International Conference Security in Pervasive ComputingSPC 06 MMC











- Slides: 17

International Conference Security in Pervasive Computing(SPC’ 06) MMC Lab. 임동혁

Introduction Related Works Specification Verification Implementation Conclusions

Limitation of sensor Storage Computational Complexity Amount of Data Transmission Range Authenticating sensor reading, confidentiality Assumptions Limited number of sensors in the range of the base station Invulnerable and powerful base station No location awareness, no network topology

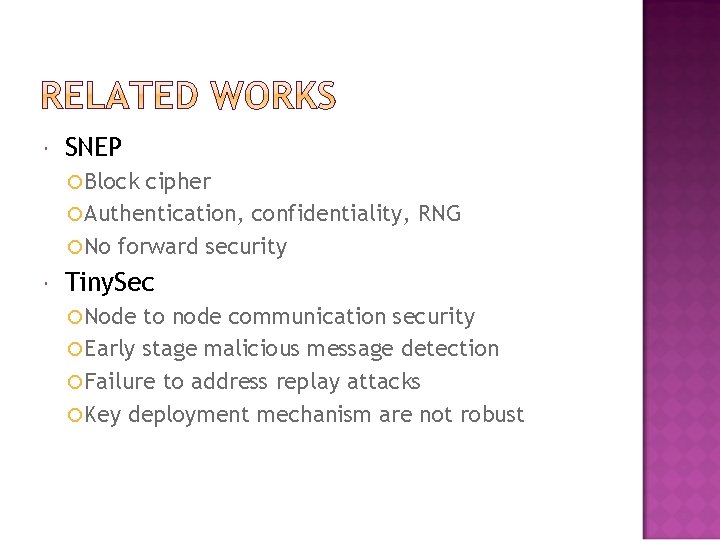
SNEP Block cipher Authentication, confidentiality, RNG No forward security Tiny. Sec Node to node communication security Early stage malicious message detection Failure to address replay attacks Key deployment mechanism are not robust

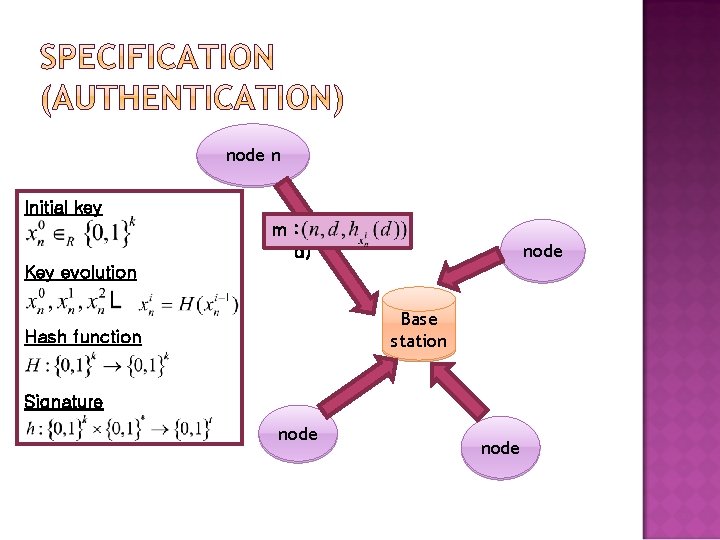
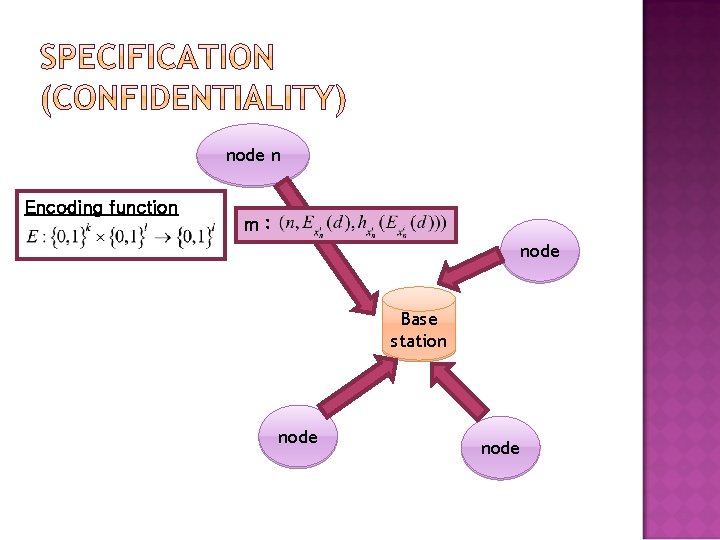
Authentication Confidentiality Freshness Forward Security Continuously evolving key

node n Initial key m : (n, d) node Key evolution Base station Hash function Signature node

node n Encoding function mm : : node Base station node

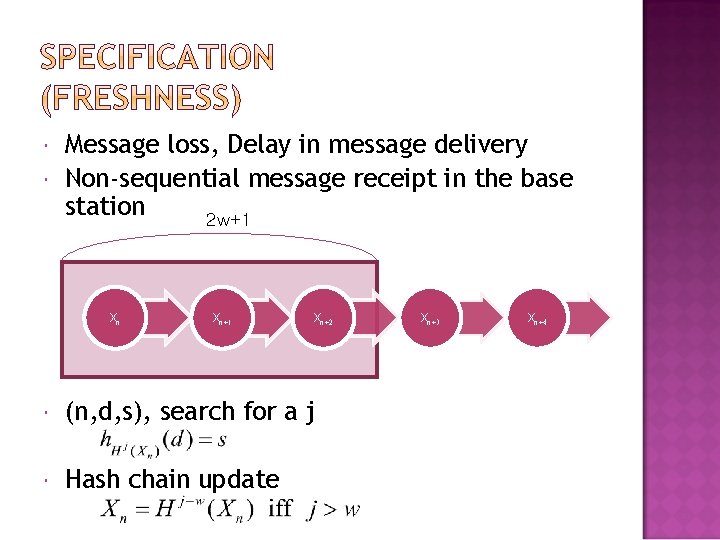
Message loss, Delay in message delivery Non-sequential message receipt in the base station 2 w+1 Xn Xn+1 Xn+2 (n, d, s), search for a j Hash chain update Xn+3 Xn+4

Signature Forgery Confidentiality Violation Forward Security

Signature forgery attack Without Constructing a valid signature at knowledge of key x, constructing (n, d, s) most 2 -t ( t <= k ) Acceptable keys Probability of successful forgery at most 2 -t+log(2 w+1)

Attack can query OC Attack is successful Attacker gets any information on d other than |d| Probability distribution: Uniform over {0, 1}|d| E is random oracle Input to E is unique Without , cannot be distinguished from

Assumption Attacker can physically extract or obtain Oracle Attacker can query OF at input (n, j) not (n, i), Non-invertibility of H Knowledge of Do not help to decipher message under any key ,

Resource requirements Hash Function MAC Function Encryption Function Choice of Security Parameter Size

Hash function (SHA-1) Non-invertibility Collision resistance property 15 µJ is required to establish a new key assuming k=160 Code size 2000 byte MAC function HMAC-SHA 1 -t 1 µJ/byte is required to generate a signature

Encryption Function G : non-invertible collision resistant hash function Encryption Code Function E size/Chip area viewpoint G, H use the same concrete hash function Choice of Security Parameter Sizes k : the size of the key (160 bit) t : the size of the signature (64 bit)

Wireless sensor networks Authentication of the origin data Confidentiality of data Forward security Freshness Minimise the resource requirements Low computational complexity using a hash function No data expansion to minimise the communication overhead

Problems Only the base station verifies the messages DOS attack Acceptance window messages can be ignored