Network Protocols A network protocol defines the structure


- Slides: 12

Network Protocols • A network protocol defines the structure of messages sent over the network • We will only talk about the Internet • Network protocols need to address many complexities How is the physical hardware controlled? How is routing performed? How do you guarantee the message sequence? How do you guarantee message arrival? How do you manage high traffic, guarantee timing? • Ex. US postal service

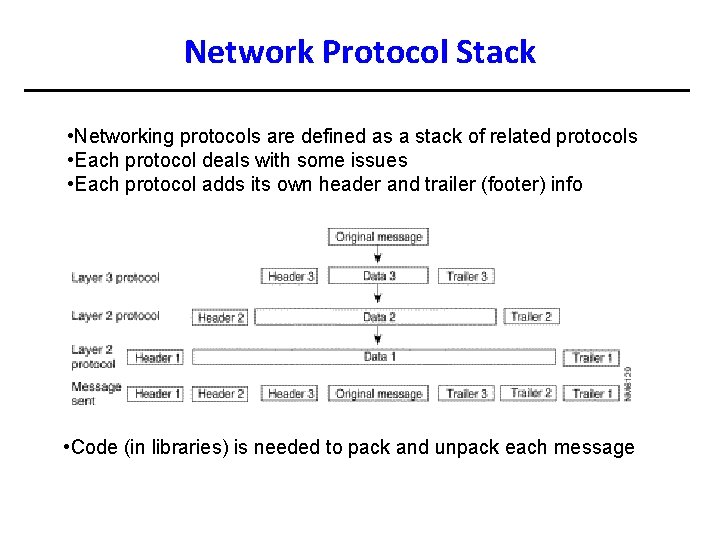
Network Protocol Stack • Networking protocols are defined as a stack of related protocols • Each protocol deals with some issues • Each protocol adds its own header and trailer (footer) info • Code (in libraries) is needed to pack and unpack each message

TCP/IP Protocol Stack • TCP/IP protocol stack defines the Internet Application Layer - Seen by the applications. Services are application specific. Transport Layer - Provides a “reliable bitstream”. Guarantees reliability, message order, no duplication, traffic control Network Layer - Provides “virtual network abstraction”. Provides abstract addressing and routing. Link Layer - Describes how to control the physical hardware. Deals with contention.

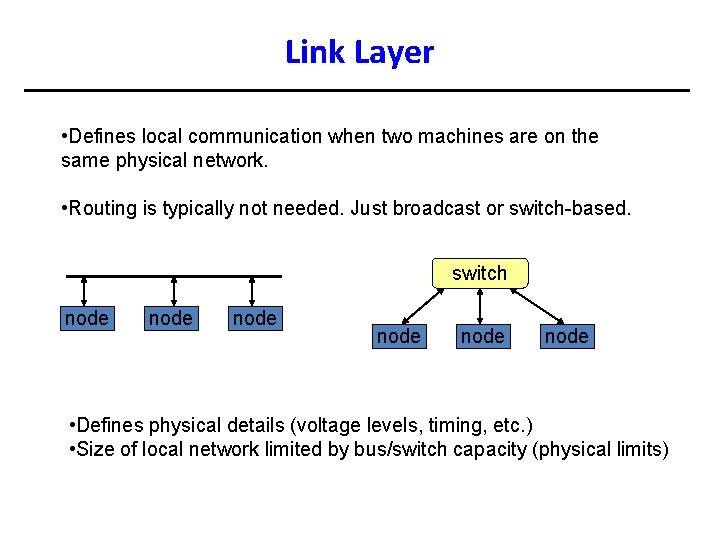
Link Layer • Defines local communication when two machines are on the same physical network. • Routing is typically not needed. Just broadcast or switch-based. switch node node • Defines physical details (voltage levels, timing, etc. ) • Size of local network limited by bus/switch capacity (physical limits)

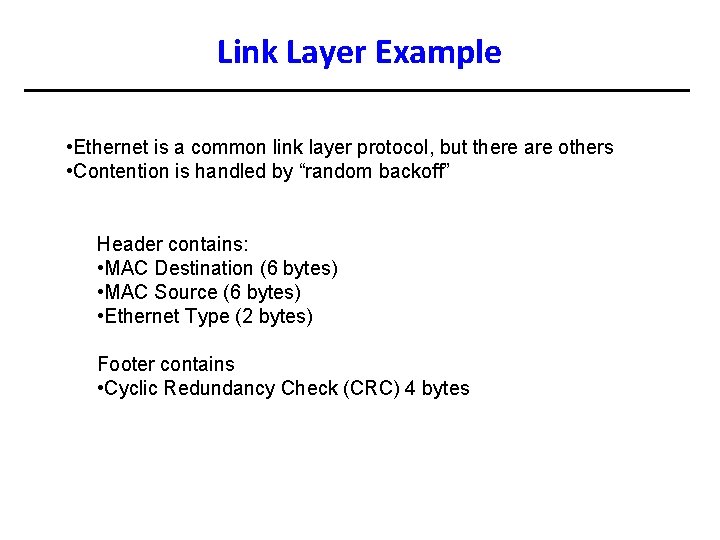
Link Layer Example • Ethernet is a common link layer protocol, but there are others • Contention is handled by “random backoff” Header contains: • MAC Destination (6 bytes) • MAC Source (6 bytes) • Ethernet Type (2 bytes) Footer contains • Cyclic Redundancy Check (CRC) 4 bytes

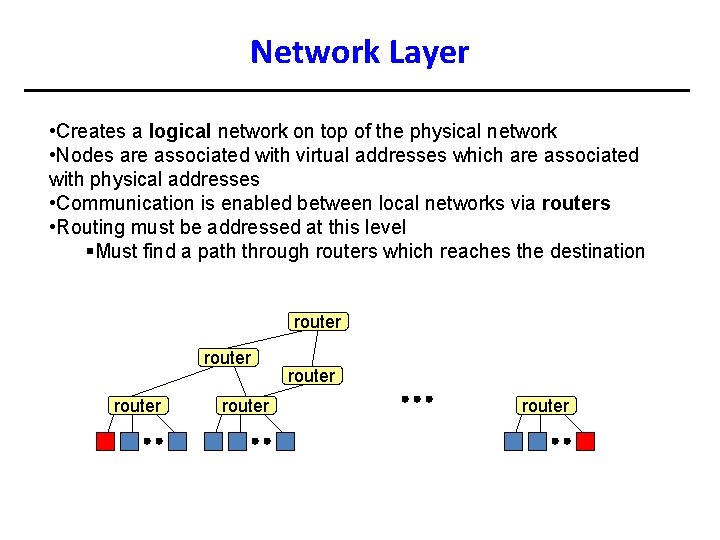
Network Layer • Creates a logical network on top of the physical network • Nodes are associated with virtual addresses which are associated with physical addresses • Communication is enabled between local networks via routers • Routing must be addressed at this level §Must find a path through routers which reaches the destination router router

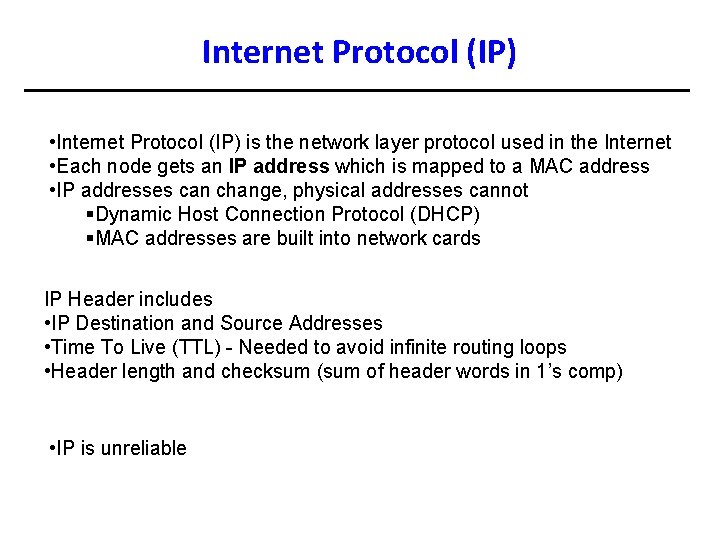
Internet Protocol (IP) • Internet Protocol (IP) is the network layer protocol used in the Internet • Each node gets an IP address which is mapped to a MAC address • IP addresses can change, physical addresses cannot §Dynamic Host Connection Protocol (DHCP) §MAC addresses are built into network cards IP Header includes • IP Destination and Source Addresses • Time To Live (TTL) - Needed to avoid infinite routing loops • Header length and checksum (sum of header words in 1’s comp) • IP is unreliable

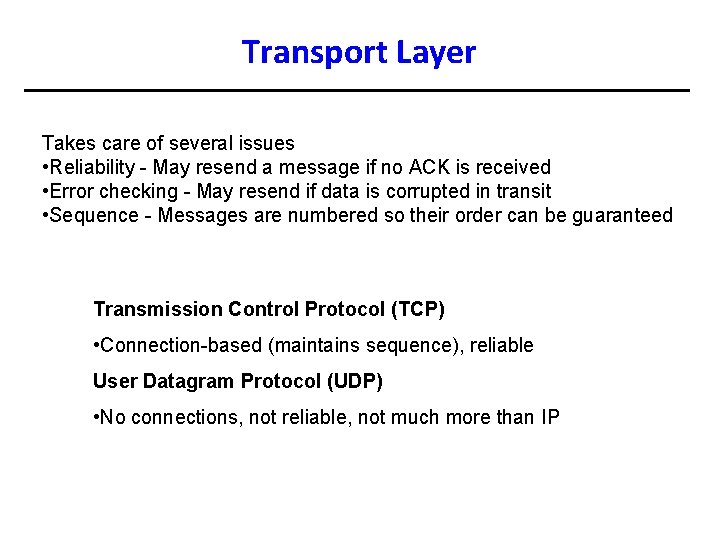
Transport Layer Takes care of several issues • Reliability - May resend a message if no ACK is received • Error checking - May resend if data is corrupted in transit • Sequence - Messages are numbered so their order can be guaranteed Transmission Control Protocol (TCP) • Connection-based (maintains sequence), reliable User Datagram Protocol (UDP) • No connections, not reliable, not much more than IP

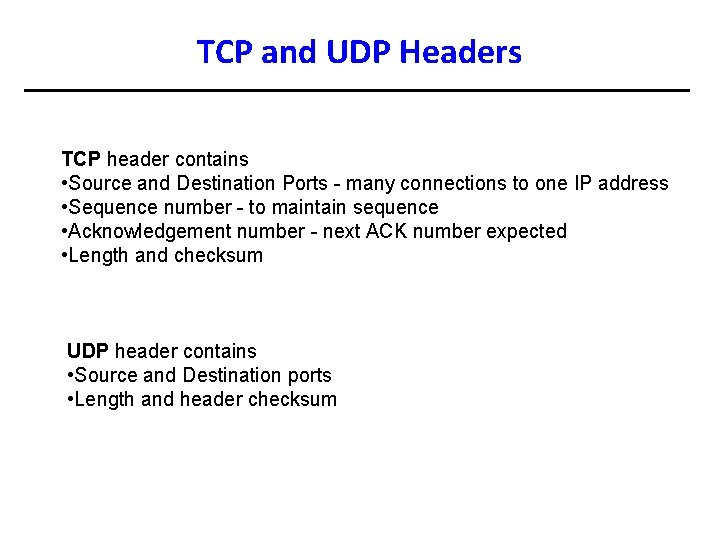
TCP and UDP Headers TCP header contains • Source and Destination Ports - many connections to one IP address • Sequence number - to maintain sequence • Acknowledgement number - next ACK number expected • Length and checksum UDP header contains • Source and Destination ports • Length and header checksum

Application Layer ØApplication-specific protocols • Hypertext Transfer Protocol (HTTP), Session Initiation Protocol (SIP), File Transfer Protocol (FTP), etc. • Seen by the programmer, should be human-readable • Headers contain application data ØDifferentiation between client and server • Client sends requests, server sends responses • Requests and responses differ in headers

HTTP Request Example • HTTP Request generated by going to www. mtv. com GET / HTTP/1. 1[CRLF] Host: www. mtv. com[CRLF] Connection: close[CRLF] User-Agent: Web-sniffer/1. 0. 27 (+http: //web-sniffer. net/)[CRLF] Accept-Encoding: gzip[CRLF] Accept-Charset: ISO-8859 -1, UTF-8; q=0. 7, *; q=0. 7[CRLF] Cache-Control: no[CRLF] Accept-Language: de, en; q=0. 7, en-us; q=0. 3[CRLF] Referer: http: //web-sniffer. net/[CRLF]

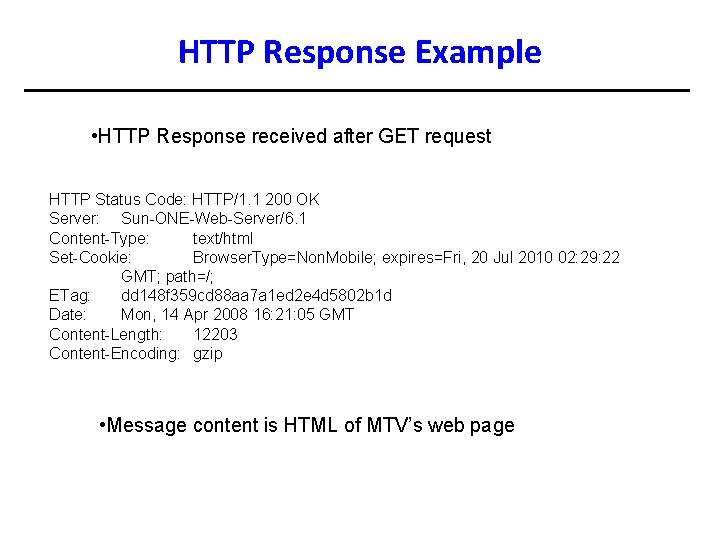
HTTP Response Example • HTTP Response received after GET request HTTP Status Code: HTTP/1. 1 200 OK Server: Sun-ONE-Web-Server/6. 1 Content-Type: text/html Set-Cookie: Browser. Type=Non. Mobile; expires=Fri, 20 Jul 2010 02: 29: 22 GMT; path=/; ETag: dd 148 f 359 cd 88 aa 7 a 1 ed 2 e 4 d 5802 b 1 d Date: Mon, 14 Apr 2008 16: 21: 05 GMT Content-Length: 12203 Content-Encoding: gzip • Message content is HTML of MTV’s web page