Ethical Hacking Defeating Logon Passwords HandsOn Ethical Hacking

















- Slides: 21

Ethical Hacking: Defeating Logon Passwords Hands-On Ethical Hacking and Network Defense

Contact Sam Bowne n Computer Networking and Information Technology n City College San Francisco n Email: sbowne@ccsf. edu n Web: samsclass. info n 2

Teaching Hacking Hands-On Ethical Hacking and Network Defense

What do Hackers Do? Get into computer systems without valid accounts and passwords n Open encrypted files without the key n Take over Web servers n Collect passwords from Internet traffic n Take over computers with remote access trojans n And much, much more n 4

Ethical Hackers do the same thing criminal hackers do, with one difference n Ethical Hackers have permission from the owner of the machines to hack in n These "Penetration Tests" reveal security problems so they can be fixed n 5

Two Hacking Classes CNIT 123: Ethical Hacking and Network Defense Has been taught since Spring 2007 (four times) Face-to-face and Online sections available Fall 2008 CNIT 124: Advanced Ethical Hacking Taught for the first time in Spring 2008 6

Supplemental Materials Projects from recent research n Students get extra credit by attending conferences n 7

Certified Ethical Hacker n Those two classes prepare students for CEH Certification 8

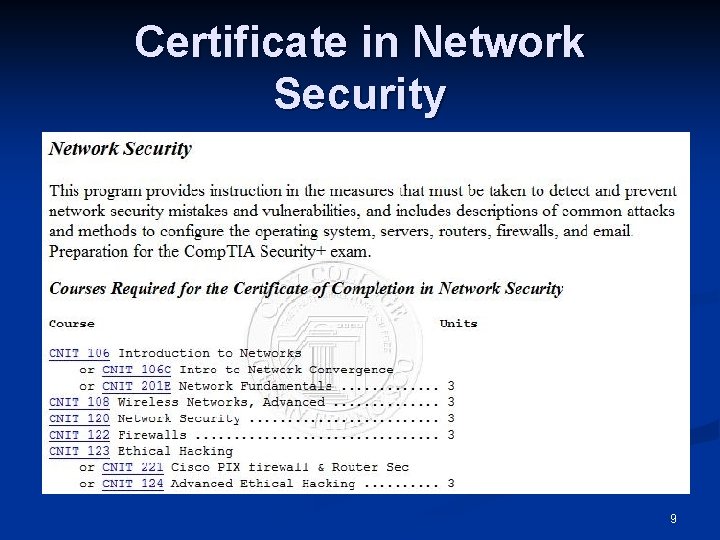
Certificate in Network Security 9

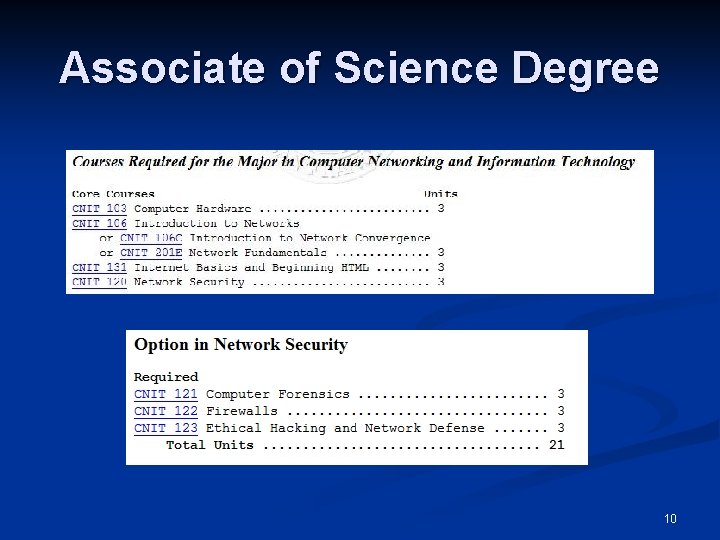
Associate of Science Degree 10

Windows Passwords Hands-On Ethical Hacking and Network Defense

Password Hashes Passwords are not stored on Windows computers in plaintext n They are run through one-way mathematical Hash Functions n 12

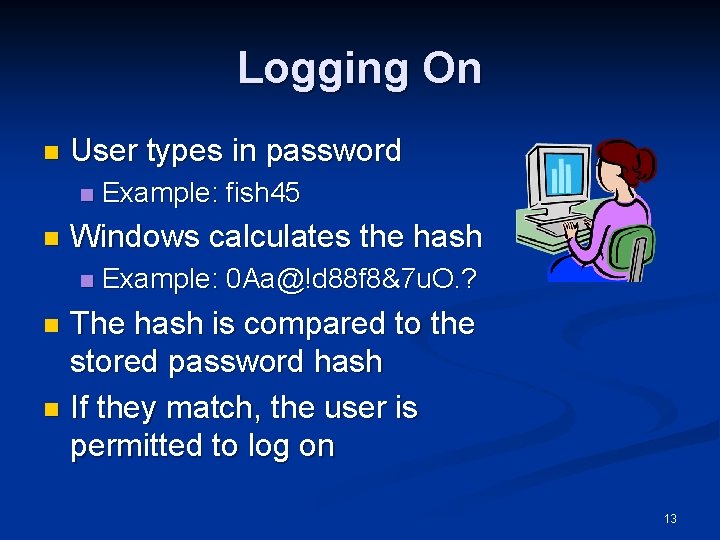
Logging On n User types in password n n Example: fish 45 Windows calculates the hash n Example: 0 Aa@!d 88 f 8&7 u. O. ? The hash is compared to the stored password hash n If they match, the user is permitted to log on n 13

LM Hashes Windows breaks the password into two 7 -character pieces n Each section is hashed separately n So a long, strong password like n n n Alligator 1978 Becomes two short passwords n ALLIGAT OR 1978 14

Weakness of LM Hashes Each section has only 243 possible values n Modern computers can try all those values in just a few minutes n 15

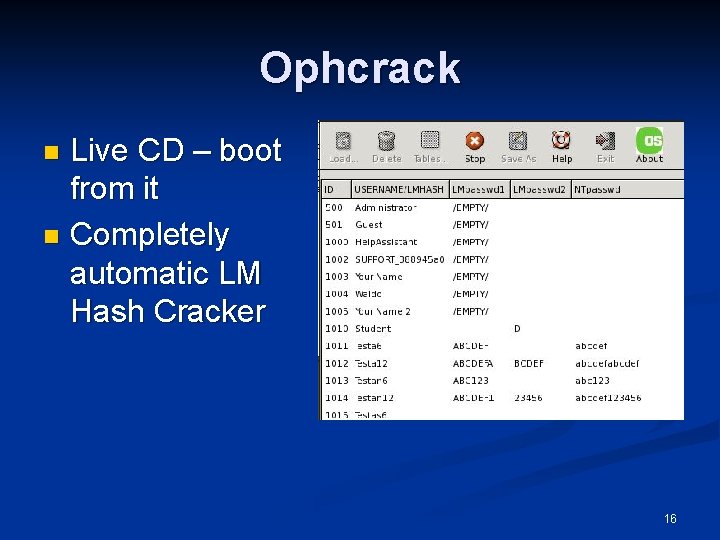
Ophcrack Live CD – boot from it n Completely automatic LM Hash Cracker n 16

Countermeasures Hands-On Ethical Hacking and Network Defense

Hardening Windows Microsoft has a stronger hashing technique called NTLM Hashes n But all versions of Windows before Vista use LM Hashes by default n A change in Local Security Policy can eliminate the LM Hashes (see references) n 18

Cracking Vista Hands-On Ethical Hacking and Network Defense

Ultimate Boot CD With this CD, you can create new Administrator accounts on Windows XP, Vista, and Server 2008 n It does not reveal existing passwords n 20

References n Wikipedia: LM Hashes n n Ophcrack Live. CD n n http: //ophcrack. sourceforge. net/ Ultimate Boot CD n n http: //en. wikipedia. org/wiki/LM_hash http: //www. ubcd 4 win. com/howto. htm Turning off LM Hashes n http: //support. microsoft. com/kb/299656 n Last modified 6 -26 -08 21