Privilege Check for Control TransferCode Access Control transfers





- Slides: 15

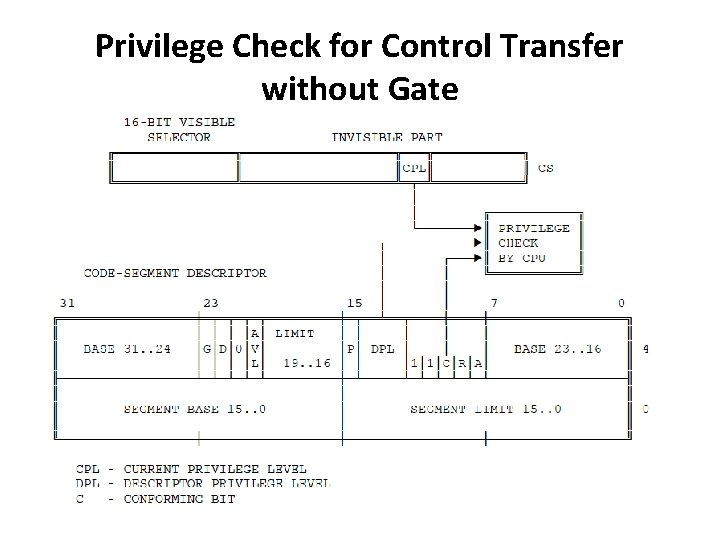
Privilege Check for Control Transfer(Code Access) • Control transfers (except interrupts) are accomplished by the instructions JMP, CALL, and RET • The "near" forms of JMP, CALL, and RET transfer within the current code segment and hence does not require privilege checks. • The "far" forms of JMP and CALL refer to other segments and hence requires privilege checking.

Privilege Check for Control Transfer • There are two ways a JMP or CALL can transfer to another segment 1. Without call gate 2. With call gate

Types of Code Segments • There are two types of code segments: – Conforming Code Segment – Nonconforming Code Segment

Conforming Code Segment • An executable segment whose descriptor has the conforming bit set • It permits sharing of procedures that may be called from various privilege levels but should execute at the privilege level of the calling procedure. • Example: math libraries • When control is transferred to a conforming segment, the CPL does not change

Nonconforming Code Segment • Most code segments are not conforming • For nonconforming segments, control can be transferred without a gate only to executable segments at the same level of privilege • To transfer control to higher privilege levels(not numerical)-for e. g. application want to use system service- CALL instruction need to be used with call-gate descriptors • JMP instruction never transfer control to a nonconforming segment whose DPL ≠ CPL.

Privilege Check for Control Transfer without Gate

Gate Descriptors • To provide protection for control transfers among executable segments at different privilege levels, the 80386 uses gate descriptors. • There are four kinds of gate descriptors: – Call gates for far jmp & call – Trap gates for exceptions – Interrupt gates for interrupts – Task gates for task switching

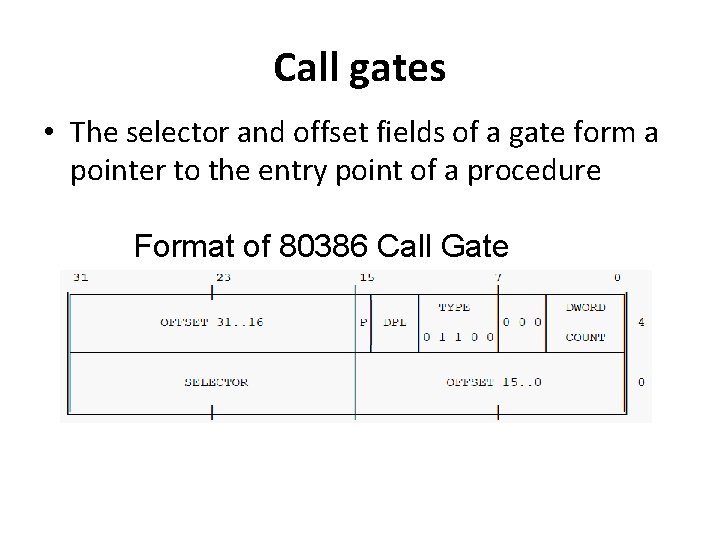
Call gates • A call gate descriptor may reside in GDT or LDT • A call gate has two primary functions: 1. To define an entry point of a procedure 2. To specify the privilege level of entry point • When the h/w recognizes that the destination selector refers to a gate descriptor the operation of the instruction is expanded by the contents of the call gate.

Call gates • The selector and offset fields of a gate form a pointer to the entry point of a procedure Format of 80386 Call Gate

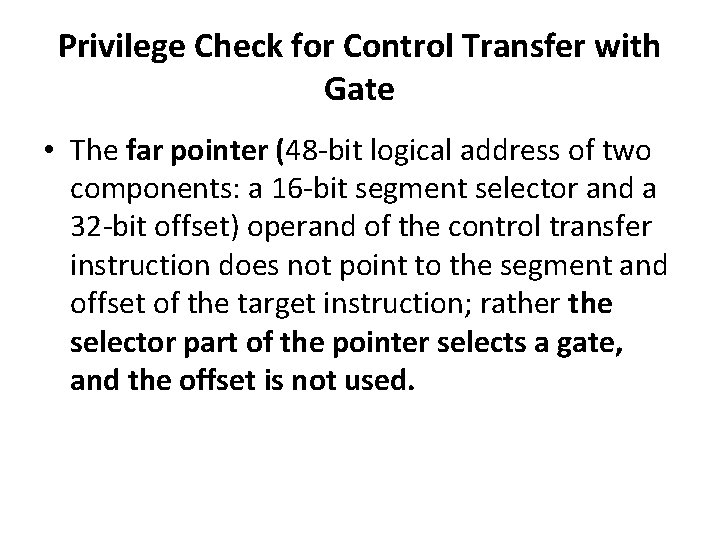
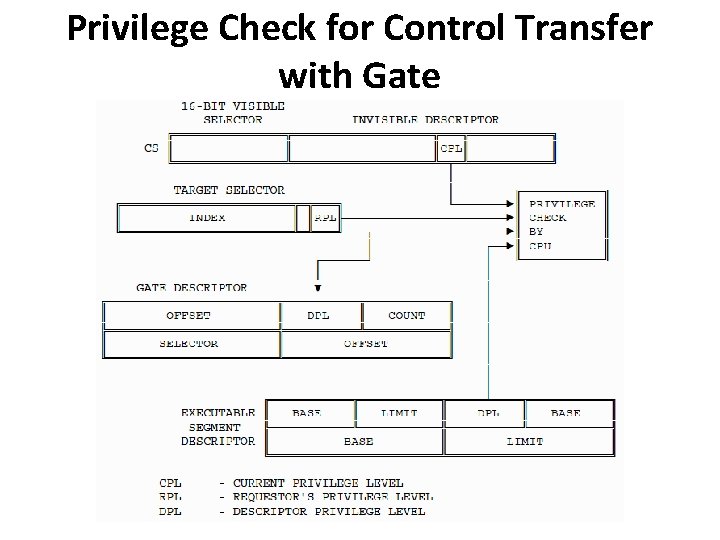
Privilege Check for Control Transfer with Gate • The far pointer (48 -bit logical address of two components: a 16 -bit segment selector and a 32 -bit offset) operand of the control transfer instruction does not point to the segment and offset of the target instruction; rather the selector part of the pointer selects a gate, and the offset is not used.

Privilege Check for Control Transfer with Gate

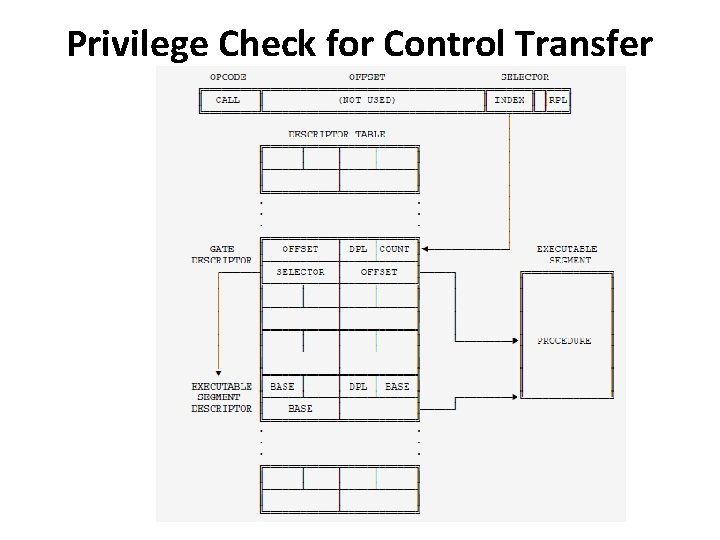
Privilege Check for Control Transfer with Gate • Four different privilege levels are used to check the validity of a control transfer via a call gate: 1. CPL 2. RPL of the selector used to specify the call gate. 3. DPL of the gate descriptor. 4. DPL of the descriptor of the target segment

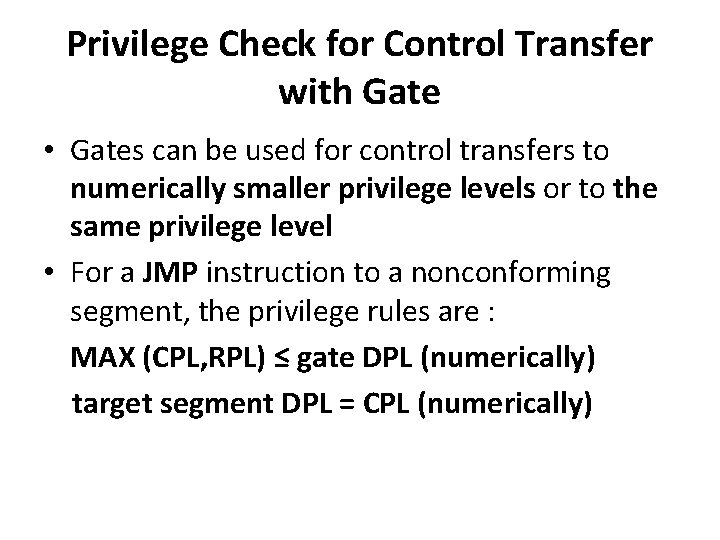
Privilege Check for Control Transfer with Gate • Gates can be used for control transfers to numerically smaller privilege levels or to the same privilege level • For a JMP instruction to a nonconforming segment, the privilege rules are : MAX (CPL, RPL) ≤ gate DPL (numerically) target segment DPL = CPL (numerically)

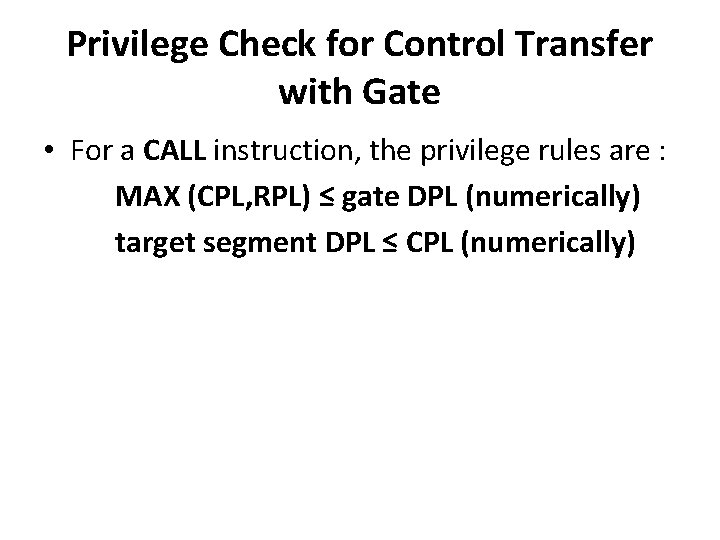
Privilege Check for Control Transfer with Gate • For a CALL instruction, the privilege rules are : MAX (CPL, RPL) ≤ gate DPL (numerically) target segment DPL ≤ CPL (numerically)

Privilege Check for Control Transfer with Gate