Information Security Crisis Management Daryl Goodwin How Does











- Slides: 13

Information Security Crisis Management Daryl Goodwin

How Does a Crisis Occur? • Daily events that occur through the workday are monitored as they enter an organizations network. A situation that causes a threat is considered an “incident”. There are five indicators that show an incident has occurred: – – – Use of Dormant Accounts Changes to Logs Presence of Hacker Tools Notifications by Partners or Peers Notification by Hacker

How Does a Crisis Occur? • If an incident is either not detected early enough or is not taken care of, it becomes more serious. In some cases, this will escalate into a disaster. When a disaster occurs and heavily effects normal business operations, it can be considered a crisis. • A crisis can also be caused by a natural disaster such as an earthquake or damage from lightning.

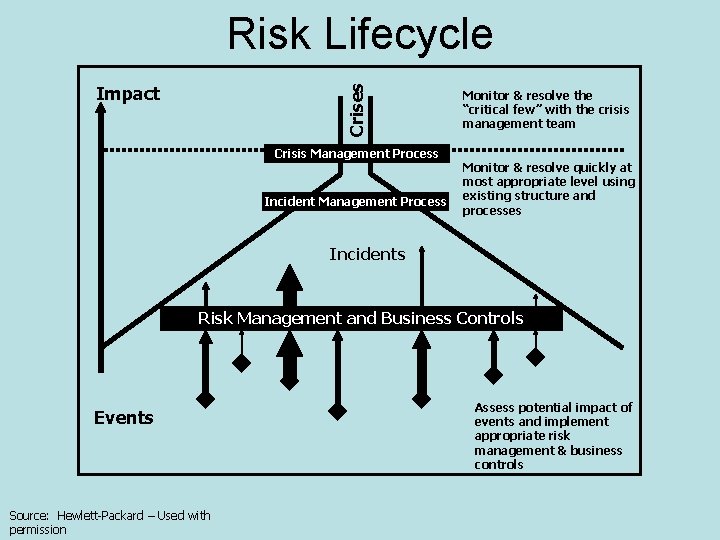
Risk Lifecycle Crises Impact Crisis Management Process Incident Management Process Monitor & resolve the “critical few” with the crisis management team Monitor & resolve quickly at most appropriate level using existing structure and processes Incidents Risk Management and Business Controls Events Source: Hewlett-Packard – Used with permission Assess potential impact of events and implement appropriate risk management & business controls

Contingency Planning • Contingency Planning is the overall process of preparing for unexpected events • Three Major Components – Incident Response Plan, Disaster Recovery Plan, and Business Continuity Plan • The process of Crisis Management takes place in the Disaster Recovery Plan

3 Components of Contingency Planning • Incident Response Plan – A process to establish procedures an organization’s staff would follow if it were attacked • Disaster Recovery Plan – A program to limit losses during a disaster and resume business afterwards • Business Continuity Plan – A plan for the continuation of business activities if a catastrophic event occurs, such as the unrecoverable loss of an entire database, building, or operations center. – All three of these plans are equally important and must be designed accordingly to work together.

Crisis Management • The actions or steps taken during and after a disaster. Crisis Management entails a set of focused steps that deal primarily with the people involved • A specific group of people should be chosen prior to a disaster taking place to take care of the situation as efficiently as possible. This group is known as the crisis management team.

Crisis Management Team • • • MAIN RESPONSIBILITIES Supporting personnel during the crisis Determine the events impact on normal business operations Keep the public informed about what occurred and what is being done Communicate with outside parties (media, partners, suppliers, etc. )

Business Continuity Planning • Ensures that critical business functions can continue if a disaster occurs. • Usually managed by CEO • If a disaster makes normal working conditions unsuitable, other options are used by the organization to allow business to function.

Business Continuity Planning • Exclusive-Use Continuity Strategies • – Usually Determined by factor of cost – Hot Site – Fully Functional (All computer equip. ready and software installed) – Warm Site – Partially Functional (Computer equip. available but not necessarily ready for use) – Cold Site – Not Functional (No computer hardware and software available, simply an empty room) • As expected, Hot site is the most expensive where a Cold Site is the cheapest

Business Continuity Planning • Shared-Use Continuity Strategies • Timeshare – Leased in conjunction with a business partner (Similar to sharing an apartment) – Advantage – Allows disaster recovery at lower cost – Disadvantage – More than one share participant needing space at same time • Service Bureau – Service agency that provides facilities in time of need for a fee – Advantage – Service is guaranteed when needed (Due to contract, bureau must supply extra space in time of widespread crisis) – Disadvantage – Contracts negotiated often and rate changes • Mutual Agreement – Contract where two organizations agree to assist each other in time of need – Advantage – Both companies benefit from facilities and resources of each other – Disadvantage – One company constantly using the others services can upset them

Getting Data to Backup Sight • Electronic Vaulting – The process of transferring archived data to the receiving server in the backup site through leased lines or data communication services • Remote Journaling – Online transfer of current transactions. This process is much faster than electronic vaulting but does not provide archived data. • Database Shadowing – Combines the features of electronic vaulting and remote journaling, by storing transaction data online and the database is written to separate locations simultaneously

Questions?