INFORMATION SECURITY MANAGEMENT LECTURE 8 RISK MANAGEMENT CONTROLLING









- Slides: 26

INFORMATION SECURITY MANAGEMENT LECTURE 8: RISK MANAGEMENT CONTROLLING RISK You got to be careful if you don’t know where you’re going, because you might not get there. – Yogi Berra

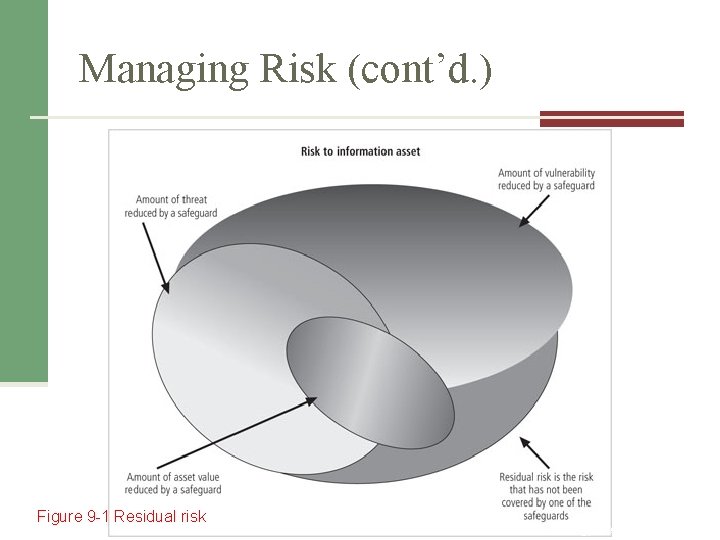
Managing Risk (cont’d. ) Figure 9 -1 Residual risk Source: Course Technology/Cengage Learning

Managing Risk – Risk Control • Risk control involves selecting one of the four risk control strategies Should the organization ever accept the risk?

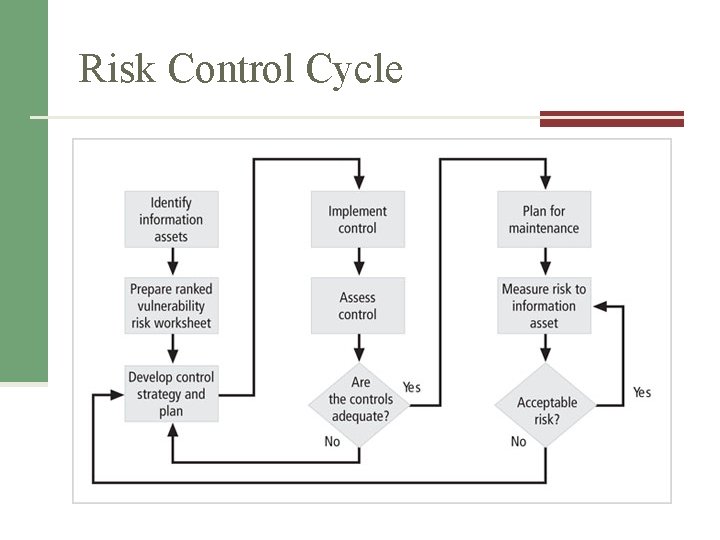
Risk Control Cycle Figure 9 -3 Risk control cycle Source: Course Technology/Cengage Learning

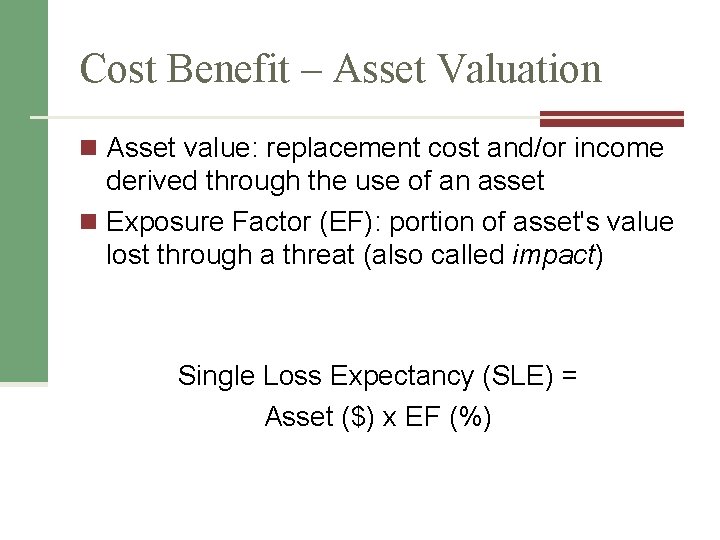
Cost Benefit – Asset Valuation n Asset value: replacement cost and/or income derived through the use of an asset n Exposure Factor (EF): portion of asset's value lost through a threat (also called impact) Single Loss Expectancy (SLE) = Asset ($) x EF (%)

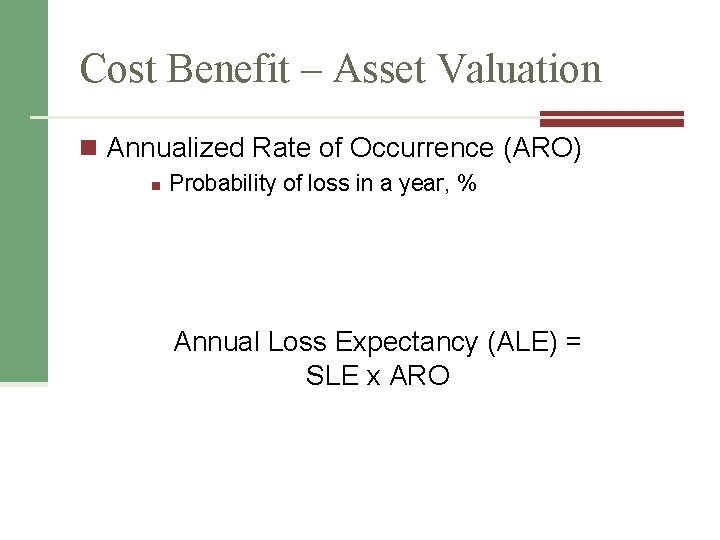
Cost Benefit – Asset Valuation n Annualized Rate of Occurrence (ARO) n Probability of loss in a year, % Annual Loss Expectancy (ALE) = SLE x ARO

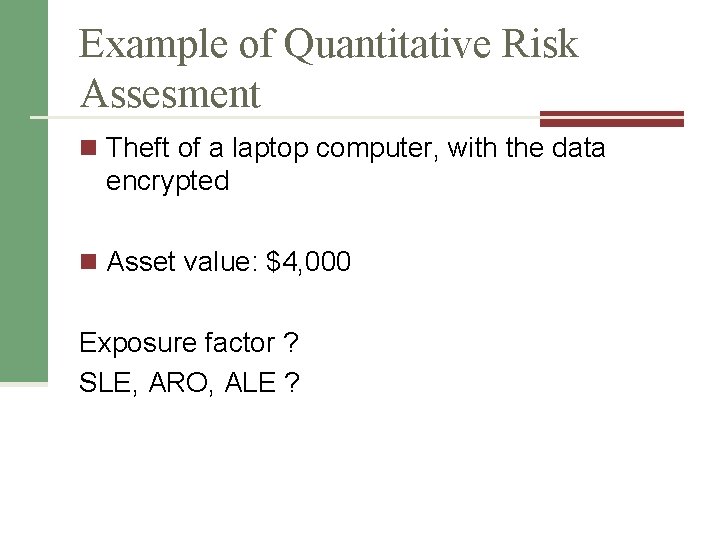
Example of Quantitative Risk Assesment n Theft of a laptop computer, with the data encrypted n Asset value: $4, 000 Exposure factor ? SLE, ARO, ALE ?

Example of Quantitative Risk Assesment n Dropping a laptop computer and breaking the screen n Asset value: $4, 000 Exposure factor ? SLE, ARO, ALE ?

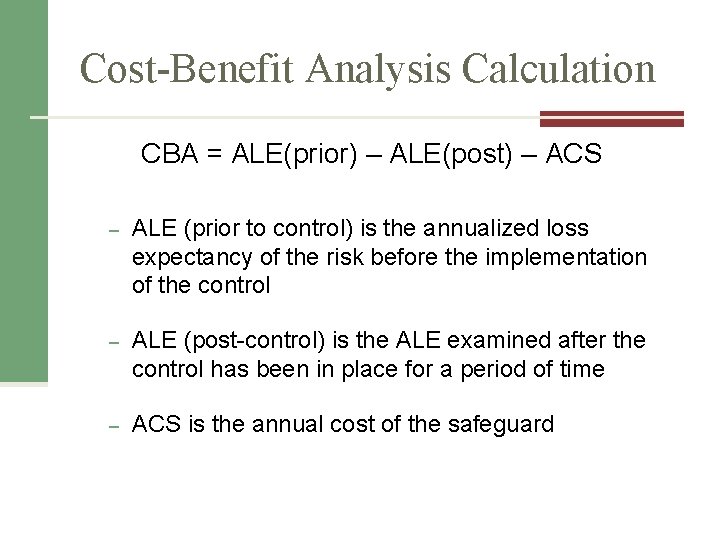
Cost-Benefit Analysis Calculation CBA = ALE(prior) – ALE(post) – ACS – ALE (prior to control) is the annualized loss expectancy of the risk before the implementation of the control – ALE (post-control) is the ALE examined after the control has been in place for a period of time – ACS is the annual cost of the safeguard

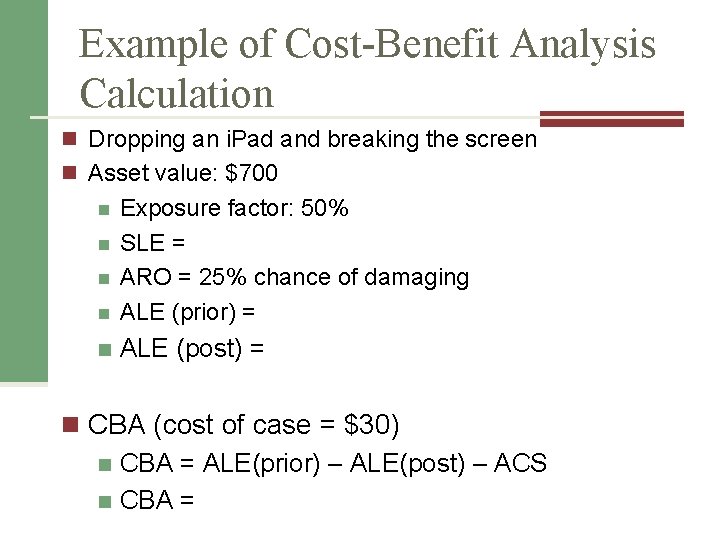
Example of Cost-Benefit Analysis Calculation n Dropping an i. Pad and breaking the screen n Asset value: $700 n Exposure factor: 50% SLE = ARO = 25% chance of damaging ALE (prior) = n ALE (post) = n n CBA (cost of case = $30) n CBA = ALE(prior) – ALE(post) – ACS n CBA =

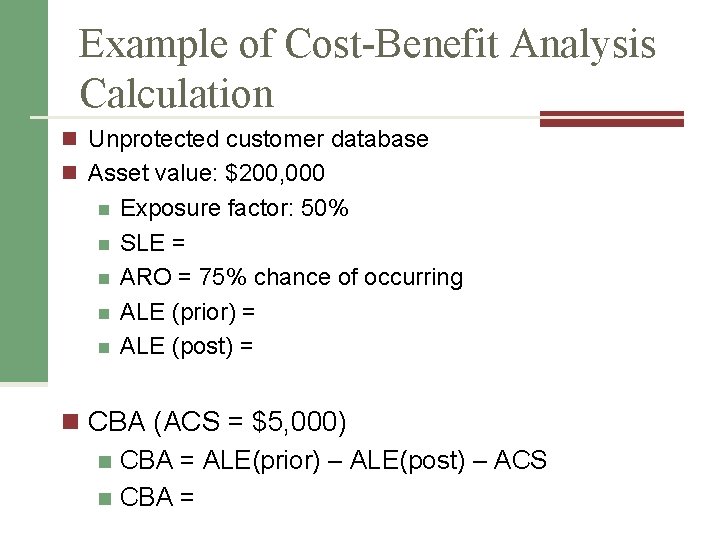
Example of Cost-Benefit Analysis Calculation n Unprotected customer database n Asset value: $200, 000 n n n Exposure factor: 50% SLE = ARO = 75% chance of occurring ALE (prior) = ALE (post) = n CBA (ACS = $5, 000) n CBA = ALE(prior) – ALE(post) – ACS n CBA =

Recommended Risk Control Practices • Qualitative/Quantitative Approach • Octave Methods • Microsoft Risk Management Approach • FAIR

Qualitative and Hybrid Measures • Quantitative assessment • Qualitative assessment • Hybrid assessment

OCTAVE Method • The Operationally Critical Threat, Asset, and Vulnerability Evaluation (OCTAVE) Method • Variations of the OCTAVE method – The original OCTAVE method – OCTAVE-S – OCTAVE-Allegro www. cert. org/octave/

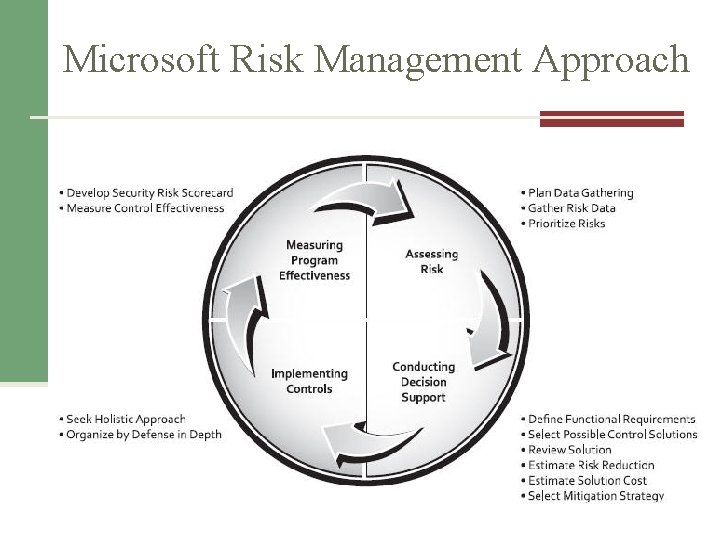
Microsoft Risk Management Approach • Four phases in the Microsoft Info. Sec risk management process: – – Assessing risk Conducting decision support Implementing controls Measuring program effectiveness www. cert. org/octave/omig. html

Microsoft Risk Management Approach Figure A-1 Security Risk Management Guide Source: Course Technology/Cengage Learning

Factor analysis of Information Risk (FAIR) • Basic FAIR analysis is comprised of four stages: • Stage 1 - Identify scenario components • Stage 2 - Evaluate loss event frequency • Stage 3 - Evaluate probable loss magnitude(PLM) • Stage 4 - Derive and articulate Risk • Unlike other risk management frameworks, FAIR relies on the qualitative assessment of many risk components using scales with value ranges, for example very high to very low http: //fairwiki. riskmanagementinsight. com

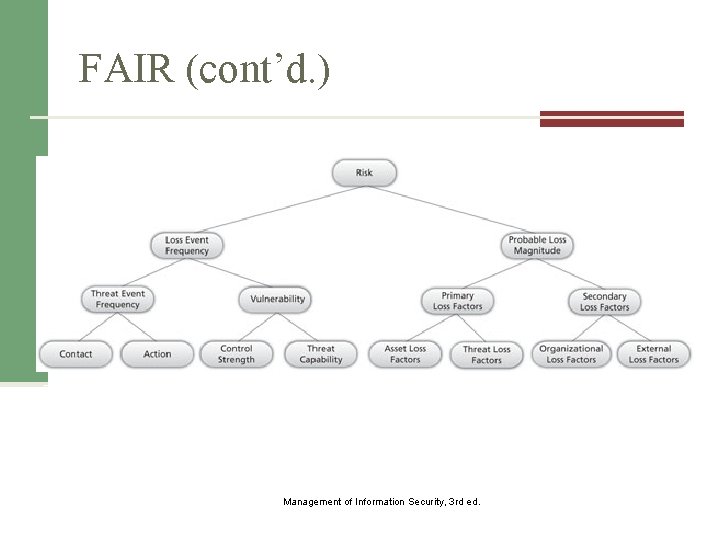
FAIR (cont’d. ) Figure 9 -4 Factor analysis of information risk (FAIR) Management of Information Security, 3 rd ed. Source: Course Technology/Cengage Learning (Based on concepts from Jack A. Jones)

HEALTH FIRST CASE STUDY Analyzing Risk

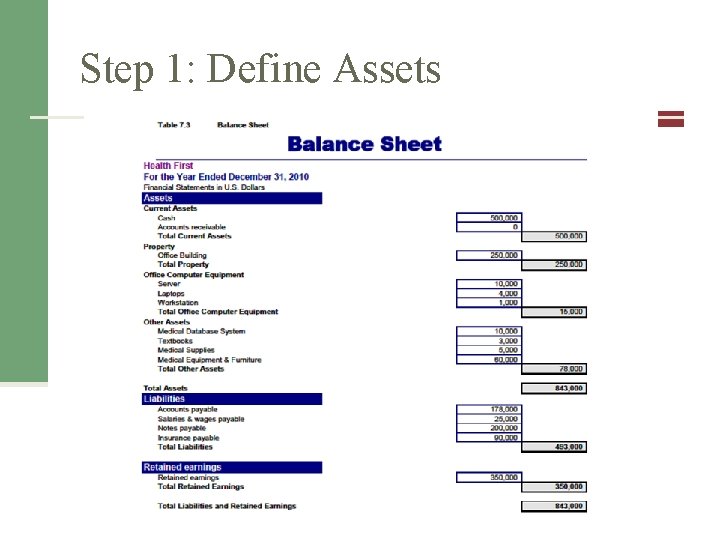
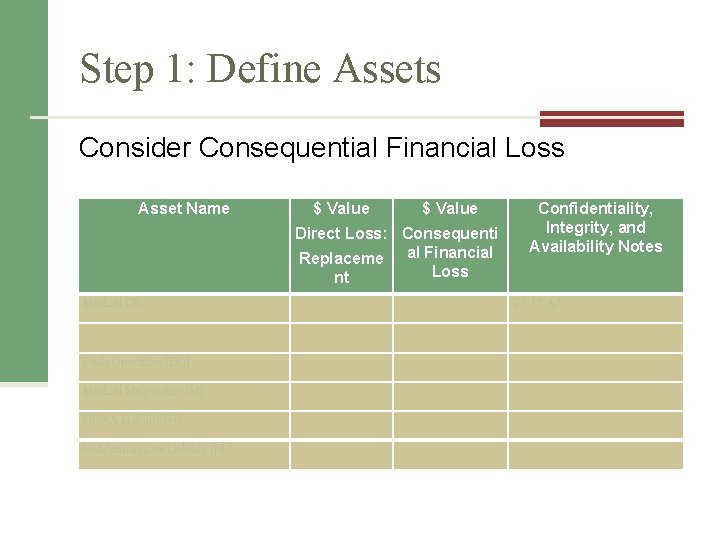
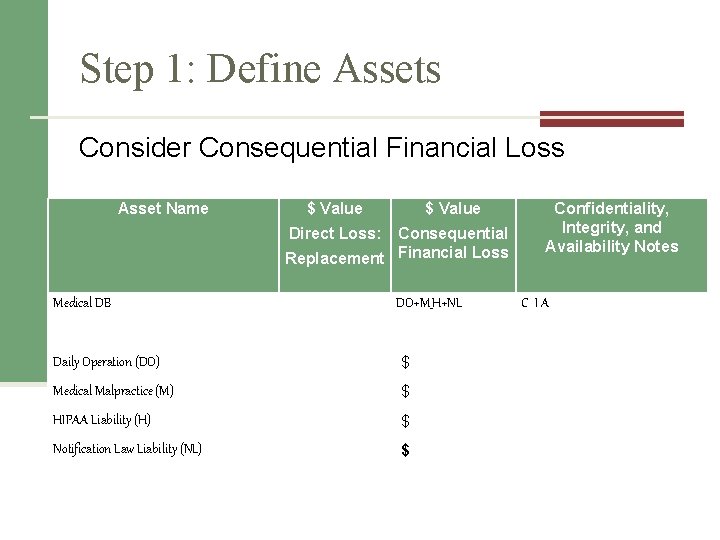
Step 1: Define Assets

Step 1: Define Assets Consider Consequential Financial Loss Asset Name $ Value Confidentiality, Integrity, and Availability Notes Direct Loss: Consequenti Replaceme al Financial Loss nt Medical DB C? I? A? Daily Operation (DO) Medical Malpractice (M) HIPAA Liability (H) Notification Law Liability (NL)

Step 1: Define Assets Consider Consequential Financial Loss Asset Name $ Value Confidentiality, Integrity, and Availability Notes Direct Loss: Consequential Replacement Financial Loss Medical DB DO+M_H+NL C IA Daily Operation (DO) $ Medical Malpractice (M) $ HIPAA Liability (H) $ Notification Law Liability (NL) $

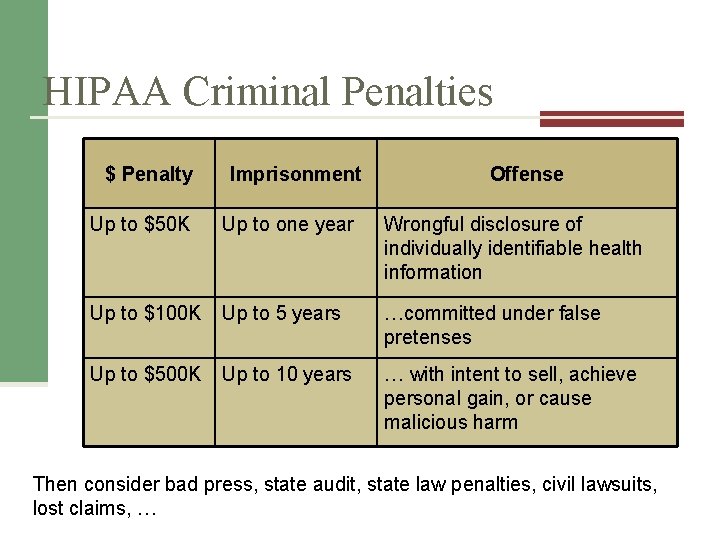
HIPAA Criminal Penalties $ Penalty Imprisonment Offense Up to $50 K Up to one year Wrongful disclosure of individually identifiable health information Up to $100 K Up to 5 years …committed under false pretenses Up to $500 K Up to 10 years … with intent to sell, achieve personal gain, or cause malicious harm Then consider bad press, state audit, state law penalties, civil lawsuits, lost claims, …

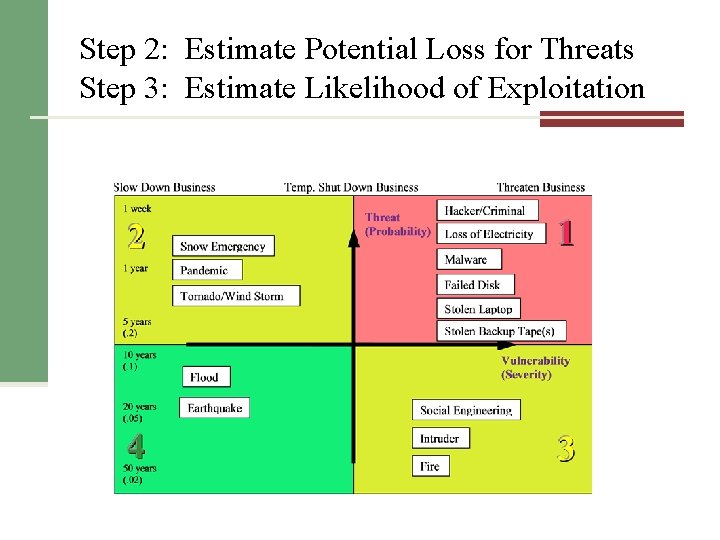
Step 2: Estimate Potential Loss for Threats Step 3: Estimate Likelihood of Exploitation n Normal threats: Threats common to all organizations n Inherent threats: Threats particular to your specific industry n Known vulnerabilities: Previous audit reports indicate deficiencies.

Step 2: Estimate Potential Loss for Threats Step 3: Estimate Likelihood of Exploitation

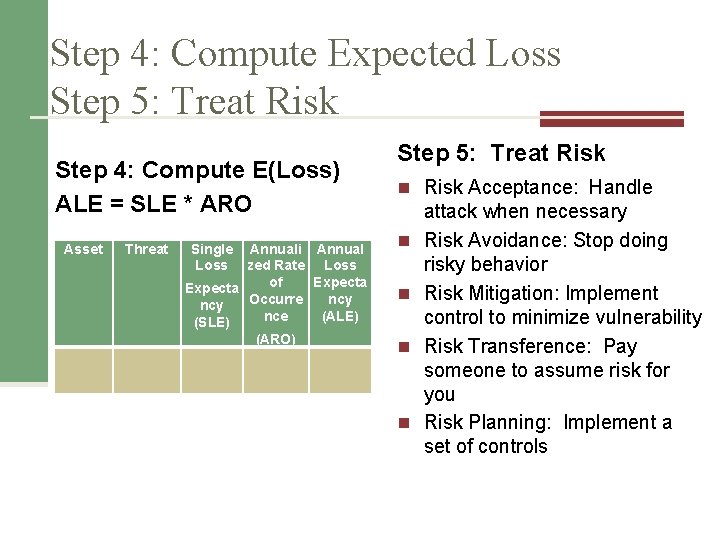
Step 4: Compute Expected Loss Step 5: Treat Risk Step 4: Compute E(Loss) ALE = SLE * ARO Asset Threat Single Annuali Annual Loss zed Rate Loss of Expecta Occurre ncy nce (ALE) (SLE) (ARO) Step 5: Treat Risk n Risk Acceptance: Handle n n attack when necessary Risk Avoidance: Stop doing risky behavior Risk Mitigation: Implement control to minimize vulnerability Risk Transference: Pay someone to assume risk for you Risk Planning: Implement a set of controls