Next Generation Firewalls Do We Need Them D



- Slides: 15

Next Generation Firewalls – Do We Need Them? D 12 – Wednesday 18 th July 10. 30 -11. 45 am John Tannahill Mail: jtannahi@rogers. com © 2018 J. Tannahill & Associates

Network Security – Key Risk Areas n Internet Network Perimeter Virtual Private Networks (VPN) Wireless LAN Networks Sensitive Network Segments WAN Connectivity n Software Defined Networking (SDN) n n © 2018 J. Tannahill & Associates 2

Common Network Vulnerabilities n n Network services with known vulnerabilities and not patched Network services with poor authentication Unnecessary network services that are not properly configured or secured Network transmission of clear text credentials and data © 2018 J. Tannahill & Associates 3

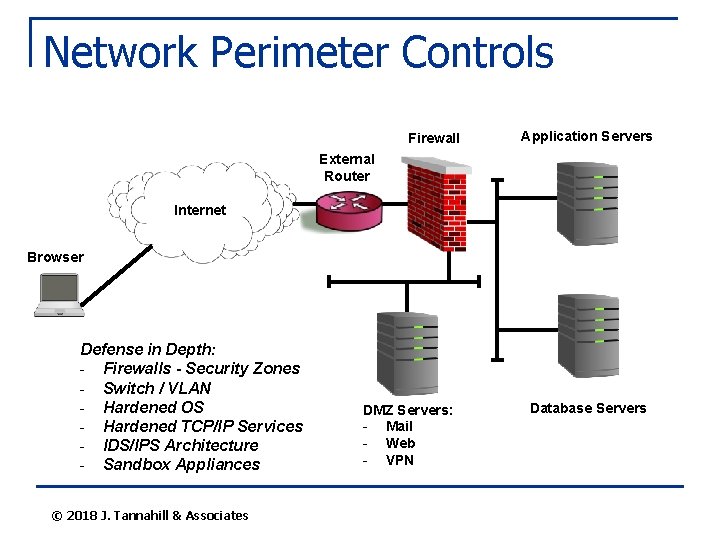
Network Perimeter Controls Firewall Application Servers External Router Internet Browser Defense in Depth: - Firewalls - Security Zones - Switch / VLAN - Hardened OS - Hardened TCP/IP Services - IDS/IPS Architecture - Sandbox Appliances © 2018 J. Tannahill & Associates DMZ Servers: - Mail - Web - VPN Database Servers

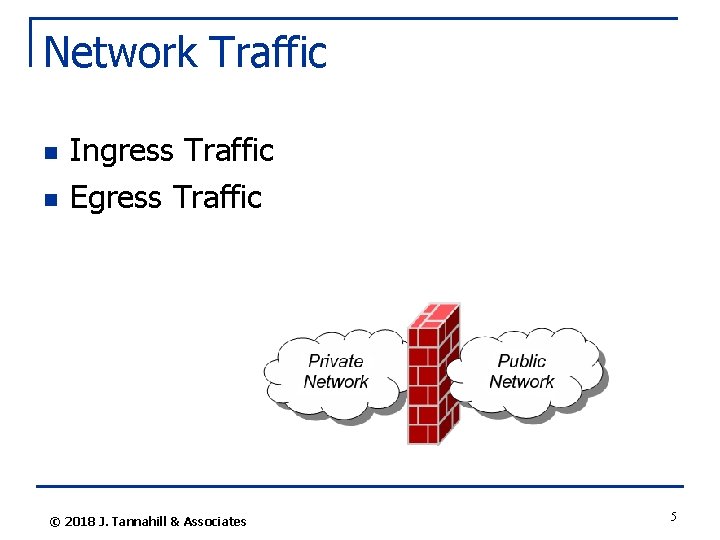
Network Traffic n n Ingress Traffic Egress Traffic © 2018 J. Tannahill & Associates 5

Egress Traffic Controls n n n Network monitoring for egress traffic relating to C 2 traffic Understand anomalous outbound traffic Firewall rules to restrict outbound protocols NGFW to inspect traffic (e. g. https) Use indicators of compromise Use blacklists for C&C Servers © 2018 J. Tannahill & Associates 6

Network Firewall Technologies n n n Packet Filters Stateful Inspection Next Generation Firewalls © 2018 J. Tannahill & Associates 7

NGFW Examples n n n Palo Alto Cisco ASA with Firepower Fortigate © 2018 J. Tannahill & Associates 8

Next Generation Firewall Functions n Palo Alto Example q q q q User-id / App-id Wildfire (Anti-malware) Vulnerability Protection URL Filtering Data Filtering (Data Loss Prevention) Zone Protection SSL Decryption © 2018 J. Tannahill & Associates 9

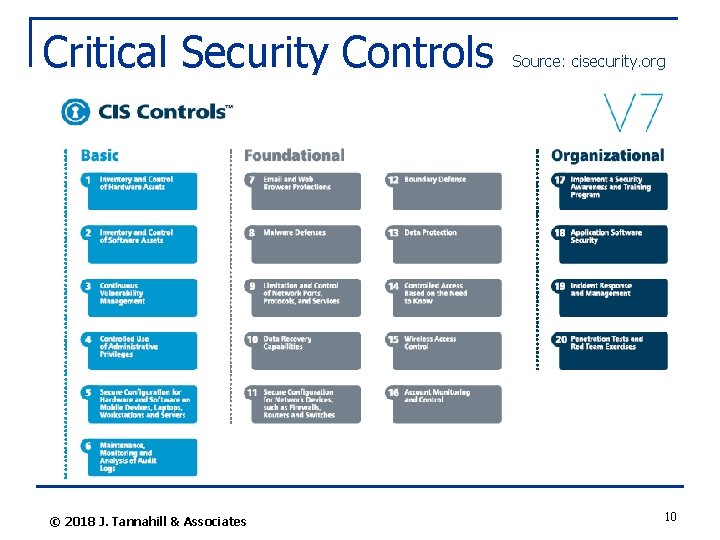
Critical Security Controls © 2018 J. Tannahill & Associates Source: cisecurity. org 10

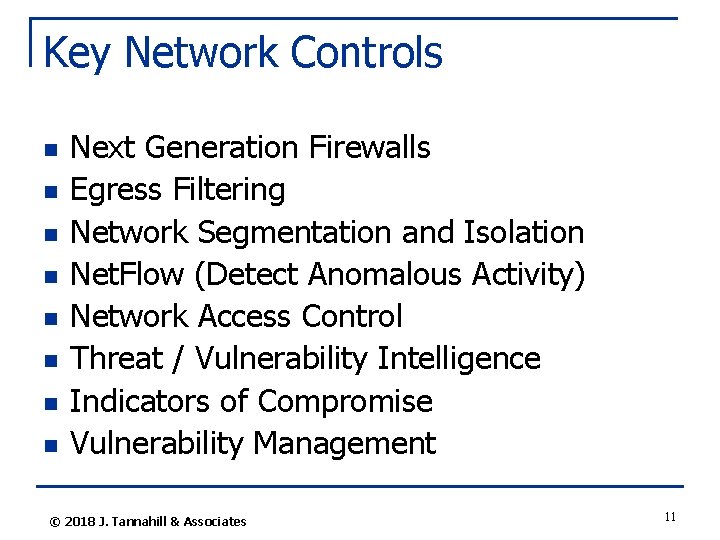
Key Network Controls n n n n Next Generation Firewalls Egress Filtering Network Segmentation and Isolation Net. Flow (Detect Anomalous Activity) Network Access Control Threat / Vulnerability Intelligence Indicators of Compromise Vulnerability Management © 2018 J. Tannahill & Associates 11

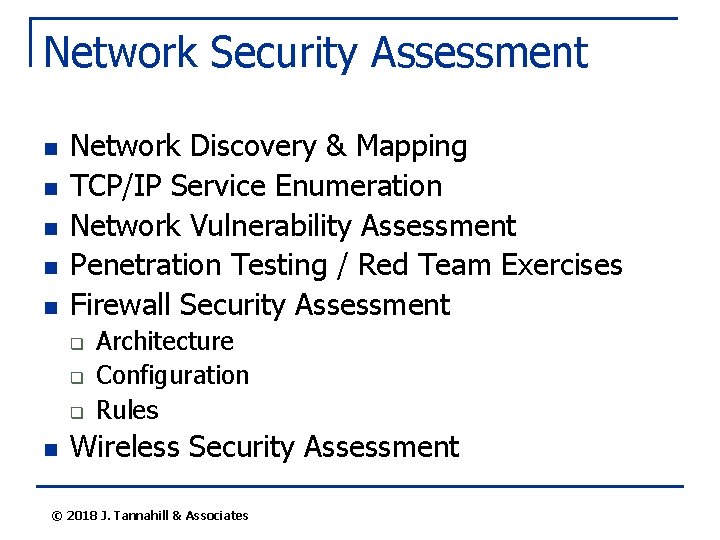
Network Security Assessment n n n Network Discovery & Mapping TCP/IP Service Enumeration Network Vulnerability Assessment Penetration Testing / Red Team Exercises Firewall Security Assessment q q q n Architecture Configuration Rules Wireless Security Assessment © 2018 J. Tannahill & Associates

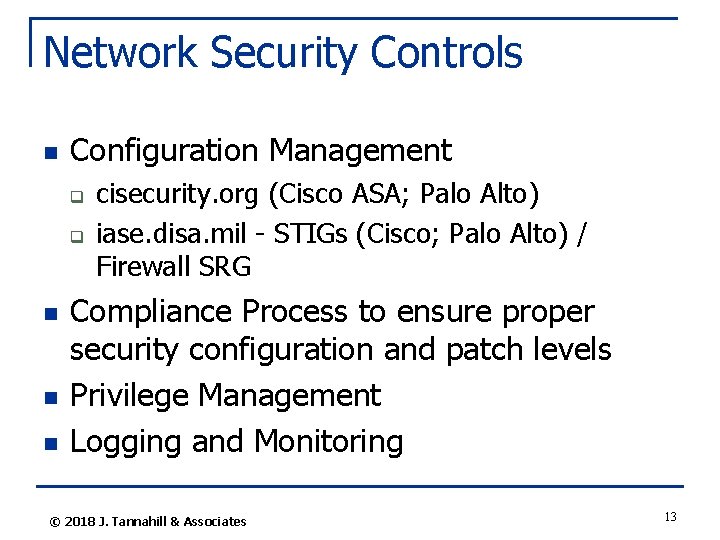
Network Security Controls n Configuration Management q q n n n cisecurity. org (Cisco ASA; Palo Alto) iase. disa. mil - STIGs (Cisco; Palo Alto) / Firewall SRG Compliance Process to ensure proper security configuration and patch levels Privilege Management Logging and Monitoring © 2018 J. Tannahill & Associates 13

Risks of Unsupported/Unpatched Network Perimeter Devices q q E. g. Fortinet Firewall backdoor E. g. Cisco PIX © 2018 J. Tannahill & Associates 14

Summary n No Silver Bullets Avoid Snake Oil Pay Attention to NGFW Configuration Vulnerability Management Layered Defence n Firewall as a Service n n © 2018 J. Tannahill & Associates 15