Digital Image Watermarking ErHsien Fu EE 381 K15280




![Convolutional Codes C 0 Input=[. . . 101101010110000] G 0 = [1 1 0 Convolutional Codes C 0 Input=[. . . 101101010110000] G 0 = [1 1 0](https://slidetodoc.com/presentation_image/5339d2b628a81b7b67f834923fa02ad6/image-11.jpg)


- Slides: 17

Digital Image Watermarking Er-Hsien Fu EE 381 K-15280 Student Presentation

Overview • Introduction • Background Watermark Properties Embedding Detection • The Project Introduction Embedding Detection • Conclusions

Introduction • Watermark--an invisible signature embedded inside an image to show authenticity or proof of ownership • Discourage unauthorized copying and distribution of images over the internet • Ensure a digital picture has not been altered • Software can be used to search for a specific watermark

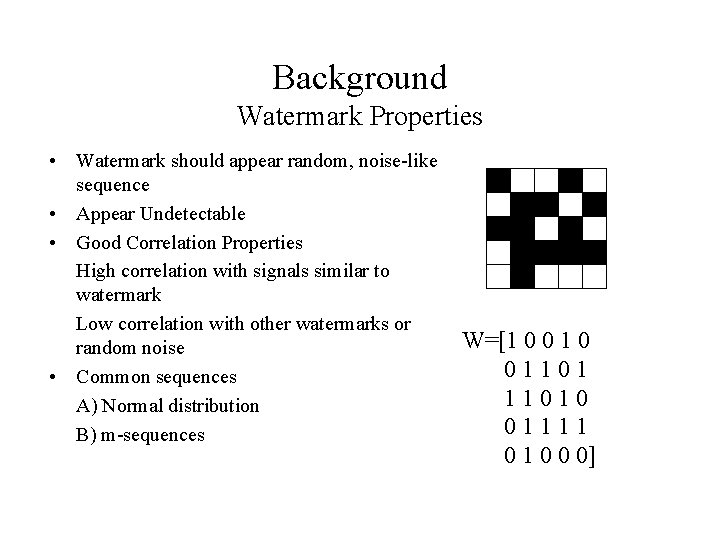
Background Watermark Properties • Watermark should appear random, noise-like sequence • Appear Undetectable • Good Correlation Properties High correlation with signals similar to watermark Low correlation with other watermarks or random noise • Common sequences A) Normal distribution B) m-sequences W=[1 0 011010 01111 0 0 0]

Project: Introduction • Possible for watermark to be binary sequence • Error-correction coding techniques • Use convolutional codes • Decode by Viterbi algorithm • Compare with non-coding method • See if it improves watermark detection • More or less robust to attacks? Additive noise, JPEG Compression, Rescale, Unzign • Performance assessed by correlation coefficient

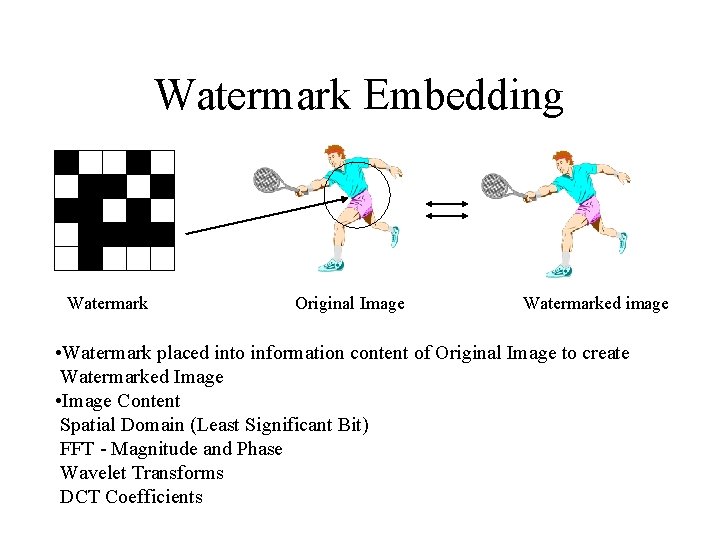
Watermark Embedding Watermark Original Image Watermarked image • Watermark placed into information content of Original Image to create Watermarked Image • Image Content Spatial Domain (Least Significant Bit) FFT - Magnitude and Phase Wavelet Transforms DCT Coefficients

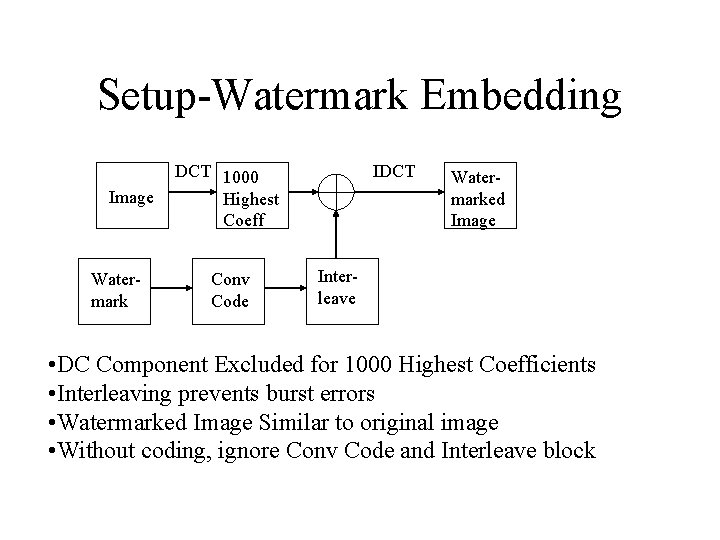
Setup-Watermark Embedding Image Watermark DCT 1000 Highest Coeff Conv Code IDCT Watermarked Image Interleave • DC Component Excluded for 1000 Highest Coefficients • Interleaving prevents burst errors • Watermarked Image Similar to original image • Without coding, ignore Conv Code and Interleave block

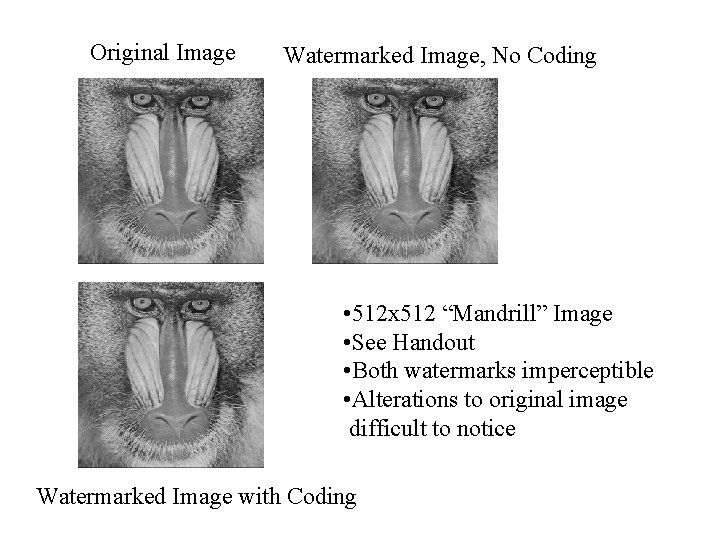
Original Image Watermarked Image, No Coding • 512 x 512 “Mandrill” Image • See Handout • Both watermarks imperceptible • Alterations to original image difficult to notice Watermarked Image with Coding

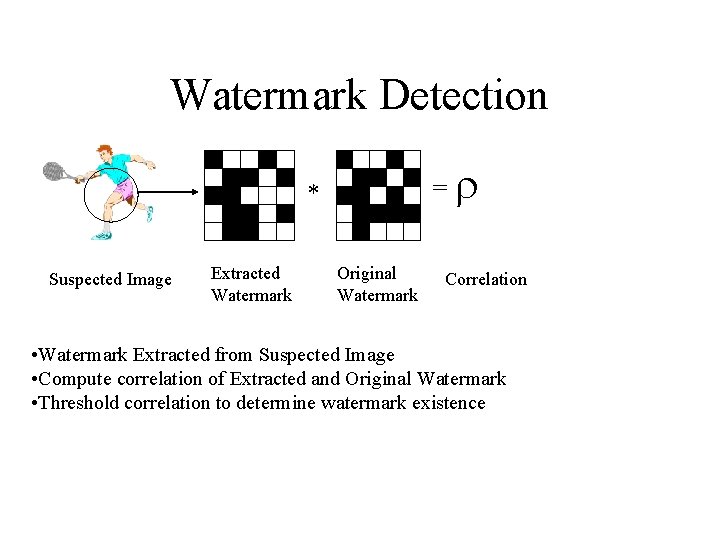
Watermark Detection = * Suspected Image Extracted Watermark Original Watermark Correlation • Watermark Extracted from Suspected Image • Compute correlation of Extracted and Original Watermark • Threshold correlation to determine watermark existence

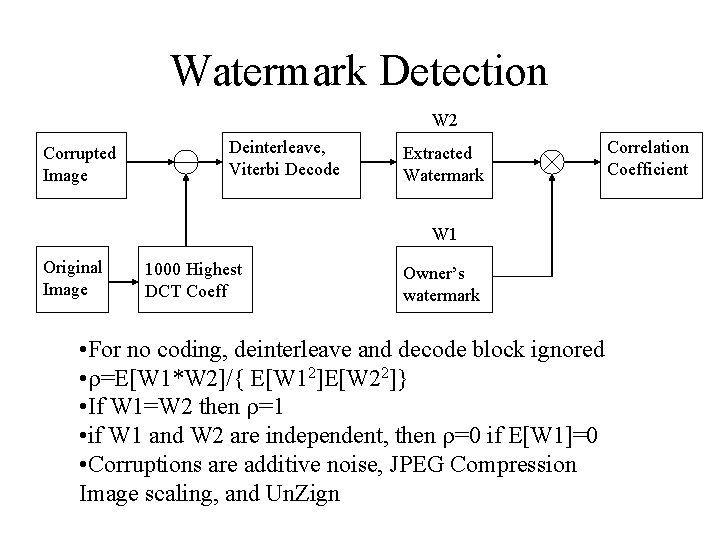
Watermark Detection W 2 Corrupted Image Deinterleave, Viterbi Decode Extracted Watermark W 1 Original Image 1000 Highest DCT Coeff Owner’s watermark • For no coding, deinterleave and decode block ignored • =E[W 1*W 2]/{ E[W 12]E[W 22]} • If W 1=W 2 then =1 • if W 1 and W 2 are independent, then =0 if E[W 1]=0 • Corruptions are additive noise, JPEG Compression Image scaling, and Un. Zign Correlation Coefficient
![Convolutional Codes C 0 Input 101101010110000 G 0 1 1 0 Convolutional Codes C 0 Input=[. . . 101101010110000] G 0 = [1 1 0](https://slidetodoc.com/presentation_image/5339d2b628a81b7b67f834923fa02ad6/image-11.jpg)
Convolutional Codes C 0 Input=[. . . 101101010110000] G 0 = [1 1 0 1 1] G 1 = [1 0 1 1 1 0 0 0 1] C 1 • Output C 0 = conv(G 0, Input); Output C 1=conv(G 1, Input) • Convolutional code implemented using linear shift registers • Adds redundancy for error-correction • Encoding/Decoding well researched • Good coding performance, very popular

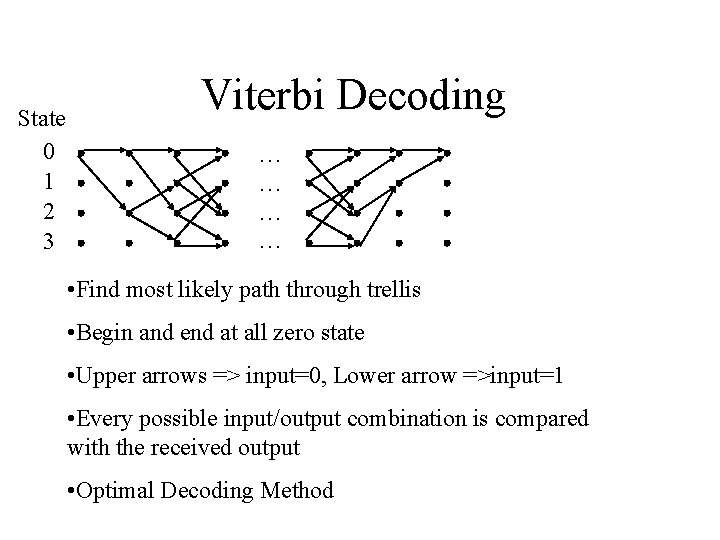
State 0 1 2 3 Viterbi Decoding … … • Find most likely path through trellis • Begin and end at all zero state • Upper arrows => input=0, Lower arrow =>input=1 • Every possible input/output combination is compared with the received output • Optimal Decoding Method

No Coding: Additive Noise(0, 900) With Coding: Additive Noise (0, 900) • Zero mean additive noise, variance=100, 400, 900 • Both methods had high correlation • Coding method performed slightly better • For variance = 900 (no coding) = 77% p (coding) = 84%

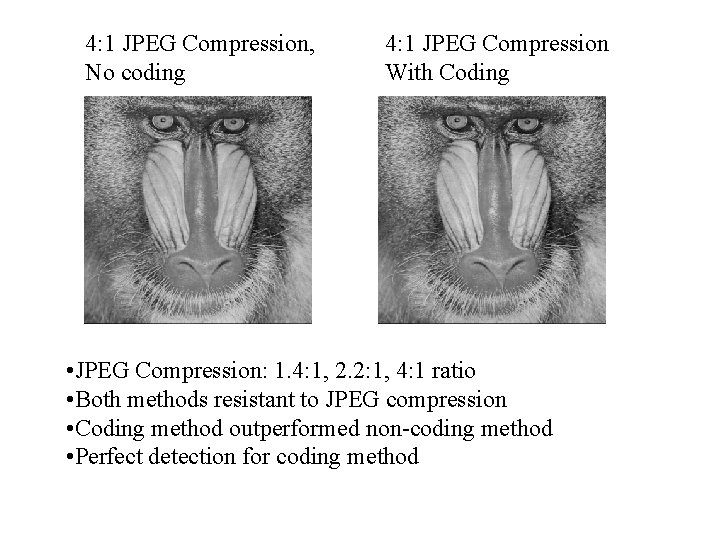
4: 1 JPEG Compression, No coding 4: 1 JPEG Compression With Coding • JPEG Compression: 1. 4: 1, 2. 2: 1, 4: 1 ratio • Both methods resistant to JPEG compression • Coding method outperformed non-coding method • Perfect detection for coding method

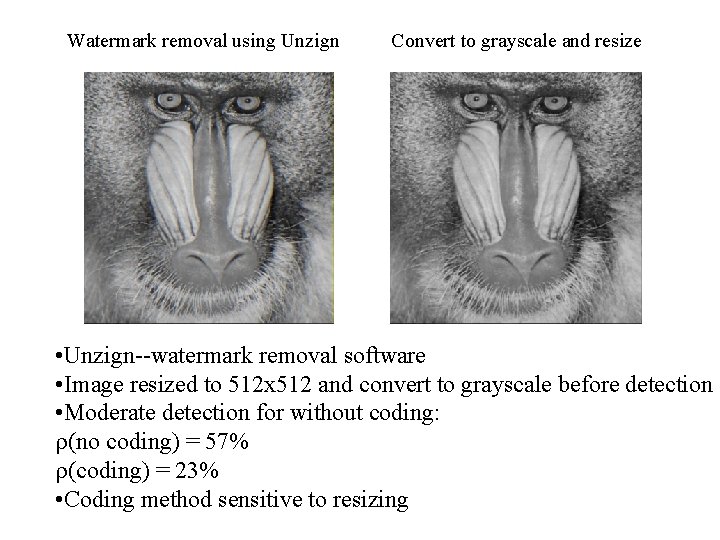
Watermark removal using Unzign Convert to grayscale and resize • Unzign--watermark removal software • Image resized to 512 x 512 and convert to grayscale before detection • Moderate detection for without coding: (no coding) = 57% (coding) = 23% • Coding method sensitive to resizing

Conclusions • Convolutional coding more immune to additive noise and JPEG Compression • Coding method fragile w. r. t. rescaled images • Moderate detection levels for unzigned images • Further Suggestion: Try block DCT Use Wavelet Transform Exploit Human Visual System

Questions