DEPARTMENT OF THE NAVY CHIEF INFORMATION OFFICER DON








- Slides: 14

DEPARTMENT OF THE NAVY CHIEF INFORMATION OFFICER DON IM/IT Conference Identity Theft/Fraud DON IT/CYBERSPACE EFFICIENCIES • ENTERPRISE ARCHITECTURE • EMERGING TECHNOLOGY • ENTERPRISE COMMERCIAL IT STRATEGY • CYBERSECURITY • CYBER / IT WORKFORCE INVESTMENT MANAGEMENT • CRITICAL INFRASTRUCTURE • INFORMATION SHARING • KNOWLEDGE & RECORDS MANAGEMENT • PRIVACY • NAVAL NETWORKS • ENTERPRISE

DEPARTMENT OF THE NAVY CHIEF INFORMATION OFFICER Objectives § Understand the terms, identity fraud and identity theft § Know the different types of identity theft § Remember key trends and facts regarding identity theft § Know how identity thieves operate § Be able to take steps that reduce the chance that you will be a victim of identity fraud § Know what actions you must take in the office to minimize the loss of PII § Know the pros and cons of buying credit monitoring service § Understand what actions are needed if you become a victim of identity fraud DON IT/CYBERSPACE EFFICIENCIES • ENTERPRISE ARCHITECTURE • EMERGING TECHNOLOGY • ENTERPRISE COMMERCIAL IT STRATEGY • CYBERSECURITY • CYBER / IT WORKFORCE INVESTMENT MANAGEMENT • CRITICAL INFRASTRUCTURE • INFORMATION SHARING • KNOWLEDGE & RECORDS MANAGEMENT • PRIVACY • NAVAL NETWORKS • ENTERPRISE

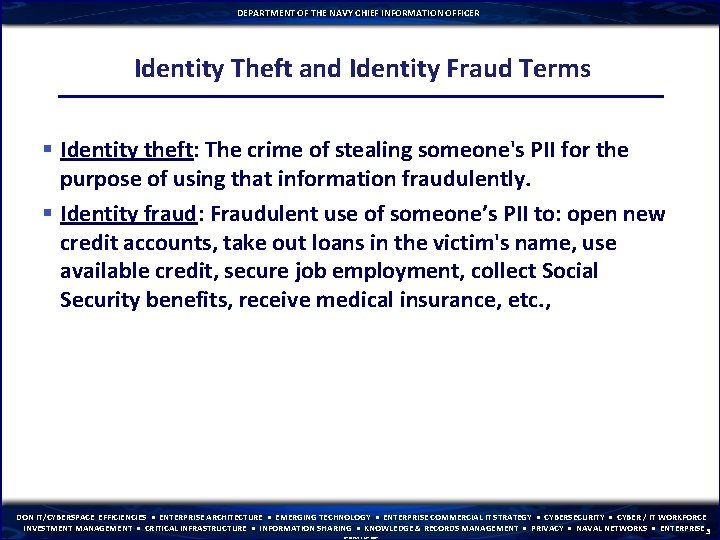
DEPARTMENT OF THE NAVY CHIEF INFORMATION OFFICER Identity Theft and Identity Fraud Terms § Identity theft: The crime of stealing someone's PII for the purpose of using that information fraudulently. § Identity fraud: Fraudulent use of someone’s PII to: open new credit accounts, take out loans in the victim's name, use available credit, secure job employment, collect Social Security benefits, receive medical insurance, etc. , DON IT/CYBERSPACE EFFICIENCIES • ENTERPRISE ARCHITECTURE • EMERGING TECHNOLOGY • ENTERPRISE COMMERCIAL IT STRATEGY • CYBERSECURITY • CYBER / IT WORKFORCE INVESTMENT MANAGEMENT • CRITICAL INFRASTRUCTURE • INFORMATION SHARING • KNOWLEDGE & RECORDS MANAGEMENT • PRIVACY • NAVAL NETWORKS • ENTERPRISE 3

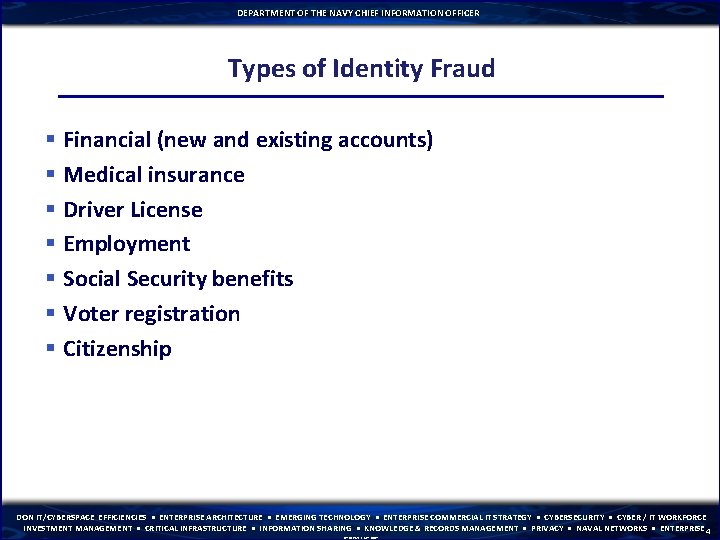
DEPARTMENT OF THE NAVY CHIEF INFORMATION OFFICER Types of Identity Fraud § Financial (new and existing accounts) § Medical insurance § Driver License § Employment § Social Security benefits § Voter registration § Citizenship DON IT/CYBERSPACE EFFICIENCIES • ENTERPRISE ARCHITECTURE • EMERGING TECHNOLOGY • ENTERPRISE COMMERCIAL IT STRATEGY • CYBERSECURITY • CYBER / IT WORKFORCE INVESTMENT MANAGEMENT • CRITICAL INFRASTRUCTURE • INFORMATION SHARING • KNOWLEDGE & RECORDS MANAGEMENT • PRIVACY • NAVAL NETWORKS • ENTERPRISE 4

DEPARTMENT OF THE NAVY CHIEF INFORMATION OFFICER Identity Theft/Fraud Trends § FTC reports 7 M+ of U. S. adult population has experienced ID fraud in 2010 § In ’ 05, 1. 8 M cases new account fraud; 6. 5 M cases existing account fraud § Crimes are still more often offline than online but thieves are becoming more organized and sophisticated § Risk is greatest when information was stolen by someone targeting the data e. g. hacker, burglar. Insider threat is growing § “Friendly Fraud” 1 in 7 ID thieves were known by victim § SSNs with full name are "the most valuable commodities for an identity thief. “ Sources: old public records , internet, old official Do. D photos § Phishing attacks aimed at ID theft affect all of us – Banks, Pay Pal, bogus job offers § ID fraud of children and people who are deceased, a growing problem § Most consumers have zero liability for credit card thefts; Only 44% of major banks offer same protection for debit card transactions; 33 % for ATM withdrawals § The average consumer cost of ID fraud involving debit card is $795. 00 DON IT/CYBERSPACE EFFICIENCIES • ENTERPRISE ARCHITECTURE • EMERGING TECHNOLOGY • ENTERPRISE COMMERCIAL IT STRATEGY • CYBERSECURITY • CYBER / IT WORKFORCE INVESTMENT MANAGEMENT • CRITICAL INFRASTRUCTURE • INFORMATION SHARING • KNOWLEDGE & RECORDS MANAGEMENT • PRIVACY • NAVAL NETWORKS • ENTERPRISE

DEPARTMENT OF THE NAVY CHIEF INFORMATION OFFICER What are the “tools” of the trade? § Phishing – Uses fear factor in “legitimate” email to get recipient to give up high value PII used to commit fraud. § Skimming – Installing devices and cameras to capture bank card numbers and pin numbers from ATMs and other credit/debit card machines – Copying credit/debit card information during purchase transactions § Telephone scamming § Dumpster diving § Thievery/internet hacking § Mail tampering § Using PII found on social networks DON IT/CYBERSPACE EFFICIENCIES • ENTERPRISE ARCHITECTURE • EMERGING TECHNOLOGY • ENTERPRISE COMMERCIAL IT STRATEGY • CYBERSECURITY • CYBER / IT WORKFORCE INVESTMENT MANAGEMENT • CRITICAL INFRASTRUCTURE • INFORMATION SHARING • KNOWLEDGE & RECORDS MANAGEMENT • PRIVACY • NAVAL NETWORKS • ENTERPRISE 6

DEPARTMENT OF THE NAVY CHIEF INFORMATION OFFICER PII Elements Needed to Commit Fraud § The more PII elements disclosed, the easier it is to commit fraud § Disclosure of PII in the public domain may be difficult to recover PII has a very long shelf life § Loss of sensitive PII causes greatest “harm” to an individual – Full name and full Social Security Number (SSN) – Financial information- bank account #, credit card #, bank routing # – Medical data- diagnoses, treatment, medical history – Place of birth – Date of birth – Mother’s maiden name – Passport # DON IT/CYBERSPACE EFFICIENCIES • ENTERPRISE ARCHITECTURE • EMERGING TECHNOLOGY • ENTERPRISE COMMERCIAL IT STRATEGY • CYBERSECURITY • CYBER / IT WORKFORCE INVESTMENT MANAGEMENT • CRITICAL INFRASTRUCTURE • INFORMATION SHARING • KNOWLEDGE & RECORDS MANAGEMENT • PRIVACY • NAVAL NETWORKS • ENTERPRISE

DEPARTMENT OF THE NAVY CHIEF INFORMATION OFFICER Useful Documents to Commit Fraud § Income Tax return § Death certificate § Birth certificate § SSN card § Lease agreement § Real Estate Settlement Agreement (HUD-1) § Military ID card § Cancelled bank check § Passport § Credit report § DD 214 – Military Discharge Certificate DON IT/CYBERSPACE EFFICIENCIES • ENTERPRISE ARCHITECTURE • EMERGING TECHNOLOGY • ENTERPRISE COMMERCIAL IT STRATEGY • CYBERSECURITY • CYBER / IT WORKFORCE INVESTMENT MANAGEMENT • CRITICAL INFRASTRUCTURE • INFORMATION SHARING • KNOWLEDGE & RECORDS MANAGEMENT • PRIVACY • NAVAL NETWORKS • ENTERPRISE 8

DEPARTMENT OF THE NAVY CHIEF INFORMATION OFFICER PII “Gold Mines” § Auto dealer’s finance/credit office § Receptionist desk in medical/dental office § Pentagon visitor’s processing area § Grocery store checkout line § Incoming and outgoing mail in home mailbox § Your paper trash § Your car glove box § A purse, wallet and or briefcase § Personal cell phone § Personal computer DON IT/CYBERSPACE EFFICIENCIES • ENTERPRISE ARCHITECTURE • EMERGING TECHNOLOGY • ENTERPRISE COMMERCIAL IT STRATEGY • CYBERSECURITY • CYBER / IT WORKFORCE INVESTMENT MANAGEMENT • CRITICAL INFRASTRUCTURE • INFORMATION SHARING • KNOWLEDGE & RECORDS MANAGEMENT • PRIVACY • NAVAL NETWORKS • ENTERPRISE 9

DEPARTMENT OF THE NAVY CHIEF INFORMATION OFFICER Ways You Can Protect Yourself § Never leave your purse/wallet/laptop in car. § Do not use free WI-FI cafes – install secure firewall at home. § Do not provide PII over the phone unless you initiate the call. § Do not click on any links in email sent from your financial institution – go to their web site and sign in to do business. § Install virus and spyware detection software on your PC. § Limit the number of credit/debit cards you have. § Shred everything with PII that you dispose of. § Physically destroy your hard drive when getting rid of old computers (e. g. drill holes, crush with sledge hammer). DON IT/CYBERSPACE EFFICIENCIES • ENTERPRISE ARCHITECTURE • EMERGING TECHNOLOGY • ENTERPRISE COMMERCIAL IT STRATEGY • CYBERSECURITY • CYBER / IT WORKFORCE INVESTMENT MANAGEMENT • CRITICAL INFRASTRUCTURE • INFORMATION SHARING • KNOWLEDGE & RECORDS MANAGEMENT • PRIVACY • NAVAL NETWORKS • ENTERPRISE 10

DEPARTMENT OF THE NAVY CHIEF INFORMATION OFFICER Handling PII in the office… § Mail § Rosters § Hard copy storage § Collecting PII from employees § FOUO privacy marking § Disposal § FAX machine § Your computer § Copier § Shared drive § Email § Telephone DON IT/CYBERSPACE EFFICIENCIES • ENTERPRISE ARCHITECTURE • EMERGING TECHNOLOGY • ENTERPRISE COMMERCIAL IT STRATEGY • CYBERSECURITY • CYBER / IT WORKFORCE INVESTMENT MANAGEMENT • CRITICAL INFRASTRUCTURE • INFORMATION SHARING • KNOWLEDGE & RECORDS MANAGEMENT • PRIVACY • NAVAL NETWORKS • ENTERPRISE

DEPARTMENT OF THE NAVY CHIEF INFORMATION OFFICER Choosing a Credit Monitoring Service: § One or more of your credit reports is constantly tracked § Monitors suspicious account activity after fraud occurs § Monitors only financial fraud activity, not medical, employment, etc. , § Serves as an early warning that accounts may be tampered with § Must have your permission to impose fraud alert or credit freeze on your accounts § Average cost is $15/mo – how long do you pay for service? § Look for legal services and insurance protection § Laws hold individual liable for $50. 00, if credit card fraud DON IT/CYBERSPACE EFFICIENCIES • ENTERPRISE ARCHITECTURE • EMERGING TECHNOLOGY • ENTERPRISE COMMERCIAL IT STRATEGY • CYBERSECURITY • CYBER / IT WORKFORCE INVESTMENT MANAGEMENT • CRITICAL INFRASTRUCTURE • INFORMATION SHARING • KNOWLEDGE & RECORDS MANAGEMENT • PRIVACY • NAVAL NETWORKS • ENTERPRISE 12

DEPARTMENT OF THE NAVY CHIEF INFORMATION OFFICER If You Are A Victim of Identity Theft… 1. Place a fraud alert on your credit reports, and review your credit reports. Call Trans. Union: 1 -800 -680 -7289; www. transunion. com; Fraud Victim Assistance Division, P. O. Box 6790, ; Equifax: 1 -800 -525 -6285; www. equifax. com; 30374 -0241; or Experian: 1 -888 -EXPERIAN (397 -3742); www. experian. com 2. Close the accounts that you know, or believe, have been tampered with or opened fraudulently. 3. File a complaint with the Federal Trade Commission. 4. File a report with your local police or the police in the community where the identity theft took place. 5. Consider buying credit monitoring services. DON IT/CYBERSPACE EFFICIENCIES • ENTERPRISE ARCHITECTURE • EMERGING TECHNOLOGY • ENTERPRISE COMMERCIAL IT STRATEGY • CYBERSECURITY • CYBER / IT WORKFORCE INVESTMENT MANAGEMENT • CRITICAL INFRASTRUCTURE • INFORMATION SHARING • KNOWLEDGE & RECORDS MANAGEMENT • PRIVACY • NAVAL NETWORKS • ENTERPRISE 13

DEPARTMENT OF THE NAVY CHIEF INFORMATION OFFICER DON Privacy POCs STEVE MUCK DON CIO DON Privacy Team Lead Phone: (703) 695 -1297 Email: steven. muck@navy. mil STEVE DAUGHETY DON CIO Phone: (703) 602 -6393 Email: steve. daughety 1. ctr@navy. mil BARBARA FIGUEROA DON Forms Manager (DNS 51) Phone: (202) 433 -2835 Email: barbara. figueroa@navy. mil ROBIN PATTERSON OPNAV DNS-36 DON Privacy Act Program Manager Phone: (202) 685 -6545 Email: robin. patterson@navy. mil Vacant HQMC C 4 CYBER SECURITY DIVISION PII/PIA Analyst Phone: (571) 256 -8876 Email: XXX@hqmc. mil DEBORAH CONTAOI OPNAV DNS-36 Phone: (202) 685 -6546 Email: teri. contaoi. ctr@navy. mil LAURIE SOMERS HQMC Phone: (703) 6614 -2951 Email: laurie. somers@hqmc. mil www. doncio. navy. mil/privacy DON IT/CYBERSPACE EFFICIENCIES • ENTERPRISE ARCHITECTURE • EMERGING TECHNOLOGY • ENTERPRISE COMMERCIAL IT STRATEGY • CYBERSECURITY • CYBER / IT WORKFORCE 14 INVESTMENT MANAGEMENT • CRITICAL INFRASTRUCTURE • INFORMATION SHARING • KNOWLEDGE & RECORDS MANAGEMENT • PRIVACY • NAVAL NETWORKS • ENTERPRISE
 Department of the navy chief information officer
Department of the navy chief information officer Office of the government chief information officer
Office of the government chief information officer Jp9102
Jp9102 Navy supply corps officer career path
Navy supply corps officer career path Block 40 chief eval
Block 40 chief eval You better pay attention
You better pay attention Submarine officer career path
Submarine officer career path Chapter 9 lesson 3 commander in chief and chief diplomat
Chapter 9 lesson 3 commander in chief and chief diplomat Chief knowledge officer job description
Chief knowledge officer job description Chief data officer training
Chief data officer training Cfo in organization chart
Cfo in organization chart Chief improvement officer
Chief improvement officer Adolfo gonzales chief probation officer
Adolfo gonzales chief probation officer Alexander kjerulf happiness at work
Alexander kjerulf happiness at work Chief reality officer
Chief reality officer