Internet Research Ethics 2 0 Research Ethics WorkshopEthical


















- Slides: 26

Internet Research Ethics 2. 0 Research Ethics Workshop Ethical internet research: challenges and (re)solutions Dr. Charles Ess IMV, Aarhus University <charles. ess@gmail. com>

overview 1. Introduction: (A) the nature of ethical judgments and (B) the primary principles at work in Internet research, particularly as these rest on conceptions of identity, ethical agency and responsibility, and ownership (i. e. , of one’s texts and other creative expressions). 2. Ethics and methodology as mutually interacting, and focusing on ethical issues surrounding participant-observation methodology as examples. 3. Ao. IR ethical guidelines 2. 0 (working copies provided), specifically as applied to: (A) the status of data (public? private? …? ) provided in social networking profiles and correlative ethical requirements for researchers, and (B) “dissemination ethics” and informed consent, especially with regard to profile data and blog posts. 4. Ethical variables and Discussion (handout) 5. (Time permitting): Blogs: Public, Private, and the Intimsphere - A Danish Example 2

1. Introduction the nature of ethical judgments - phronesis determinative, “top-down” ethical judgments that run from (more or less) accepted general principles specific ethical conclusion(s) and reflective, “bottom-up // top-down” ethical judgments that require us first to discern (from the “bottom-up”) within a given, specific, fine-grained, and incomplete context of actors, relationships, and possible choices what general ethical principles, norms, practices apply? 3

1. Introduction i) we can - with good reason, i. e. , legitimately - discern a) which general principles / norms / practices apply, and b) in case of conflict, their relative weight / priority, in part, precisely through a reflexive dialogical interrogation of a specific given context. But this means: ii) it is perfectly possible for different persons - or, e. g. , the same person at different stages / contexts - to draw different judgments as to the proper course of action, e. g. “judgment calls” iii) such judgments, moreover, may bring into play tacit, inarticulate understandings of the world and our place in it as developed through experience and known in and through the body “gut feeling” “what my heart tells me” … 4

1. Introduction (iv) Such judgments, finally, thereby allow for a pluralism - i. e. , a diversity of judgments may be legitimately made and rationally defended, especially in light of culturally-variable norms, practices, values, etc. Consider, for example whether or not your right to privacy (a general norm) means that I am allowed to take your photograph in a public space without your consent privacy US - yes Norway - no 5

In sum: given 1) the range of possible ethical decision-making procedures: Utilitarianism – ethical cost-benefit analysis: will (potential) benefits of a given choice/act/rule outweigh possible harms (=costs)? “Greatest good for the greatest number” – primary framework in U. S. – UK? Deontology – emphasizes basic rights of autonomous individuals (including life, liberty, pursuit of property … privacy, etc. ) as near -absolute; to be protected (more or less) no matter what benefits might otherwise accrue. Strongly influential in Northern Europe, Scandinavia feminist ethics/ethics of care – feeling as much as reason is a crucial “way of knowing, ” especially with regard to ethics as a matter of “sustaining the web of relationships” virtue ethics – what virtues (habit, practices, facilities) are requisite for the good life and community harmony? (“Eastern, ” 6 increasingly “Western”)

1. Introduction In sum: given 1) the range of possible ethical decision-making procedures (utilitarianism, deontology, feminist ethics, etc. ), 2) the multiple interpretations and applications of these procedures to specific cases, and 3) their refraction through culturally-diverse emphases and values across the globe …. 7

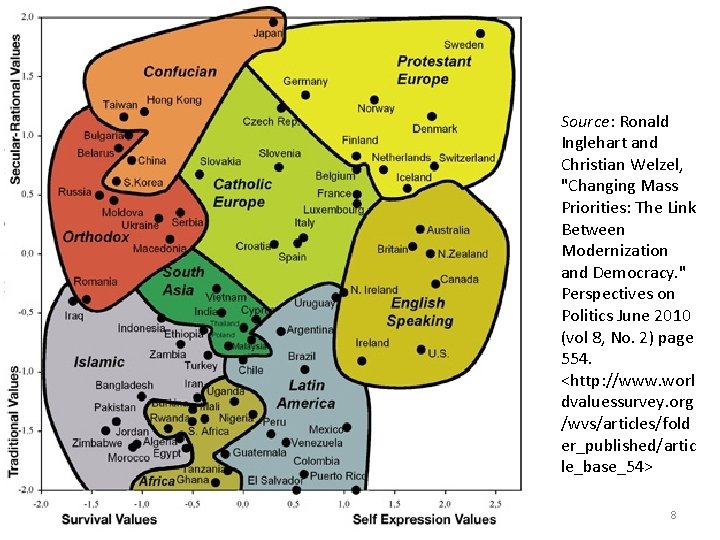
Source: Ronald Inglehart and Christian Welzel, "Changing Mass Priorities: The Link Between Modernization and Democracy. " Perspectives on Politics June 2010 (vol 8, No. 2) page 554. <http: //www. worl dvaluessurvey. org /wvs/articles/fold er_published/artic le_base_54> 8

1. Introduction In sum: given 1) the range of possible ethical decision-making procedures (utilitarianism, deontology, feminist ethics, etc. ), 2) the multiple interpretations and applications of these procedures to specific cases, and 3) their refraction through culturally-diverse emphases and values across the globe – the issues raised by Internet research are ethical problems precisely because they evoke more than one ethically defensible response to a specific dilemma or problem. Ambiguity, uncertainty, and disagreement are inevitable. The best we can do: general guidelines + case histories (casuistics) possible resolutions (not “solutions”) of specific ethical challenges, dilemmas. 9

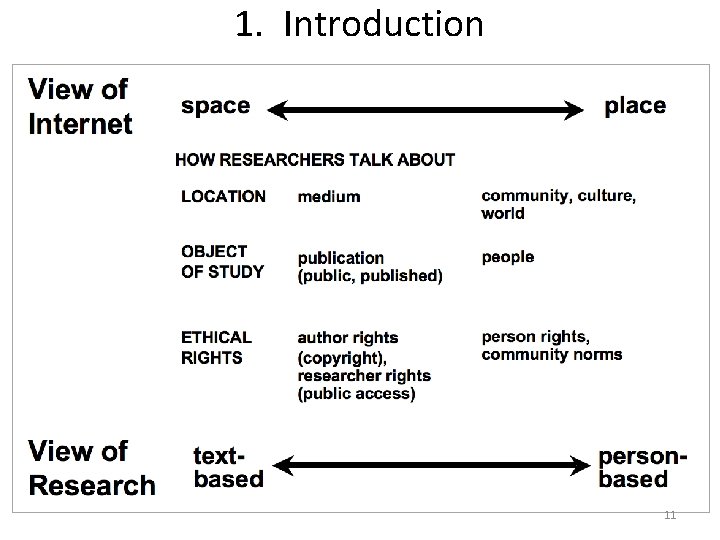
1. B. primary principles/norms in Internet research ethics i) issues based on conceptions of identity and ethical agency - i. e. , as focused on the (inter-)actions of persons, understood to have basic rights (including the rights to privacy and protection from harms). In the “standard model” of research Human Subjects Protections, these rights are further specified in terms of confidentiality anonymity informed consent - specifically as intended to protect ethical autonomy (cf. Swedish Research Council’s Ethical Research Principles, Rules 1 -3) what Mc. Kee & Porter call a “person-based” view of research ii) issues of ownership copyright and other matters of authorial control over one's texts what Mc. Kee & Porter call a “text-based” view of research 10

1. Introduction 11

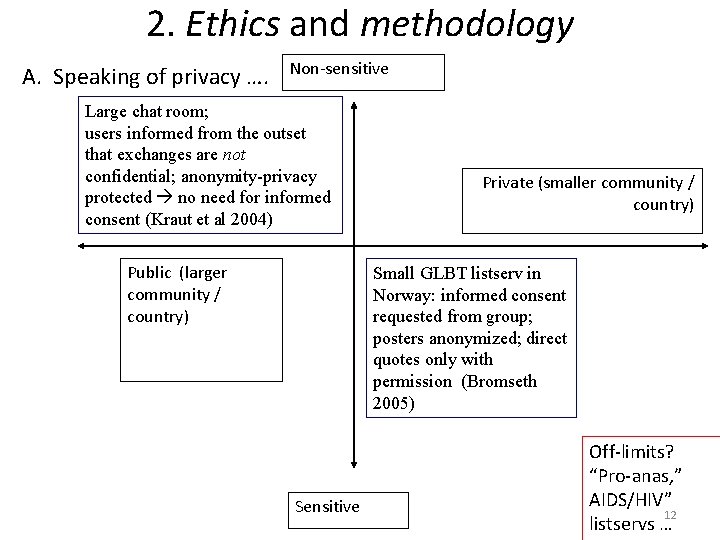
2. Ethics and methodology A. Speaking of privacy …. Non-sensitive Large chat room; users informed from the outset that exchanges are not confidential; anonymity-privacy protected no need for informed consent (Kraut et al 2004) Public (larger community / country) Private (smaller community / country) Small GLBT listserv in Norway: informed consent requested from group; posters anonymized; direct quotes only with permission (Bromseth 2005) Sensitive Off-limits? “Pro-anas, ” AIDS/HIV” 12 listservs …

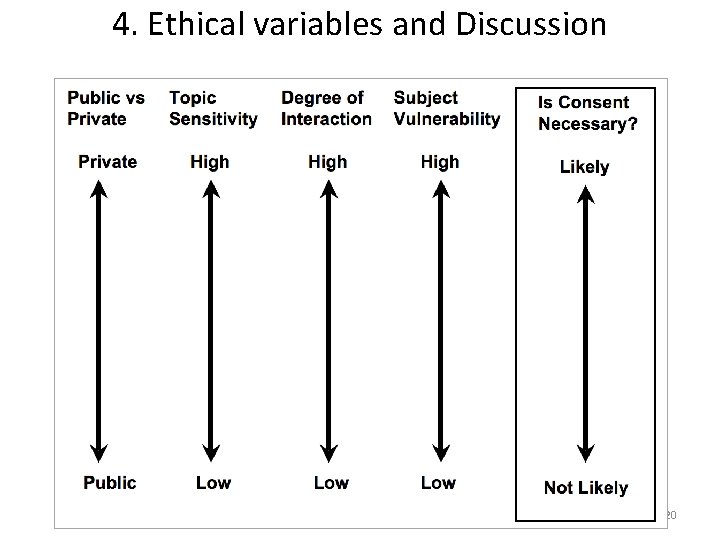
2. Ethics and methodology A. Speaking of privacy …. changing conceptions? Individual privacy group privacy “publicy” public “publicly private” “privately public” close friends, relatives videos on You. Tube “hidden” by tagging them so that only friends and relatives would know how to find them relatively unknown “friends” - but still highly private / personal information re. identities, sexual orientation, but not, e. g. , home address (Patricia Lange (2007) in Mc. Kee & Porter 2009, 78) 13

2. Ethics and methodology B. Ethical issues surrounding participant-observation methodology as examples. In general … Participant-observation /discourse analysis heighten the importance of privacy, informed consent, and attending to the ethical issues surrounding the use of participants’ texts: As participant-observation emphasizes more personal, empathic relationship increases researchers’ inclination to accord higher degrees of privacy protection (“Golden Rule”) + pragmatic recognition that participants can easily disconnect from online engagements, increasing the importance of a “trusted, reciprocal exchange” (feminist) Oliver & Lunt 2004, 107) Cf. Mc. Kee and Porter, 2009: still true today? Possible case-study discussion on blogging, below 14

2. Ethics and methodology B. Ethical issues surrounding participant-observation methodology as examples. In general … Humanities approaches - poster as author, seeking publicity… A. All materials published online are considered copyright by the author under U. S. law B. Citations and references guided by “fair use” considerations which are unclear for digital materials. C. See, for example, Twitter’s privacy policy: 15

2. Ethics and methodology Tweets, Following, Lists and other Public Information: Our Services are primarily designed to help you share information with the world. Most of the information you provide to us is information you are asking us to make public. This includes not only the messages you Tweet and the metadata provided with Tweets, such as when you Tweeted, but also the lists you create, the people you follow, the Tweets you mark as favorites or Retweet and many other bits of information. Our default is almost always to make the information you provide public but we generally give you settings to make the information more private if you want. Your public information is broadly and instantly disseminated. For example, your public Tweets are searchable by many search engines and are immediately delivered via SMS and our APIs to a wide range of users and services. You should be careful about all information that will be made public by Twitter, not just your Tweets. 16 <http: //twitter. com/privacy>

3. Ao. IR ethical guidelines 2. 0 But first: very brief history of Internet research ethics … (see: E. Buchanan, “Internet Research Ethics: Past, Present, and Future, ” in M. Consalvo & C. Ess (eds. ), The Blackwell Handbook of Internet Studies, 83108. ) 1990 s (“First Age”) – from hard “virtual / real” // online / offline distinction to: yes, real harm can be enacted online (Dibbell, 1993) occasional articles and a special issue of The Information Society (12, 1996) with articles by C. Allen, S. Boehlefeld, S. King (see Ao. IR Ethics Document, 2002, References, pp. 11 ff. ) 2000 -2002: Ao. IR ethical guidelines working committee, first Ao. IR Ethics Document 2003: NESH guidelines and an explosion of books (Thorseth, 2003, Buchanan, 2004; Johns, Chen & Hall 2004; ) and articles … 2005 -present (“the Buchanan Era”): continued development, including ever-more international discussion – the Ao. IR pre-conference workshops and panels – important NSF grants – Mc. Kee & Porter’s The Ethics of Internet Research (2009) Ao. IR ethical guidelines 2. 017

3. Ao. IR ethical guidelines 2. 0 (A) the status of data (public? private? …? ) provided in social networking profiles Terms of service? Local / international laws? Expectations of users / community / author? additional questions: How do the terms of service articulate privacy of content and/or how it is shared with 3 rd parties ? Does the author/participant consider personal network of connections sensitive information ? How is profile or location information used or stored by researcher ? Does author/participant understand agree to interaction that may be used for research purposes ? Does research purpose and design balance possible conflicts between participant and researcher perceptions of public/private and sensitive/nonsensitive ? 18

3. Ao. IR ethical guidelines 2. 0 (B) “dissemination ethics” and informed consent, especially with regard to profile data and blog posts. Ao. IR 2. 0 questions: Does the dissemination of findings protect confidentiality ? Is the data easily searchable and retrievable ? If the content of a subject’s communication was ever linked to the person, would harm likely result ? 19

4. Ethical variables and Discussion 20

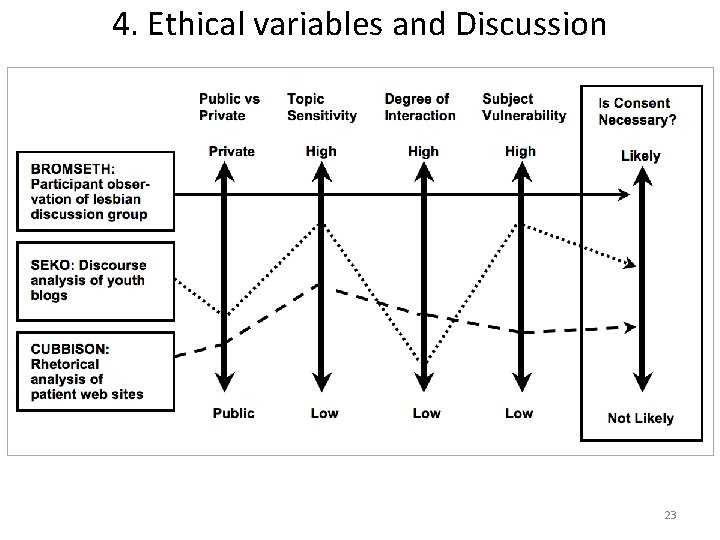
Examples: Yukari Seko (Ph. D student, communications, York University, CA): studied an online forum and blogs for people with suicidal and self-hurting tendencies. Particular difficulties with one young blogger who wrote frequently about own suicide. Laurie Cubbison (assistant prof. , rhetoric & writing, Radford University, USA): studied medical patient support groups develop rhetorical strategies for communicating their views of illness to doctors, support persons, general public. Participant-observer, argues for an ethic of care in research and reporting. Janne Bromseth (cultural, media researcher, Stockholm): studied gendered and sexual identity expression in a listserv for lesbian and bisexual women. Participant-observer, especially sensitive to risks and problems of such women in more conservative, more rural areas of Norway – as itself a relatively small country. -- Mc. Kee & Porter 2009: 76 21

What counts as “sensitive”? Sensitive based on nature of information Personal information or individual views that would expose a person to ridicule, embarrassment, or negative public exposure; That pertain to illegal activity, personal health, sexual activity, religious beliefs, sexual preferences, family background, traumatic or emotionally distressing life experiences (death, injury, abuse), bodily functions, idiosyncratic behaviors, etc. Sensitive based on views of individual or community Personal information or individual views that the person or community regards as sensitive and wants to keep confidential. Who decides? Broad consensus: the (researched) individual and/or the community. -- Mc. Kee & Porter 2009: 88 f. 22

4. Ethical variables and Discussion 23

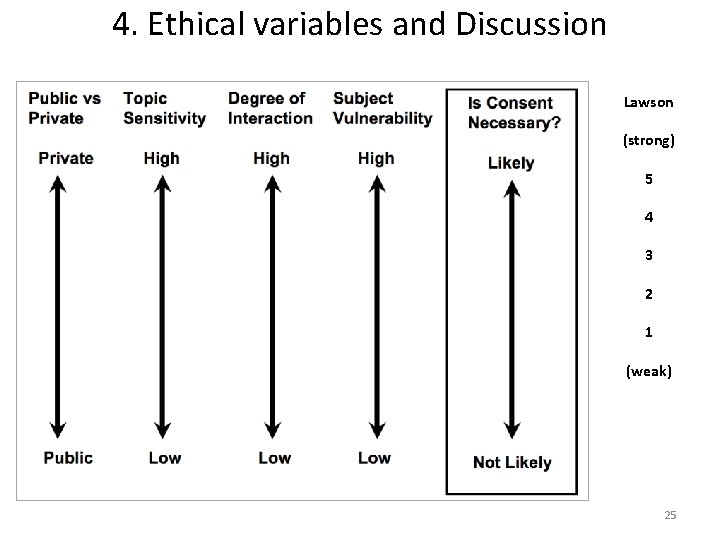
4. Ethical variables and Discussion Lawson offers a range of possible options that researchers can offer to participants: (1) consent to having their nickname and communicative text used for data analysis only (no publication of name or text); (2) consent to having either their nickname or text published in an academic work, but never together (i. e. , no identifiers); (3) consent to having either their nickname or text published in an academic work, but never together (i. e. , no identifiers) and providing they get to see the “write up” prior to publication; (4) consent to having both their nickname and text published in academic work, thereby being credited as the authors of their own words or (5) consent to having both their nickname and text published in academic work, thereby being credited as the authors of their own words, providing they get to see the “write up” prior to publication. The last two options deal directly with the issue of CMC copyright. (2004, 93) 24

4. Ethical variables and Discussion Lawson (strong) 5 4 3 2 1 (weak) 25

A thousand thanks! 26