Internet 2 DNSSEC Pilot Shumon Huque University of















- Slides: 19

Internet 2 DNSSEC Pilot Shumon Huque University of Pennsylvania ESCC/Internet 2 Joint Techs Workshop Minneapolis, Minnesota, U. S. A. , Feb 14 th 2007

Description of the Pilot • http: //www. dnssec-deployment. org/internet 2/ • Deploy DNSSEC • Gain Operational experience • Does it work (does it catch anything? ) • Test DNSSEC aware applications • Participants sign at least one of their zones • Exchange keys (trust anchors) that will allow them to mutually validate DNS data 2 Shumon Huque

What is DNSSEC? • A system to verify the authenticity of DNS “data” • RFC 4033, 4034, 4035 • Helps detect: spoofing, misdirection, cache poisoning • Some secondary benefits appear: • You could store keying material in DNS • DKIM, SSHFP, IPSECKEY, etc 3 Shumon Huque

A little background. . • Feb ‘ 06: DNSSEC Workshop held at Albuquerque Joint Techs • Mar ‘ 06: dnssec@internet 2 mailing list • Apr ‘ 06: Internet 2 Spring Member meeting • Advisory group formed and plans for a pilot project formulated • May ‘ 06: Pilot group began • Bi-weekly conference calls and progress reports 4 Shumon Huque

Co-ordination • Internet 2 • Shinkuro シンクロ • Partner in DNSSEC Deployment Initiative • http: //www. dnssec-deployment. org/ • Some funding from US government 5 Shumon Huque

DNSSEC Deployment Efforts so far • MAGPI Giga. Po. P • All zones: magpi. {net, org} & 15 reverse zones • https: //rosetta. upenn. edu/magpi/dnssec. html • MERIT • radb. net • nanog. org • http: //www. merit. edu/networkresearch/dnssec. html • NYSERNet - test zone • nyserlab. org 6 Shumon Huque

Others considering or planning deployment • University of Pennsylvania • University of California - Berkeley • University of California - Los Angeles • University of Massachusetts - Amherst • Internet 2 7 Shumon Huque

DLV (DNSSEC Lookaside Validation) • A mechanism to securely locate DNSSEC trust anchors “off-path” • An early deployment aid until top-down deployment of DNSSEC happens • Pilot group is in talks to make use of ISC’s DLV registry • http: //www. isc. org/index. pl? /ops/dlv/ • More on this at a later date. . 8 Shumon Huque

More participants welcome! • (participation not restricted to Internet 2) • Join mailing list • Participate in conference calls 9 Shumon Huque

Thoughts on deployment obstacles (1) • A Chicken & Egg problem • Marginal benefits, until much more deployment • Why should I go first? • We had (have? ) the same problem with other technologies (IPv 6 etc) • Some folks will need to take the lead, if there is hope for wider adoption • Good way to find out how well it works 10 Shumon Huque

Thoughts on deployment obstacles (2) • Operational stability • More complicated software infrastructure • New processes for: • • Zone changes Secure delegations Security (protection of crypto keys) Key rollover and maintenance • Integration w/ existing DNS management software • What is the experience of the pilot? 11 Shumon Huque

Thoughts on deployment obstacles (3) • Additional system requirements • Authoritative servers: memory • Resolvers: memory & CPU • Memory use can be calculated • Probably not a big issue (unless you’re. COM!) • CPU • Not too much of an issue today (dearth of signed data that needs validation) • Caveat: some potential Do. S attacks could hit CPU 12 Shumon Huque

Thoughts on deployment obstacles (4) • Key distribution in islands of trust • Why is there no top down deployment? • Work on signing root and (many) TLDs and inaddr. arpa is in progress • . SE, RIPE reverse done • . EDU work in motion • Interim mechanisms like DLV exist • Manual key exchange (unscalable) 13 Shumon Huque

Thoughts on deployment obstacles (5) • Stub resolver security (e 2 e security) • An area of neglect in my opinion • Push DNSSEC validation to endstations? • Secure path from stub resolver to recursive resolver • Possibilities: SIG(0), TSIG, IPSEC 14 Shumon Huque

Thoughts on deployment obstacles (6) • Application layer feedback • Coming gradually • DNSSEC aware resolution APIs and applications enhanced to use them • DNSSEC aware applications • See http: //www. dnssec-tools. org/ • Note: some folks think it might be nice to protect DNSSEC oblivious applications silently as an interim step 15 Shumon Huque

Thoughts on deployment obstacles (7) • Zone enumeration threat • See NSEC 3 record (spec almost done) • draft-ietf-dnsext-nsec 3 -09. txt 16 Shumon Huque

References • Internet 2 DNSSEC Pilot • http: //www. dnssec-deployment. org/internet 2/ • http: //rosetta. upenn. edu/magpi/dnssec. html • Mailing list: dnssec@internet 2. edu • https: //mail. internet 2. edu/wws/info/dnssec • Internet 2 DNSSEC Workshop • http: //events. internet 2. edu/2006/jtalbuquerque/session. Details. cfm? session=2491&ev ent=243 17 Shumon Huque

References (2) • DNSSEC(bis) technical specs: • RFC 4033, 4034, 4035 • Related: • DNSSEC HOWTO: • http: //www. nlnetlabs. nl/dnssec_howto/ • • • 18 Threat analysis of the DNS: RFC 3833 Operational practices: RFC 4641 NSEC 3: draft-ietf-dnsext-nsec 3 -09 DLV: draft-weiler-dnssec-dlv-01 draft-hubert-dns-anti-spoofing-00 Shumon Huque

Questions? • Shumon Huque • shuque -at- isc. upenn. edu 19 Shumon Huque
 Dnssec analyzer
Dnssec analyzer Internet or internet
Internet or internet 沈榮麟
沈榮麟 Md mizanur rahman pilot
Md mizanur rahman pilot Wings pilot proficiency program
Wings pilot proficiency program Kilanga congo
Kilanga congo Direct changeover
Direct changeover Pilot conversion advantages and disadvantages
Pilot conversion advantages and disadvantages Plural of pilot
Plural of pilot Landos co pilot
Landos co pilot Large scale fermenter design
Large scale fermenter design Pilot csöves áramlásmérő
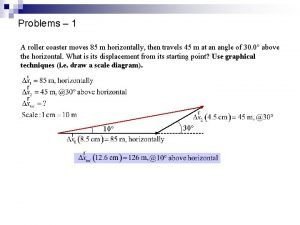
Pilot csöves áramlásmérő A football player runs directly down the field for 35 m
A football player runs directly down the field for 35 m Dieter eppler pilot
Dieter eppler pilot Pilot testing meaning
Pilot testing meaning Pilot study adalah
Pilot study adalah La pilot
La pilot Pilot club international logo
Pilot club international logo First deaf pilot
First deaf pilot Pilot plan template six sigma
Pilot plan template six sigma