Header Space Analysis Kazemian Varghese Mc Keown NSDI



- Slides: 25

Header Space Analysis Kazemian, Varghese, Mc. Keown, NSDI 2012 - abstraction across vendors, devices - navigating large header spaces - all counterexamples not just one 1

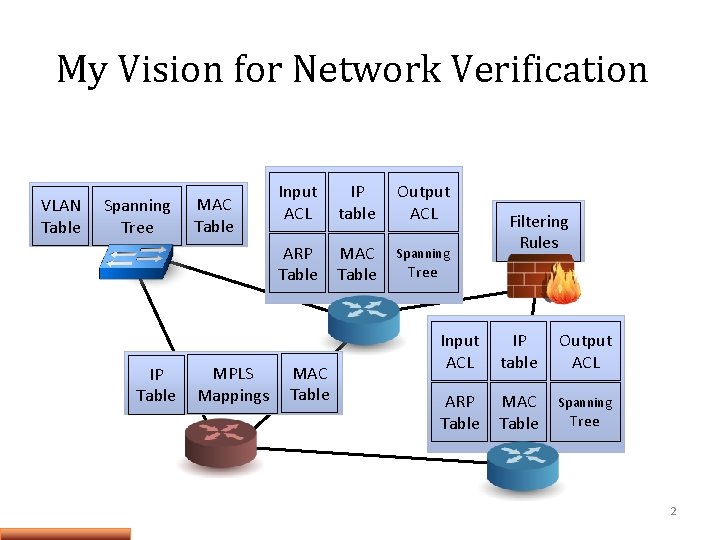
My Vision for Network Verification VLAN Table Spanning Tree IP Table MAC Table MPLS Mappings Input ACL IP table Output ACL ARP Table MAC Table Spanning MAC Table Filtering Rules Tree Input ACL IP table Output ACL ARP Table MAC Table Spanning Tree 2

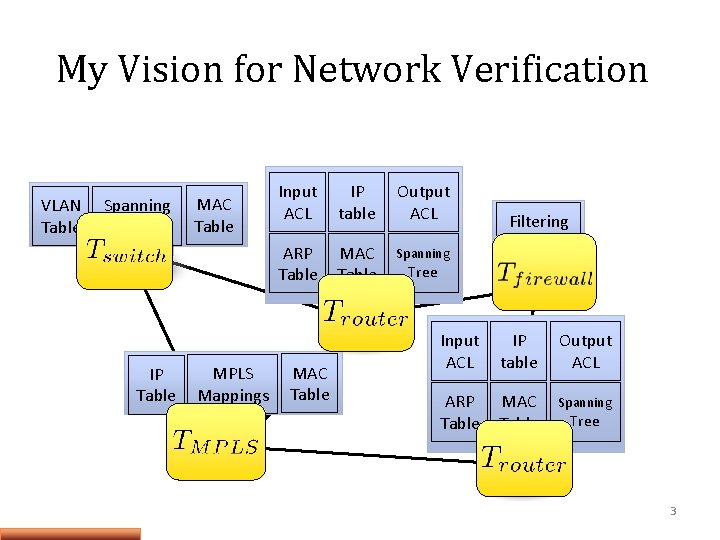
My Vision for Network Verification VLAN Table Spanning Tree IP Table MAC Table MPLS Mappings Input ACL IP table Output ACL ARP Table MAC Table Spanning MAC Table Filtering Rules Tree Input ACL IP table Output ACL ARP Table MAC Table Spanning Tree 3

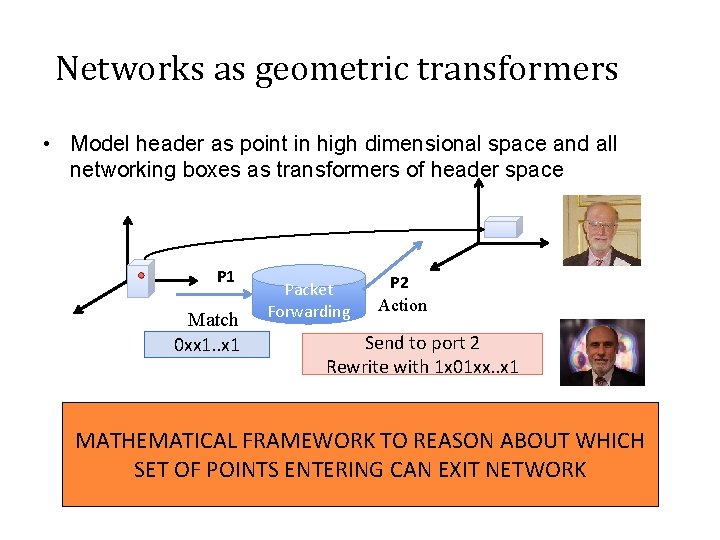
Networks as geometric transformers • Model header as point in high dimensional space and all networking boxes as transformers of header space P 1 Match 0 xx 1. . x 1 Packet Forwarding P 2 Action Send to port 2 Rewrite with 1 x 01 xx. . x 1 MATHEMATICAL FRAMEWORK TO REASON ABOUT WHICH SET OF POINTS ENTERING CAN EXIT NETWORK 4

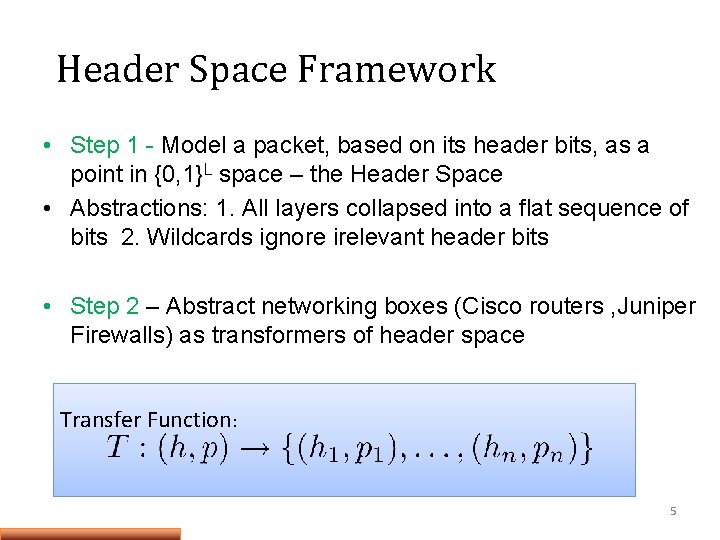
Header Space Framework • Step 1 - Model a packet, based on its header bits, as a point in {0, 1}L space – the Header Space • Abstractions: 1. All layers collapsed into a flat sequence of bits 2. Wildcards ignore irelevant header bits • Step 2 – Abstract networking boxes (Cisco routers , Juniper Firewalls) as transformers of header space Transfer Function: 5

My Vision for Network Verification VLAN Table Spanning Tree IP Table MAC Table MPLS Mappings Input ACL IP table Output ACL ARP Table MAC Table Spanning MAC Table Filtering Rules Tree Input ACL IP table Output ACL ARP Table MAC Table Spanning Tree 6

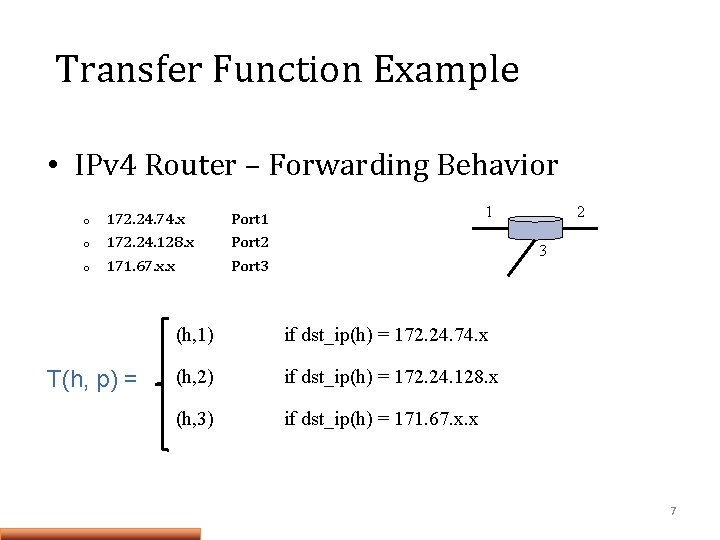
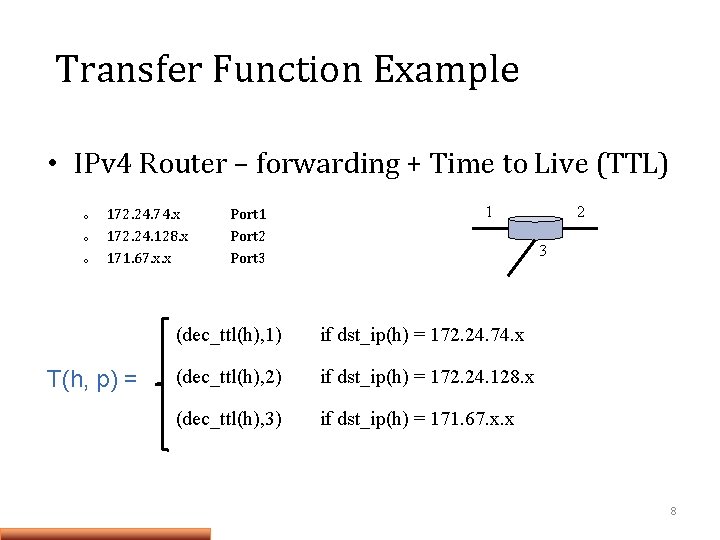
Transfer Function Example • IPv 4 Router – Forwarding Behavior o o o 172. 24. 74. x 172. 24. 128. x 171. 67. x. x T(h, p) = 1 Port 2 Port 3 2 3 (h, 1) if dst_ip(h) = 172. 24. 74. x (h, 2) if dst_ip(h) = 172. 24. 128. x (h, 3) if dst_ip(h) = 171. 67. x. x 7

Transfer Function Example • IPv 4 Router – forwarding + Time to Live (TTL) o o o 172. 24. 74. x 172. 24. 128. x 171. 67. x. x T(h, p) = Port 1 Port 2 Port 3 1 2 3 (dec_ttl(h), 1) if dst_ip(h) = 172. 24. 74. x (dec_ttl(h), 2) if dst_ip(h) = 172. 24. 128. x (dec_ttl(h), 3) if dst_ip(h) = 171. 67. x. x 8

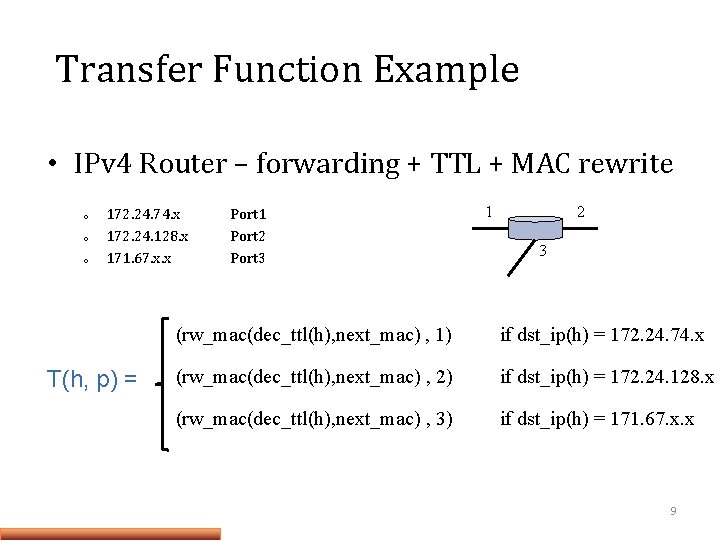
Transfer Function Example • IPv 4 Router – forwarding + TTL + MAC rewrite o o o 172. 24. 74. x 172. 24. 128. x 171. 67. x. x T(h, p) = Port 1 Port 2 Port 3 1 2 3 (rw_mac(dec_ttl(h), next_mac) , 1) if dst_ip(h) = 172. 24. 74. x (rw_mac(dec_ttl(h), next_mac) , 2) if dst_ip(h) = 172. 24. 128. x (rw_mac(dec_ttl(h), next_mac) , 3) if dst_ip(h) = 171. 67. x. x 9

Example Actions: • Rewrite: rewrite bits 0 -2 with value 101 o (h & 000111…) | 101000… • Encapsulation: encap packet in a 1010 header. o (h >> 4) | 1010…. • Decapsulation: decap 1010 xxx… packets o (h << 4) | 000…xxxx • TTL Decrement: o o if ttl(h) == 0: if ttl(h) > 0: Drop h – 0… 000000010… 0 • Load Balancing: o LB(h, p) = {(h, P 1), …(h, Pn)} 10

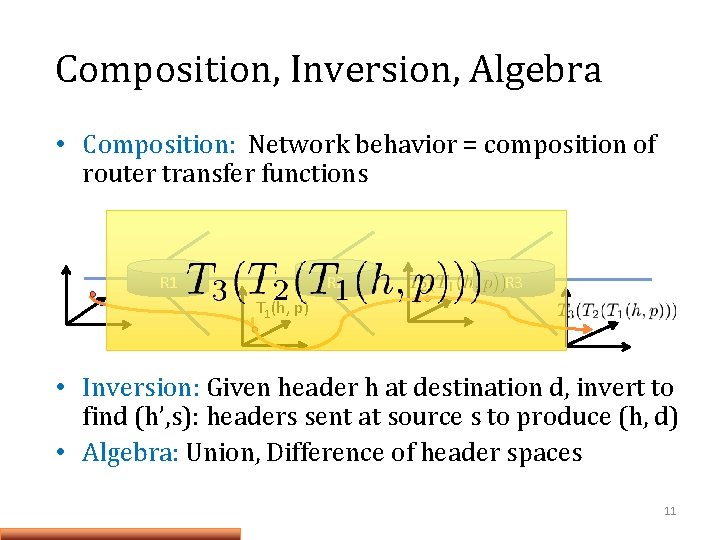
Composition, Inversion, Algebra • Composition: Network behavior = composition of router transfer functions R 1 R 2 R 3 T 1(h, p) • Inversion: Given header h at destination d, invert to find (h’, s): headers sent at source s to produce (h, d) • Algebra: Union, Difference of header spaces 11

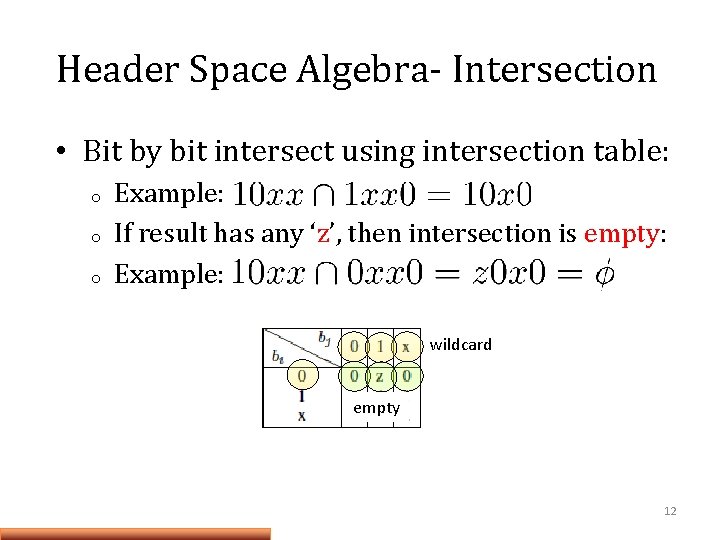
Header Space Algebra- Intersection • Bit by bit intersect using intersection table: o o o Example: If result has any ‘z’, then intersection is empty: Example: wildcard empty 12

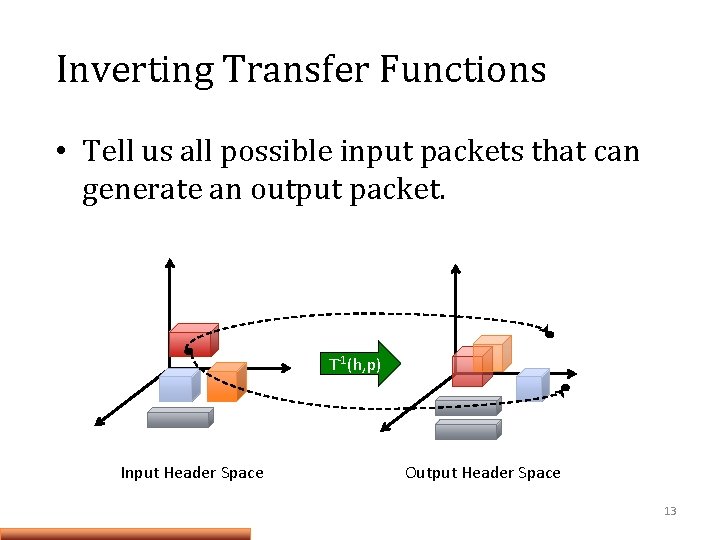
Inverting Transfer Functions • Tell us all possible input packets that can generate an output packet. -1(h, p) TT(h, p) Input Header Space Output Header Space 13

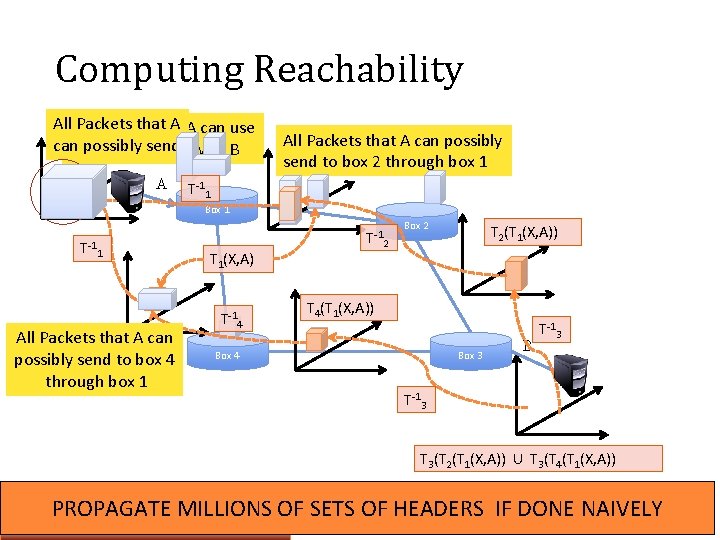
Computing Reachability All Packets that A A can use Packets that can send with B topossibly communicate A All Packets that A can possibly send to box 2 through box 1 T-11 Box 1 T-1 1 All Packets that A can possibly send to box 4 through box 1 T 1(X, A) T-14 T-12 Box 2 T 2(T 1(X, A)) T 4(T 1(X, A)) Box 4 Box 3 B T-13 T 3(T 2(T 1(X, A)) U T 3(T 4(T 1(X, A)) PROPAGATE MILLIONS OF SETS OF HEADERS IF DONE NAIVELY 14

Secure Slicing of Networks • Network slice of resources defined by o o A topology consisting of switches and ports. A set of predicates on packet headers. • Think Citibank & BOA sharing network. • Generalizes what are known as VLANs today

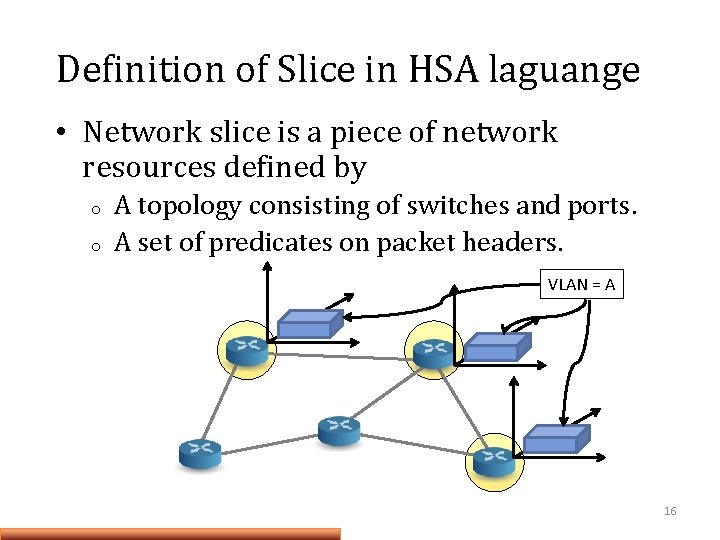
Definition of Slice in HSA laguange • Network slice is a piece of network resources defined by o o A topology consisting of switches and ports. A set of predicates on packet headers. VLAN = A 16

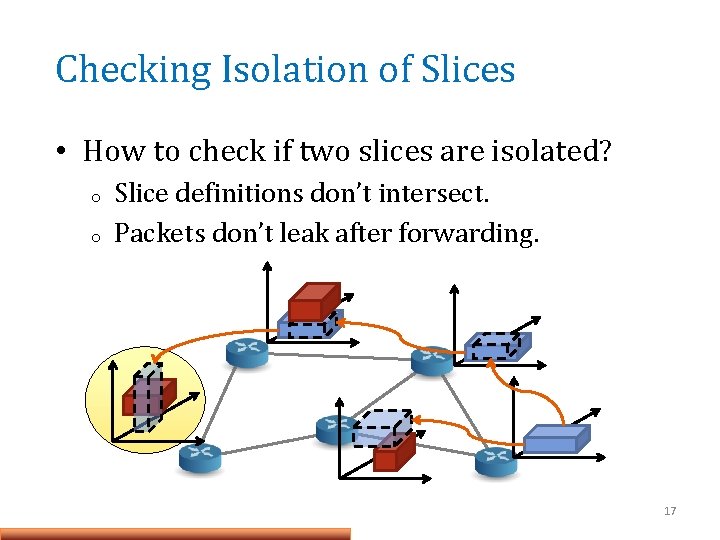
Checking Isolation of Slices • How to check if two slices are isolated? o o Slice definitions don’t intersect. Packets don’t leak after forwarding. 17

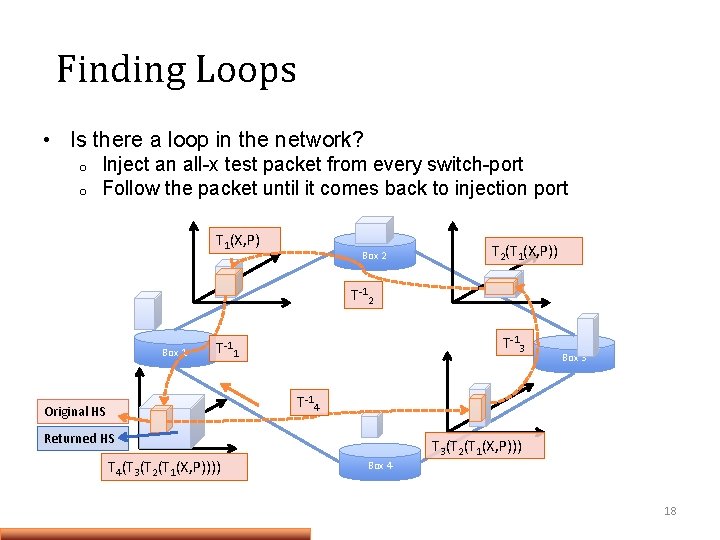
Finding Loops • Is there a loop in the network? o o Inject an all-x test packet from every switch-port Follow the packet until it comes back to injection port T 1(X, P) Box 2 T 2(T 1(X, P)) T-12 Box 1 T-13 T-11 Box 3 T-14 Original HS Returned HS T 4(T 3(T 2(T 1(X, P)))) T 3(T 2(T 1(X, P))) Box 4 18

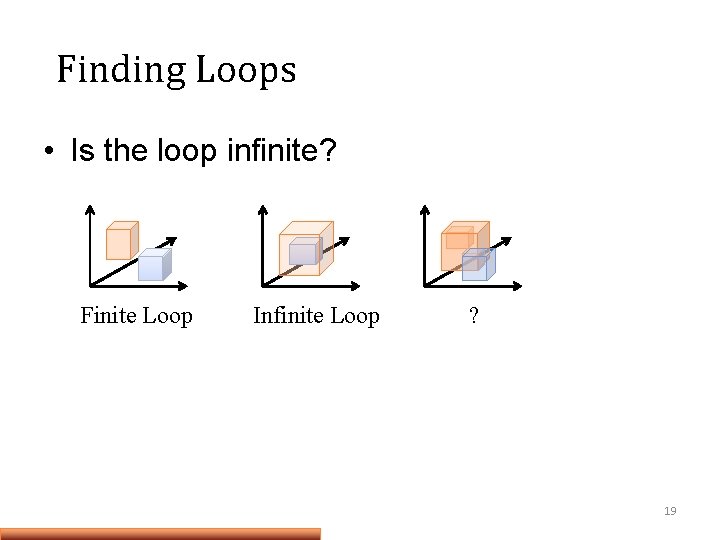
Finding Loops • Is the loop infinite? Finite Loop Infinite Loop ? 19

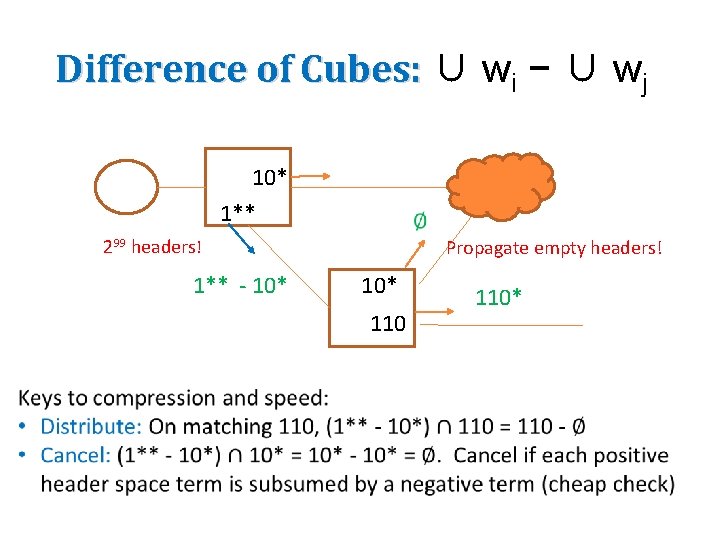
Difference of Cubes: ∪ wi − ∪ wj 10* 1** 299 headers! 1** - 10* Propagate empty headers! 10* 110*

Network versus classical verification o o Took days for 1 query till we compressed headers via difference of cubes 10, 000 x Difference of cubes worked better and faster than Binary Decision Diagrams Difference of cubes seems to work because router “formulae” have 1 level of negation Beyond reachability: secure slicing. Etc. STRUCTURE IN DOMAIN: LIMITED NEGATION, SMALL FORWARDING EQUIVALENCE CLASSES, LIMITED WRITES, NO LOOPS, SMALL DIAMETER 21

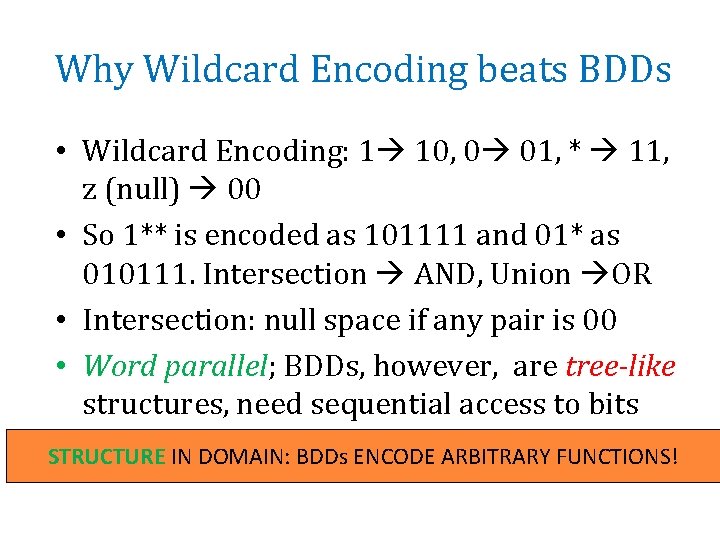
Why Wildcard Encoding beats BDDs • Wildcard Encoding: 1 10, 0 01, * 11, z (null) 00 • So 1** is encoded as 101111 and 01* as 010111. Intersection AND, Union OR • Intersection: null space if any pair is 00 • Word parallel; BDDs, however, are tree-like structures, need sequential access to bits STRUCTURE IN DOMAIN: BDDs ENCODE ARBITRARY FUNCTIONS!

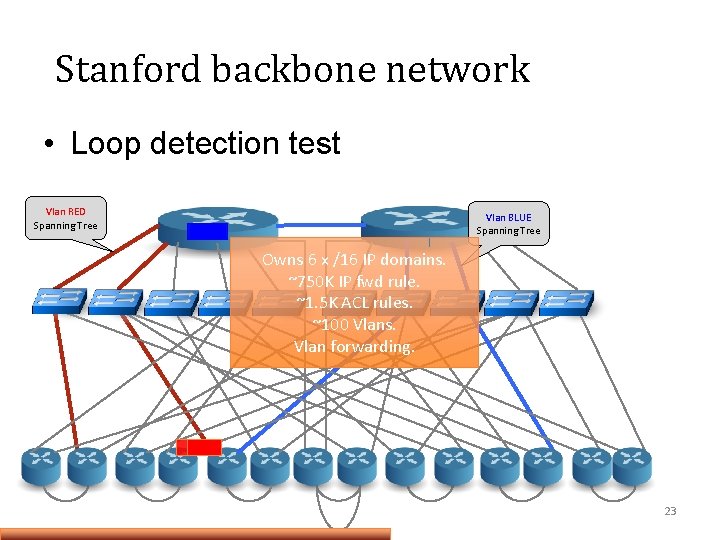
Stanford backbone network • Loop detection test Vlan RED Spanning Tree Vlan BLUE Spanning Tree Owns 6 x /16 IP domains. ~750 K IP fwd rule. ~1. 5 K ACL rules. ~100 Vlans. Vlan forwarding. 23

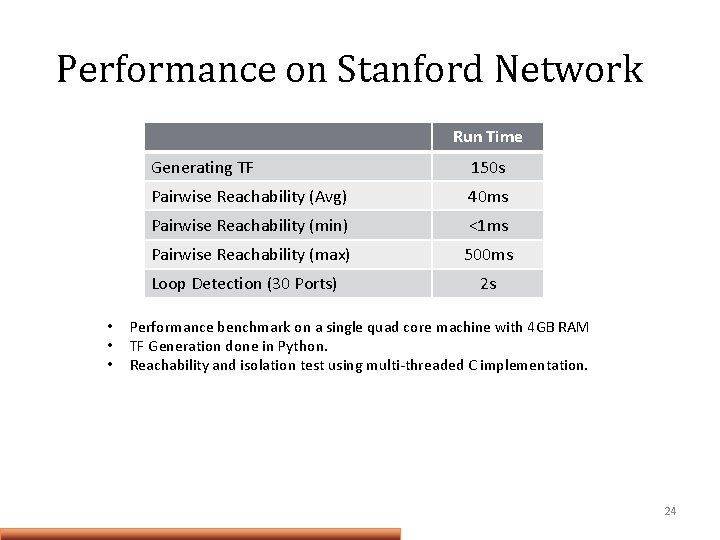
Performance on Stanford Network Run Time Generating TF 150 s Pairwise Reachability (Avg) 40 ms Pairwise Reachability (min) <1 ms Pairwise Reachability (max) 500 ms Loop Detection (30 Ports) • • • 2 s Performance benchmark on a single quad core machine with 4 GB RAM TF Generation done in Python. Reachability and isolation test using multi-threaded C implementation. 24

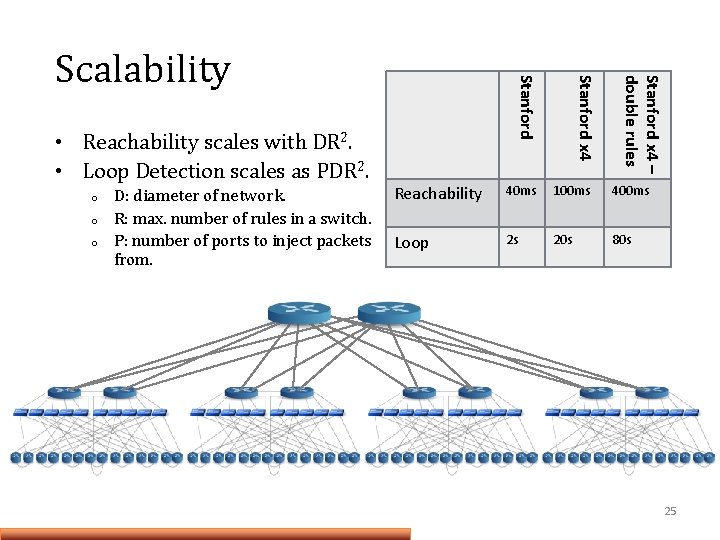
o o D: diameter of network. R: max. number of rules in a switch. P: number of ports to inject packets from. Stanford x 4 – double rules o Stanford x 4 • Reachability scales with DR 2. • Loop Detection scales as PDR 2. Stanford Scalability Reachability 40 ms 100 ms 400 ms Loop 2 s 20 s 80 s 25
 Jeff keown
Jeff keown Arthur j keown
Arthur j keown Peyman kazemian
Peyman kazemian Nick kazemian
Nick kazemian Icmp protokoll
Icmp protokoll Julian varghese
Julian varghese Melissa varghese
Melissa varghese Header space analysis
Header space analysis Header space analysis
Header space analysis Joint space vs cartesian space
Joint space vs cartesian space Space junk the space age began
Space junk the space age began Camera space to world space
Camera space to world space Unscented trajectory chapter 5
Unscented trajectory chapter 5 World space computer
World space computer Rfc tcp
Rfc tcp Tcp segment len
Tcp segment len Title page format apa
Title page format apa Message header analyzer
Message header analyzer History-info sip header
History-info sip header History-info sip header
History-info sip header Sip contact header
Sip contact header Tcp header
Tcp header React native header bar
React native header bar Power point temple
Power point temple Pgm header
Pgm header Dhcp
Dhcp