Identity Devices Apps Data Microsoft Azure Cloud apps






- Slides: 34


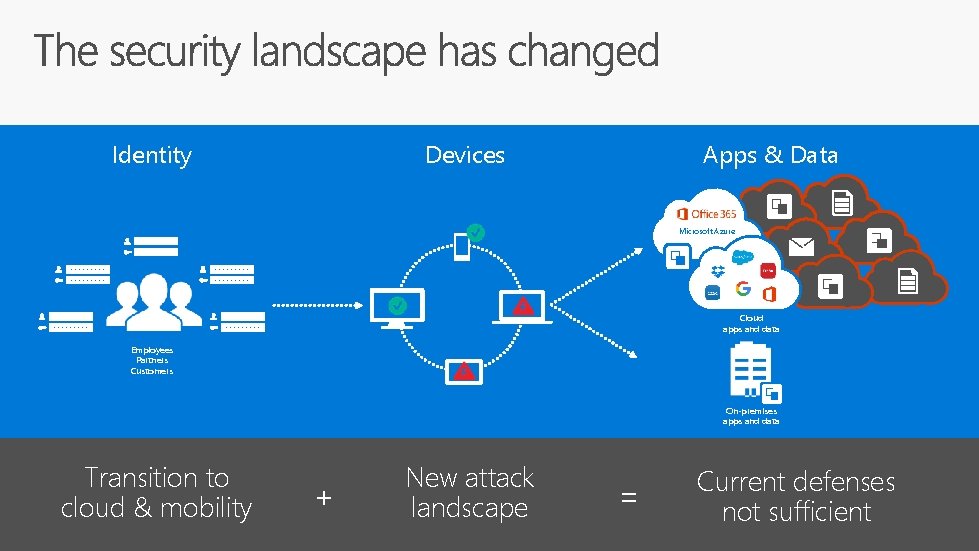
Identity Devices Apps & Data Microsoft Azure Cloud apps and data Employees Partners Customers On-premises apps and data Transition to cloud & mobility + New attack landscape = Current defenses not sufficient

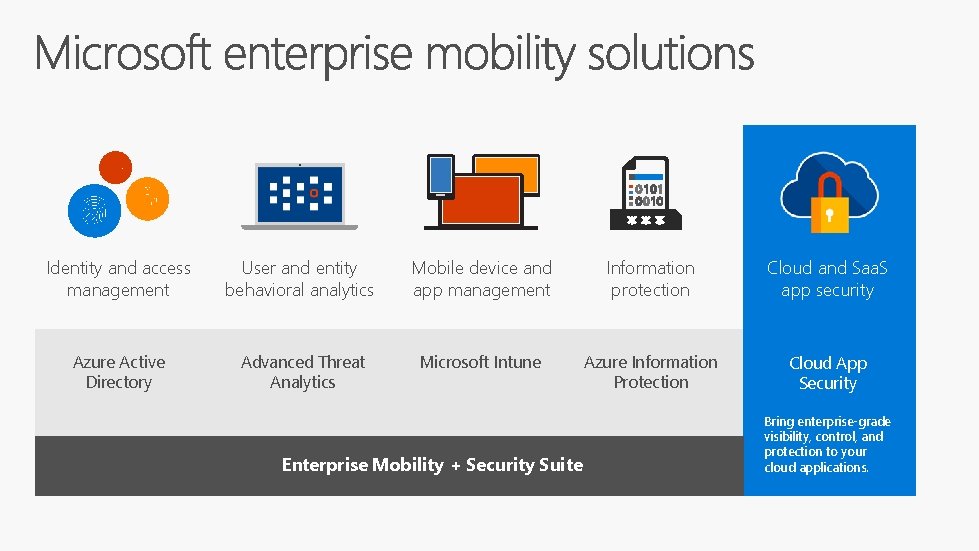
Identity and access management User and entity behavioral analytics Mobile device and app management Information protection Cloud and Saa. S app security Azure Active Directory Advanced Threat Analytics Microsoft Intune Azure Information Protection Cloud App Security Enterprise Mobility + Security Suite Bring enterprise-grade visibility, control, and protection to your cloud applications.

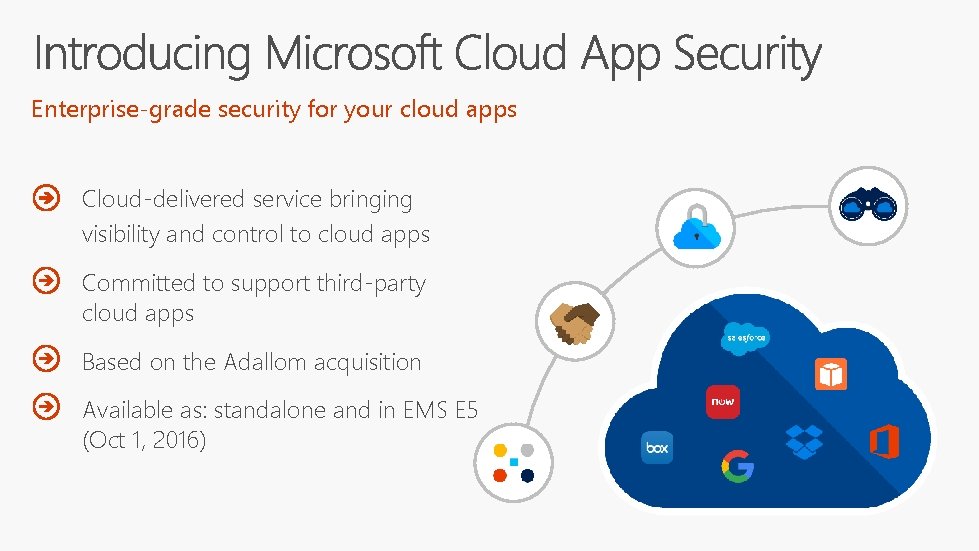
Enterprise-grade security for your cloud apps Cloud-delivered service bringing visibility and control to cloud apps Committed to support third-party cloud apps Based on the Adallom acquisition Available as: standalone and in EMS E 5 (Oct 1, 2016)

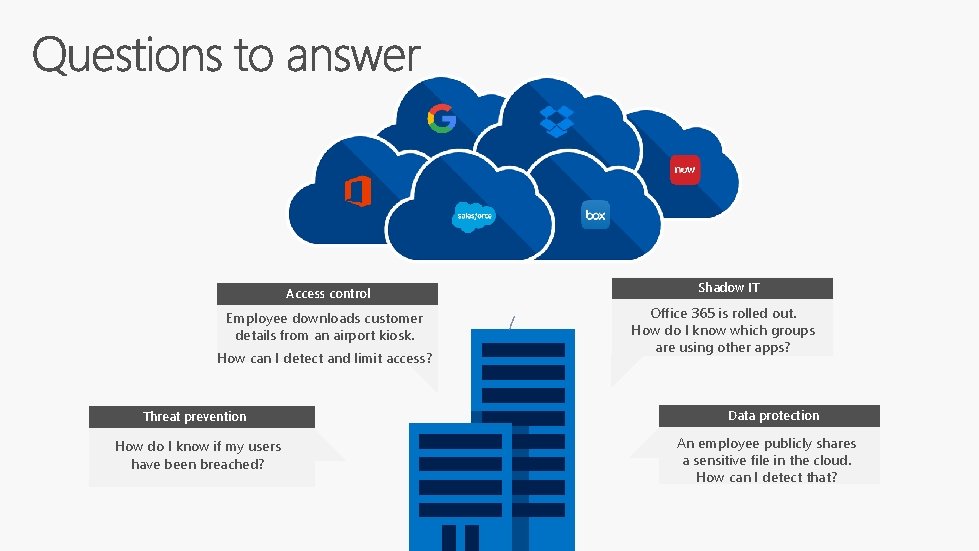
Access control Employee downloads customer details from an airport kiosk. How can I detect and limit access? Threat prevention How do I know if my users have been breached? Shadow IT Office 365 is rolled out. How do I know which groups are using other apps? Data protection An employee publicly shares a sensitive file in the cloud. How can I detect that?

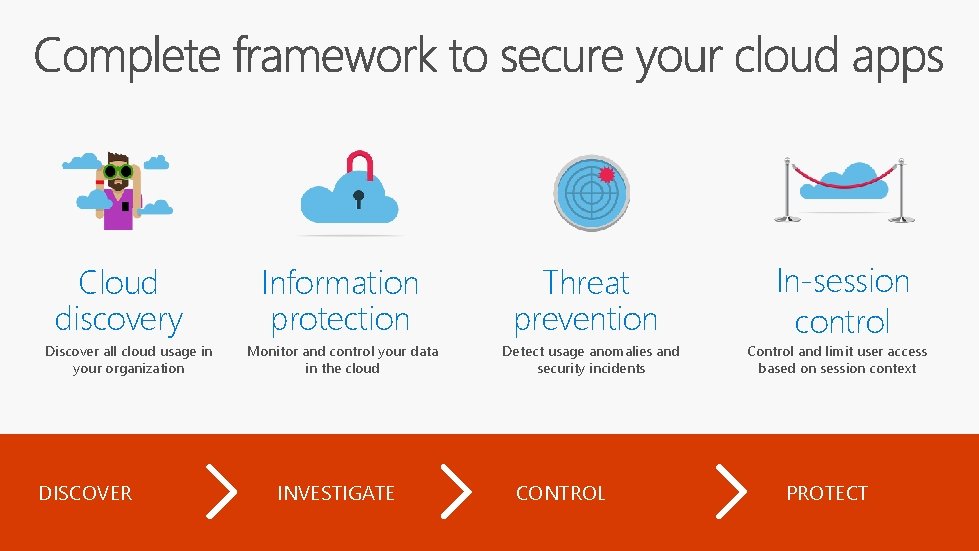
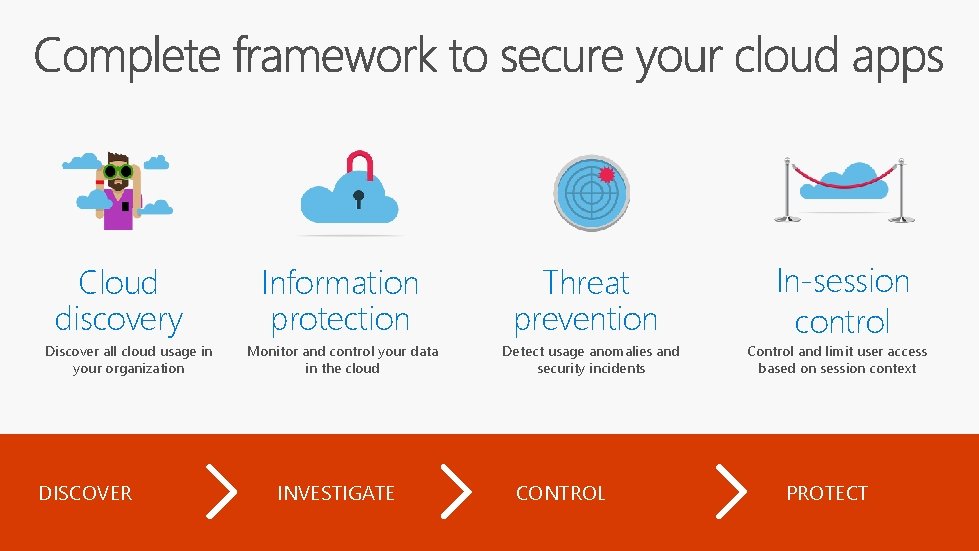
Cloud discovery Discover all cloud usage in your organization DISCOVER Information protection Monitor and control your data in the cloud INVESTIGATE Threat prevention Detect usage anomalies and security incidents CONTROL In-session control Control and limit user access based on session context PROTECT



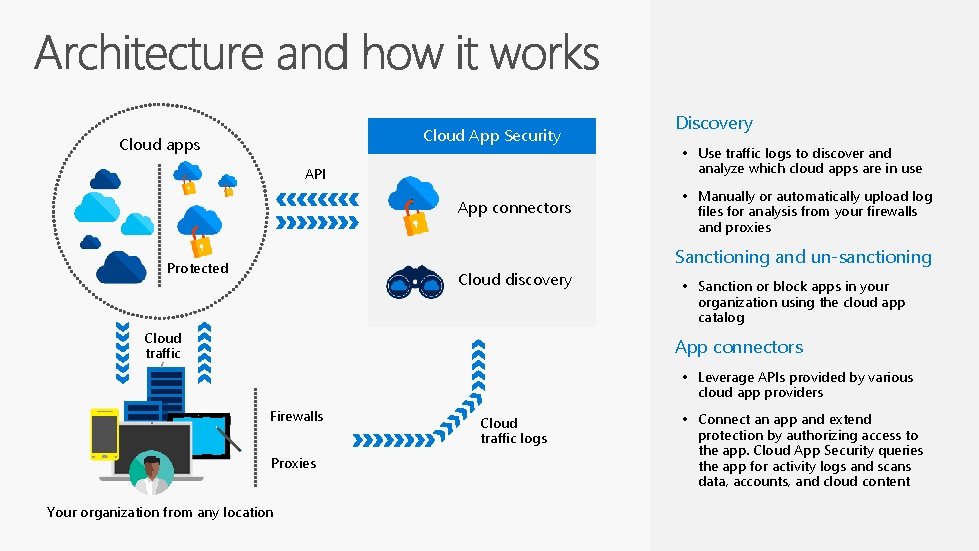
Cloud App Security Cloud apps API App connectors Discovery • Use traffic logs to discover and analyze which cloud apps are in use • Manually or automatically upload log files for analysis from your firewalls and proxies Sanctioning and un-sanctioning Protected Cloud discovery Cloud traffic • Sanction or block apps in your organization using the cloud app catalog App connectors • Leverage APIs provided by various cloud app providers Firewalls Proxies Your organization from any location Cloud traffic logs • Connect an app and extend protection by authorizing access to the app. Cloud App Security queries the app for activity logs and scans data, accounts, and cloud content

Create a trial tenant Log in to your Microsoft work account Live demo Go to www. cloudappsecurity. com Sign up for a free trial Assign licenses to users [at least one]


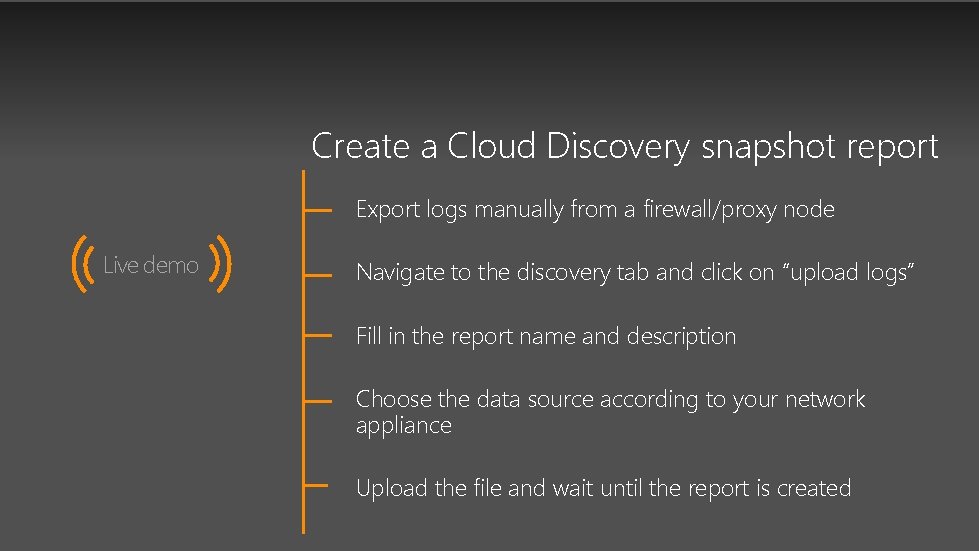
Create a Cloud Discovery snapshot report Export logs manually from a firewall/proxy node Live demo Navigate to the discovery tab and click on “upload logs” Fill in the report name and description Choose the data source according to your network appliance Upload the file and wait until the report is created

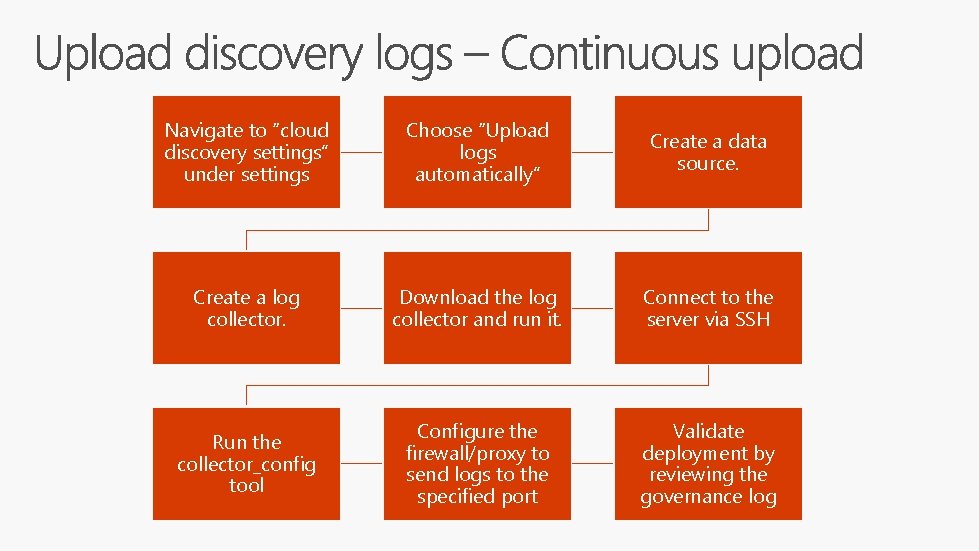
Navigate to “cloud discovery settings” under settings Choose “Upload logs automatically” Create a data source. Create a log collector. Download the log collector and run it. Connect to the server via SSH Run the collector_config tool Configure the firewall/proxy to send logs to the specified port Validate deployment by reviewing the governance log

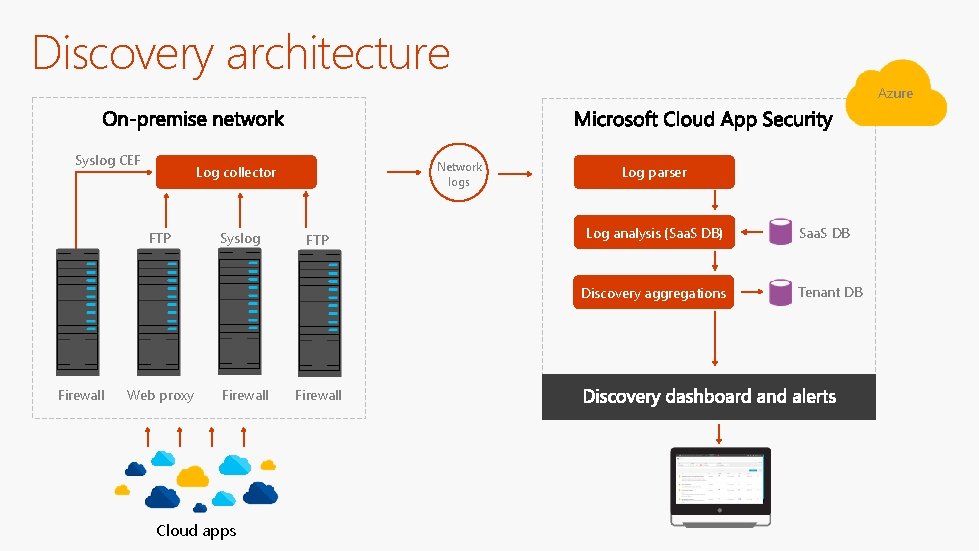
Discovery architecture Azure Syslog CEF Network logs Log collector FTP Syslog FTP Log parser Log analysis (Saa. S DB) Discovery aggregations Firewall Web proxy Firewall Cloud apps Firewall Saa. S DB Tenant DB

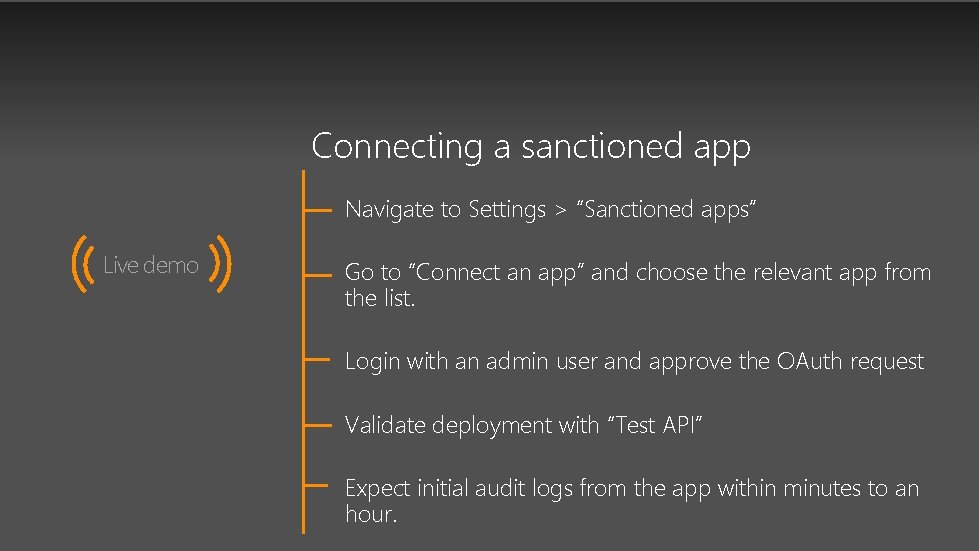
Connecting a sanctioned app Navigate to Settings > “Sanctioned apps” Live demo Go to “Connect an app” and choose the relevant app from the list. Login with an admin user and approve the OAuth request Validate deployment with “Test API” Expect initial audit logs from the app within minutes to an hour.

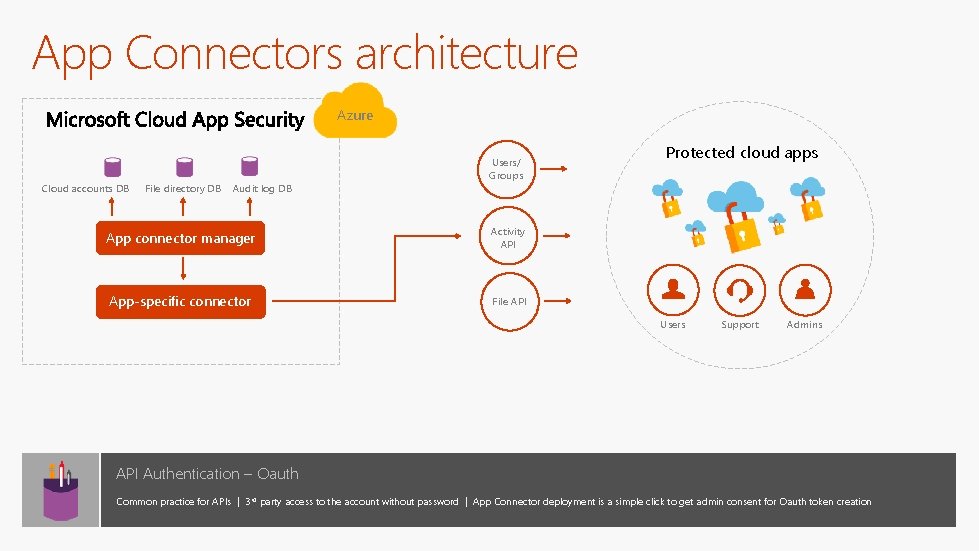
App Connectors architecture Azure Cloud accounts DB File directory DB Audit log DB Users/ Groups App connector manager Activity API App-specific connector File API Protected cloud apps Users Support Admins API Authentication – Oauth Common practice for APIs | 3 rd party access to the account without password | App Connector deployment is a simple click to get admin consent for Oauth token creation

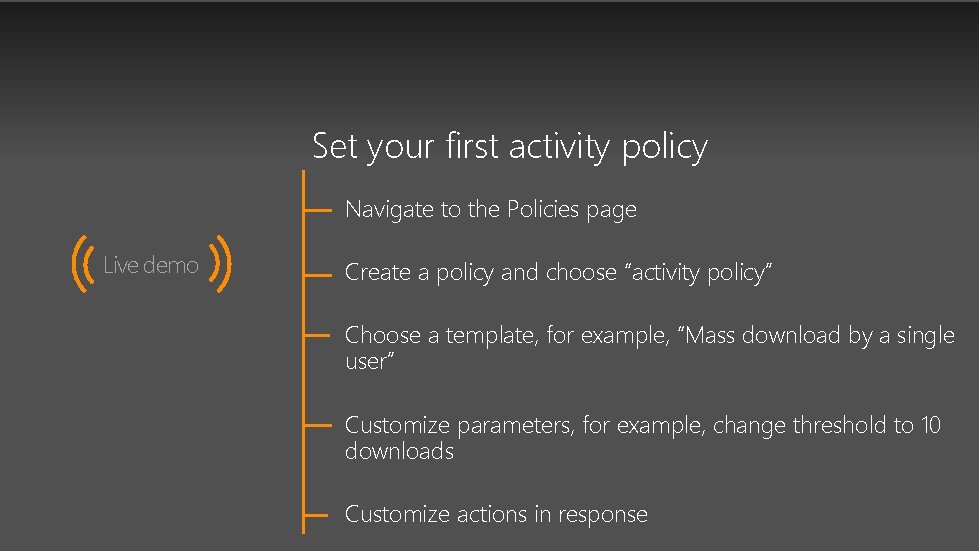
Set your first activity policy Navigate to the Policies page Live demo Create a policy and choose “activity policy” Choose a template, for example, “Mass download by a single user” Customize parameters, for example, change threshold to 10 downloads Customize actions in response

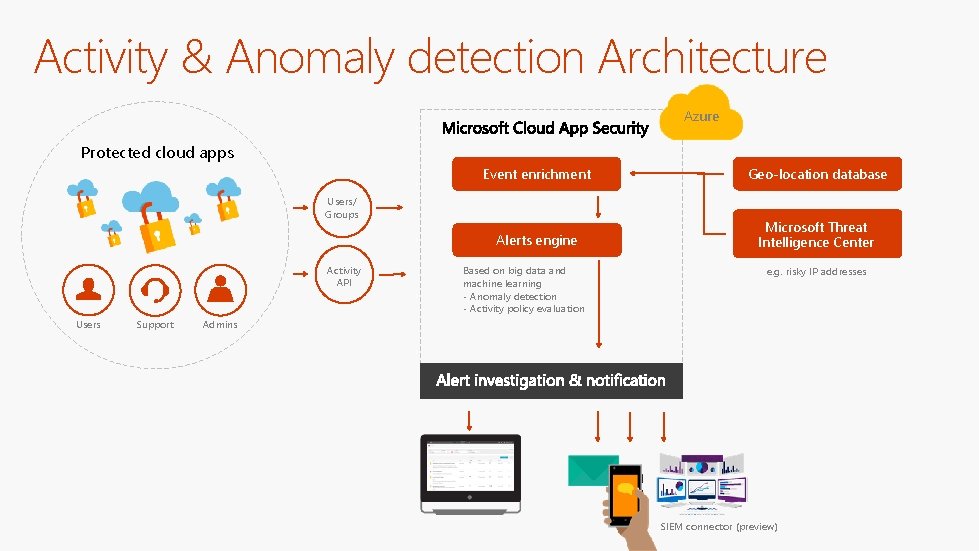
Activity & Anomaly detection Architecture Azure Protected cloud apps Event enrichment Geo-location database Alerts engine Microsoft Threat Intelligence Center Users/ Groups Activity API Users Support Based on big data and machine learning - Anomaly detection - Activity policy evaluation e. g. risky IP addresses Admins SIEM connector (preview)

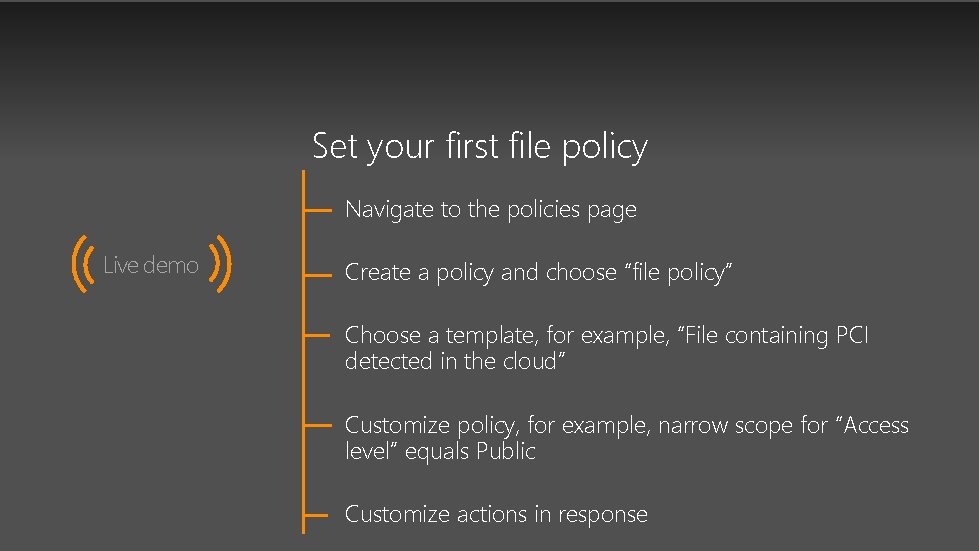
Set your first file policy Navigate to the policies page Live demo Create a policy and choose “file policy” Choose a template, for example, “File containing PCI detected in the cloud” Customize policy, for example, narrow scope for “Access level” equals Public Customize actions in response

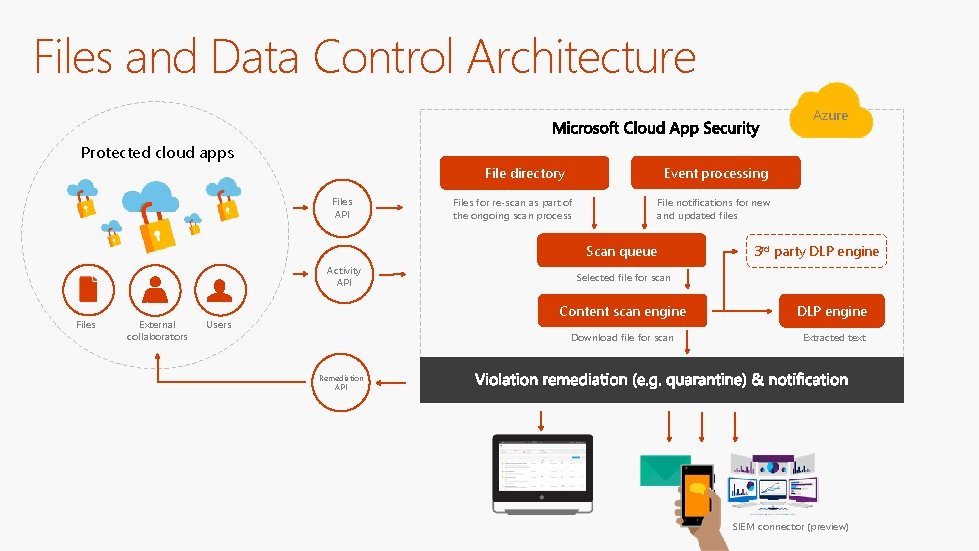
Files and Data Control Architecture Azure Protected cloud apps Event processing File directory Files API Files for re-scan as part of the ongoing scan process File notifications for new and updated files Scan queue Activity API Files External collaborators Users 3 rd party DLP engine Selected file for scan Content scan engine DLP engine Download file for scan Extracted text Remediation API SIEM connector (preview)


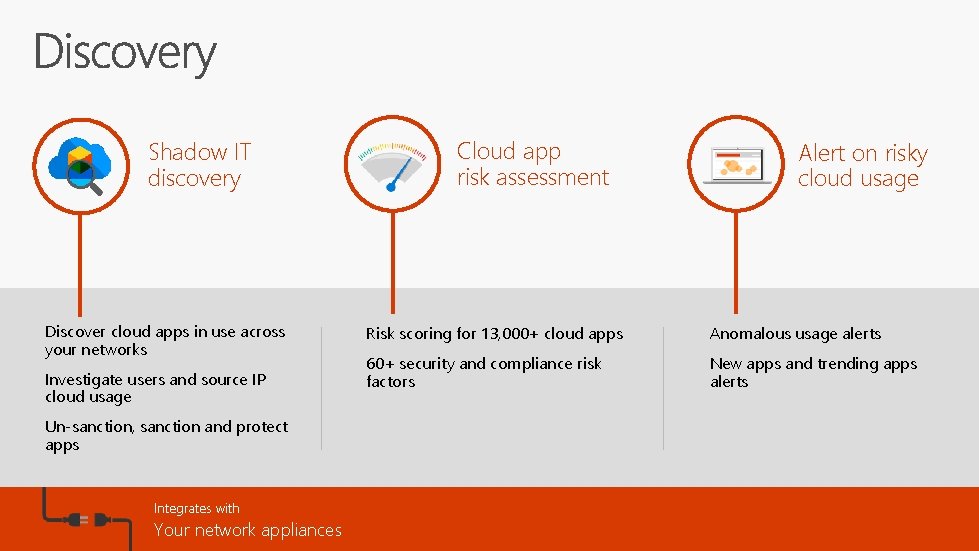
Cloud app risk assessment Shadow IT discovery Alert on risky cloud usage Discover cloud apps in use across your networks Investigate users and source IP cloud usage Un-sanction, sanction and protect apps Integrates with Your network appliances Risk scoring for 13, 000+ cloud apps Anomalous usage alerts 60+ security and compliance risk factors New apps and trending apps alerts

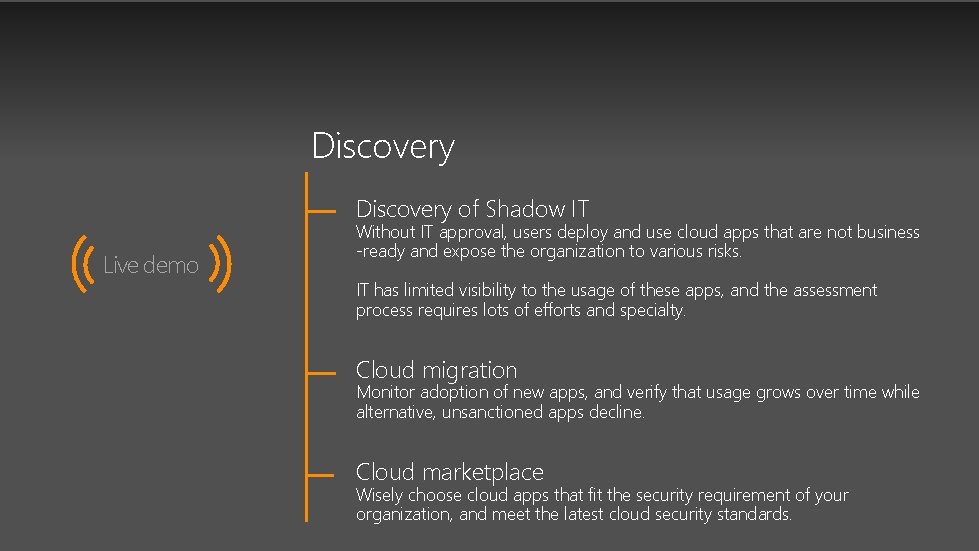
Discovery of Shadow IT Live demo Without IT approval, users deploy and use cloud apps that are not business -ready and expose the organization to various risks. IT has limited visibility to the usage of these apps, and the assessment process requires lots of efforts and specialty. Cloud migration Monitor adoption of new apps, and verify that usage grows over time while alternative, unsanctioned apps decline. Cloud marketplace Wisely choose cloud apps that fit the security requirement of your organization, and meet the latest cloud security standards.

Enforce DLP policies & control sharing Gain cloud data visibility Get alerts and investigate Visibility to sharing level and classification labels Govern data in the cloud with granular DLP policies Quantify exposure and risk Leverage Microsoft and 3 rd party DLP engines for classification Detect and manage 3 rd apps access Identify policy violations Investigate incidents and related activities Quarantine and permissions removal Integrates with Azure Information Protection, Office 365 Information Protection, 3 rd party DLP

Information protection scenarios Live demo Quantify risk: how many confidential files are stored in my cloud apps? Detect sensitive content in files stored in your cloud apps Auto-remediate public sharing of confidential data Detect confidential data shared publicly and autoremediate Investigate and alert Investigate files activity upon violation and trigger alerts on violations and suspicious activity.

Advanced investigation Behavioral analytics Threat Intelligence Support sharing level and classification labels Advanced incident Investigation tools Leverage Microsoft Intelligent Security Graph Quantify exposure and risk Pivot on users, file, activities and locations Unique insights, informed by trillions of signals across Microsoft’s customer base Detect and manage 3 rd apps access Customize detections based on your findings Integrates with Microsoft Intelligent Security Graph, 3 rd party SIEM

Threat detection scenarios Suspicious access Live demo Unauthorized users accessing your cloud environment or possible breaches in your environment Anomalous behavior Activities that were probably not done by your employees or may indicate data exfiltration by an insider Privileged user monitoring Monitor privileged users to keep your cloud environment safe.

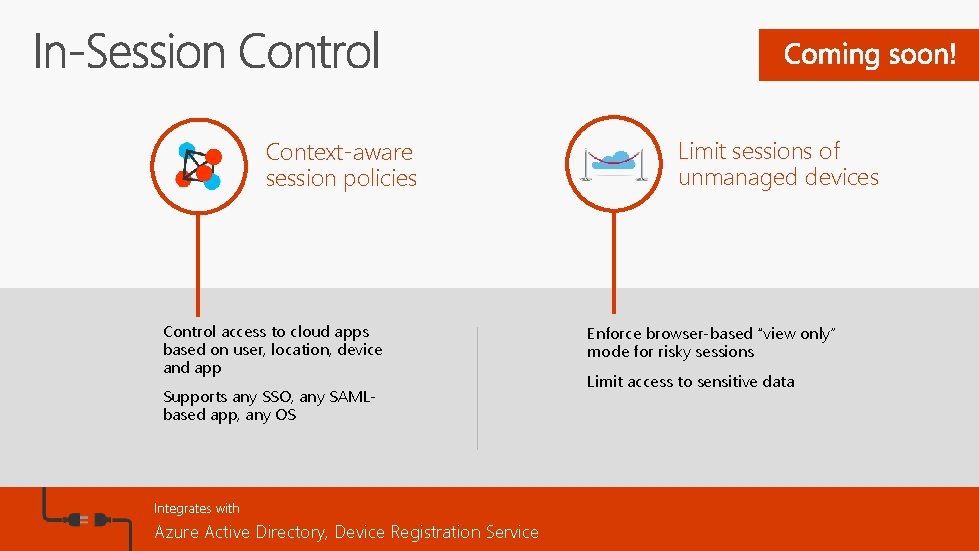
Context-aware session policies Limit sessions of unmanaged devices Control access to cloud apps based on user, location, device and app Supports any SSO, any SAMLbased app, any OS Integrates with Azure Active Directory, Device Registration Service Enforce browser-based “view only” mode for risky sessions Limit access to sensitive data

Cloud discovery Discover all cloud usage in your organization DISCOVER Information protection Monitor and control your data in the cloud INVESTIGATE Threat prevention Detect usage anomalies and security incidents CONTROL In-session control Control and limit user access based on session context PROTECT

www. cloudappsecurity. com

www. microsoft. com/itprocareercenter www. microsoft. com/itprocloudessentials www. microsoft. com/mechanics https: //techcommunity. microsoft. com

http: //myignite. microsoft. com https: //aka. ms/ignite. mobileapp

Try Enterprise Mobility + Security for free, today: www. microsoft. com/en-us/cloud-platform/enterprise-mobility-trial See Microsoft Cloud App Security in action https: //www. microsoft. com/en-us/cloud-platform/cloud-app-security-trial Evaluate and try Microsoft Advanced Threat Analytics now www. microsoft. com/enus/evalcenter/evaluate-microsoft-advanced-threat-analytics Explore Identity + Access Management www. microsoft. com/en-us/cloud-platform/identity-management Learn more about Azure Information Protection www. microsoft. com/en-us/cloud-platform/information-protection Discover new MDM and MAM solutions with Microsoft Intune www. microsoft. com/en-us/cloud-platform/mobile-device-managementlink
