Deadlock Characterization Deadlock can arise if four conditions
















- Slides: 33

Deadlock Characterization Deadlock can arise if four conditions hold simultaneously: 1. 2. 3. 4. Mutual Exclusion Hold and Wait No Preemption Circular Wait

Mutual Exclusion n n only one process at a time can use a resource. If another process requests that resource, the requesting process must be delayed until the resource has been released

Hold and Wait n a process that holding at least one resource is waiting to acquire additional resources held by other processes.

No preemption n a resource can be released only voluntarily by the process holding it, after that process has completed its task.

Circular Wait there exists a set {P 0, P 1, …, P 0} of waiting processes such that P 0 is waiting for a resource that is held by P 1, P 1 is waiting for a resource that is held by P 2, …, Pn– 1 is waiting for a resource that is held by Pn, and P 0 is waiting for a resource that is held by P 0.

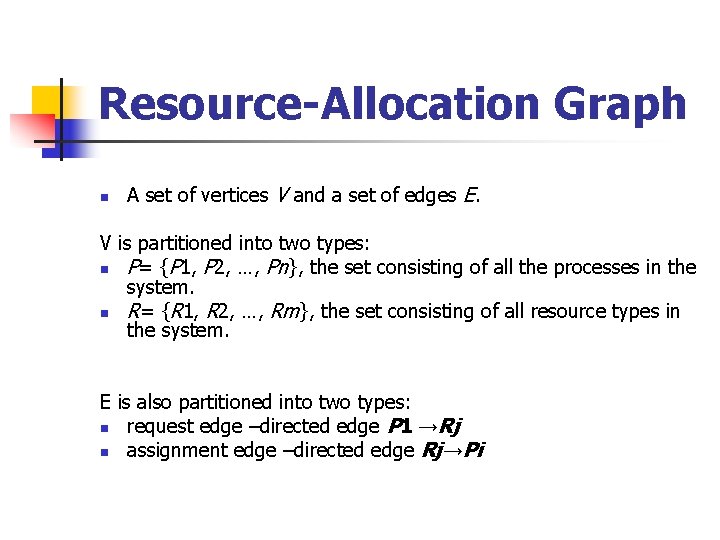
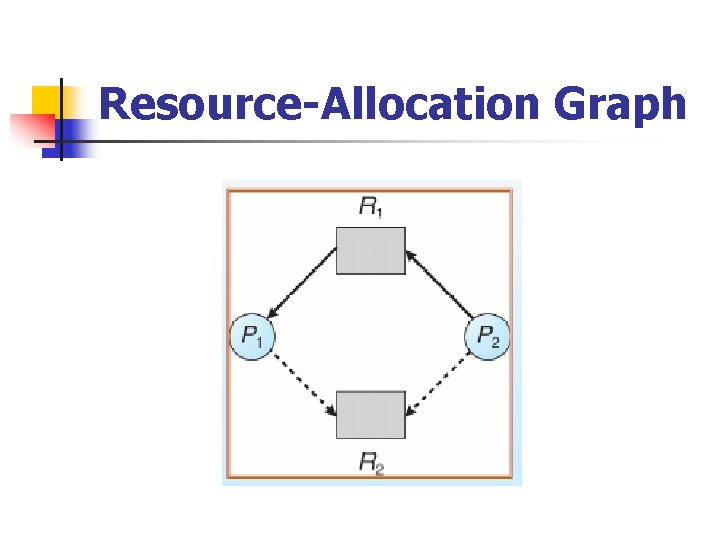
Resource-Allocation Graph n A set of vertices V and a set of edges E. V is partitioned into two types: n P= {P 1, P 2, …, Pn}, the set consisting of all the processes in the system. n R= {R 1, R 2, …, Rm}, the set consisting of all resource types in the system. E is also partitioned into two types: n request edge –directed edge P 1 →Rj n assignment edge –directed edge Rj→Pi

7. 4 Deadlock Prevention n We try to ensure that one of the four necessary conditions cannot hold, then we can prevent it Mutual Exclusion: If it is shareable resource, then we can break the mutual exclusion (such as: Read-only file) n If it is not a shareable resource, then mutual exclusion must hold (such as: Printer)

7. 4 Deadlock Prevention n Hold and wait: two methods 1. Require process to request and be allocated all its resources before it begins execution. 2. allow process to request resources only when the process has none.

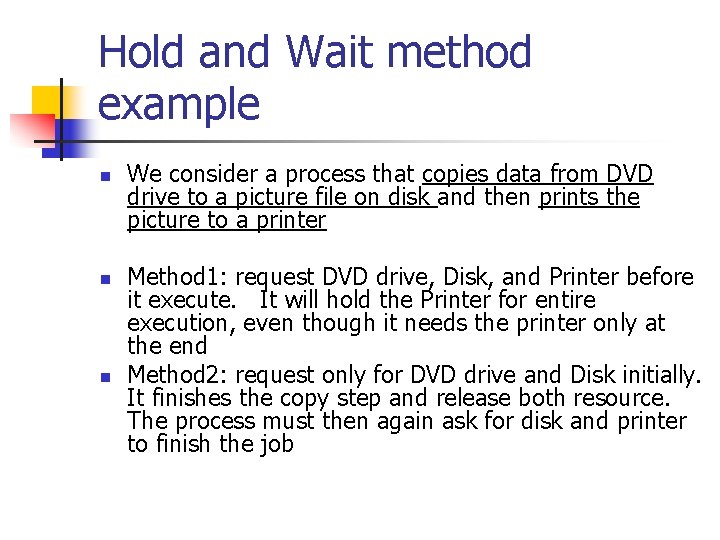
Hold and Wait method example n n n We consider a process that copies data from DVD drive to a picture file on disk and then prints the picture to a printer Method 1: request DVD drive, Disk, and Printer before it execute. It will hold the Printer for entire execution, even though it needs the printer only at the end Method 2: request only for DVD drive and Disk initially. It finishes the copy step and release both resource. The process must then again ask for disk and printer to finish the job

Hold and Wait method example n n Low resource utilization; starvation possible, (if a process needs several popular resources)

7. 4 Deadlock Prevention n NO preemption: If a process that is holding some resources requests another resource that cannot be immediately to allocated it, then all resources currently being held are released. Preempted resources are added to the list of resources for which the process is waiting. Process will be restarted only when it can regain its old resources, as well as the new ones that it is requesting.

7. 4 Deadlock Prevention Circular wait: impose a total ordering of all resource types, and require that each process requests resources in an increasing order of enumeration. n

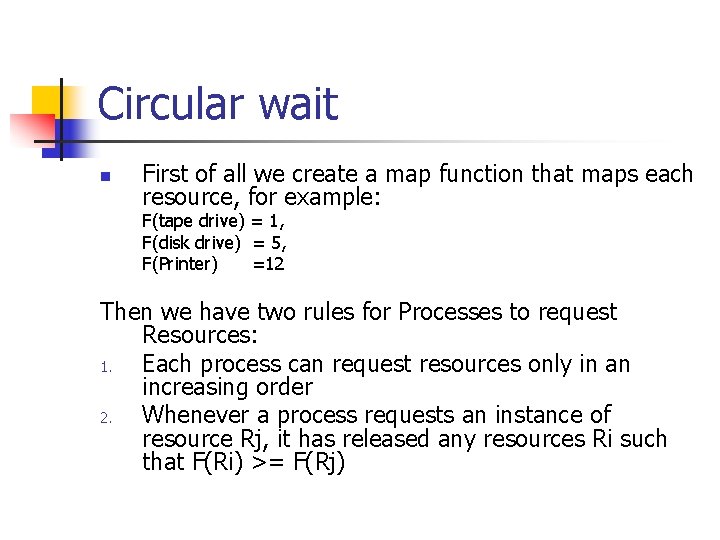
Circular wait n First of all we create a map function that maps each resource, for example: F(tape drive) = 1, F(disk drive) = 5, F(Printer) =12 Then we have two rules for Processes to request Resources: 1. Each process can request resources only in an increasing order 2. Whenever a process requests an instance of resource Rj, it has released any resources Ri such that F(Ri) >= F(Rj)

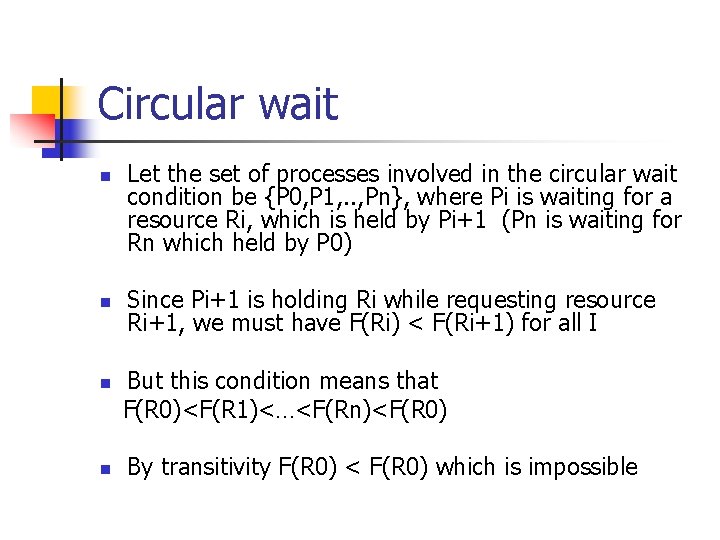
Circular wait n n Let the set of processes involved in the circular wait condition be {P 0, P 1, . . , Pn}, where Pi is waiting for a resource Ri, which is held by Pi+1 (Pn is waiting for Rn which held by P 0) Since Pi+1 is holding Ri while requesting resource Ri+1, we must have F(Ri) < F(Ri+1) for all I But this condition means that F(R 0)<F(R 1)<…<F(Rn)<F(R 0) By transitivity F(R 0) < F(R 0) which is impossible

7. 5 Deadlock Avoidance n n Possible side effects of preventing deadlock are low device utilization and reduce system throughput An alternative method for avoiding deadlocks is to require additional information about how resources are to be required.

7. 5 Deadlock Avoidance n n With this knowledge of the complete sequence of requests and releases for each process the system can decide for each request whether or not the process should wait in order to avoid possible future deadlock A deadlock avoidance algorithm dynamically examines the resource-allocation state to ensure that a circular wait condition can never happen

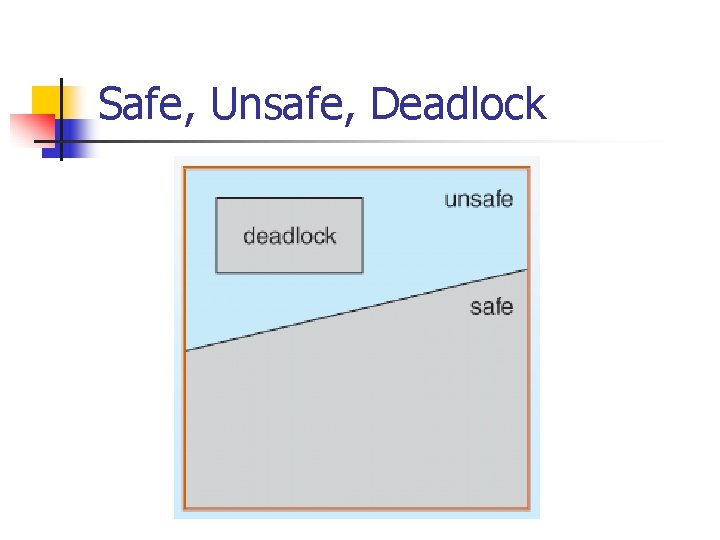
Safe State n n A state is safe if the system can allocate resources to each processes in some order (safe sequence) and still avoid a deadlock If no such sequence exists, then the system state is said to be unsafe

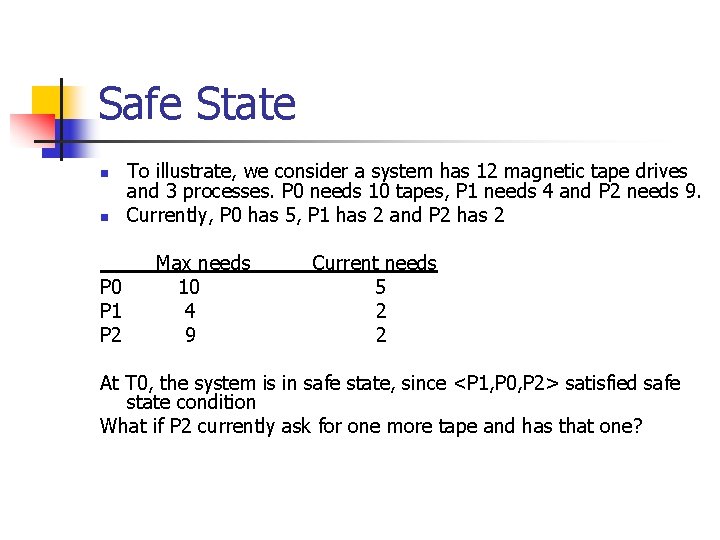
Safe State n n P 0 P 1 P 2 To illustrate, we consider a system has 12 magnetic tape drives and 3 processes. P 0 needs 10 tapes, P 1 needs 4 and P 2 needs 9. Currently, P 0 has 5, P 1 has 2 and P 2 has 2 Max needs 10 4 9 Current needs 5 2 2 At T 0, the system is in safe state, since <P 1, P 0, P 2> satisfied safe state condition What if P 2 currently ask for one more tape and has that one?

Safe, Unsafe, Deadlock

7. 5 Deadlock Avoidance n n n The algorithm is simply to ensure that the system will always remain in safe state. Therefore, if a process requests a resource that is currently available, it may still have to wait. Thus, resource utilization may be lower

Avoidance algorithms n n Single instance of a resource type. Use a resource allocation graph Multiple instances of a resource type. Use the banker’s algorithm

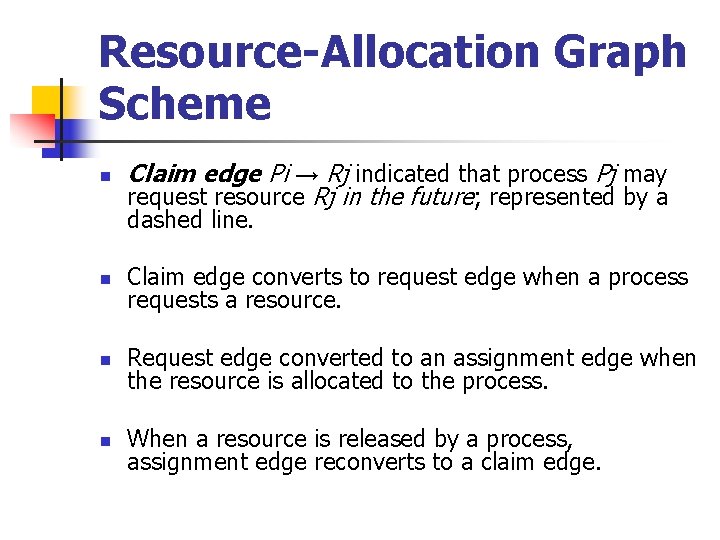
Resource-Allocation Graph Scheme n Claim edge Pi → Rj indicated that process Pj may request resource Rj in the future; represented by a dashed line. n Claim edge converts to request edge when a process requests a resource. n Request edge converted to an assignment edge when the resource is allocated to the process. n When a resource is released by a process, assignment edge reconverts to a claim edge.

Resource-Allocation Graph

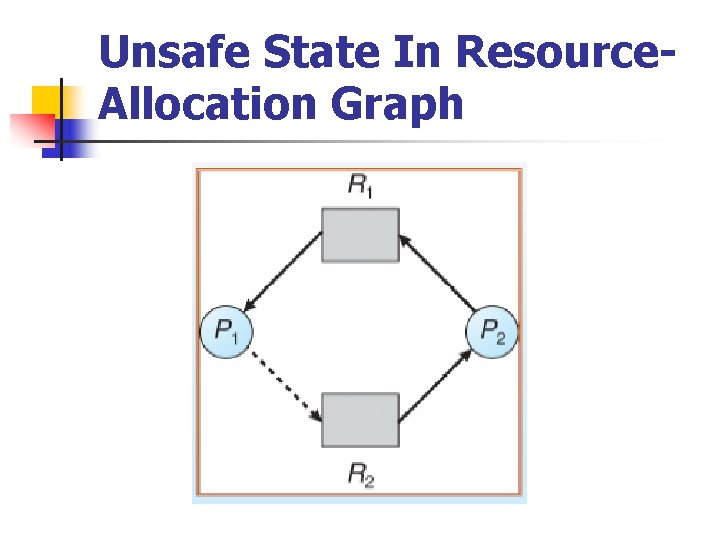
Unsafe State In Resource. Allocation Graph

Resource-Allocation Graph Algorithm n n Suppose that process Pi requests a resource Rj The request can be granted only if converting the request edge to an assignment edge does not result in the formation of a cycle in the resource allocation graph

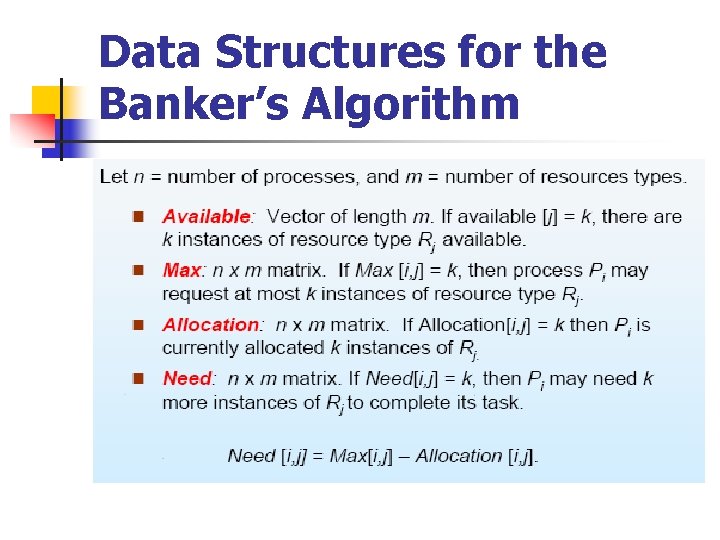
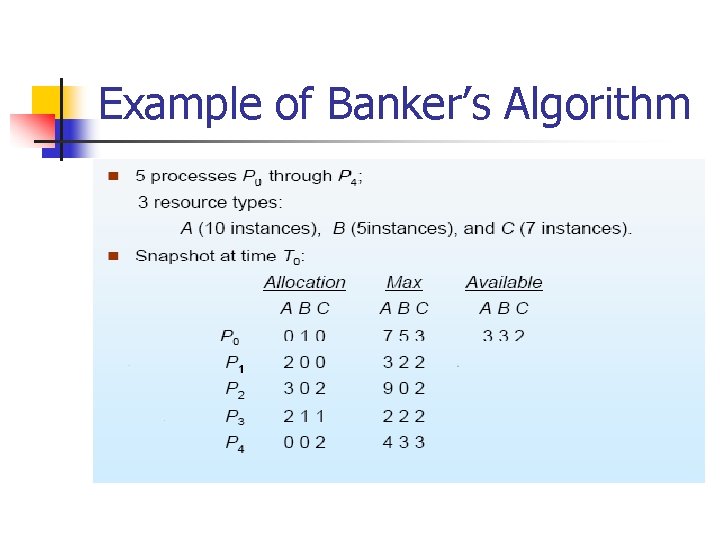
Banker’s Algorithm n n Multiple instances. Each process must a claim maximum use in advance. When a process requests a resource it may have to wait. When a process gets all its resources it must return them in a finite amount of time.

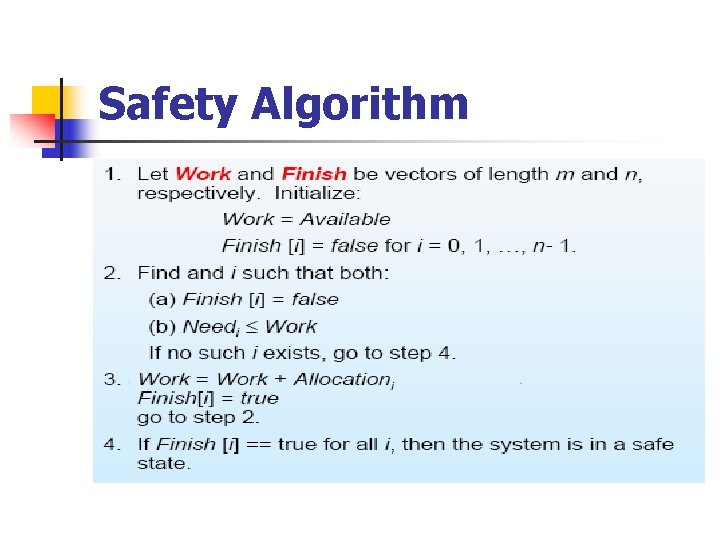
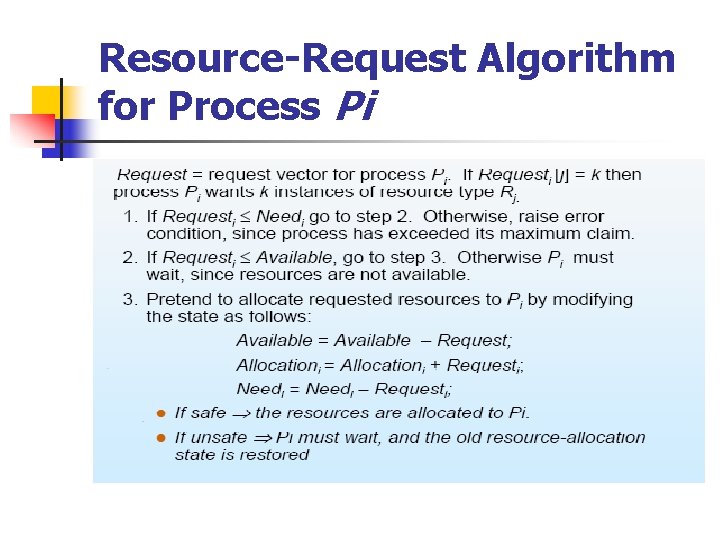
Banker’s Algorithm n Two algorithms need to be discussed: n 1. Safety state check algorithm n 2. Resource request algorithm

Data Structures for the Banker’s Algorithm

Safety Algorithm

Resource-Request Algorithm for Process Pi

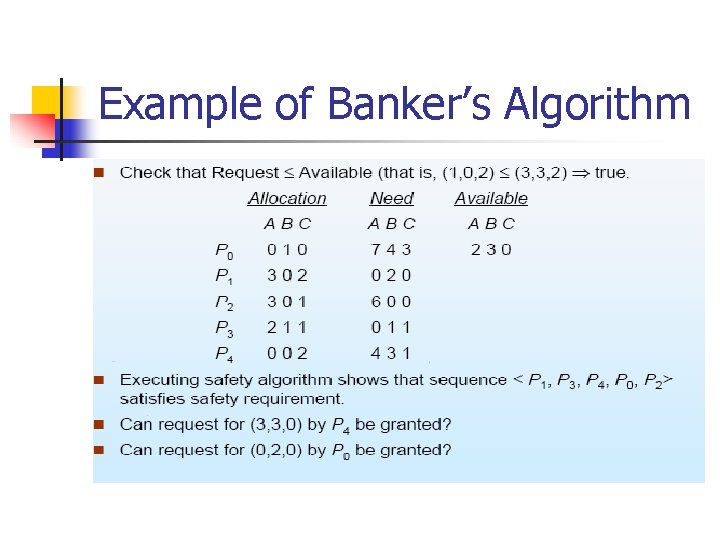
Example of Banker’s Algorithm

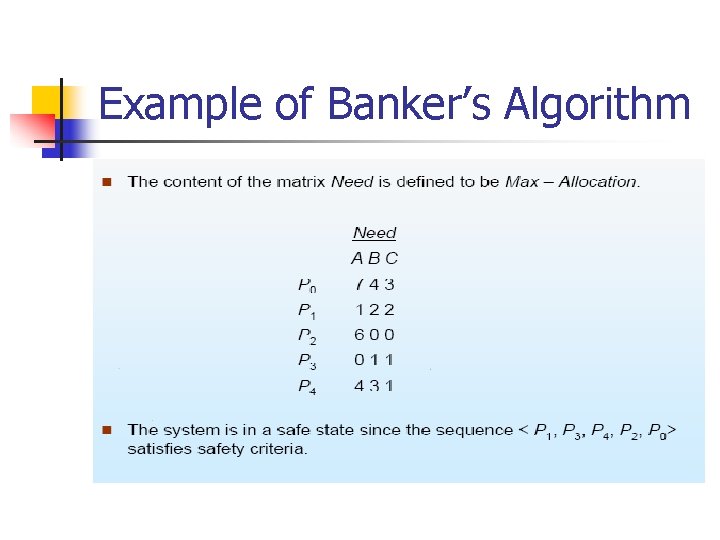
Example of Banker’s Algorithm

Example of Banker’s Algorithm