May 2003 doc IEEE 802 11 03241 r



- Slides: 17

May 2003 doc. : IEEE 802. 11 -03/241 r 3 Fast Roaming Compromise Proposal Tim Moore, Microsoft Nancy Cam-Winget, Cisco Systems Clint Chaplin, Symbol Technologies Donald Eastlake, Motorola Laboratories Dan Harkins, Trapeze Networks Russ Housley, Vigil Security Fred Stivers, Texas Instruments Jesse Walker, Intel Submission 1 Cam-Winget et. al.

May 2003 doc. : IEEE 802. 11 -03/241 r 3 Voice Requirements for reassociation – ITU guidance on TOTAL hand-off latency is that it should be less than 50 ms. Cellular networks try to keep it less than 35 ms. Submission 2 Cam-Winget et. al.

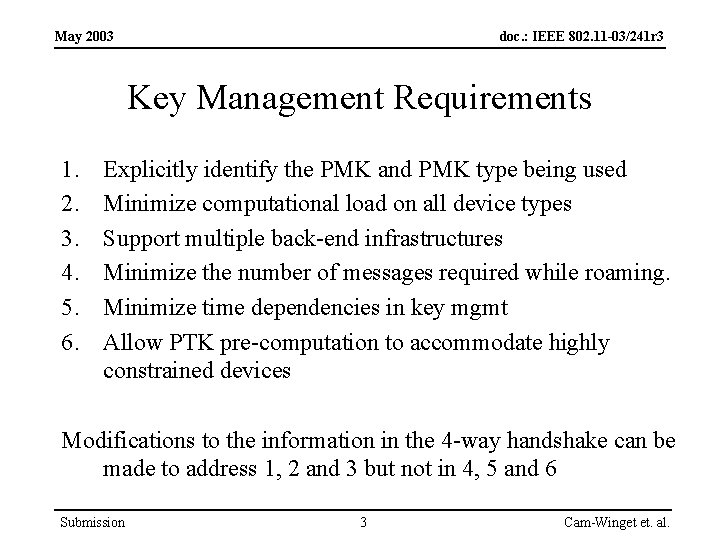
May 2003 doc. : IEEE 802. 11 -03/241 r 3 Key Management Requirements 1. 2. 3. 4. 5. 6. Explicitly identify the PMK and PMK type being used Minimize computational load on all device types Support multiple back-end infrastructures Minimize the number of messages required while roaming. Minimize time dependencies in key mgmt Allow PTK pre-computation to accommodate highly constrained devices Modifications to the information in the 4 -way handshake can be made to address 1, 2 and 3 but not in 4, 5 and 6 Submission 3 Cam-Winget et. al.

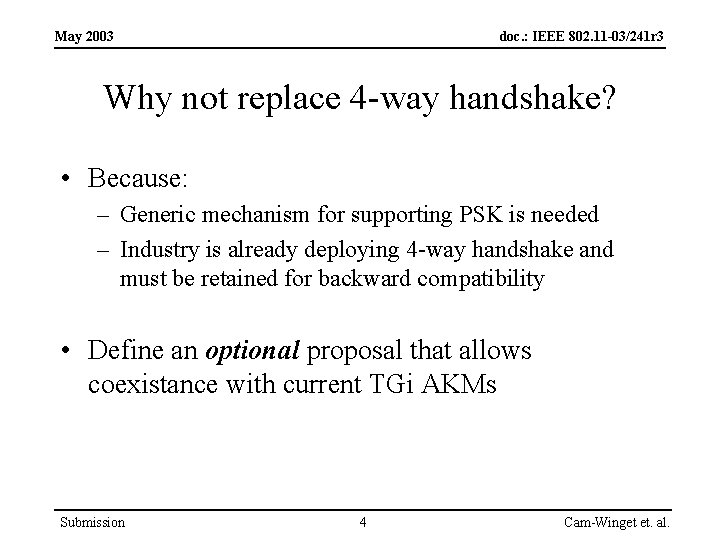
May 2003 doc. : IEEE 802. 11 -03/241 r 3 Why not replace 4 -way handshake? • Because: – Generic mechanism for supporting PSK is needed – Industry is already deploying 4 -way handshake and must be retained for backward compatibility • Define an optional proposal that allows coexistance with current TGi AKMs Submission 4 Cam-Winget et. al.

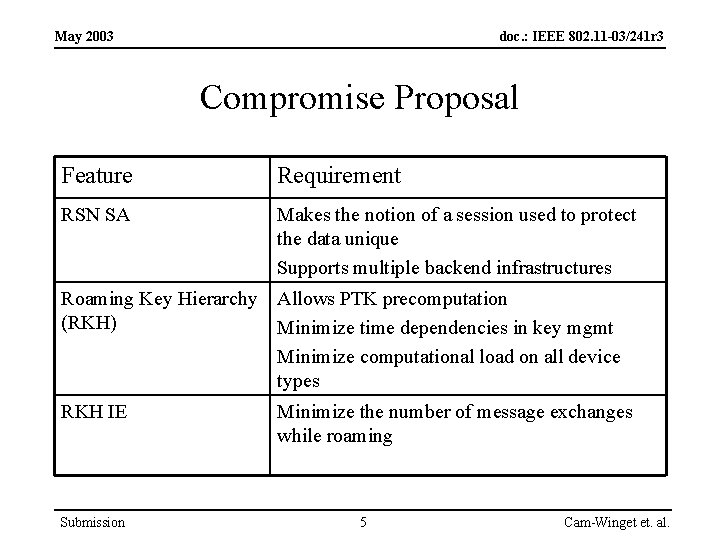
May 2003 doc. : IEEE 802. 11 -03/241 r 3 Compromise Proposal Feature Requirement RSN SA Makes the notion of a session used to protect the data unique Supports multiple backend infrastructures Roaming Key Hierarchy Allows PTK precomputation (RKH) Minimize time dependencies in key mgmt Minimize computational load on all device types RKH IE Submission Minimize the number of message exchanges while roaming 5 Cam-Winget et. al.

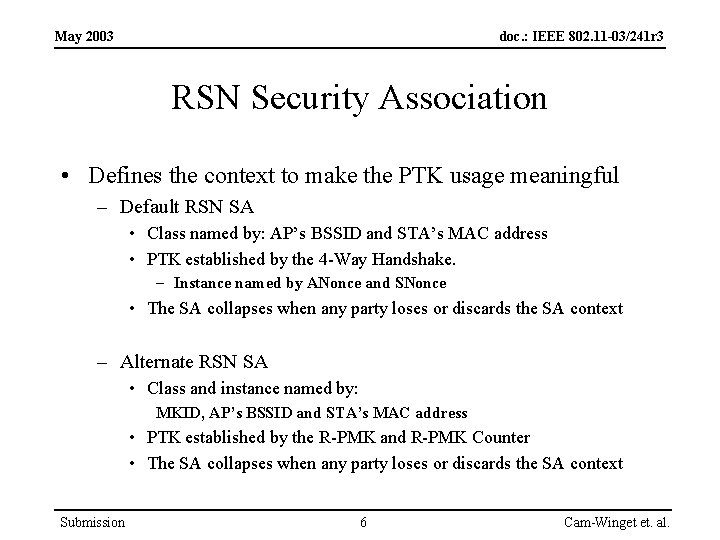
May 2003 doc. : IEEE 802. 11 -03/241 r 3 RSN Security Association • Defines the context to make the PTK usage meaningful – Default RSN SA • Class named by: AP’s BSSID and STA’s MAC address • PTK established by the 4 -Way Handshake. – Instance named by ANonce and SNonce • The SA collapses when any party loses or discards the SA context – Alternate RSN SA • Class and instance named by: MKID, AP’s BSSID and STA’s MAC address • PTK established by the R-PMK and R-PMK Counter • The SA collapses when any party loses or discards the SA context Submission 6 Cam-Winget et. al.

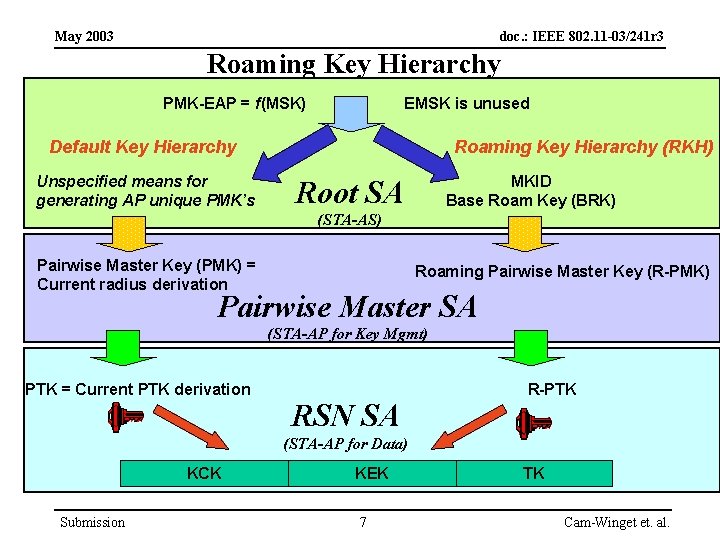
May 2003 doc. : IEEE 802. 11 -03/241 r 3 Roaming Key Hierarchy PMK-EAP = f(MSK) EMSK is unused Default Key Hierarchy Unspecified means for generating AP unique PMK’s Roaming Key Hierarchy (RKH) MKID Base Roam Key (BRK) Root SA (STA-AS) Pairwise Master Key (PMK) = Current radius derivation Roaming Pairwise Master Key (R-PMK) Pairwise Master SA (STA-AP for Key Mgmt) PTK = Current PTK derivation RSN SA R-PTK (STA-AP for Data) KCK Submission KEK 7 TK Cam-Winget et. al.

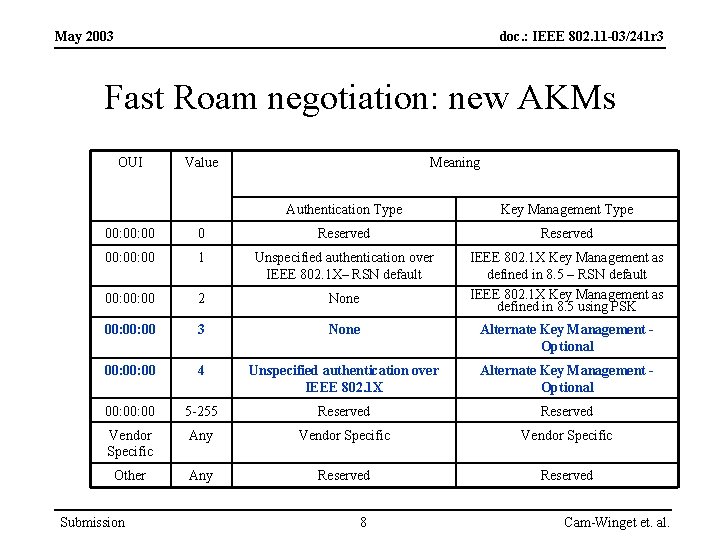
May 2003 doc. : IEEE 802. 11 -03/241 r 3 Fast Roam negotiation: new AKMs OUI Value Meaning Authentication Type Key Management Type 00: 00 0 Reserved 00: 00 1 Unspecified authentication over IEEE 802. 1 X– RSN default 00: 00 2 None IEEE 802. 1 X Key Management as defined in 8. 5 – RSN default IEEE 802. 1 X Key Management as defined in 8. 5 using PSK 00: 00 3 None Alternate Key Management Optional 00: 00 4 Unspecified authentication over IEEE 802. 1 X Alternate Key Management Optional 00: 00 5 -255 Reserved Vendor Specific Any Vendor Specific Other Any Reserved Submission 8 Cam-Winget et. al.

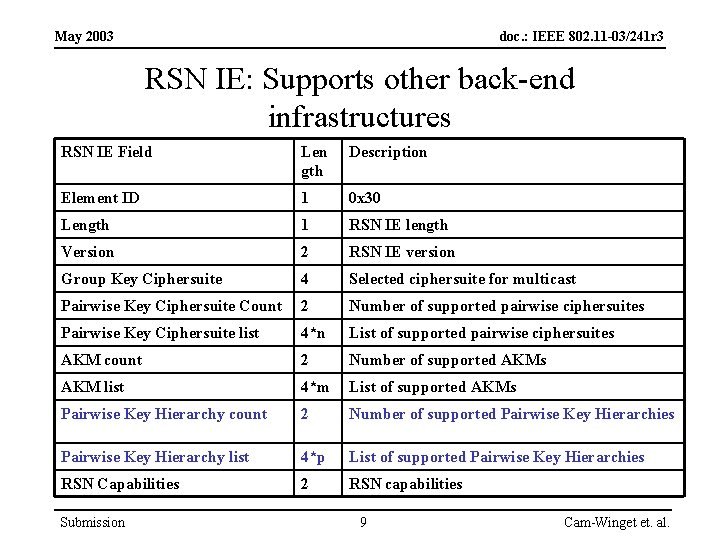
May 2003 doc. : IEEE 802. 11 -03/241 r 3 RSN IE: Supports other back-end infrastructures RSN IE Field Len gth Description Element ID 1 0 x 30 Length 1 RSN IE length Version 2 RSN IE version Group Key Ciphersuite 4 Selected ciphersuite for multicast Pairwise Key Ciphersuite Count 2 Number of supported pairwise ciphersuites Pairwise Key Ciphersuite list 4*n List of supported pairwise ciphersuites AKM count 2 Number of supported AKMs AKM list 4*m List of supported AKMs Pairwise Key Hierarchy count 2 Number of supported Pairwise Key Hierarchies Pairwise Key Hierarchy list 4*p List of supported Pairwise Key Hierarchies RSN Capabilities 2 RSN capabilities Submission 9 Cam-Winget et. al.

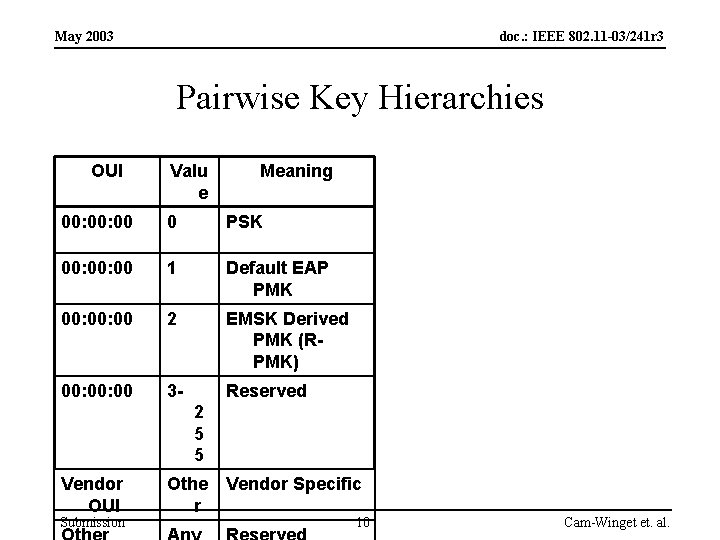
May 2003 doc. : IEEE 802. 11 -03/241 r 3 Pairwise Key Hierarchies OUI Valu e Meaning 00: 00 0 PSK 00: 00 1 Default EAP PMK 00: 00 2 EMSK Derived PMK (RPMK) 00: 00 3 - Reserved 2 5 5 Vendor OUI Submission Othe Vendor Specific r 10 Cam-Winget et. al.

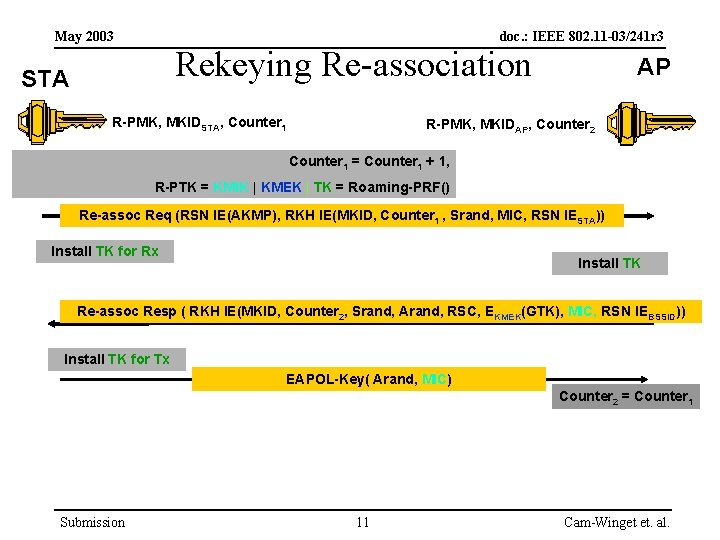
May 2003 doc. : IEEE 802. 11 -03/241 r 3 Rekeying Re-association STA R-PMK, MKIDSTA, Counter 1 AP R-PMK, MKIDAP, Counter 2 Counter 1 = Counter 1 + 1, R-PTK = KMIK | KMEK | TK = Roaming-PRF() Re-assoc Req (RSN IE(AKMP), RKH IE(MKID, Counter 1 , Srand, MIC, RSN IESTA)) Install TK for Rx Install TK Re-assoc Resp ( RKH IE(MKID, Counter 2, Srand, Arand, RSC, EKMEK(GTK), MIC, RSN IEBSSID)) Install TK for Tx EAPOL-Key( Arand, MIC) Counter 2 = Counter 1 Submission 11 Cam-Winget et. al.

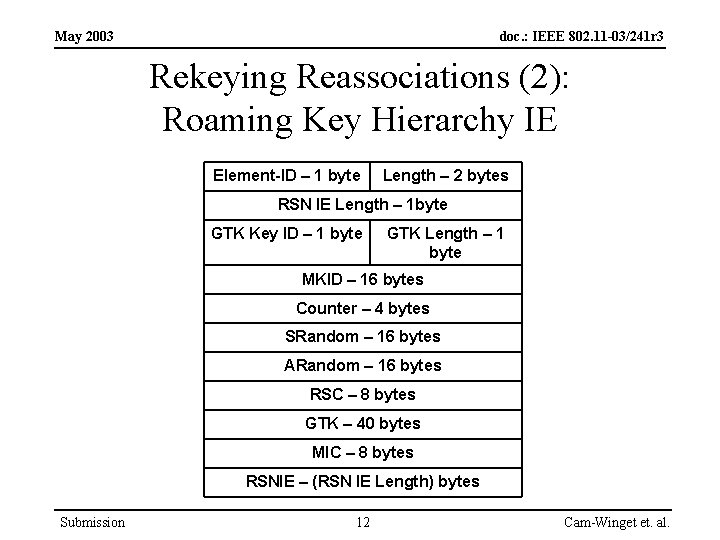
May 2003 doc. : IEEE 802. 11 -03/241 r 3 Rekeying Reassociations (2): Roaming Key Hierarchy IE Element-ID – 1 byte Length – 2 bytes RSN IE Length – 1 byte GTK Key ID – 1 byte GTK Length – 1 byte MKID – 16 bytes Counter – 4 bytes SRandom – 16 bytes ARandom – 16 bytes RSC – 8 bytes GTK – 40 bytes MIC – 8 bytes RSNIE – (RSN IE Length) bytes Submission 12 Cam-Winget et. al.

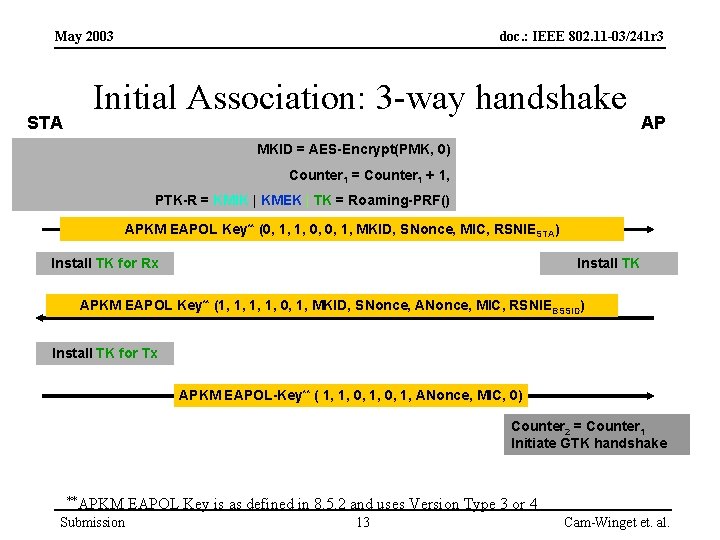
May 2003 STA doc. : IEEE 802. 11 -03/241 r 3 Initial Association: 3 -way handshake AP MKID = AES-Encrypt(PMK, 0) Counter 1 = Counter 1 + 1, PTK-R = KMIK | KMEK | TK = Roaming-PRF() APKM EAPOL Key** (0, 1, 1, 0, 0, 1, MKID, SNonce, MIC, RSNIESTA) Install TK for Rx Install TK APKM EAPOL Key** (1, 1, 0, 1, MKID, SNonce, ANonce, MIC, RSNIEBSSID) Install TK for Tx APKM EAPOL-Key** ( 1, 1, 0, 1, ANonce, MIC, 0) Counter 2 = Counter 1 Initiate GTK handshake **APKM Submission EAPOL Key is as defined in 8. 5. 2 and uses Version Type 3 or 4 13 Cam-Winget et. al.

May 2003 doc. : IEEE 802. 11 -03/241 r 3 Supports Push and Pull Models • In either Initial Contact or Roam: – If the AP does not have the RSN SA, it can contact the AS to establish it – Through prediction, the AP – AS can establish the RSN SA before the STA attempts reassociation Submission 14 Cam-Winget et. al.

May 2003 doc. : IEEE 802. 11 -03/241 r 3 Motions • Move to adopt draft text in 03/241 r 3 • Move to request IEEE 802. 11 Working Group Chair to forward the letter 03/361 titled “Input to IETF AAA Working Group on Keying Distribution Methods” to the IETF Chair Submission 15 Cam-Winget et. al.

May 2003 doc. : IEEE 802. 11 -03/241 r 3 Feedback? Submission 16 Cam-Winget et. al.

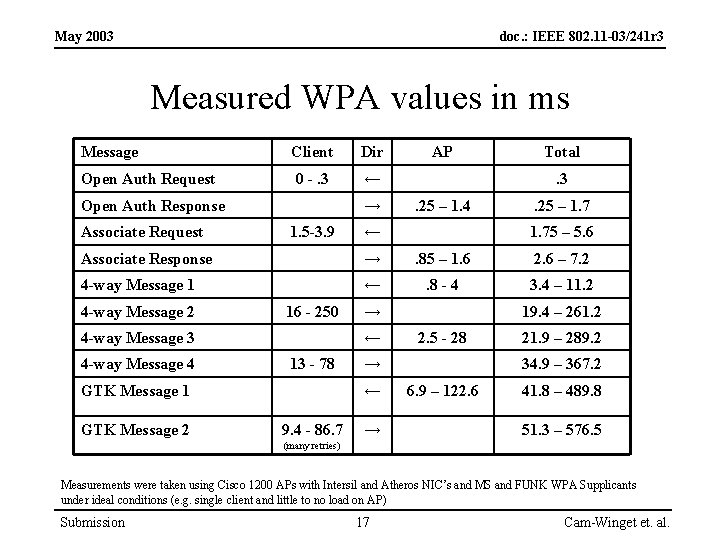
May 2003 doc. : IEEE 802. 11 -03/241 r 3 Measured WPA values in ms Message Client Dir Open Auth Request 0 -. 3 ← Open Auth Response Associate Request → 1. 5 -3. 9 AP Total. 3 . 25 – 1. 4 ← . 25 – 1. 75 – 5. 6 Associate Response → . 85 – 1. 6 2. 6 – 7. 2 4 -way Message 1 ← . 8 - 4 3. 4 – 11. 2 4 -way Message 2 16 - 250 4 -way Message 3 4 -way Message 4 ← 13 - 78 GTK Message 1 GTK Message 2 → 2. 5 - 28 → ← 9. 4 - 86. 7 19. 4 – 261. 2 → 21. 9 – 289. 2 34. 9 – 367. 2 6. 9 – 122. 6 41. 8 – 489. 8 51. 3 – 576. 5 (many retries) Measurements were taken using Cisco 1200 APs with Intersil and Atheros NIC’s and MS and FUNK WPA Supplicants under ideal conditions (e. g. single client and little to no load on AP) Submission 17 Cam-Winget et. al.