Java Program to Implement RSA Algorithm YuLi Chen











- Slides: 16

Java Program to Implement RSA Algorithm Yu-Li Chen April, 2002 1

RSA: • public key cryptographic system • algorithm of RSA is openly published • much slower than encrypting with a secret key • provides both confidentiality and digital signing functions • mostly used for authentication and exchanging a secret key 2

The RSA algorithm: • Key generation • Encryption with public key • Decryption with private key 3

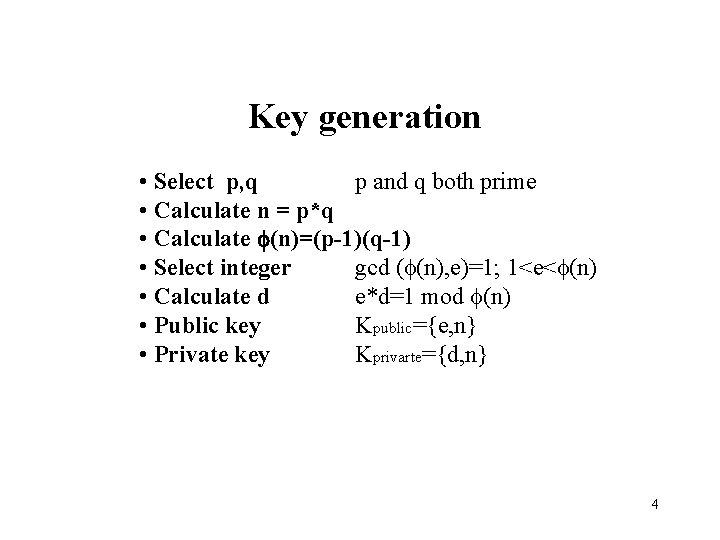
Key generation • Select p, q p and q both prime • Calculate n = p*q • Calculate (n)=(p-1)(q-1) • Select integer gcd ( (n), e)=1; 1<e< (n) • Calculate d e*d=1 mod (n) • Public key Kpublic={e, n} • Private key Kprivarte={d, n} 4

Encryption Plaintext: M<n e Ciphertext: C=M mode n 5

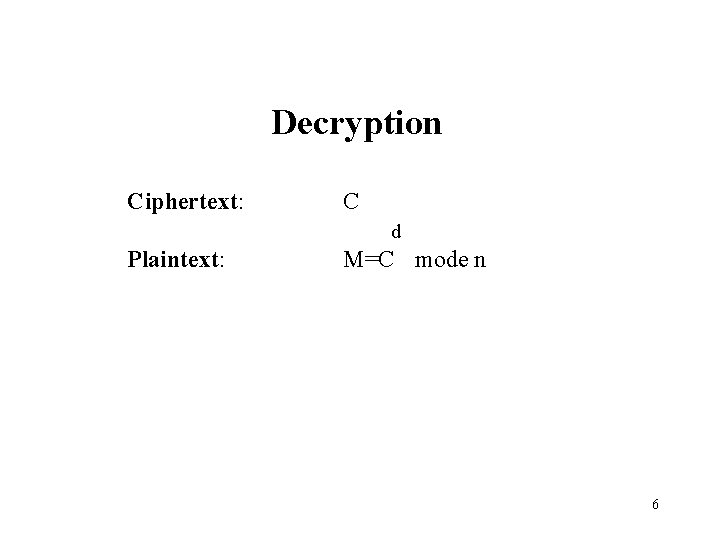
Decryption Ciphertext: C d Plaintext: M=C mode n 6

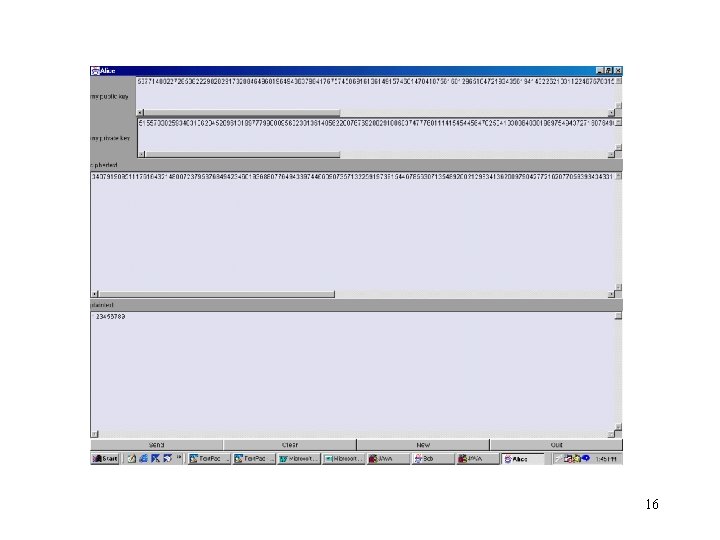
Objectives: • Write a Java program to implement RSA algorithm • After public key and private key been generated, use Alice/Bob application over TCP to demonstrate encryption and decryption process. 7

Method: Alice class: • Generate the public key pair (1024 bit) and send to Bob. • Decrypt the message received from Bob class: • Receive public key from Alice • Use the public key to encrypt the message • Send the ciphertext to Alice. 8

Alice: bit. Length = 512; certainty = 50; rnd = new Secure. Random(); p = new Big. Integer(bit. Length, certainty, rnd); q = new Big. Integer(bit. Length, certainty, rnd); n= p. multiply(q); one= new Big. Integer("1"); x = p. subtract(one). multiply(q. subtract(one)); e = new Big. Integer("65537"); d = e. mod. Inverse(x); 9

Alice: Socket client. Socket = new Socket(hostname, 6789); Data. Output. Stream out. To. Bob =new Data. Output. Stream(client. Socket. get. Output. Stream()); out. To. Bob. write. Bytes(public. Key + 'n'); client. Socket. close(); 10

Bob: Server. Socket welcome. Socket = new Server. Socket(6789); while(true) { Socket connection. Socket = welcome. Socket. accept(); Buffered. Reader in. From. Alice =new Buffered. Reader(new Input. Stream. Reader(connection. Socket. get. Input. Stream())); public. Key = in. From. Alice. read. Line(); publicky. Text. set. Text(public. Key); } 11

Bob: n= new Big. Integer(public. Key); e = new Big. Integer("65537"); plaintext=plain. Text. get. Text(); m= new Big. Integer(plaintext); c = m. mod. Pow(e, n); ciphertext=c. to. String(); 12

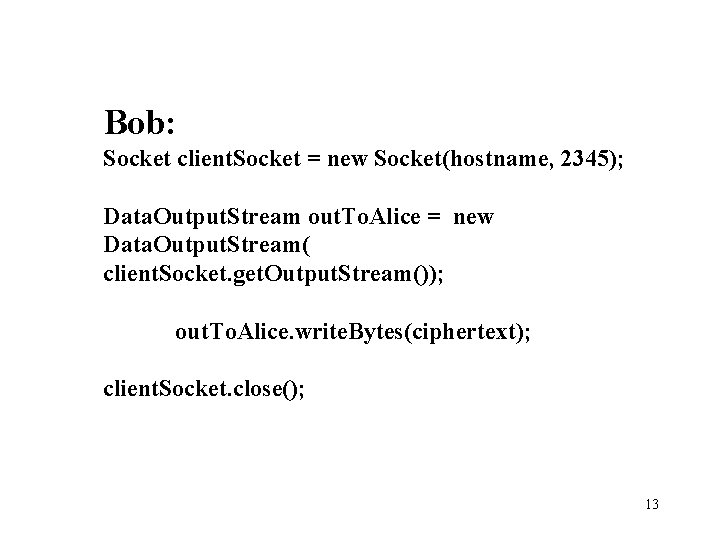
Bob: Socket client. Socket = new Socket(hostname, 2345); Data. Output. Stream out. To. Alice = new Data. Output. Stream( client. Socket. get. Output. Stream()); out. To. Alice. write. Bytes(ciphertext); client. Socket. close(); 13

Alice: Server. Socket welcome. Socket = new Server. Socket(2345); while(true) { Socket connection. Socket= welcome. Socket. accept(); Buffered. Reader in. From. Bob = new Buffered. Reader(new Input. Stream. Reader(connection. Socket. get. Input. Stream())); cipher=in. From. Bob. read. Line(); cipher. Text. set. Text(cipher); c= new Big. Integer(cipher); m=c. mod. Pow(d, n); 14

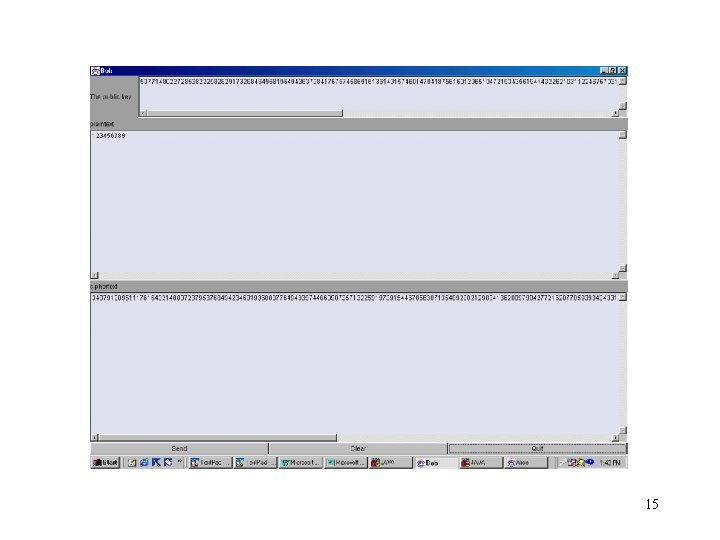
15

16