Edexcel GCSE Computer Science Topic 22 Emerging Issues










- Slides: 14

Edexcel GCSE Computer Science Topic 22 - Emerging Issues



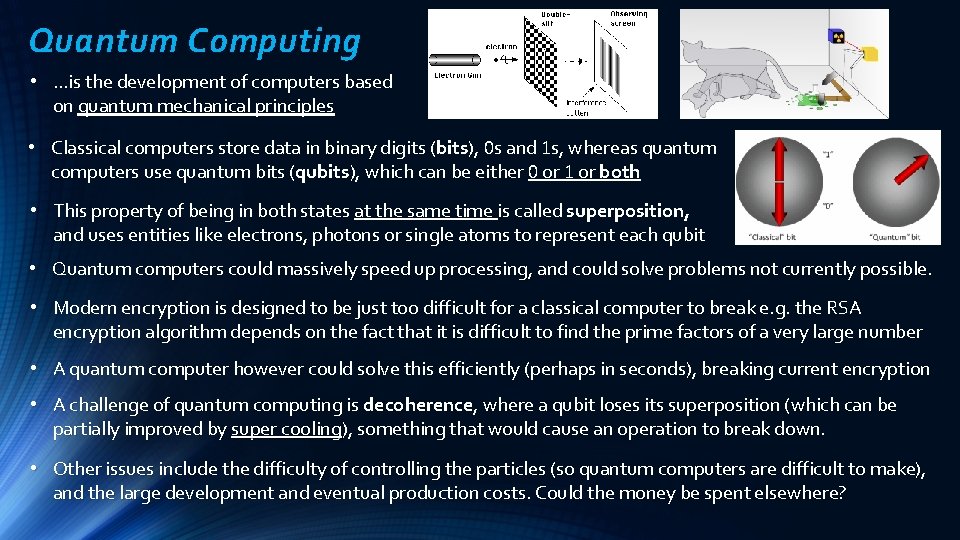
Quantum Computing • …is the development of computers based on quantum mechanical principles • Classical computers store data in binary digits (bits), 0 s and 1 s, whereas quantum computers use quantum bits (qubits), which can be either 0 or 1 or both • This property of being in both states at the same time is called superposition, and uses entities like electrons, photons or single atoms to represent each qubit • Quantum computers could massively speed up processing, and could solve problems not currently possible. • Modern encryption is designed to be just too difficult for a classical computer to break e. g. the RSA encryption algorithm depends on the fact that it is difficult to find the prime factors of a very large number • A quantum computer however could solve this efficiently (perhaps in seconds), breaking current encryption • A challenge of quantum computing is decoherence, where a qubit loses its superposition (which can be partially improved by super cooling), something that would cause an operation to break down. • Other issues include the difficulty of controlling the particles (so quantum computers are difficult to make), and the large development and eventual production costs. Could the money be spent elsewhere?

DNA Computing • This uses DNA as the material used to make processors, rather than those currently based on silicon, which will eventually reach their limits of speed and how small them can make them. • DNA molecules are what carry our genes – they store biological information about us. • This information is represented by the four bases: Adenine, Cytosine, Guanine and Thymine, contrasting with the two bits of information used in binary systems. • Despite there being a large supply of silicon (it makes up 27. 7% of the Earth’s crust), it needs to be highly purified for electronics which is expensive. DNA has a large supply so it is comparatively cheap. • DNA computers can be many times smaller than current computers, and be much better at parallel processing – think about how much is working in parallel in your body right now!! • DNA may not survive long enough (it has a half life of ~ 520 years) to get a result. • Other biological building blocks, like enzymes, have also been able to be used to execute instructions, sometimes in combination with DNA. This biological technology is evolvable, self-replicating, selfrepairing and is responsive to external stimuli.

…is the study of creating machines and software exhibiting signs of intelligence Professor Stephen Hawking on AI: The aim of this field is to build autonomous machines (machines that can carry out complex tasks without “The development of full artificial intelligence could spell our constant involvement). These are ‘intelligent agents’ – which take in and respond to external changes. the end of the human race. It would take off on its own, Some modern robots (an autonomous agent) have the ability to learn in a limited and re-design itself at an ever increasing rate. Humans, who capacity, such as mimicking the actions of humans. are limited by slow biological evolution, couldn't compete, and would be superseded. ” Some AI is built to try and replicate some properties of our brains, like Elon Musk: Google Deep. Mind using neural (AI is) “the most serious threat to the survival of the human race” networks, causing them to work “I'm increasingly inclined to think that there should be some differently to normal computers. regulatory oversight, maybe at the national and international level, just to make sure that we don't do something very foolish” Our brains have evolved for hundreds of millions of years, but to survive, so our ability to do maths (e. g. ) is not Artificial Intelligence (AI) • • done as efficiently possible, if our neurons were rewired designed for calculations, it would be much faster. • AI systems may be much more accurate – they can detect and solve problems on their own • AI, especially robots, can do the boring, repetitive tasks that humans don’t like – but will cause unemployment • However there is a fear that AI could eventually replace humans, should they become ‘superintelligent’ (where they exceed human capabilities in everything), and if their goals then conflict with mankind’s.

Nanotechnology • This is the manipulation of matter on a very small (about 1 to 100 nanometres) scale. Most biological processes occur at this nanoscale, and quantum phenomena start to occur. • Electronic devices use nanomaterials (structures at this nanoscale). For example, nanoscale transistors are faster, more powerful and more energy efficient. • IBM have developed working chips with transistors 7 nm long, something previously thought impossible without decreased performance – the limit for pure silicon use is 10 nm. • They will be commercially ready in 2017, and IBM says they’ll result in “at least a 50 percent power/performance improvement for next generation systems”. Intel’s new processors can fit 1. 9 billion transistors on, these may be able to fit 20 billion. • Memory technology is being developed with nanotechnology, e. g. ‘nanodots’, which are like tiny (~ 50 nm) magnets which can have their polarity switched to represent the binary digits. Using nanotechnology for this increases memory density. • Nanoparticles could be much more toxic because they can pass through membranes larger molecules can’t. Nanotechnology may also allow people to create more powerful weapons.

Benefits / Problems QUANTUM COMPUTING - DNA COMPUTING - All of them are expensive to develop, could the money be spent elsewhere? – This would count as evaluation Process data much fast and in parallel using qubits instead of bits, but the particles used (e. g. photons) are hard to control Uses biological processes and components (e. g. DNA, enzymes) to speed up large and complicated process, however they would be a lot slower to solve simple problems, due to the difficultly in setting them up and getting the answers. ARTIFICIAL INTELLIGENCE - Based on creating machines that exhibit intelligence, which could solve complicated problems accurately, but in the short term cause unemployment and in the long term there are fears AI could supersede humans. NANOTECHNOLOGY - Constructed using parts in the nanoscale (1 to 100 nm). Apart from being able decrease size without reducing performance (or vice versa), power consumption can be improved. However, apart from the difficulties in making the technology, it can be risky for humans and can make weapons more powerful.

Ethical Social Issues surrounding Computing Environmental Legal

Ownership Issues • Intellectual property (IP) refers to creations ‘of the mind’, like art, inventions, slogans etc. • IP is protected under law such through patents, copyright (©) and trademarks (™ or if registered ®). A patent gives an inventor the right to stop other people making or using their invention. It protects how the invention works or what it • E. g. patents and copyright could be used to protect the does by legally allowing the inventor to exclude technology itself, whereas trademarks protects the names others from selling their work. Computer and symbols that distinguish the technology in the market. programs usually can’t be patented. Copyright is the legal ownership applying to IP like music and films and also software and Internet content. Copyright, Designs and Patents Act (CDPA) (1988) • This Act protects the intellectual property rights of individuals and organisations • It makes it illegal to copy, modify or distribute software or other IP without permission • It is also illegal to download IP like music or films without permission of the copyright holder • Most commercial software comes with a license agreement specifying how the purchaser may use the product and to prove they have paid for it. A license key is often required to access the software.

A software license provides a user with either paper-based or digital proof they have a right to use software because they have purchased it legally. You might have to enter license keys to use software. • Software is generally protected by copyright, unless it has been made available in the public domain • You don’t only have to agree to a license if you pay for software, free software has them too. • Commercial software is produced for sale – and can be either proprietary or open source software. Proprietary Software • This is software licensed under strict conditions, usually preventing you from modifying or distributing the software. The source code is not available, it has already been compiled to machine code. • If people could see the source code, then it would be easy for competitors to copy and steal. Open Source Software • Open source software has the source code publicly available. Typically its license will allow a user Open source software has the source code to study, modify and distribute the software and prevents them from restricting its distribution i. e. selling the software later. • Due to this public nature, there is little point charging for OSS, so it is often free.

The Computer Misuse Act (1990) • This Act makes it a criminal offence to make any unauthorised access to computer material… …with intent to commit or facilitate commission of further crimes e. g. theft or blackmail …with intent to impair the operation of the computer e. g. distributing viruses • It is aimed at people commonly called hackers, who (now) illegally break into a computer system. The Health and Safety at Work Act (1974) • This Act sets out the general duties which employers have towards employees and This Act members of the public, and employees have to themselves and to each other. • Employers need to ensure systems at work need to be safe and without risks to the user’s health • Testing needs to be done to ensure safety e. g. PAT (portable appliance testing) • People using the equipment need to have adequate information about how to use it safely and whether/ when it has been tested.

The Cookie Law • This started as a EU Directive (just an Act of the EU), which was adopted by all member states in 2011. A cookie is a small piece of data sent from a Web server and stored in the user's Web browser while the user is browsing. • It requires Web sites to get consent from users visiting their website for them to use cookies to store or retrieve data about them. • It gives people the right to refuse the use of cookies about them. Data Protection Act (1998) • The purpose of this Act is to “regulate the processing of information relating to individuals, The purpose of this Act is to “r including the obtaining, holding, use or disclosure of such information. ” • It creates rights for people who have data stored about them elsewhere, such as viewing the data stored about them, requesting that any incorrect data be corrected, and requiring that data about them isn’t used for direct marketing (e. g. telesales, such as cold calls)

There are 8 data protection principles in the Data Protection Act: 1) Data should be processed fairly and lawfully (e. g. data should not be obtained by deception) 2) Personal data shall be obtained only for one or more specified and lawful purposes, and shall not be further processed in any manner incompatible with that purpose or those purposes. 3) Personal data shall be adequate, relevant and not excessive in relation to the purpose or purposes for which they are processed. 4) Personal data shall be accurate and, where necessary, kept up to date. 5) Personal data processed for any purpose or purposes shall not be kept for longer than is necessary for that purpose or those purposes. 6) Individuals have the right to access data kept about them, and check and update it if necessary. 7) Appropriate technical and organisational measures shall be taken against unauthorised or unlawful processing of personal data and against accidental loss or destruction of, or damage to, personal data. (They needfor: security) Exemptions include data processing • National security 8) Personal data shall not be transferred to a country or territory outside the European Economic Area unless that • Crime and taxation country or territory ensures an adequate level of protection for the rights and freedoms of data subjects in relation to the processing of personal data. • Domestic purposes (any data used solely for an household, like a phonebook)