Gartner Authentication Methods Evaluation Scorecards GAMES Ant Allan










- Slides: 17

Gartner Authentication Methods Evaluation Scorecards (GAMES) Ant Allan Twitter: @G_ant This presentation, including any supporting materials, is owned by Gartner, Inc. and/or its affiliates and is for the sole use of the intended Gartner audience or other authorized recipients. This presentation may contain information that is confidential, proprietary or otherwise legally protected, and it may not be further copied, distributed or publicly displayed without the express written permission of Gartner, Inc. or its affiliates. © 2013 Gartner, Inc. and/or its affiliates. All rights reserved.

Why GAMES? • To assist Gartner clients in evaluating (and choosing) new authentication methods • Published guidelines (eg NIST SP 800 -63 -1) focus on authentication strength (assurance, risk, or trust levels) - GAMES also considers UX and TCO • Published guidelines might rank some available methods, but with little transparency - Why does X provide greater assurance than Y? - How can I rank P, Q, … that aren’t explicitly mentioned? • Why is Gartner doing this? Because no-one else is!

GAMES Timeline • First iteration - Gartner Authentication Method Evaluation Scorecards, 30 Sep 2008 - Toolkit: Gartner Authentication Method Evaluation Scorecards, 8 Sep 2009 • Second iteration - Gartner Authentication Method Evaluation Scorecards, 2011: Overview, 7 Mar 2011 - : Total Cost of Ownership, 7 Mar 2011 - : User Experience, 23 May 2011 - : Assurance and Accountability 5 Mar 2012 [sic] • Third iteration… ?

Changes in GAMES • General discussion of TCO elements chart of accounts • Ease of use UX • Authentication strength … multiple changes: - V 2 has explicit discussion of accountability, not completely orthogonal to assurance - Scrapped complex, effortful quantitative approach (implying a precision that is really unattainable in this kind of evaluation) for a simpler, more qualitative approach - Two parts: • A 1: The method's resistance to attack — that is, how difficult is it for an attacker to directly compromise or undermine the authentication method (without the user's knowing collusion)? • A 2: The method's resistance to willful misuse — that is, how difficult is it for a user to deliberately allow colleagues and others to share his or her account?

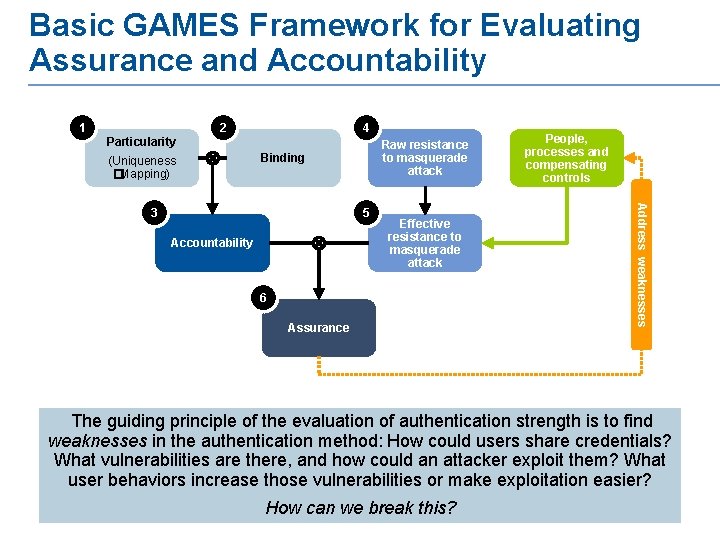
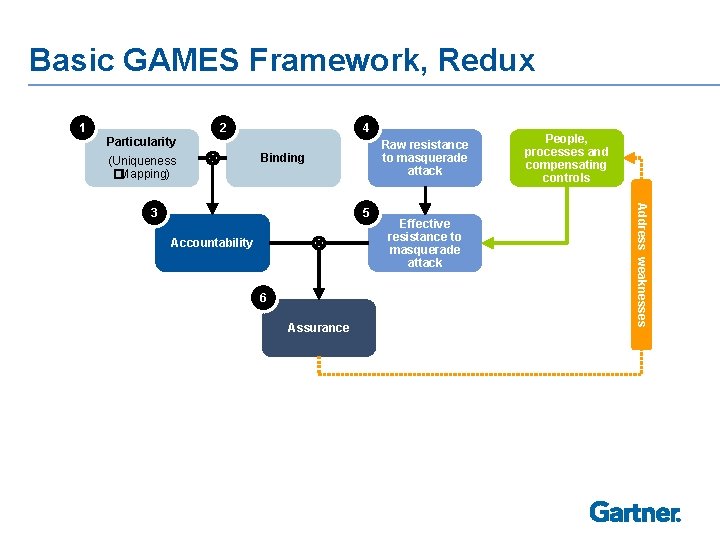
Basic GAMES Framework for Evaluating Assurance and Accountability 1 2 4 Particularity (Uniqueness � Mapping) Raw resistance to masquerade attack Binding 5 Accountability Effective resistance to masquerade attack 6 Assurance Address weaknesses 3 People, processes and compensating controls The guiding principle of the evaluation of authentication strength is to find weaknesses in the authentication method: How could users share credentials? What vulnerabilities are there, and how could an attacker exploit them? What user behaviors increase those vulnerabilities or make exploitation easier? How can we break this?

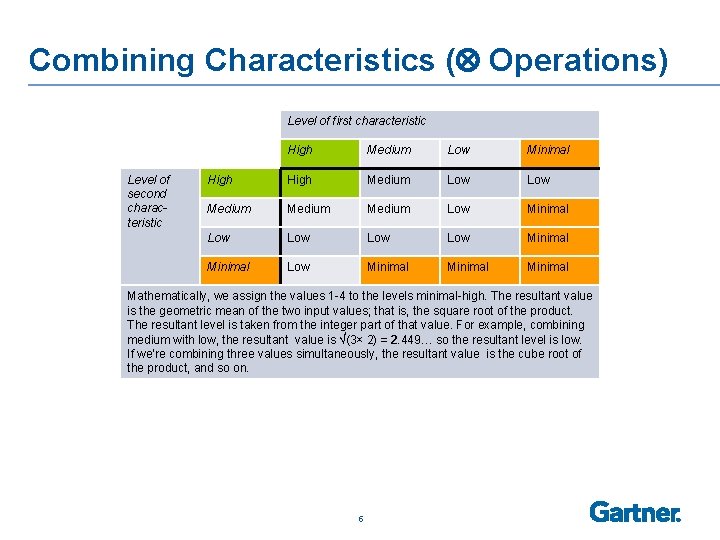
Combining Characteristics ( Operations) Level of first characteristic Level of second characteristic High Medium Low Minimal High Medium Low Medium Low Minimal Low Minimal Mathematically, we assign the values 1 -4 to the levels minimal-high. The resultant value is the geometric mean of the two input values; that is, the square root of the product. The resultant level is taken from the integer part of that value. For example, combining medium with low, the resultant value is √(3× 2) = 2. 449… so the resultant level is low. If we’re combining three values simultaneously, the resultant value is the cube root of the product, and so on. 5

Particularity Binding Accountability • Particularity: To what degree are the authentication attributes — and the authentication information derived from them: - Unique? - Uniquely mapped to the user? • Binding: How difficult is it for the user to willingly share authentication attributes with others? - Or: How tightly are the authentication attributes bound to the user? • Accountability: An expression of resistance to willful misuse. (A 2) 6

How Difficult Is it For an Attacker to Execute a Masquerade Attack? (A 1) This decomposes into four more-granular questions, each of which addresses a different attack mode: • B 1: How difficult is it for an attacker to gain possession of (a copy of) the authentication attributes the user possesses? • B 2: How difficult is it for an attacker to capture and successfully reuse the authentication information? • B 3: How difficult is it for an attacker to directly or indirectly modify the stored authentication attributes? • B 4: How difficult is it for an attacker to directly or indirectly modify an authentication decision or how a decision is enforced? Any chain is only as strong as its weakest link! 7

Evaluating the Attack Mode Questions Consider the following*: • C 1: The attack vector — Where does an attacker have to be to execute the attack? If it's local (that is, physically present), the difficulty is high; if on a local network, medium; if on the Internet, minimal. • C 2: The access complexity — What level of effort is required? This can be directly expressed as minimal to high. • C 3: The novelty** — How unusual is the attack? If this is seen in the wild, the novelty is minimal; if it exists as a proof of concept, low; if it is unproven, medium. * Much simplified version from the Common Vulnerability Scoring System ** Note that this replaces "exploitability of the attack" used in the original GAMES research, in order to have the scoring in the "right direction. ") 8

Evaluating an Authentication Method's Effective Resistance to Attack A method's inherent or "raw" resistance to masquerade attack can be modified — strengthened or weakened — by external considerations that will vary from one implementation to another: • D 1: How can user behavior facilitate or mitigate an attack? • D 2: How can administrative processes and administrator behavior facilitate or mitigate an attack? • D 3: How can additional compensating controls mitigate an attack? 9

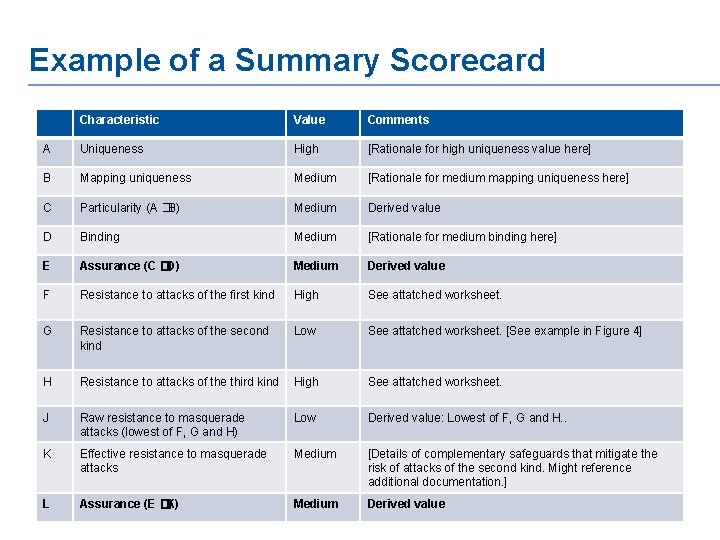
Example of a Summary Scorecard Characteristic Value Comments A Uniqueness High [Rationale for high uniqueness value here] B Mapping uniqueness Medium [Rationale for medium mapping uniqueness here] C Particularity (A � B) Medium Derived value D Binding Medium [Rationale for medium binding here] E Assurance (C �D) Medium Derived value F Resistance to attacks of the first kind High See attatched worksheet. G Resistance to attacks of the second kind Low See attatched worksheet. [See example in Figure 4] H Resistance to attacks of the third kind High See attatched worksheet. J Raw resistance to masquerade attacks (lowest of F, G and H) Low Derived value: Lowest of F, G and H. . K Effective resistance to masquerade attacks Medium [Details of complementary safeguards that mitigate the risk of attacks of the second kind. Might reference additional documentation. ] L Assurance (E �K) Medium Derived value 10

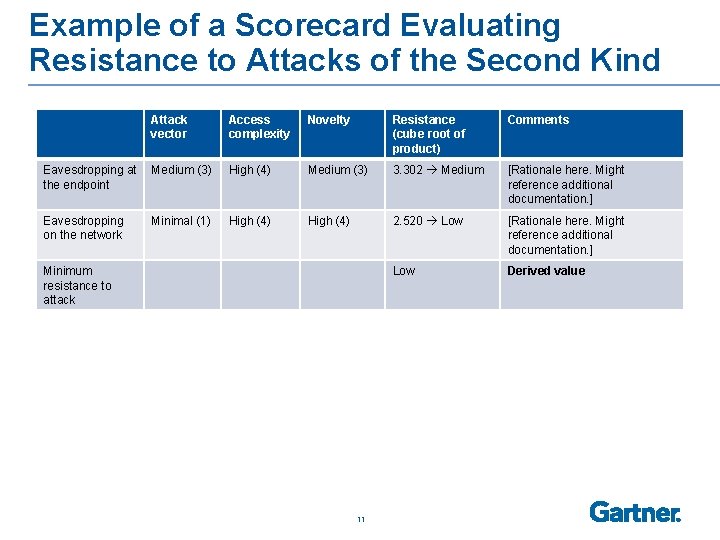
Example of a Scorecard Evaluating Resistance to Attacks of the Second Kind Attack vector Access complexity Novelty Resistance (cube root of product) Comments Eavesdropping at Medium (3) the endpoint High (4) Medium (3) 3. 302 Medium [Rationale here. Might reference additional documentation. ] Eavesdropping on the network High (4) 2. 520 Low [Rationale here. Might reference additional documentation. ] Low Derived value Minimal (1) Minimum resistance to attack 11

Basic GAMES Framework, Redux 1 2 4 Particularity (Uniqueness � Mapping) Raw resistance to masquerade attack Binding 5 Accountability 6 Assurance Effective resistance to masquerade attack Address weaknesses 3 People, processes and compensating controls

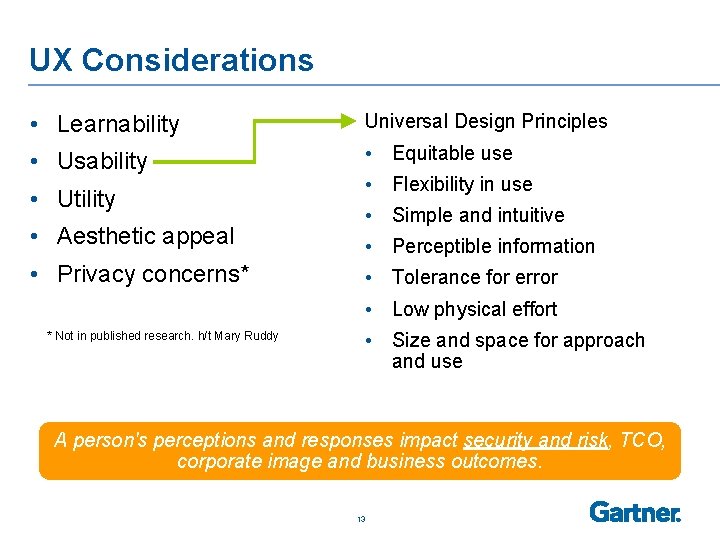
UX Considerations • Learnability Universal Design Principles • Usability • Equitable use • Utility • Aesthetic appeal • Privacy concerns* • Flexibility in use • Simple and intuitive • Perceptible information • Tolerance for error • Low physical effort * Not in published research. h/t Mary Ruddy • Size and space for approach and use A person's perceptions and responses impact security and risk, TCO, corporate image and business outcomes. 13

TCO Considerations (High Level!) • Authentication infrastructure components: • Target system components - Hardware • End-user and endpoint components - Software • Administration - Services - Management • IT operations - Implementation - Support - Training • End users - Training - Identity administration - Downtime - Logistics 14

Q&A

Gartner Authentication Methods Evaluation Scorecards (GAMES) Ant Allan Twitter: @G_ant This presentation, including any supporting materials, is owned by Gartner, Inc. and/or its affiliates and is for the sole use of the intended Gartner audience or other authorized recipients. This presentation may contain information that is confidential, proprietary or otherwise legally protected, and it may not be further copied, distributed or publicly displayed without the express written permission of Gartner, Inc. or its affiliates. © 2013 Gartner, Inc. and/or its affiliates. All rights reserved.