Killian CSCI 380 Millersville University Dynamic Memory Allocation





- Slides: 33

Killian – CSCI 380 – Millersville University Dynamic Memory Allocation: Basic Concepts CSCI 380: Operating Systems Instructor: William Killian Bryant and O’Hallaron, Computer Systems: A Programmer’s Perspective, Third Edition 1

Killian – CSCI 380 – Millersville University Today ¢ ¢ Basic concepts Implicit free lists Bryant and O’Hallaron, Computer Systems: A Programmer’s Perspective, Third Edition 2

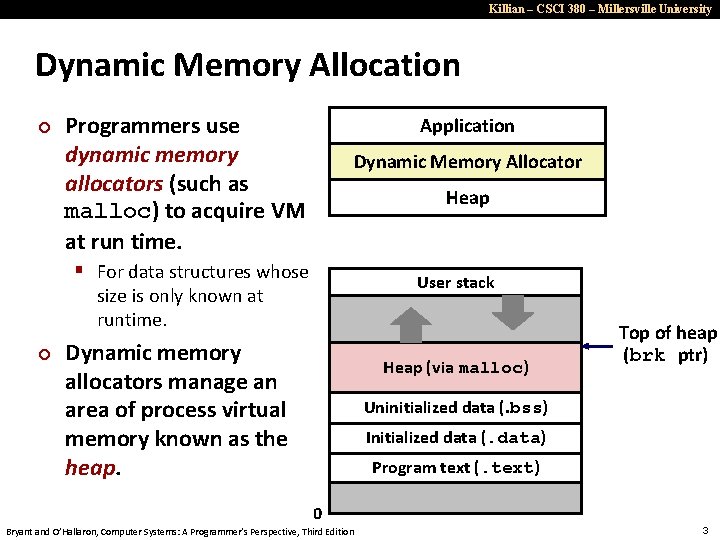
Killian – CSCI 380 – Millersville University Dynamic Memory Allocation ¢ Programmers use dynamic memory allocators (such as malloc) to acquire VM at run time. Application Dynamic Memory Allocator Heap § For data structures whose User stack size is only known at runtime. ¢ Dynamic memory allocators manage an area of process virtual memory known as the heap. Heap (via malloc) Top of heap (brk ptr) Uninitialized data (. bss) Initialized data (. data) Program text (. text) 0 Bryant and O’Hallaron, Computer Systems: A Programmer’s Perspective, Third Edition 3

Killian – CSCI 380 – Millersville University Dynamic Memory Allocation ¢ ¢ Allocator maintains heap as collection of variable sized blocks, which are either allocated or free Types of allocators § Explicit allocator: application allocates and frees space E. g. , malloc and free in C § Implicit allocator: application allocates, but does not free space § E. g. garbage collection in Java, ML, and Lisp § ¢ Will discuss simple explicit memory allocation today Bryant and O’Hallaron, Computer Systems: A Programmer’s Perspective, Third Edition 4

Killian – CSCI 380 – Millersville University The malloc Package #include <stdlib. h> void *malloc(size_t size) § Successful: § Returns a pointer to a memory block of at least size bytes aligned to an 8 -byte (x 86) or 16 -byte (x 86 -64) boundary § If size == 0, returns NULL § Unsuccessful: returns NULL (0) and sets errno void free(void *p) § Returns the block pointed at by p to pool of available memory § p must come from a previous call to malloc or realloc Other functions § calloc: Version of malloc that initializes allocated block to zero. § realloc: Changes the size of a previously allocated block. § sbrk: Used internally by allocators to grow or shrink the heap Bryant and O’Hallaron, Computer Systems: A Programmer’s Perspective, Third Edition 5

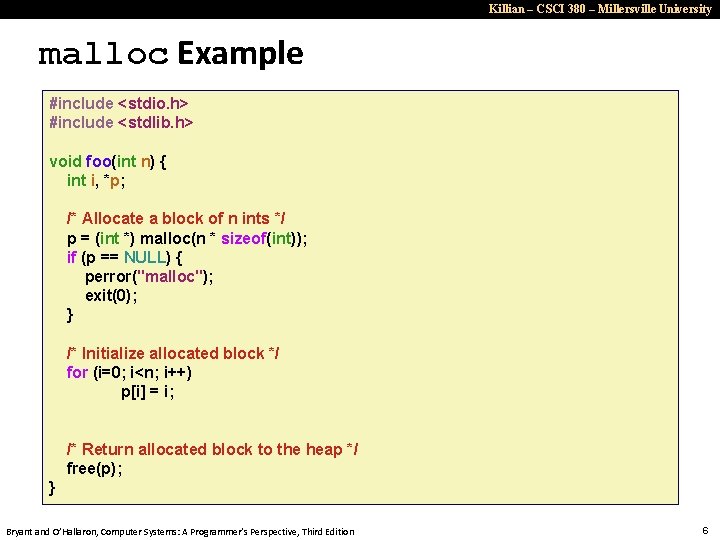
Killian – CSCI 380 – Millersville University malloc Example #include <stdio. h> #include <stdlib. h> void foo(int n) { int i, *p; /* Allocate a block of n ints */ p = (int *) malloc(n * sizeof(int)); if (p == NULL) { perror("malloc"); exit(0); } /* Initialize allocated block */ for (i=0; i<n; i++) p[i] = i; /* Return allocated block to the heap */ free(p); } Bryant and O’Hallaron, Computer Systems: A Programmer’s Perspective, Third Edition 6

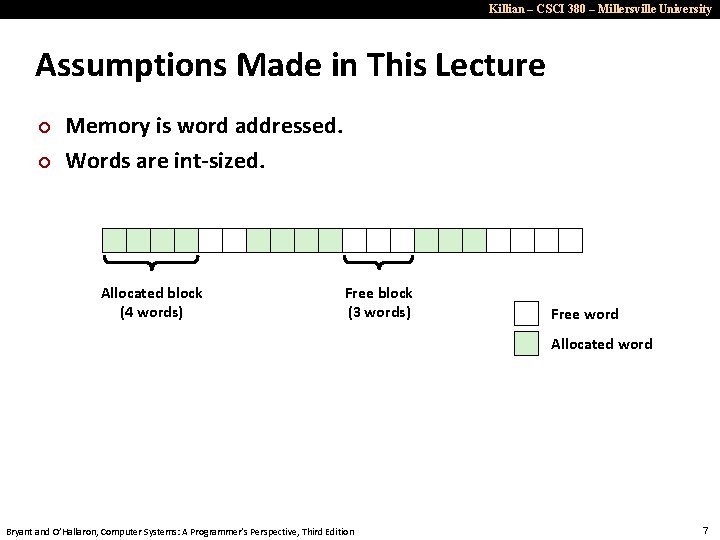
Killian – CSCI 380 – Millersville University Assumptions Made in This Lecture ¢ ¢ Memory is word addressed. Words are int-sized. Allocated block (4 words) Free block (3 words) Free word Allocated word Bryant and O’Hallaron, Computer Systems: A Programmer’s Perspective, Third Edition 7

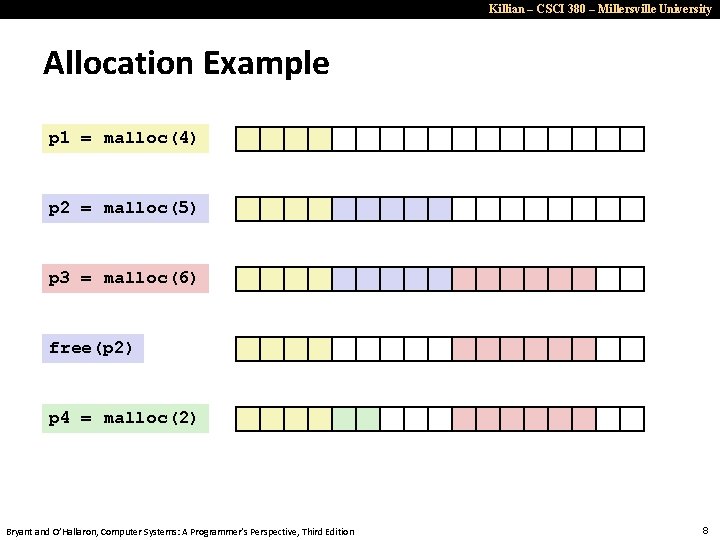
Killian – CSCI 380 – Millersville University Allocation Example p 1 = malloc(4) p 2 = malloc(5) p 3 = malloc(6) free(p 2) p 4 = malloc(2) Bryant and O’Hallaron, Computer Systems: A Programmer’s Perspective, Third Edition 8

Killian – CSCI 380 – Millersville University Constraints ¢ Applications § Can issue arbitrary sequence of malloc and free requests § free request must be to a malloc’d block ¢ Allocators § Can’t control number or size of allocated blocks § Must respond immediately to malloc requests i. e. , can’t reorder or buffer requests Must allocate blocks from free memory § i. e. , can only place allocated blocks in free memory Must align blocks so they satisfy all alignment requirements § 8 -byte (x 86) or 16 -byte (x 86 -64) alignment on Linux boxes Can manipulate and modify only free memory Can’t move the allocated blocks once they are malloc’d § i. e. , compaction is not allowed § § § Bryant and O’Hallaron, Computer Systems: A Programmer’s Perspective, Third Edition 9

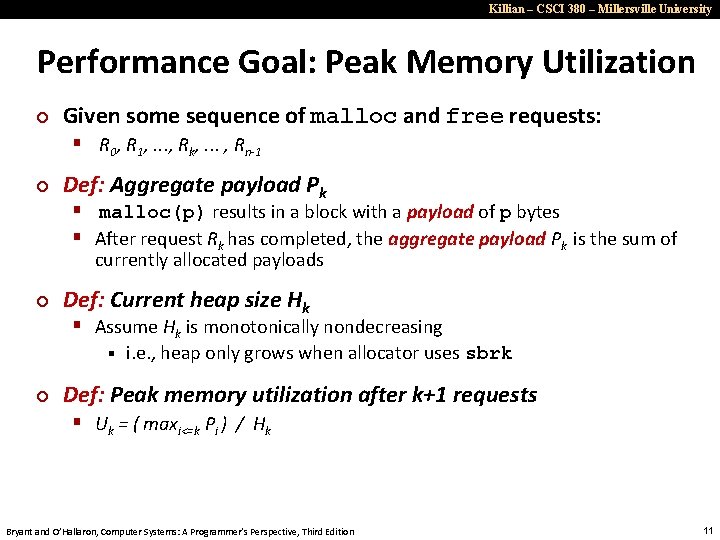
Killian – CSCI 380 – Millersville University Performance Goal: Throughput ¢ Given some sequence of malloc and free requests: § R 0, R 1, . . . , Rk, . . . , Rn-1 ¢ Goals: maximize throughput and peak memory utilization § These goals are often conflicting ¢ Throughput: § Number of completed requests per unit time § Example: 5, 000 malloc calls and 5, 000 free calls in 10 seconds § Throughput is 1, 000 operations/second § Bryant and O’Hallaron, Computer Systems: A Programmer’s Perspective, Third Edition 10

Killian – CSCI 380 – Millersville University Performance Goal: Peak Memory Utilization ¢ Given some sequence of malloc and free requests: § R 0, R 1, . . . , Rk, . . . , Rn-1 ¢ Def: Aggregate payload Pk § malloc(p) results in a block with a payload of p bytes § After request Rk has completed, the aggregate payload Pk is the sum of currently allocated payloads ¢ Def: Current heap size Hk § Assume Hk is monotonically nondecreasing § ¢ i. e. , heap only grows when allocator uses sbrk Def: Peak memory utilization after k+1 requests § Uk = ( maxi<=k Pi ) / Hk Bryant and O’Hallaron, Computer Systems: A Programmer’s Perspective, Third Edition 11

Killian – CSCI 380 – Millersville University Fragmentation ¢ Poor memory utilization caused by fragmentation § internal fragmentation § external fragmentation Bryant and O’Hallaron, Computer Systems: A Programmer’s Perspective, Third Edition 12

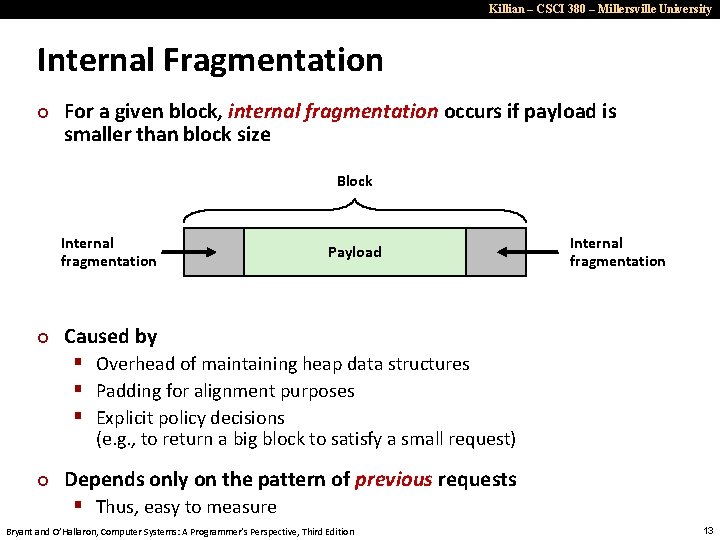
Killian – CSCI 380 – Millersville University Internal Fragmentation ¢ For a given block, internal fragmentation occurs if payload is smaller than block size Block Internal fragmentation ¢ Payload Internal fragmentation Caused by § Overhead of maintaining heap data structures § Padding for alignment purposes § Explicit policy decisions (e. g. , to return a big block to satisfy a small request) ¢ Depends only on the pattern of previous requests § Thus, easy to measure Bryant and O’Hallaron, Computer Systems: A Programmer’s Perspective, Third Edition 13

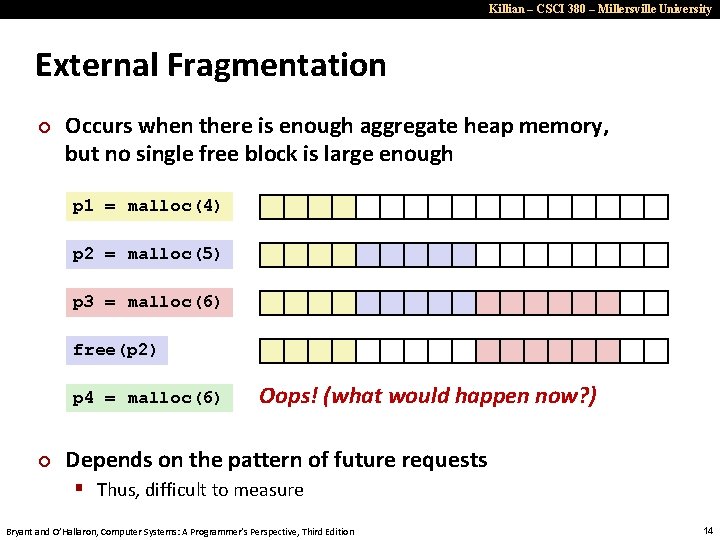
Killian – CSCI 380 – Millersville University External Fragmentation ¢ Occurs when there is enough aggregate heap memory, but no single free block is large enough p 1 = malloc(4) p 2 = malloc(5) p 3 = malloc(6) free(p 2) p 4 = malloc(6) ¢ Oops! (what would happen now? ) Depends on the pattern of future requests § Thus, difficult to measure Bryant and O’Hallaron, Computer Systems: A Programmer’s Perspective, Third Edition 14

Killian – CSCI 380 – Millersville University Implementation Issues ¢ ¢ ¢ How do we know how much memory to free given just a pointer? How do we keep track of the free blocks? What do we do with the extra space when allocating a structure that is smaller than the free block it is placed in? How do we pick a block to use for allocation -- many might fit? How do we reinsert freed block? Bryant and O’Hallaron, Computer Systems: A Programmer’s Perspective, Third Edition 15

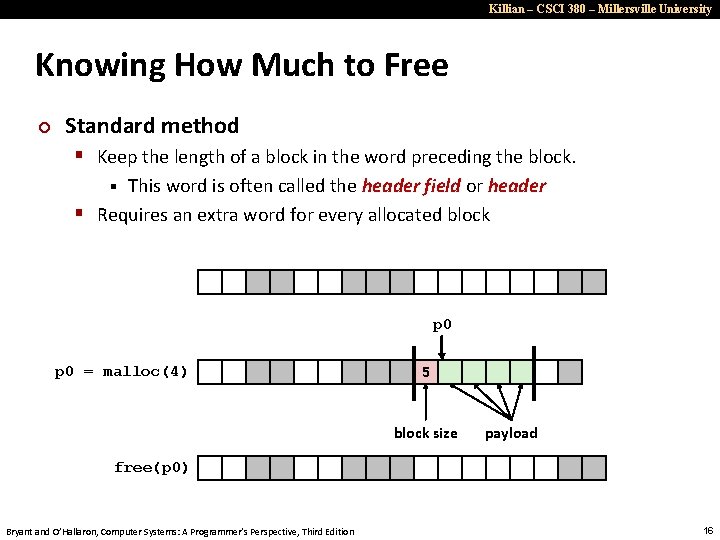
Killian – CSCI 380 – Millersville University Knowing How Much to Free ¢ Standard method § Keep the length of a block in the word preceding the block. This word is often called the header field or header § Requires an extra word for every allocated block § p 0 = malloc(4) 5 block size payload free(p 0) Bryant and O’Hallaron, Computer Systems: A Programmer’s Perspective, Third Edition 16

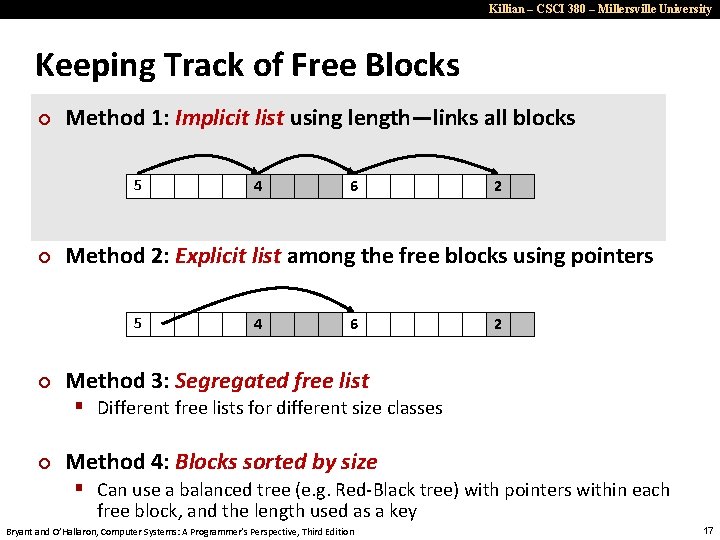
Killian – CSCI 380 – Millersville University Keeping Track of Free Blocks ¢ Method 1: Implicit list using length—links all blocks 5 ¢ 6 2 Method 2: Explicit list among the free blocks using pointers 5 ¢ 4 4 6 2 Method 3: Segregated free list § Different free lists for different size classes ¢ Method 4: Blocks sorted by size § Can use a balanced tree (e. g. Red-Black tree) with pointers within each free block, and the length used as a key Bryant and O’Hallaron, Computer Systems: A Programmer’s Perspective, Third Edition 17

Killian – CSCI 380 – Millersville University Today ¢ ¢ Basic concepts Implicit free lists Bryant and O’Hallaron, Computer Systems: A Programmer’s Perspective, Third Edition 18

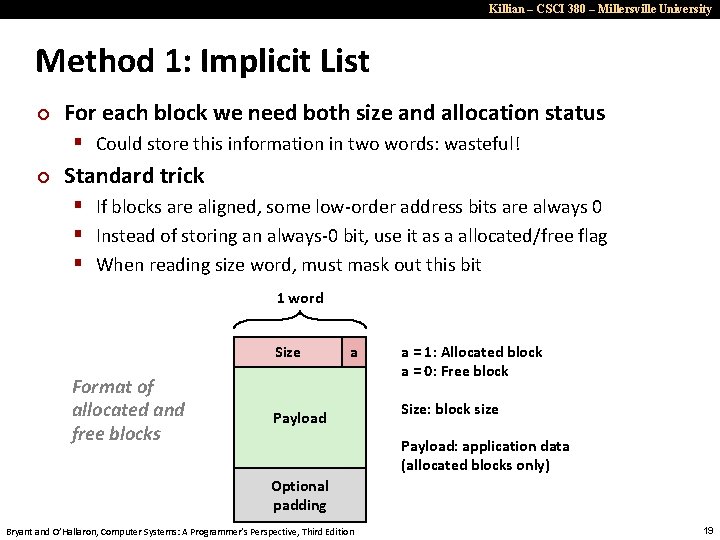
Killian – CSCI 380 – Millersville University Method 1: Implicit List ¢ For each block we need both size and allocation status § Could store this information in two words: wasteful! ¢ Standard trick § If blocks are aligned, some low-order address bits are always 0 § Instead of storing an always-0 bit, use it as a allocated/free flag § When reading size word, must mask out this bit 1 word Size Format of allocated and free blocks a Payload a = 1: Allocated block a = 0: Free block Size: block size Payload: application data (allocated blocks only) Optional padding Bryant and O’Hallaron, Computer Systems: A Programmer’s Perspective, Third Edition 19

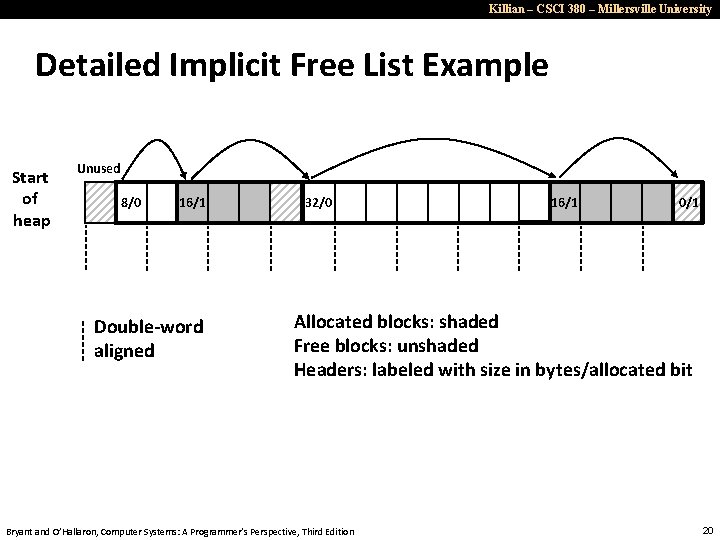
Killian – CSCI 380 – Millersville University Detailed Implicit Free List Example Start of heap Unused 8/0 16/1 Double-word aligned 32/0 16/1 0/1 Allocated blocks: shaded Free blocks: unshaded Headers: labeled with size in bytes/allocated bit Bryant and O’Hallaron, Computer Systems: A Programmer’s Perspective, Third Edition 20

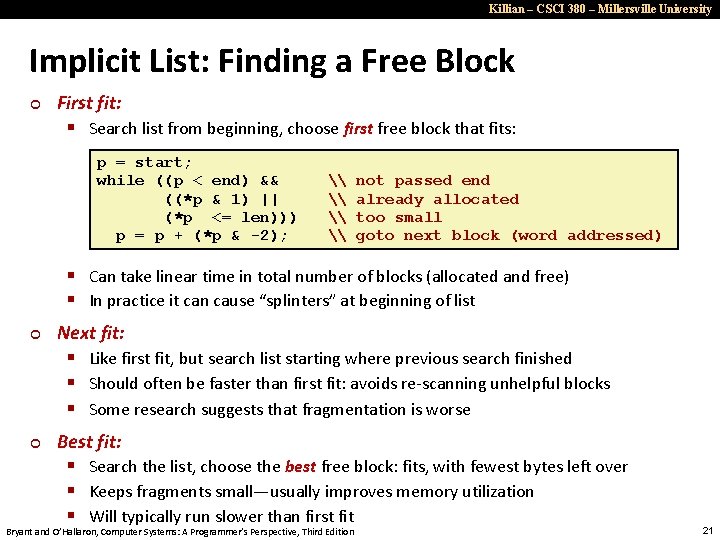
Killian – CSCI 380 – Millersville University Implicit List: Finding a Free Block ¢ First fit: § Search list from beginning, choose first free block that fits: p = start; while ((p < end) && ((*p & 1) || (*p <= len))) p = p + (*p & -2); \ \ not passed end already allocated too small goto next block (word addressed) § Can take linear time in total number of blocks (allocated and free) § In practice it can cause “splinters” at beginning of list ¢ ¢ Next fit: § Like first fit, but search list starting where previous search finished § Should often be faster than first fit: avoids re-scanning unhelpful blocks § Some research suggests that fragmentation is worse Best fit: § Search the list, choose the best free block: fits, with fewest bytes left over § Keeps fragments small—usually improves memory utilization § Will typically run slower than first fit Bryant and O’Hallaron, Computer Systems: A Programmer’s Perspective, Third Edition 21

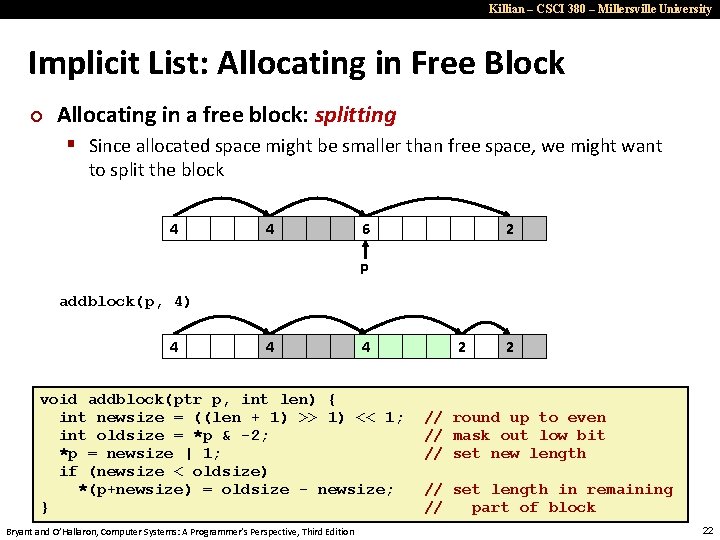
Killian – CSCI 380 – Millersville University Implicit List: Allocating in Free Block ¢ Allocating in a free block: splitting § Since allocated space might be smaller than free space, we might want to split the block 4 4 6 2 p addblock(p, 4) 4 4 4 void addblock(ptr p, int len) { int newsize = ((len + 1) >> 1) << 1; int oldsize = *p & -2; *p = newsize | 1; if (newsize < oldsize) *(p+newsize) = oldsize - newsize; } Bryant and O’Hallaron, Computer Systems: A Programmer’s Perspective, Third Edition 2 2 // round up to even // mask out low bit // set new length // set length in remaining // part of block 22

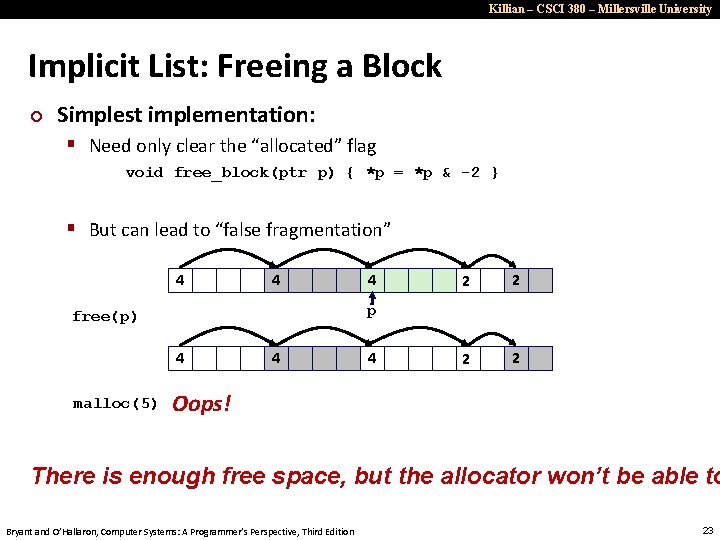
Killian – CSCI 380 – Millersville University Implicit List: Freeing a Block ¢ Simplest implementation: § Need only clear the “allocated” flag void free_block(ptr p) { *p = *p & -2 } § But can lead to “false fragmentation” 4 4 2 2 p free(p) 4 malloc(5) 4 4 4 Oops! There is enough free space, but the allocator won’t be able to Bryant and O’Hallaron, Computer Systems: A Programmer’s Perspective, Third Edition 23

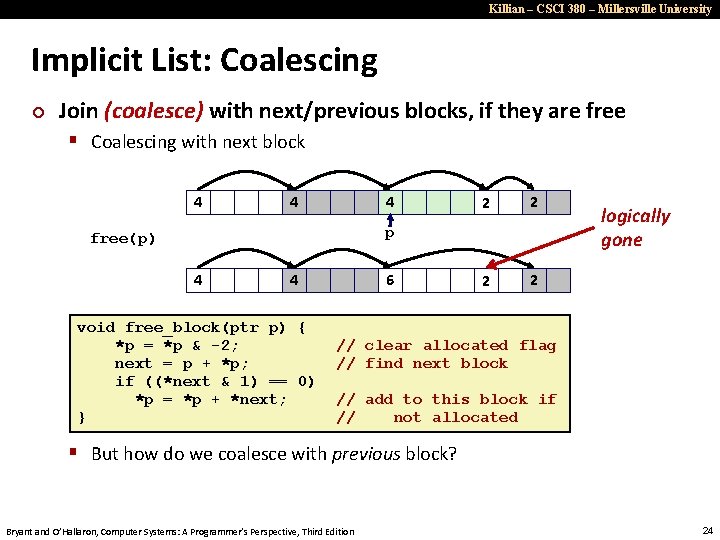
Killian – CSCI 380 – Millersville University Implicit List: Coalescing ¢ Join (coalesce) with next/previous blocks, if they are free § Coalescing with next block 4 4 4 2 2 p free(p) 4 4 void free_block(ptr p) { *p = *p & -2; next = p + *p; if ((*next & 1) == 0) *p = *p + *next; } 6 logically gone // clear allocated flag // find next block // add to this block if // not allocated § But how do we coalesce with previous block? Bryant and O’Hallaron, Computer Systems: A Programmer’s Perspective, Third Edition 24

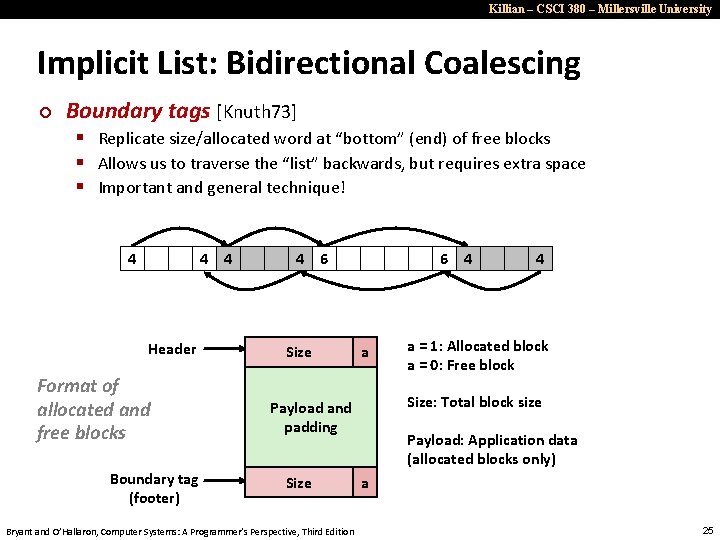
Killian – CSCI 380 – Millersville University Implicit List: Bidirectional Coalescing ¢ Boundary tags [Knuth 73] § Replicate size/allocated word at “bottom” (end) of free blocks § Allows us to traverse the “list” backwards, but requires extra space § Important and general technique! 4 4 4 Header Format of allocated and free blocks Boundary tag (footer) 4 6 Size 6 4 a Bryant and O’Hallaron, Computer Systems: A Programmer’s Perspective, Third Edition a = 1: Allocated block a = 0: Free block Size: Total block size Payload and padding Size 4 Payload: Application data (allocated blocks only) a 25

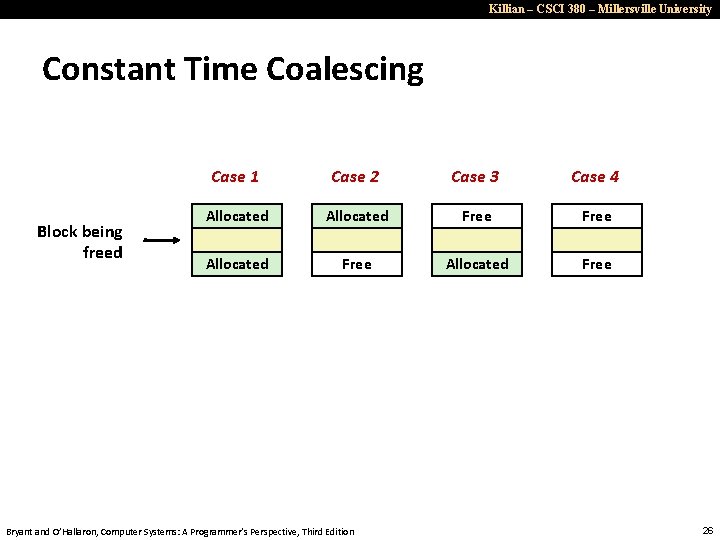
Killian – CSCI 380 – Millersville University Constant Time Coalescing Block being freed Case 1 Case 2 Case 3 Case 4 Allocated Free Bryant and O’Hallaron, Computer Systems: A Programmer’s Perspective, Third Edition 26

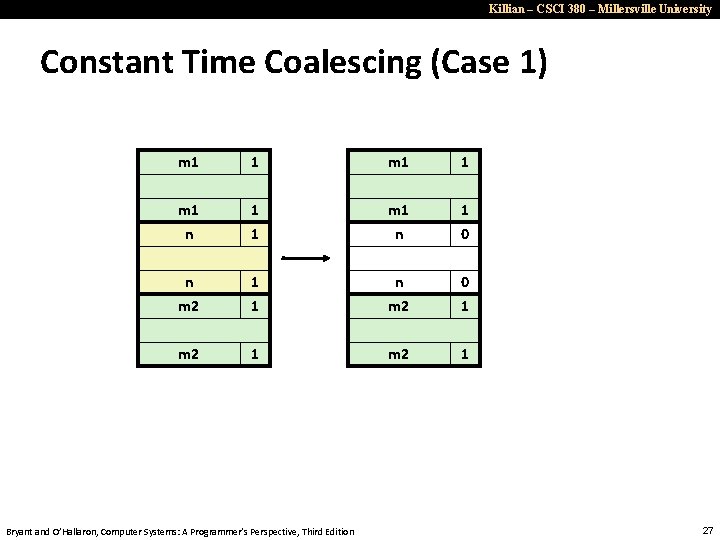
Killian – CSCI 380 – Millersville University Constant Time Coalescing (Case 1) m 1 1 m 1 n 1 0 n m 2 1 1 n m 2 0 1 m 2 1 Bryant and O’Hallaron, Computer Systems: A Programmer’s Perspective, Third Edition 27

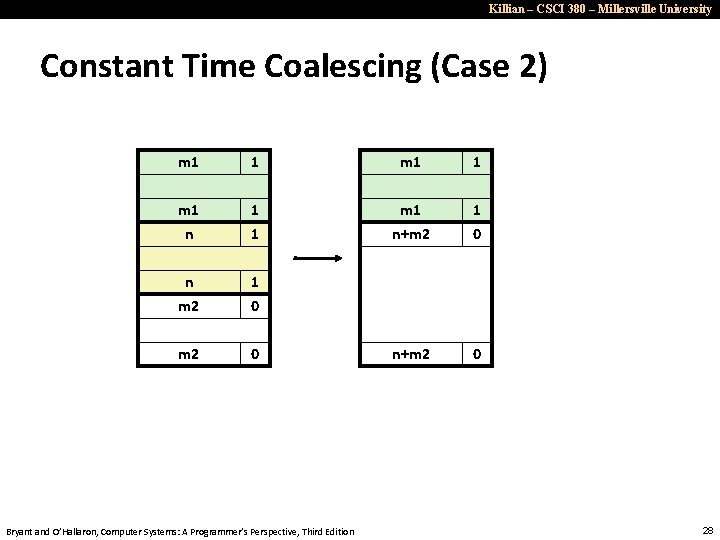
Killian – CSCI 380 – Millersville University Constant Time Coalescing (Case 2) m 1 1 m 1 n+m 2 1 0 n m 2 1 0 m 2 0 n+m 2 0 Bryant and O’Hallaron, Computer Systems: A Programmer’s Perspective, Third Edition 28

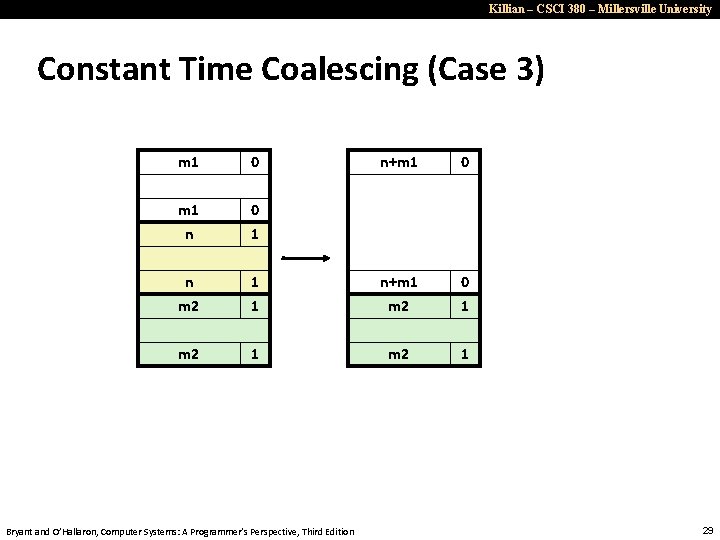
Killian – CSCI 380 – Millersville University Constant Time Coalescing (Case 3) m 1 0 n+m 1 0 m 1 n 0 1 n m 2 1 1 n+m 1 m 2 0 1 m 2 1 Bryant and O’Hallaron, Computer Systems: A Programmer’s Perspective, Third Edition 29

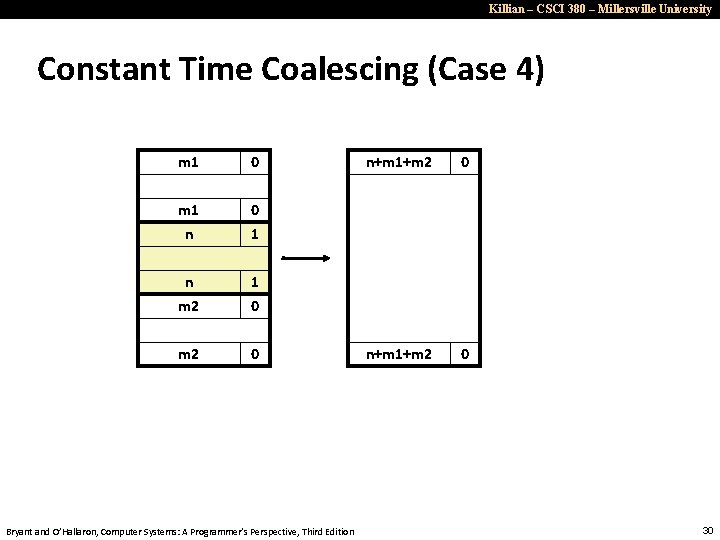
Killian – CSCI 380 – Millersville University Constant Time Coalescing (Case 4) m 1 0 m 1 n 0 1 n m 2 1 0 m 2 0 Bryant and O’Hallaron, Computer Systems: A Programmer’s Perspective, Third Edition n+m 1+m 2 0 30

Killian – CSCI 380 – Millersville University Disadvantages of Boundary Tags ¢ Internal fragmentation ¢ Can it be optimized? § Which blocks need the footer tag? § What does that mean? Bryant and O’Hallaron, Computer Systems: A Programmer’s Perspective, Third Edition 31

Killian – CSCI 380 – Millersville University Summary of Key Allocator Policies ¢ Placement policy: § First-fit, next-fit, best-fit, etc. § Trades off lower throughput for less fragmentation § Interesting observation: segregated free lists (next lecture) approximate a best fit placement policy without having to search entire free list ¢ Splitting policy: § When do we go ahead and split free blocks? § How much internal fragmentation are we willing to tolerate? ¢ Coalescing policy: § Immediate coalescing: coalesce each time free is called § Deferred coalescing: try to improve performance of free by deferring coalescing until needed. Examples: § Coalesce as you scan the free list for malloc § Coalesce when the amount of external fragmentation reaches some threshold Bryant and O’Hallaron, Computer Systems: A Programmer’s Perspective, Third Edition 32

Killian – CSCI 380 – Millersville University Implicit Lists: Summary ¢ ¢ Implementation: very simple Allocate cost: § linear time worst case ¢ Free cost: § constant time worst case § even with coalescing ¢ Memory usage: § will depend on placement policy § First-fit, next-fit or best-fit ¢ Not used in practice for malloc/free because of lineartime allocation § used in many special purpose applications ¢ However, the concepts of splitting and boundary tag coalescing are general to allocators Bryant and O’Hallaron, Computer Systems: A Programmer’s Perspective, Third Edition 33