Information Leaks Without Memory Disclosures Remote Side Channel










- Slides: 12

Information Leaks Without Memory Disclosures: Remote Side Channel Attacks on Diversified Code Jeff Seibert, Hamed Okhravi, and Eric Söderström Presented by Samuel Suddath

Introduction § Problem: detailed knowledge of code layout is required to execute a code reuse attack, such as what code is in memory, and where in memory the code is located. § In order to provide security, systems diversify code to make such attacks harder: having an element of randomness or change to where code is located, or even what code is used. § These techniques rely on the assumption that since the attacker cannot read the code in memory, then he cannot know what code is there nor where it is located, resulting in the attacker not being able to reliably exploit the code. § Two answers: Entropy Attacks and Memory Disclosure Vulnerabilities

Entropy Attacks § Are brute force attacks § Attempt to exploit diversification techniques that do not introduce enough randomness § Will eventually allow the hacker to guess how code has been diversified § Countered by diversification techniques with high degrees of complexity and randomness

Memory Disclosure Vulnerabilities § Allow a hacker to read contents of memory directly and dynamically during runtime § Allows a hacker to know exactly how code has been diversified without guessing § Requires finding two specialized vulnerabilities: read and writing to unintended memory.

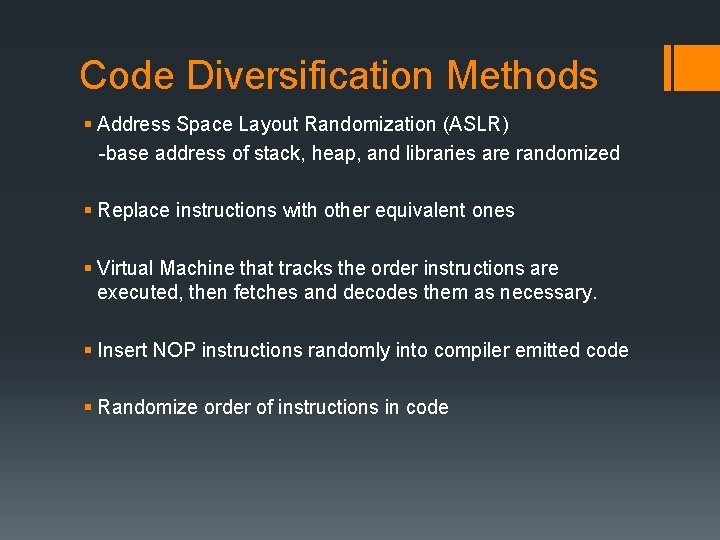
Code Diversification Methods § Address Space Layout Randomization (ASLR) -base address of stack, heap, and libraries are randomized § Replace instructions with other equivalent ones § Virtual Machine that tracks the order instructions are executed, then fetches and decodes them as necessary. § Insert NOP instructions randomly into compiler emitted code § Randomize order of instructions in code

Side Channel Attacks on Cryptography § Timing- execution time can be used to infer a secret key § Fault Analysis- faults can be induced which corrupt memory and allow the secret key to be inferred through analyzing output § Cache- Cache hits and misses can leak information about execution time and allow cryptographic keys to be inferred § Physical- there are many attacks that can only be performed when the hacker has physical access to the target machine, where the hacker uses various physical information streams(power usage, sound output, EM field) to discern the secret key.

How They Work § Hackers choose either a memory address and attempt to locate the gadget there, or choose a gadget and attempt to find its location § Hackers must be able to receive feedback, either through a network or through a scripting environment. § If gadgets can be accessed, they can be used to build an info -leak attack § Most exploits require code that handles crashes by restarting, as invalid memory access faults are caused often by the attack

Fault Analysis Attacks § Works by sending a “payload”, receiving the result of the execution, and then interpret the return. The repeated execution of this attack can be used to reveal where the executed code is located. § Types: § Overwrite Data: overwrite data used as an index to determine where in memory code is located § Overwrite Data Pointer: overwrite a data pointer so that a computation is done on a specific memory location, revealing where and what changes have been made to code. § Overwrite Code Pointer: overwrite a code pointer to cause a computation resulting in a result that could be distinct to a single piece of code.

Timing Attacks § Start a timer, send the “payload”, receive a signal upon completion of execution, stop the timer. The timing can reveal information about the code. § Types: § Crafted Input: similar to timing attacks in cryptography, sends specific series of inputs to execute different code paths § Overwrite Data: allows the hacker to modify certain variables to execute specific pieces of code. § Overwrite Data Pointer: overwrite a data pointer to reveal memory contents through a timed execution § Overwrite Code Pointer: control flow is manipulated by overwriting code pointers like return addresses and function pointers.

Effectiveness § USS – uncertainty set size § Determining the location of distinct gadgets using byte sequences like 0 x 00 and 0 xff § Return Locations- knowing these locations allow the hacker to determine which function they are exploiting § Output can be used to determine what was executed using fault analysis and timing analysis. § Timing is most likely accessible to the hacker, and while it doesn’t provide as much information as other attacks, can still identify executed functions.

Uses of Side Channels § Most commonly used as a stepping stone to other attacks, providing information on executed functions and memory locations making other attacks possible. § Once gadget locations have been found using side channels, those gadgets can be used to find others in Libc

Defenses § Complete Memory Safety § Re-randomizing pages during execution § Data Space Randomization § Instruction Set Randomization § Insertion of dead code that does not modify execution time § Normalizing every measurement to be the same, preventing timing exploits from leaking data.