May 2020 doc IEEE 802 11 200710 r







![May 2020 doc. : IEEE 802. 11 -20/0710 r 1 References [1] Tianyu Wu, May 2020 doc. : IEEE 802. 11 -20/0710 r 1 References [1] Tianyu Wu,](https://slidetodoc.com/presentation_image_h2/4ec293b1e200d6975aa41e4629c54808/image-14.jpg)

- Slides: 15

May 2020 doc. : IEEE 802. 11 -20/0710 r 1 Attacks to Fully Random QPSK Sounding Signal Date: 2020 -05 -05 Submission Slide 1 Li, Jiang, et al. , Intel

. May 2020 doc. : IEEE 802. 11 -20/0710 r 1 Introduction • In some attack mode, it is assumed that the attacker has a ISI-free channel to the sounding transmitter. • Under this assumption, the existing 8 PSK-Golay secure sounding signal is vulnerable under brute force computational attacks and therefore fully random QPSK was proposed for secure ranging [1]. • In this contribution, we will show that the fully random QPSK is vulnerable and better protection is needed for future proof. Submission Slide 2 Li, Jiang, et al. , Intel

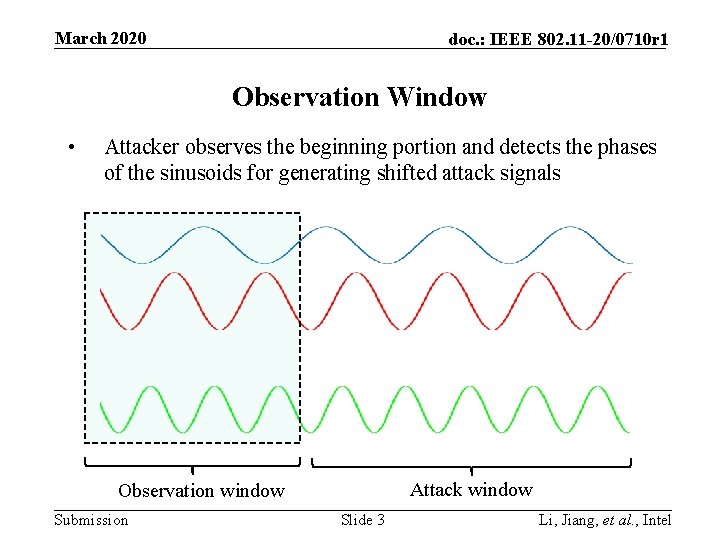
March 2020 doc. : IEEE 802. 11 -20/0710 r 1 Observation Window • Attacker observes the beginning portion and detects the phases of the sinusoids for generating shifted attack signals … Attack window Observation window Submission Slide 3 Li, Jiang, et al. , Intel

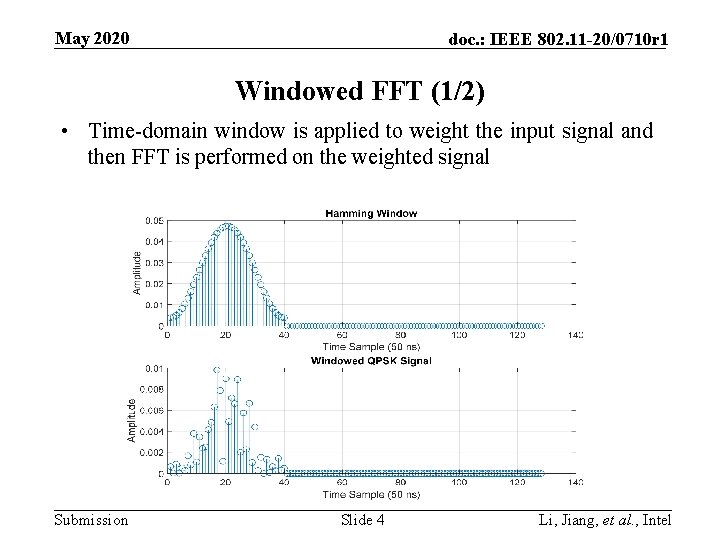
May 2020 doc. : IEEE 802. 11 -20/0710 r 1 Windowed FFT (1/2) • Time-domain window is applied to weight the input signal and then FFT is performed on the weighted signal Submission Slide 4 Li, Jiang, et al. , Intel

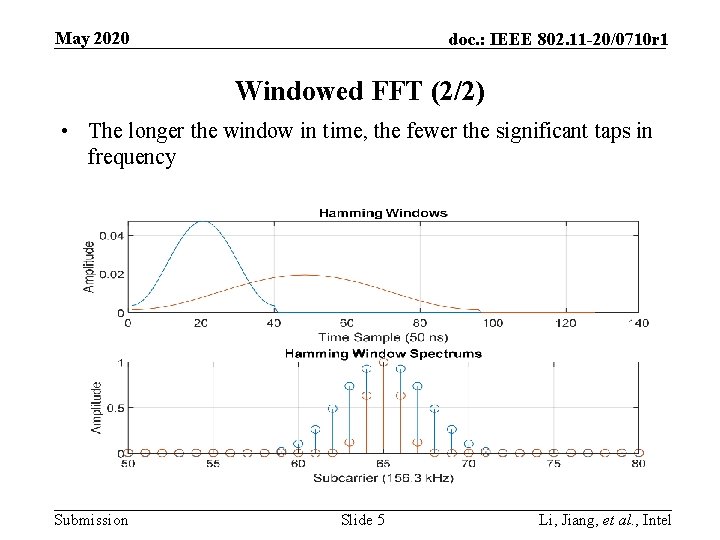
May 2020 doc. : IEEE 802. 11 -20/0710 r 1 Windowed FFT (2/2) • The longer the window in time, the fewer the significant taps in frequency Submission Slide 5 Li, Jiang, et al. , Intel

May 2020 doc. : IEEE 802. 11 -20/0710 r 1 Windowing in Time, ICI in Frequency • The time-domain windowing introduces inter-carrier interferences in frequency domain Submission Slide 6 Li, Jiang, et al. , Intel

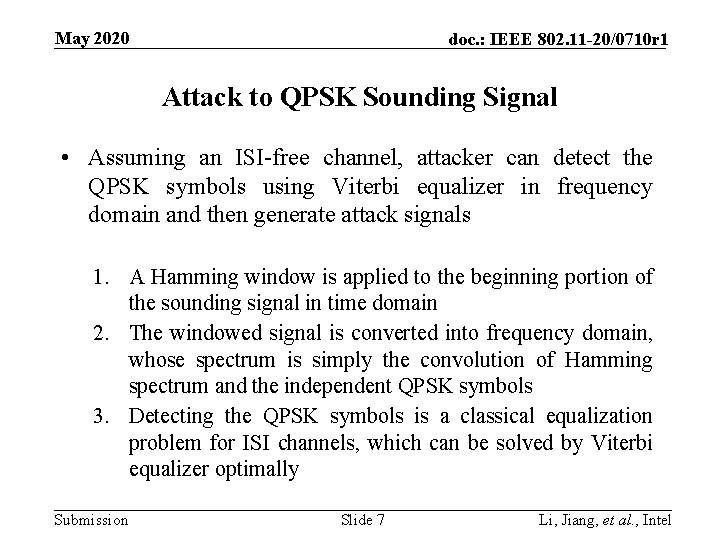
May 2020 doc. : IEEE 802. 11 -20/0710 r 1 Attack to QPSK Sounding Signal • Assuming an ISI-free channel, attacker can detect the QPSK symbols using Viterbi equalizer in frequency domain and then generate attack signals 1. A Hamming window is applied to the beginning portion of the sounding signal in time domain 2. The windowed signal is converted into frequency domain, whose spectrum is simply the convolution of Hamming spectrum and the independent QPSK symbols 3. Detecting the QPSK symbols is a classical equalization problem for ISI channels, which can be solved by Viterbi equalizer optimally Submission Slide 7 Li, Jiang, et al. , Intel

May 2020 doc. : IEEE 802. 11 -20/0710 r 1 Viterbi Equalizer • Almost the same as the Viterbi algorithm for convolutional code decoding except the operations are now in complex domain Each combination of the previous 4 symbols represents one of 28 states in the memory Current input symbol Sn Sn-1 w 0 Sn-2 w 1 w 2 w 3 + noise Submission Sn-4 Sn-3 rn Slide 8 w 4 Significant taps in Hamming spectrum Observed output symbol Li, Jiang, et al. , Intel

May 2020 doc. : IEEE 802. 11 -20/0710 r 1 Simulation Settings Submission Slide 9 Li, Jiang, et al. , Intel

May 2020 doc. : IEEE 802. 11 -20/0710 r 1 Bit detection rate > 0. 97 for ¼ cases Submission Slide 10 Li, Jiang, et al. , Intel

May 2020 doc. : IEEE 802. 11 -20/0710 r 1 Correlation Coefficient > 0. 94 for ¼ cases Submission Slide 11 Li, Jiang, et al. , Intel

May 2020 doc. : IEEE 802. 11 -20/0710 r 1 Remarks • Assuming ISI-free channels and observing about ¼ of the sounding, the attacker can know >94% of the remaining • The complexity is low ― Only 64 k Viterbi states. Using 64 M states, the observation window reduces down to 1/8 of the sounding ― Lower complexity detectors e. g. decision-feedback and LMMSE equalizers exist • Since the security relies on ICI in frequency domain, which only mixes the adjacent encryption bits, the attacker can detected the bits sequentially with a low complexity • Better protection is needed for future proof Submission Slide 12 Li, Jiang, et al. , Intel

May 2020 doc. : IEEE 802. 11 -20/0710 r 1 Conclusions • Under the assumption of ISI-free channels, QPSK fully random sounding signal can be broken with low complexities. Namely, the receiver will treats the attack signal as the 1 st arrival. • OFDM modulation is inherently sensitive to the presented attack with windowing and equalizer. Submission Slide 13 Li, Jiang, et al. , Intel
![May 2020 doc IEEE 802 11 200710 r 1 References 1 Tianyu Wu May 2020 doc. : IEEE 802. 11 -20/0710 r 1 References [1] Tianyu Wu,](https://slidetodoc.com/presentation_image_h2/4ec293b1e200d6975aa41e4629c54808/image-14.jpg)
May 2020 doc. : IEEE 802. 11 -20/0710 r 1 References [1] Tianyu Wu, et al. , IEEE 802. 11 -20/0375 r 1, Mar. 2020 Submission Slide 14 Li, Jiang, et al. , Intel

May 2020 doc. : IEEE 802. 11 -20/0710 r 1 Backup Slides Submission Slide 15 Li, Jiang, et al. , Intel