ITGS Types of network Wi Max Wi Max










- Slides: 22

ITGS Types of network

Wi. Max • Wi. Max (Worldwide Interoperability for Microwave Access) – A wireless technology designed to transfer data over distances of up to 50 kilometres (31 miles) • Bandwidth = relatively high, but reduces with distance • Good for providing Internet access to homes in areas where lying cables would be difficult • Also good for providing hotspont access in large areas, such as cities

Wi-Fi • Wi-Fi (Wireless Fidelity) • A standard for wirelessly connecting devices in a relatively small area, such as an office – Wi-fi devices connect to a wireless router, then to the Internet • Common in laptop computers and mobile devices • Wireless hotspots - common in public restaurants and businesses • Bandwidth can be up to 108 Mbps. • Bluetooth – A wireless technology used only for short distance or PANs • Examples: headsets to music players, phones, game controllers to computers, etc.

3 G and 4 G • 3 rd generation and 4 th generation – standards for wireless communication that operate using the mobile phone network • Used by smart phones and the modems in some laptop computers – Because they use the mobile phone network, 3 G and 4 G connections do not require the user to be near a Wi-Fi hotspot, making them good solutions for mobile Internet access » 4 G is faster than 3 G, but speed varies greatly depending on signal quality

Measuring Network Speed – Bandwidth - the amount of data a network can transfer at once • Narrowband - older, dialup network connections which have low speed • Broadband - more modern cable connections – Higher bandwidth connections are needed for tasks that involve large amounts of data transfer: » Video conferencing » Vo. IP calls » Quickly downloading large files – Network speeds are measured in bits per second (bps) • If your internet connection is 1 megabit per second, this is 128 kilobytes per second

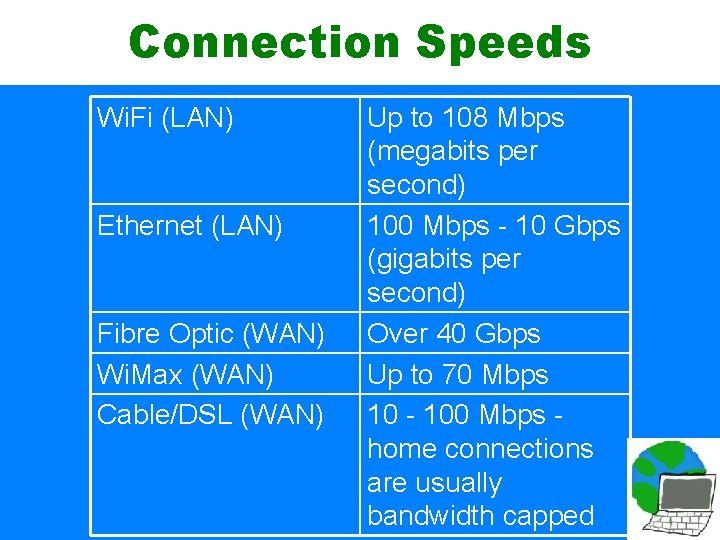
Connection Speeds Wi. Fi (LAN) Ethernet (LAN) Fibre Optic (WAN) Wi. Max (WAN) Cable/DSL (WAN) Up to 108 Mbps (megabits per second) 100 Mbps - 10 Gbps (gigabits per second) Over 40 Gbps Up to 70 Mbps 10 - 100 Mbps home connections are usually bandwidth capped

Connection Speeds, pt. 2 Dial up (WAN) 56 Kbps (Kilobits per second) 3 G (WAN) 200 Kbps 4 G (WAN) 5 - 20 Mbps (in use) Bluetooth (PAN) Up to 2 Mbps

Network Communication • In order to send and receive data on a computer network, you need a way to identify both the sender and receiver – MAC Address (also “hardware address”) • Media access control address - a unique number built into virtually every network device – Each MAC address is unique – They are stored in a device’s ROM, not designed to be changed • Sometimes wireless networks prevent access by unauthorized devices by filtering MAC addresses – Some computer users can change, or “spoof” their MAC address to get around this

Protocols • Protocol – A set of rules about how to do something. • Network communication couldn’t occur without networking protocols – Different protocols are used for different types of communication – IP (Internet Protocol) • Governs how devices on a network are identified and how information is routed between them • Used on many networks, not just the internet • On an IP network, each machine is assigned an IP address, which uniquely identifies it on that network – An IP address contains 4 groups of digits separated by dots (like 10. 5. 7. 115) – You don’t want 2 devices to have the same IP address, so addresses are usually assigned by a DHCP (Dynamic Host Control) Server

IP Protocol, continued – With all of the computers in the world, it is impossible to have a unique IP Address for each one • Because of this, the IP protocol features private addresses only used by computers on private networks such as LANs – Other computers on other networks can use the same private IP addresses – When a private network is connected to the Internet, the network gateway (the router) is assigned one public IP address which represents the entire network on the Internet

Assigning IP Addresses • Geolocation - since IP Addresses are assigned to ISPs by regions, then assigned to users by the ISPs, a record exists which can find a user’s location – All IP addresses are managed by the Internet Assigned Numbers Authority (IANA) • IANA assigns blocks of IP addresses to Regional Internet Registries (RIR), who manage IP addresses in different geographical regions – The RIRs assign addresses to Internet Service Providers (ISPs) » The ISP assigns you one of the IP addresses from its allocation 1. Dynamic IP address - changes each time you connect 2. Static IP address - remains the same each time you connect

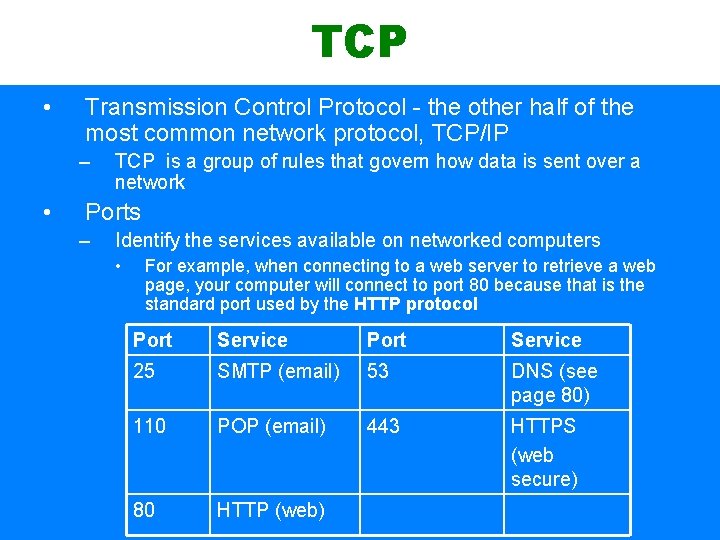
TCP • Transmission Control Protocol - the other half of the most common network protocol, TCP/IP – • TCP is a group of rules that govern how data is sent over a network Ports – Identify the services available on networked computers • For example, when connecting to a web server to retrieve a web page, your computer will connect to port 80 because that is the standard port used by the HTTP protocol Port Service 25 SMTP (email) 53 DNS (see page 80) 110 POP (email) 443 HTTPS (web secure) 80 HTTP (web)

The future of IP Addresses • IPv 4, the current IP addressing system, uses 32 bit addresses – – • There a total of around 4. 3 billion possible IP addresses According to the IANA, there were 150 million unassigned addresses remaining in 2010. 243 million a year are being assigned Soon, there will be no addresses for new users IPv 6 uses 128 bit addresses

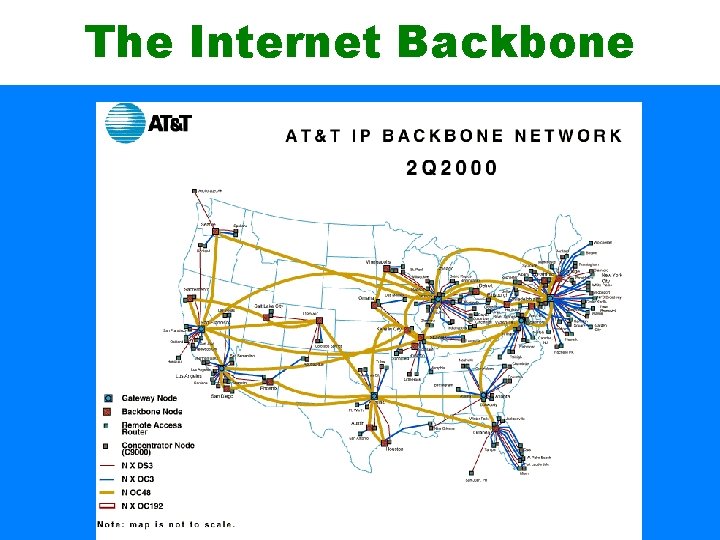
The Internet • The Internet Backbone – The internet is a network of networks • Local networks are connected via Internet Service Providers (ISPs) • ISPs are connected to national Network Service Providers (NSPs) – NSPs are large companies that sell access to the Internet backbone » Internet backbone - the series of high speed links which connect major geographical areas • Backbone cables run under oceans and are usually high speed fiber optic cables – Backbones need to be high speed because of huge amounts of internet traffic » Everything from ‘below them’ on the internet travels through them » For example: Seacom backbone in Africa runs through the Indian Ocean and makes land in Mombasa, Kenya » From Mombasa, the connectivity filters down to the rest of Kenya

The Internet Backbone

Data Routing • When you send an email or access a web page, your data does not go directly to the recipient’s computer. • You don’t have a direct cable between your computer and every person’s computer that you are going to communicate with • Example: an email from El Paso to New York City • When the user clicks send, the data travels from his computer on the LAN to the ISP. • His ISP sends it to a National Service Provider, connected directly to the Internet Backbone. • An internet backbone lands at new York City, where the email travels from an NSP to the recipient’s ISP, then her computer. • Security: any of the systems that the data passes through can view or alter that data • So, don’t send sensitive info through email

Data Routing • Online shopping sites and banking systems always protect their users with SSL or TLS encryption to guard against electronic eavesdroppers. • Example of how the backbone can affect the world: • In early 2008, a ship performing work on the sea bed accidentally cut a primary backbone cab. e, affecting tens of millions of people in the Middle East and Asia. • Domain Names and DNS • URL (Universal Resource Locators) - are short enough to remember but provide enough details about the owner or content of the web site to be more memorable than IP addresses • Parts of a URL: • Domain name: kimhaefner. com • Top level domain: . com • Hostname: www. kimhaefner. com • File name: index. html

Domain Names • Top level domains: • Org charities and non-profits • Mil military sites • Edueducational sites • Govgovernmental sites • Domain Name System (DNS) - a system responsible for translating domain names that people type into their web browser address bars into IP addresses that computers can use to locate each other. • DNS consists of servers connected to the Internet whose purpose is simply to map these domain names to IP addresses.

Internet Protocols • Hyper. Text Transfer Protocol (HTTP) • The protocol that goeverns communication between web servers and web browsers • Every time you visit a web site, your browser is using http to communicate with the web server which hosts the site • Hyper. Text Transfer Protocol Secure (https) • A version of the http protocol designed to encrypt data to provide communication secure from eavesdroppers • Essential for sensitive transactions such as sending passwords or bank account details • https uses Transport Layer Security (TLS) or Secure Socket Layer (SSL) encryption to achieve this security • A secure web connection is indicated by a https at the start of the address and a padlock icon

Synchronous or Asynchronous Transfer • Data transfer between computers can occur either synchronously or asynchronously • Asynchronous transfer - the sender and receiver are not synchronized in terms of time • Synchronous transfer - the sender and receiver synchronize times and agree on a transfer rate before the start of the transfer • They then transfer data at a fixed, regular intervals • This allows faster data transfer • The Internet or the Web? • The Internet is the physical network of computers across the globe, using the TCP/IP protocol to operate. • The World Wide Web is just one of the services that runs over the Internet, providing access to interlinked web pages containing text and images.

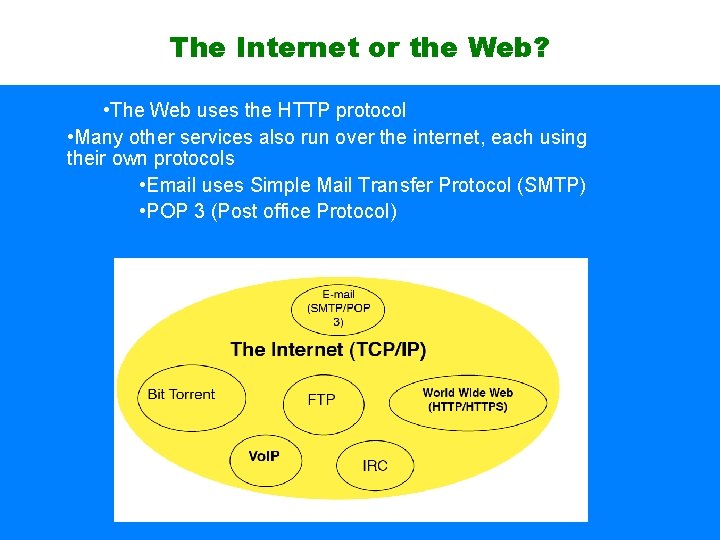
The Internet or the Web? • The Web uses the HTTP protocol • Many other services also run over the internet, each using their own protocols • Email uses Simple Mail Transfer Protocol (SMTP) • POP 3 (Post office Protocol)

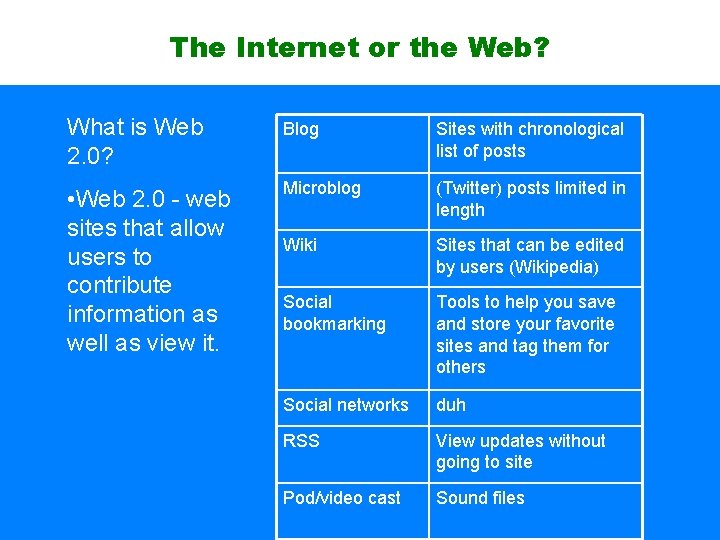
The Internet or the Web? What is Web 2. 0? Blog Sites with chronological list of posts • Web 2. 0 - web sites that allow users to contribute information as well as view it. Microblog (Twitter) posts limited in length Wiki Sites that can be edited by users (Wikipedia) Social bookmarking Tools to help you save and store your favorite sites and tag them for others Social networks duh RSS View updates without going to site Pod/video cast Sound files