Iterative detection and decoding to approach MIMO capacity

- Slides: 19

Iterative detection and decoding to approach MIMO capacity Jun Won Choi

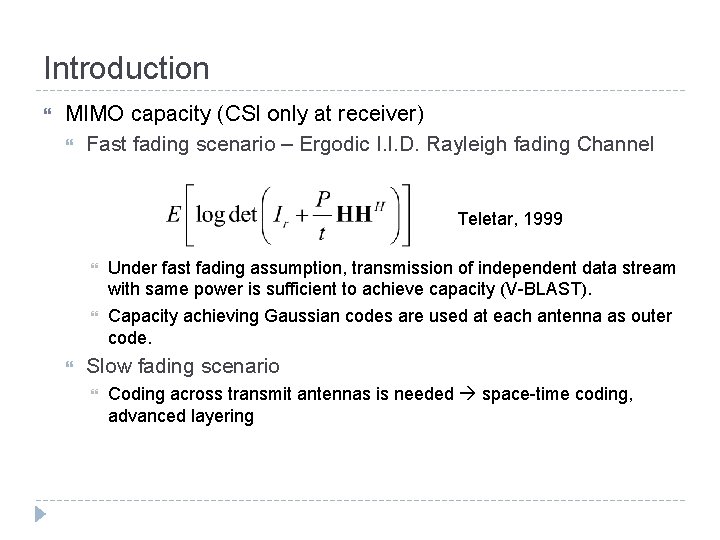
Introduction MIMO capacity (CSI only at receiver) Fast fading scenario – Ergodic I. I. D. Rayleigh fading Channel Teletar, 1999 Under fast fading assumption, transmission of independent data stream with same power is sufficient to achieve capacity (V-BLAST). Capacity achieving Gaussian codes are used at each antenna as outer code. Slow fading scenario Coding across transmit antennas is needed space-time coding, advanced layering

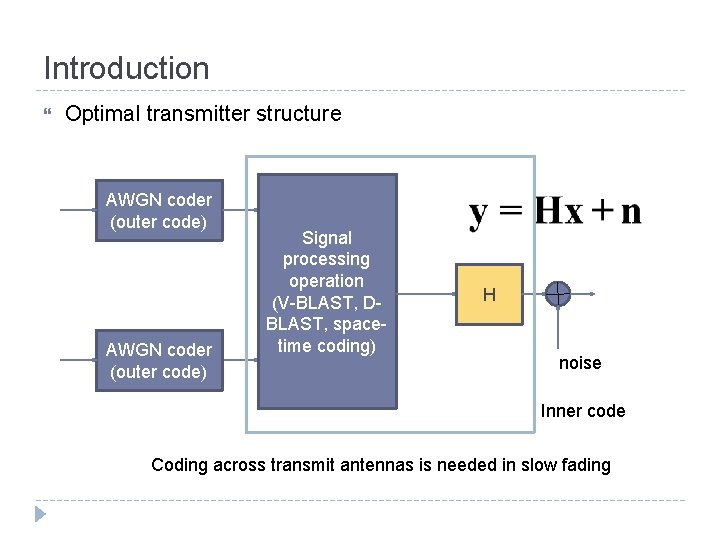
Introduction Optimal transmitter structure AWGN coder (outer code) Signal processing operation (V-BLAST, DBLAST, spacetime coding) H noise Inner code Coding across transmit antennas is needed in slow fading

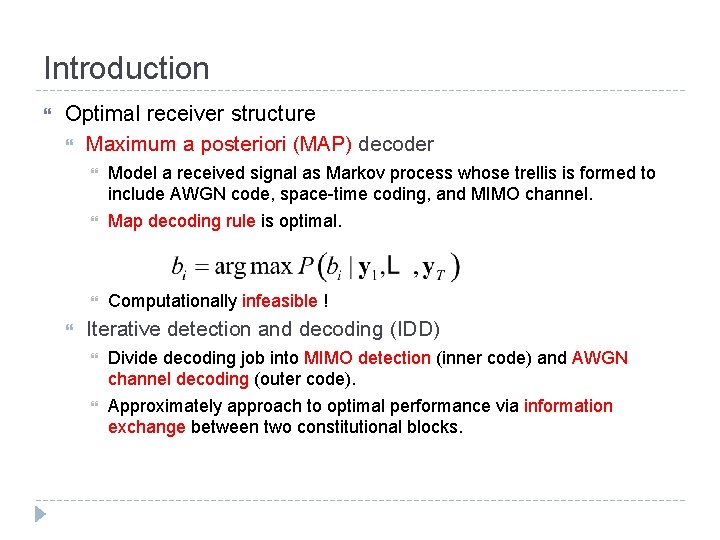
Introduction Optimal receiver structure Maximum a posteriori (MAP) decoder Model a received signal as Markov process whose trellis is formed to include AWGN code, space-time coding, and MIMO channel. Map decoding rule is optimal. Computationally infeasible ! Iterative detection and decoding (IDD) Divide decoding job into MIMO detection (inner code) and AWGN channel decoding (outer code). Approximately approach to optimal performance via information exchange between two constitutional blocks.

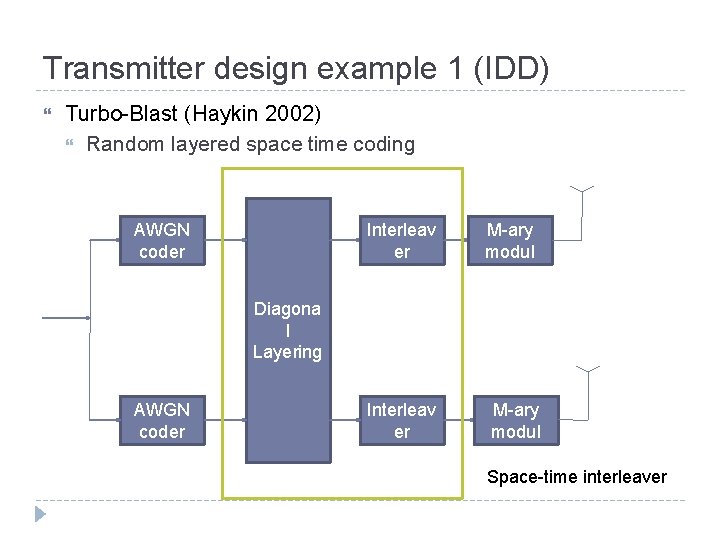
Transmitter design example 1 (IDD) Turbo-Blast (Haykin 2002) Random layered space time coding AWGN coder Interleav er M-ary modul Diagona l Layering AWGN coder Interleav er M-ary modul Space-time interleaver

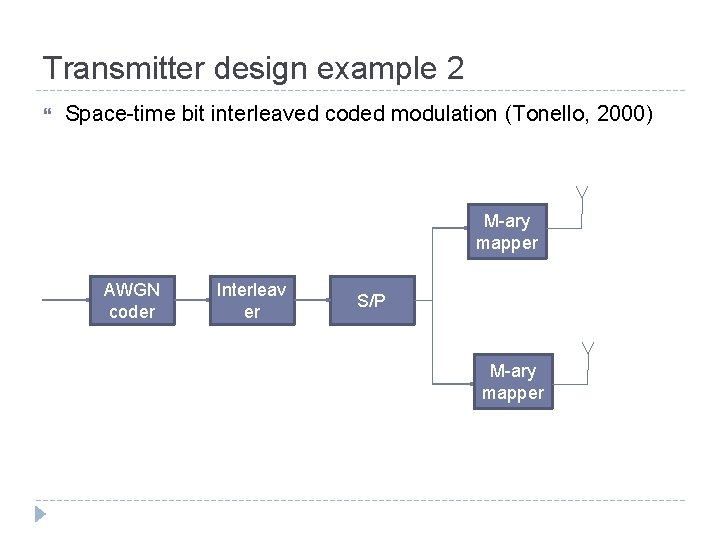
Transmitter design example 2 Space-time bit interleaved coded modulation (Tonello, 2000) M-ary mapper AWGN coder Interleav er S/P M-ary mapper

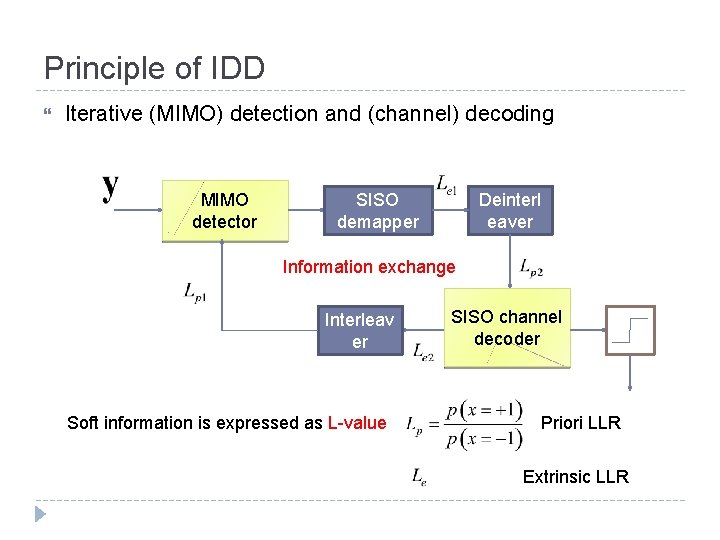
Principle of IDD Iterative (MIMO) detection and (channel) decoding MIMO detector SISO demapper Deinterl eaver Information exchange Interleav er Soft information is expressed as L-value SISO channel decoder Priori LLR Extrinsic LLR

IDD SISO Channel decoder BCJR algorithm – based on trellis-based search Low-complexity APP decoder - LOG-MAX algorithm, Soft output viterbi algorithm (SOVA) MIMO detector Complexity and performance trade-off MAP versus Sub-optimal detector with linear structure

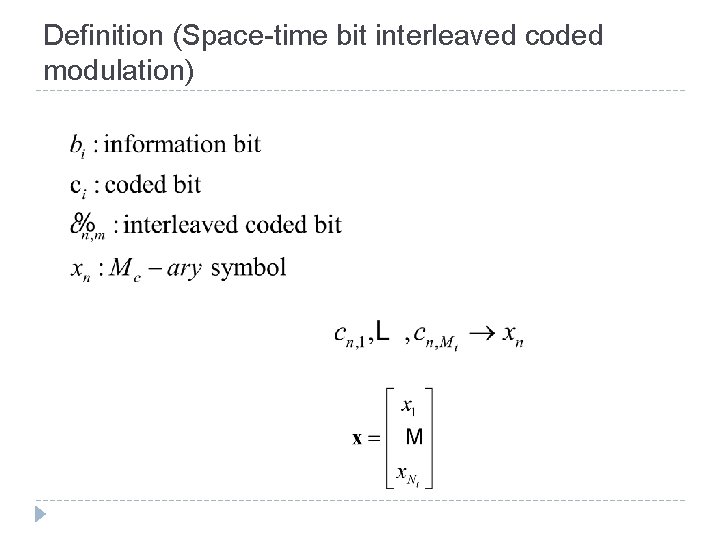
Definition (Space-time bit interleaved coded modulation)

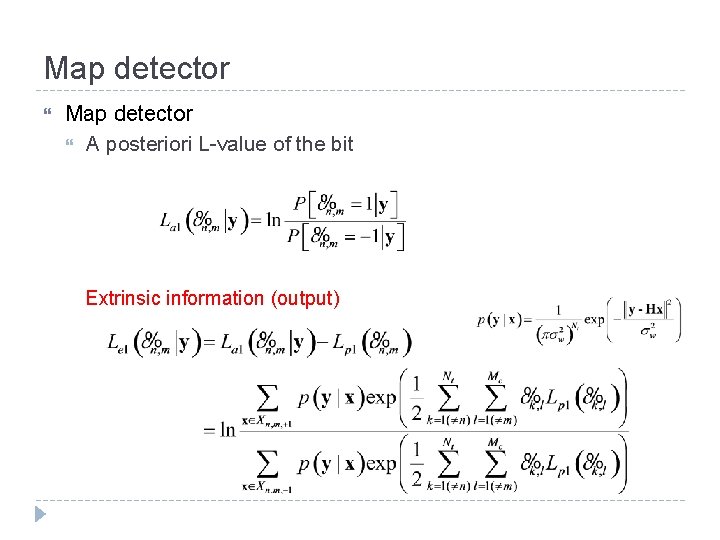
Map detector A posteriori L-value of the bit Extrinsic information (output)

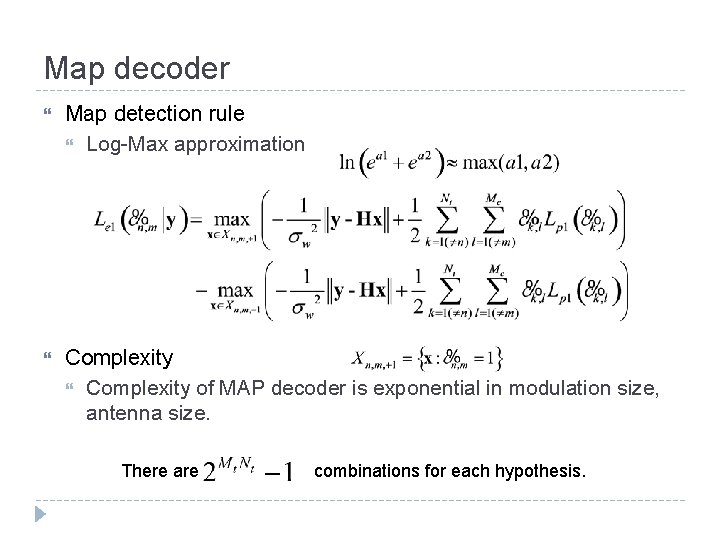
Map decoder Map detection rule Log-Max approximation Complexity of MAP decoder is exponential in modulation size, antenna size. There are combinations for each hypothesis.

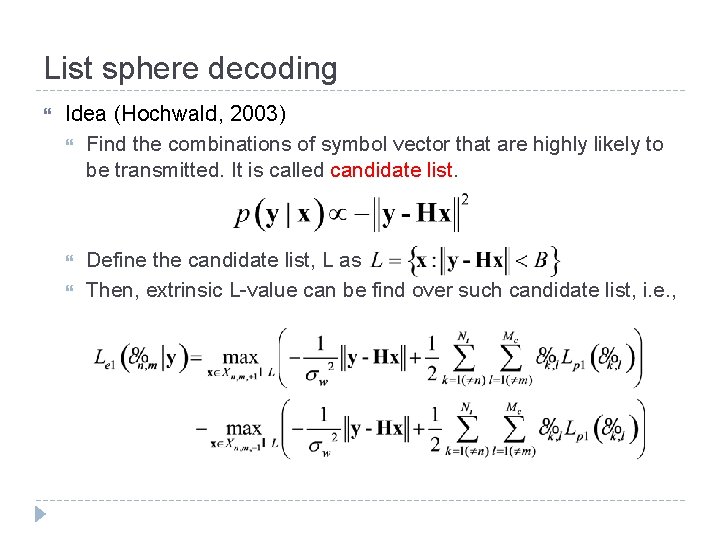
List sphere decoding Idea (Hochwald, 2003) Find the combinations of symbol vector that are highly likely to be transmitted. It is called candidate list. Define the candidate list, L as Then, extrinsic L-value can be find over such candidate list, i. e. ,

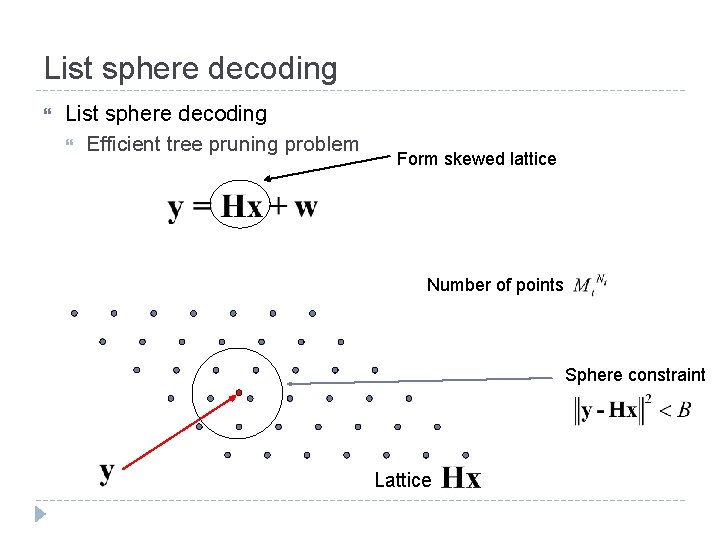
List sphere decoding Efficient tree pruning problem Form skewed lattice Number of points Sphere constraint Lattice

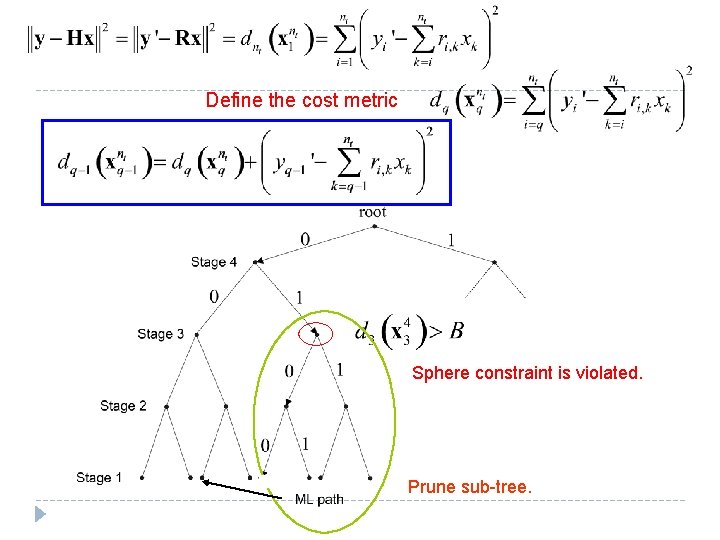
Define the cost metric Sphere constraint is violated. Prune sub-tree.

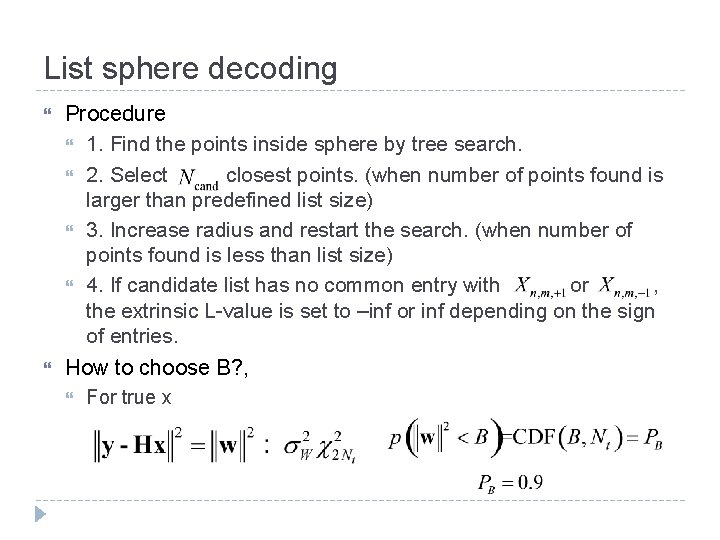
List sphere decoding Procedure 1. Find the points inside sphere by tree search. 2. Select closest points. (when number of points found is larger than predefined list size) 3. Increase radius and restart the search. (when number of points found is less than list size) 4. If candidate list has no common entry with or , the extrinsic L-value is set to –inf or inf depending on the sign of entries. How to choose B? , For true x

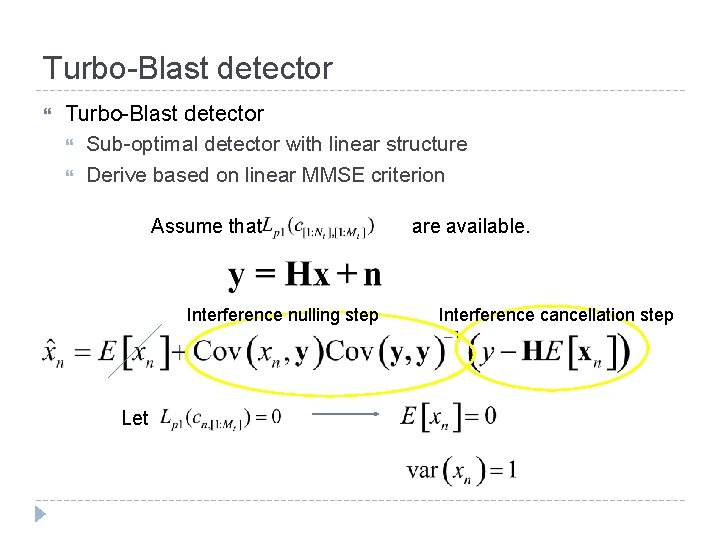
Turbo-Blast detector Sub-optimal detector with linear structure Derive based on linear MMSE criterion Assume that Interference nulling step Let are available. Interference cancellation step

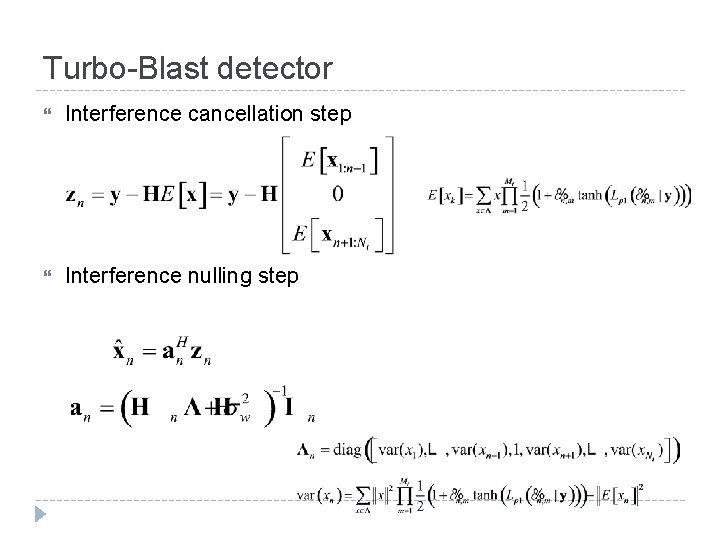
Turbo-Blast detector Interference cancellation step Interference nulling step

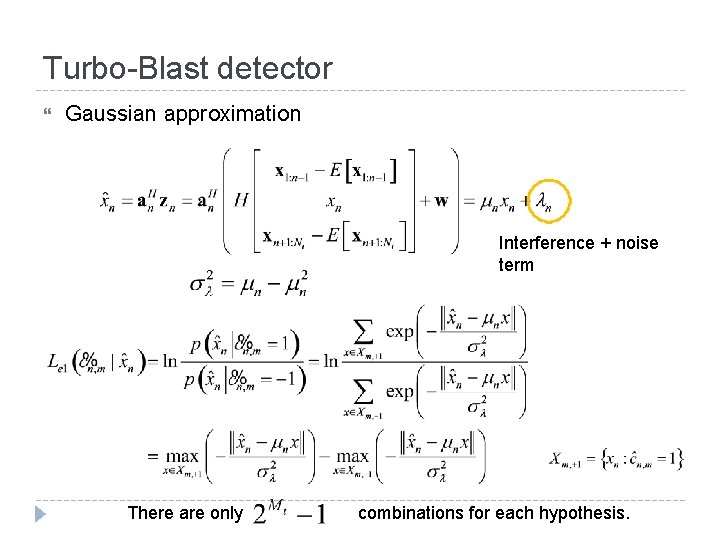
Turbo-Blast detector Gaussian approximation Interference + noise term There are only combinations for each hypothesis.

Conclusions Capacity achieving MIMO architecture Transmitter architecture V-BLAST + AWGN code for fast fading Coding across transmit antenna for slow fading space time coding, D-BLAST, Treaded space time coding Receiver architecture Global MAP decoding Iterative detection and decoding Map decoding List sphere decoder Linear MMSE detector