa awareness training cvs Comprehensible input
Comprehensible input Eli mufisovski
Eli mufisovski Anti counterfeiting trade agreement
Anti counterfeiting trade agreement Anti counterfeiting trade agreement
Anti counterfeiting trade agreement Ptc manufacturing apps
Ptc manufacturing apps Ptc precision lms
Ptc precision lms Minipcr ptc taster lab
Minipcr ptc taster lab Asme ptc 4
Asme ptc 4 Flotrans ptc
Flotrans ptc Seratus rasa ptc
Seratus rasa ptc Ptc relay diagram
Ptc relay diagram Ptc university
Ptc university Ptc
Ptc Beugungsspektrum
Beugungsspektrum Ptc wizard windham nh
Ptc wizard windham nh