Information Systems Management ISM Lesson 3 Security management








- Slides: 16

Information Systems Management (ISM) Lesson 3: Security management 21 april 2005 Marco Extra

Planning and agenda What Who When ● Introduction Marco & Hans 12 -04 ● Configuration Management Hans 14 -04 ● Security Management Marco 21 -04 ● Practice councilling Marco & Hans 28 -04 ● Change Management Hans ● Accounting & Availability Management Marco & Hans 19 -05 ● Excursion IT centre Fortis Bank NL 26 -05 12 -05 Marco & Hans

Introduction • The MCM Paradigm • ITIL • Security management • What is security? • Security management components • Structuring security measures • Administration and reporting

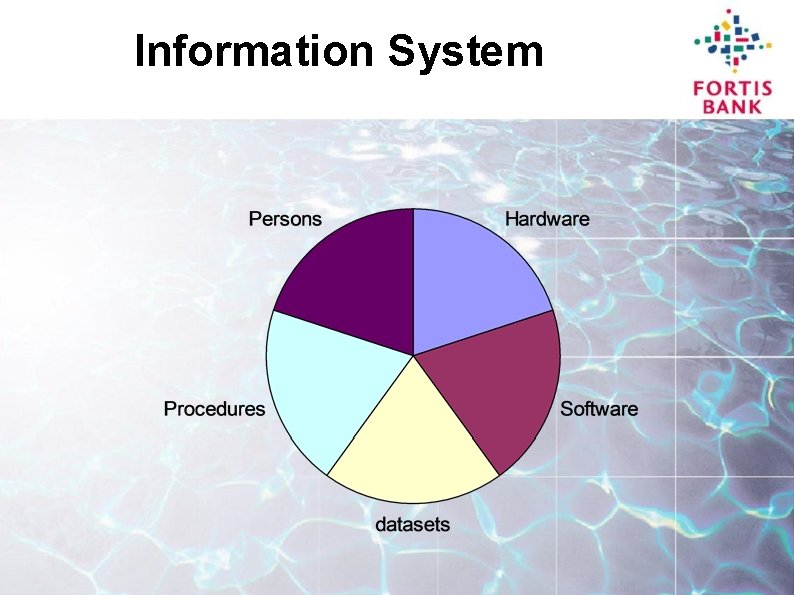
Information System

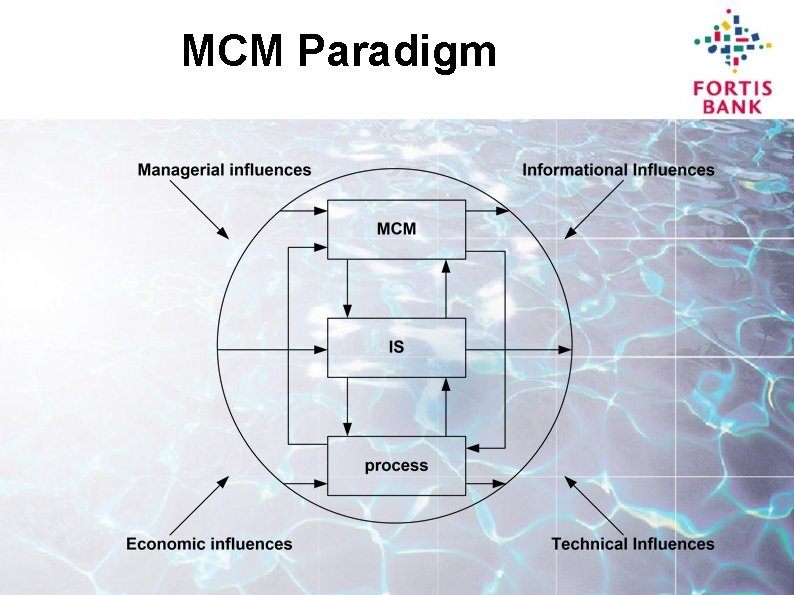
MCM Paradigm

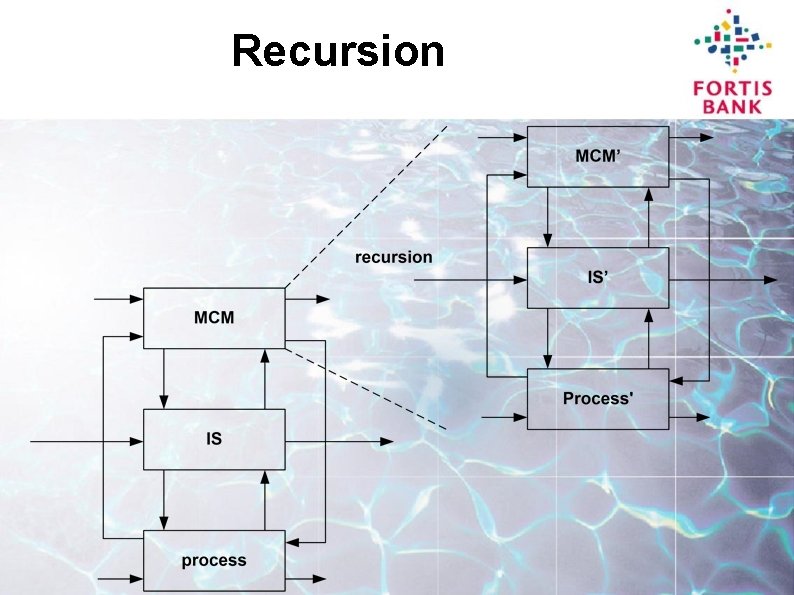
Recursion

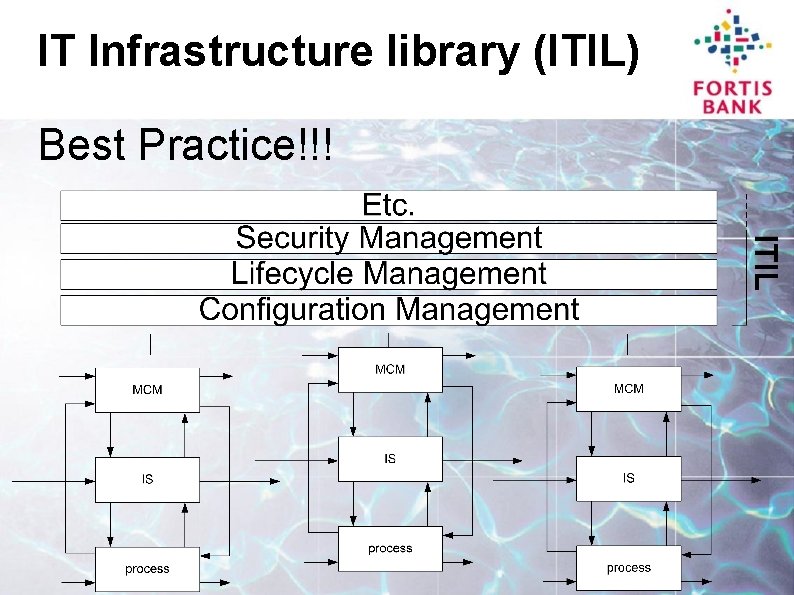
IT Infrastructure library (ITIL) Best Practice!!!

What is security? • • • Don't confuse Security with Safety! Basic question: WHO should do WHAT? Basic concepts: • WHO = which employee • WHAT = which part of the infrastructure • should do = needs in order to do his job

Security Management components • WHO: Human Resource Management • WHAT: Configuration Management An excellent relation to these departments is essential (but only if they're doing their job).

What do we want form HRM? • Who is employed? What is their job? • Who is joining? When? What will be their job? • Who is leaving? Who goes voluntary? When? • Who is being promoted? When? • Who is on a prolonged leave?

What do you want to know from Configuration Management? ● ● Whatever there is! When you don't know it's there, you can't secure it! BTW. . When something new is coming up, is modified or is removed, you want to know that too!

Life Cycle Management – – – It is good to know what is being used. . Because some products have inherent defects. . Patch management becomes feasible this way. .

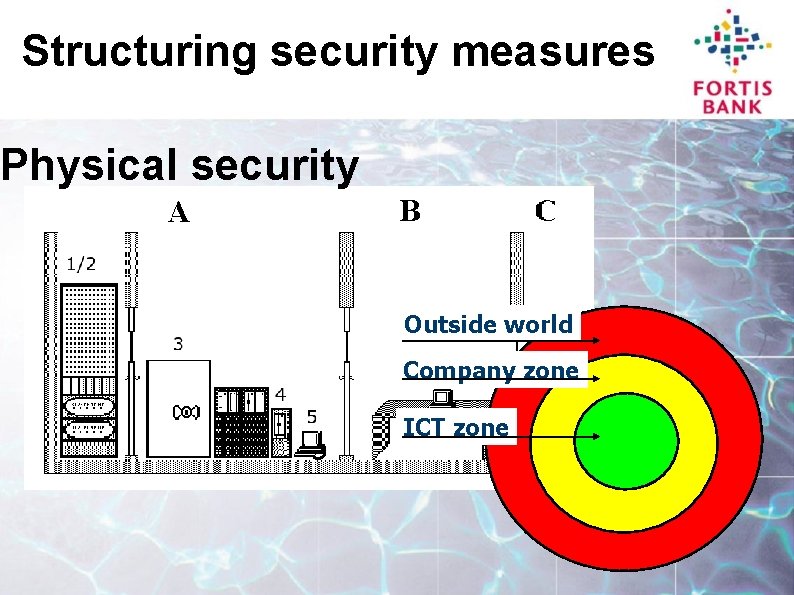
Structuring security measures Physical security Outside world Company zone ICT zone

Structuring security measures Logical security Define different user groups: • Per zone • Per application • Per job description Use information supplied by HRM and/or Business Management

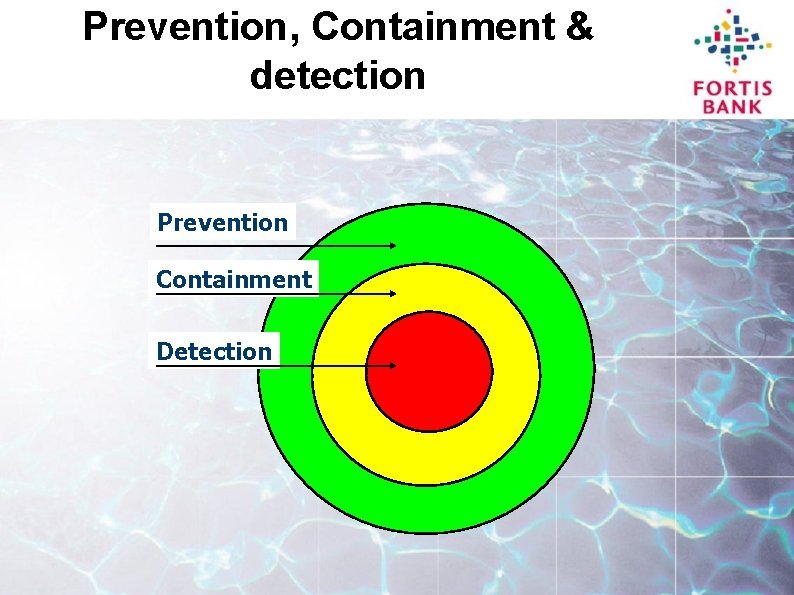
Prevention, Containment & detection Prevention Containment Detection

Administration • User. IDs • Profiles • Personnel numbers • Detections and incidents • Authorisations