IP datagrams Service paradigm IP datagrams routing encapsulation












- Slides: 24

IP datagrams Service paradigm, IP datagrams, routing, encapsulation, fragmentation and reassembly

Internet service paradigm • TCP/IP supports both connectionless and connection-oriented services – fundamental delivery service is connectionless at the Internet layer – optional reliable connection-oriented service is layered on top of this at the transport layer

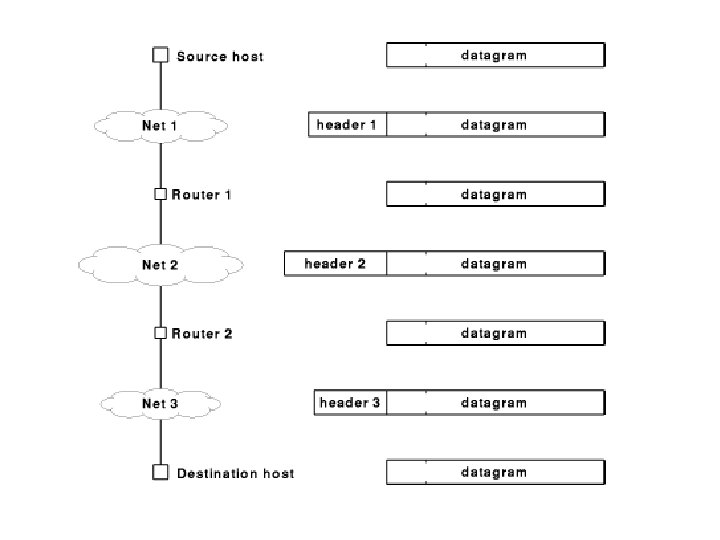
IP datagrams • Packets of data are sent across multiple physical networks via routers • Internet protocols define a universal virtual packet - the IP datagram • The amount of data carried in a datagram is not fixed and is determined by an application

Routers and routing tables • Each router forwards a virtual packet by using a local routing table • Each entry is: – destination address – mask – next hop • IP address of a router or • Deliver direct • Then does address resolution

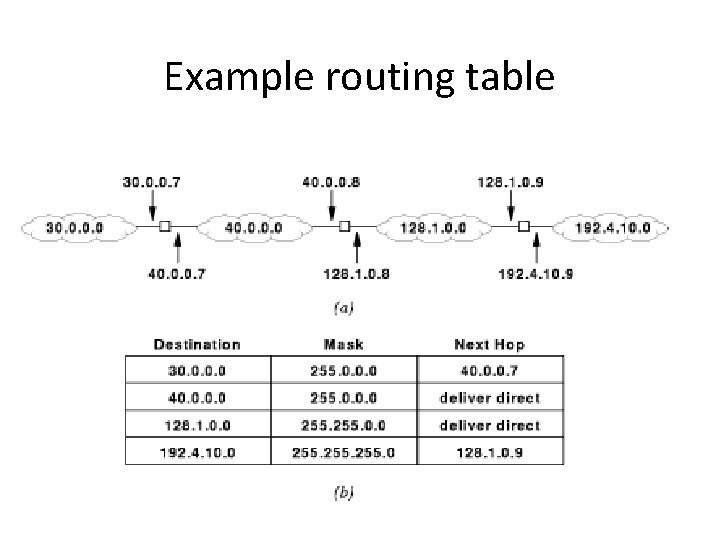
Example routing table

Best-effort delivery • IP attempts best effort delivery and does not guarantee to deal with: – datagram duplication – delayed or out of order delivery – corruption of data – datagram loss • These issues are dealt with other protocol layers

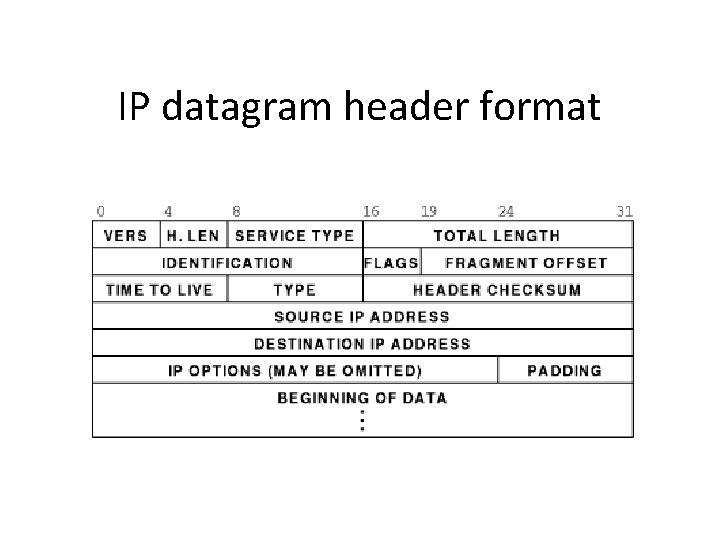
IP datagram header format

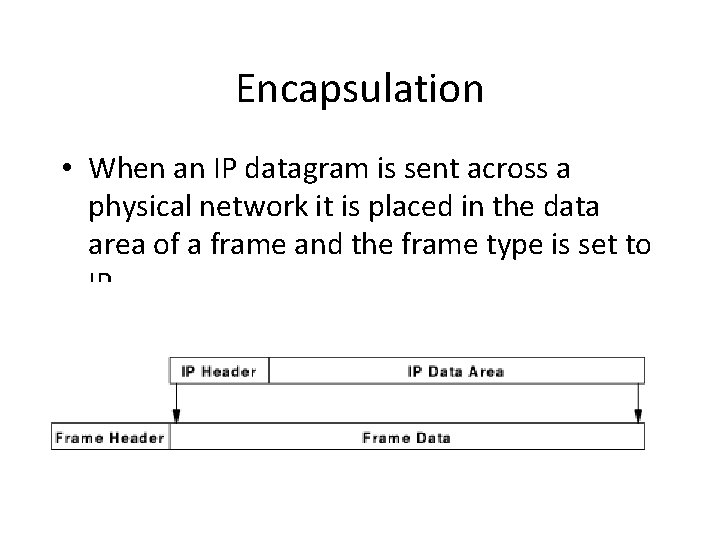
Encapsulation • When an IP datagram is sent across a physical network it is placed in the data area of a frame and the frame type is set to IP


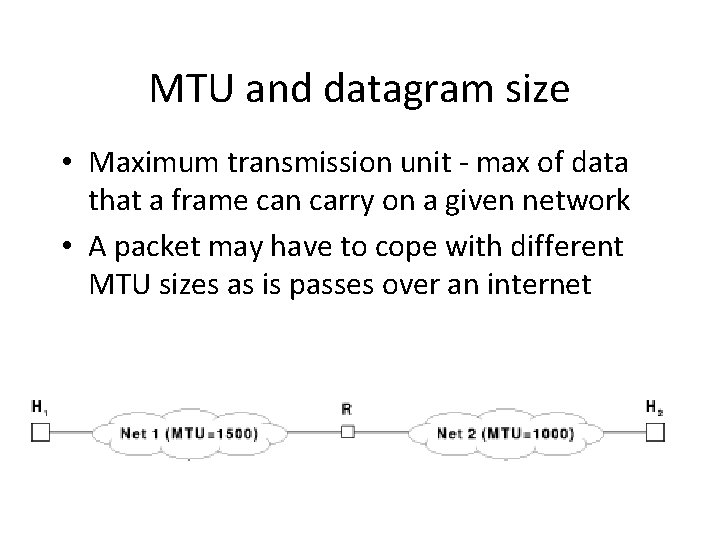
MTU and datagram size • Maximum transmission unit - max of data that a frame can carry on a given network • A packet may have to cope with different MTU sizes as is passes over an internet

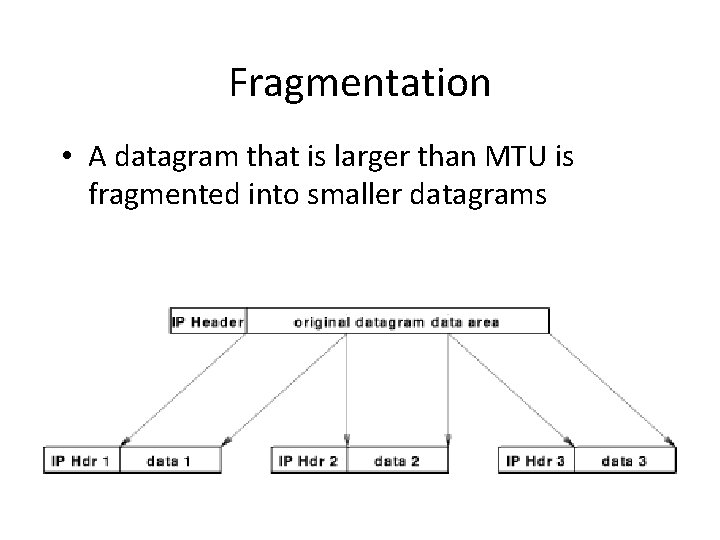
Fragmentation • A datagram that is larger than MTU is fragmented into smaller datagrams

Reassembly • Is done at the final host – routers require less state information – fragments can take different routes • Header fields indicate when the data is a fragment and also where it belongs • Whole datagram is lost if any fragment is lost

The Future of IP (IPv 6) Motivation for IPv 6, Addressing, Datagram Format, Paths

Motivation • IP has been extremely successful at coping with the expansion of The Internet and changes in network hardware over 20 years! • However: – limited address space will soon run out – new application requirements • real-time audio and video require guaranteed service • collaboration technologies require ways of sending packets to groups of hosts

What is in a name? • The current IP is IPv 4 • The new version was originally called IP The Next Generation (IPng), but this became associated with several proposals • The final proposal is called IPv 6

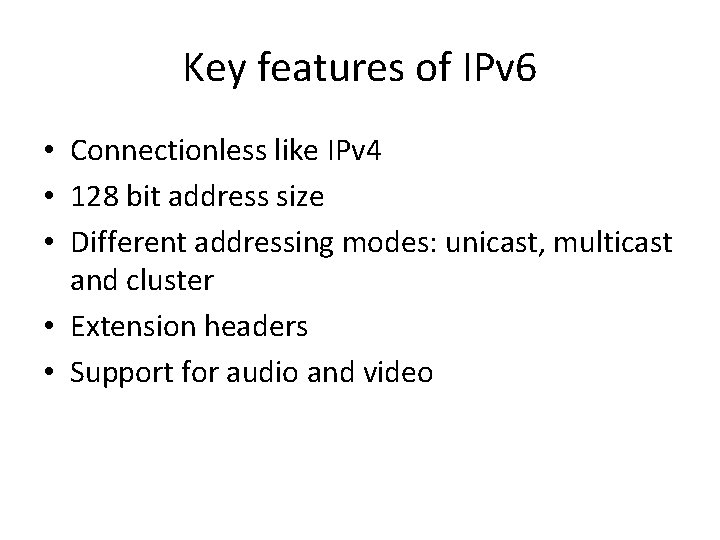
Key features of IPv 6 • Connectionless like IPv 4 • 128 bit address size • Different addressing modes: unicast, multicast and cluster • Extension headers • Support for audio and video

Three types of address • unicast - address corresponding to a single computer. Datagram sent along shortest path • multicast – address corresponding to a set of computers, – members can change at any time. – one copy of a datagram is delivered to each – only one copy passes over intervening networks – used for collaborative applications

• Cluster – address corresponds to a set of computers that share a common prefix – a datagram is delivered to one of these – used for replicating a service

Writing down IPv 6 addresses • Replaces dotted decimal notation with more compact colon hexadecimal 105. 220. 136. 100. 255. 0. 0. 18. 128. 140. 10. 255 => 69 DC: 8864: FFFF: 0: 1280: 8 C 0 A: FFFF • Zero compression further reduces space FF 0 C: 0: 0: 0: B 1 => FF 0 C: : B 1 • Especially useful because an IPv 6 address that begins with 96 zeros contains an IPv 4 address in the last 32 bits

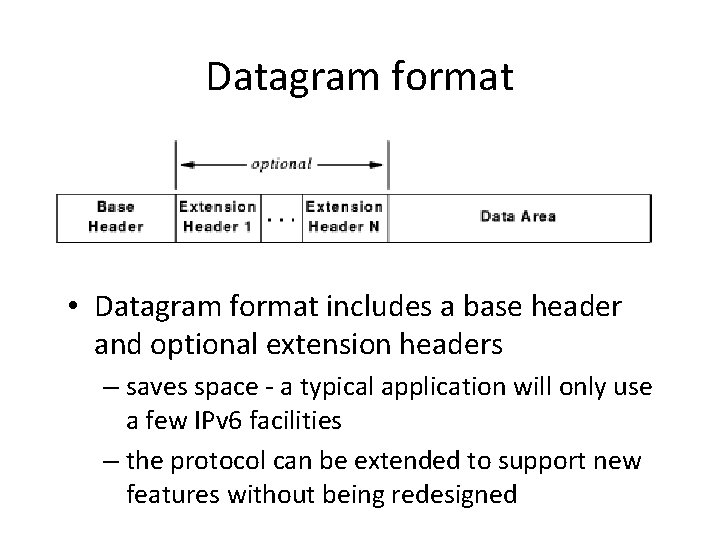
Datagram format • Datagram format includes a base header and optional extension headers – saves space - a typical application will only use a few IPv 6 facilities – the protocol can be extended to support new features without being redesigned

Base Header

Paths • Applications can be used to set up network paths in advance • These can be associated with different traffic classes that provide different Quality of Service (Qo. S) • Necessary for real-time audio and video

Examples of Collaborative Applications • �� Collaborative Virtual Environments (CVEs) – Shared 3 D virtual world – Each user controls own viewpoint – Interaction with objects – Users represented by avatars – Communication through embedded audio, video, text and graphical gestures

CVE and network traffic • In a CVE each user may be an active sender as well as a receiver of various kinds of information • Many users may send data at the same time • There may be hundreds of users • As a result, CVEs can generate large volumes of network traffic