DFARS 204 73 252 204 7012 What is











- Slides: 14

DFARS 204. 73 & 252. 204 -7012 What is Unclassified Controlled Technical Information (UCTI)?

The First Line of Defense Program Managers and Contracts Managers are your first line of defense for ensuring we are aware of UCTI as it flows into our network. You cannot protect it properly if we do not know about it.

UCTI in Layman’s Terms It was instituted in Nov 2013 by the new DFARS provision 204. 73 and contract clause 252. 204 -7012. This clause is a result of Executive Order 13556 issued 4 Nov 2010. It creates a new category of data—unclassified, controlled technical information. UCTI is identified by US Government defined markings. You have certain responsibilities regarding how you protect the data, particularly related to your network and IT Security. The US Government requires the clause be included in “all solicitations and contracts. ” These means both FAR 12 and FAR 15.

Executive Order 13556 Unclassified Controlled Information Scope: Establishes a program for managing all unclassified information in the Executive branch that requires safeguarding or dissemination controls, pursuant to and consistent with applicable law, regulations, and governmentwide policies. Agency Responsibility: Each department and agency will identify a mechanism, i. e. , office or individual(s), responsible for administering CUI policy. Agencies will also develop tailored CUI policies to meet agency-specific needs, as well as establish an internal oversight mechanism to promote consistent practices. Implementation Strategy: Departments and agencies will review all categories, subcategories, and markings used to designate unclassified information for safeguarding and dissemination controls and submit proposed categories, subcategories, and markings to the EA for review and approval.

Unclassified Controlled Technical Information (DFARS 252. 204 -7012) Technical information with military or space application that is subject to controls on the access, use, reproduction, modification, performance, display, release, disclosure, or dissemination. Controlled technical information is to be marked with one of the distribution statements B through F, in accordance with Do. D Instruction 5230. 24, Distribution Statements on Technical Documents. The term does not include information that is lawfully publicly available without restrictions.

What constitutes UCTI “marking? ” Do. D Instruction 5230. 24 “DISTRIBUTION STATEMENT B. Distribution authorized to U. S. Government agencies only (fill in reason) (date of determination). Other requests for this document shall be referred to (insert controlling Do. D office). ” “DISTRIBUTION STATEMENT C. Distribution authorized to U. S. Government agencies and their contractors (fill in reason) (date of determination). Other requests for this document shall be referred to (insert controlling Do. D office). ” “DISTRIBUTION STATEMENT D. Distribution authorized to the Department of Defense and U. S. Do. D contractors only (fill in reason) (date of determination). Other requests shall be referred to (insert controlling Do. D office). ” “DISTRIBUTION STATEMENT E. Distribution authorized to Do. D Components only (fill in reason) (date of determination). Other requests shall be referred to (insert controlling Do. D office). ” “DISTRIBUTION STATEMENT F. Further dissemination only as directed by (inserting controlling Do. D office) (date of determination) or higher Do. D authority. ” Distribution Statement F is normally used only on classified technical documents, but may be used on unclassified technical documents when specific authority exists (e. g. , designation as direct military support as in Statement E).

What exactly is “technical information? ” Technical information is “technical data or computer software, as those terms are defined in the clause at DFARS 252. 227 -7013, regardless of whether or not the clause is incorporated in this solicitation or contract. ” “Technical data” means recorded information, regardless of the form or method of the recording, of a scientific or technical nature (including computer software documentation). The term does not include computer software or data incidental to contract administration, such as financial and/or management information. “Computer software” means computer programs, source code listings, object code listings, design details, algorithms, processes, flow charts, formulae and related material that would enable the software to be reproduced, recreated, or recompiled. Computer software does not include computer data bases or computer software documentation. Examples of technical information include: ◦ research and engineering data, engineering drawings and associated lists, specifications, standards, process sheets, manuals, technical reports, technical orders, catalog-item identifications, data sets, studies and analyses and related information, and computer software executable code and source code.

Are FOUO and UCTI the same thing? No, they are not the same classification of data. FOUO is a data dissemination control marking used by the Department of Defense to identify data that may be exempt from public release under exemptions 2 through 9 of the Freedom of Information Act (FOIA). UCTI information may also often be marked as FOUO due to the sensitivity of the information, yet they remain two separate categories of data. Per the Federal Register, the final UCTI rule has been scoped to only refer to unclassified controlled technical information [Not FOUO]. UCTI items will be marked in accordance with Do. DI 5230. 24. Reference: Federal Register Volume 78, Number 222 (Monday, November 18, 2013)] [Rules and Regulations] [Pages 69273 -69282] From the Federal Register Online via the Government Printing Office [www. gpo. gov] [FR Doc No: 2013 -27313], http: //www. gpo. gov/fdsys/pkg/FR-2013 -1118/html/2013 -27313. htm

Safeguarding Requirements DFARS 252. 204 -7012(b) The Contractor shall provide adequate security to safeguard unclassified controlled technical information from compromise. To provide adequate security, the Contractor shall — (1) Implement information systems security in its project, enterprise, or company-wide unclassified information technology system(s) that may have unclassified controlled technical information resident on or transiting through them. The information systems security program shall implement, at a minimum — (i) The specified National Institute of Standards and Technology (NIST) Special Publication (SP) 800 -53 security controls identified in the following table; or of how— (ii) If a NIST control is not implemented, the Contractor shall submit to the Contracting Officer a written explanation (A) The required security control identified in the following table is not applicable; or (B) An alternative control or protective measure is used to achieve equivalent protection. (2) Apply other information systems security requirements when the Contractor reasonably determines that information systems security measures, in addition to those identified in paragraph (b)(1) of this clause, may be required to provide adequate security in a dynamic environment based on an assessed risk or vulnerability.

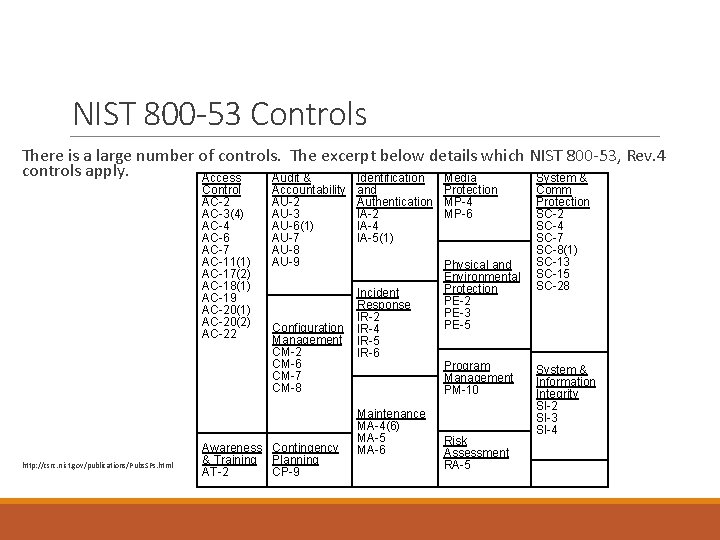
NIST 800 -53 Controls There is a large number of controls. The excerpt below details which NIST 800 -53, Rev. 4 controls apply. Access Audit & Identification Media System & Control AC-2 AC-3(4) AC-4 AC-6 AC-7 AC-11(1) AC-17(2) AC-18(1) AC-19 AC-20(1) AC-20(2) AC-22 http: //csrc. nist. gov/publications/Pubs. SPs. html Accountability AU-2 AU-3 AU-6(1) AU-7 AU-8 AU-9 Configuration Management CM-2 CM-6 CM-7 CM-8 Awareness Contingency & Training Planning AT-2 CP-9 and Protection Authentication MP-4 IA-2 MP-6 IA-4 IA-5(1) Incident Response IR-2 IR-4 IR-5 IR-6 Maintenance MA-4(6) MA-5 MA-6 Physical and Environmental Protection PE-2 PE-3 PE-5 Program Management PM-10 Risk Assessment RA-5 Comm Protection SC-2 SC-4 SC-7 SC-8(1) SC-13 SC-15 SC-28 System & Information Integrity SI-2 SI-3 SI-4

Are you required to flow this down to subcontractors? Yes, the clause must be flowed down. “The Contractor shall include the substance of this clause, including this paragraph (g), in all subcontracts, including subcontracts for commercial items. ” DFARS 252. 204 -7012(g)

Reporting The Contractor shall report. . . within 72 hours of discovery of any cyber incident. . . that affects unclassified controlled technical information resident on or transiting through the Contractor’s unclassified information systems Reportable cyber incidents include the following: (i) A cyber incident involving possible exfiltration, manipulation, or other loss or compromise of any unclassified controlled technical information resident on or transiting through Contractor’s, or its subcontractors’, unclassified information systems. (ii) Any other activities not included in paragraph (d)(2)(i) of this clause that allow unauthorized access to the Contractor’s unclassified information system on which unclassified controlled technical information is resident on or transiting.

Financial Impact of Compliance Supplementary information provided in the Federal Register addressing public comments to the rule discusses requests for: ◦ Guidance regarding whether charges are allowable under CAS ◦ Answer: Yes ◦ Requests for Do. D to provide funding to contractors to cover the costs of compliance ◦ Answer: No See following slide for details.

Financial Impact of Compliance » Allowable Costs Under Cost Accounting Standards (CAS) Comment: One respondent asked if the cost associated with compliance to the DFARS changes is allowable under CAS. ◦ Response: Cost Accounting Standards address measurement, allocation and assignment of costs. FAR 31 and DFARS 231, specifically FAR 31. 201 - 2, address the allowability of costs. There is nothing in FAR 31 or DFARS 231 that would make costs of compliance with DFARS unallowable if the costs are incurred in accordance with FAR 31. 201 -2. While we cannot know in advance if a company will incur costs in accordance with FAR 31. 201 -2, there is nothing included in the final rule that would cause or compel a company to incur costs that would be in violation of FAR 31. 201 -2. Several respondents stated that Do. D needs to account for/ provide funding for the additional costs of implementation. ◦ Response: Implementation of this rule may increase contractor costs that would be accounted for through the normal course of business. Reference: Federal Register Volume 78, Number 222 (Monday, November 18, 2013)] [Rules and Regulations] [Pages 69273 -69282] From the Federal Register Online via the Government Printing Office [www. gpo. gov] [FR Doc No: 2013 -27313], http: //www. gpo. gov/fdsys/pkg/FR-2013 -11 -18/html/2013 -27313. htm