DDo S Detection and Response System Net WRAP




- Slides: 16

DDo. S Detection and Response System Net. WRAP : Running on KREONET Yoonjoo Kwon yulli@kisti. re. kr High Performance Research Network Dept. Supercomputing Center KISTI High Performance Research Network Dept. / Supercomputing Center 1

Table of contents q Backgrounds q Motivations q Contribution and Results q Summaries and Future Plans High Performance Research Network Dept. / Supercomputing Center 2

Backgrounds q. DDo. S attacks are being appeared continuously § February, 2000 • Yahoo, Amazon § January, 2003 • Korea High Performance Research Network Dept. / Supercomputing Center 3

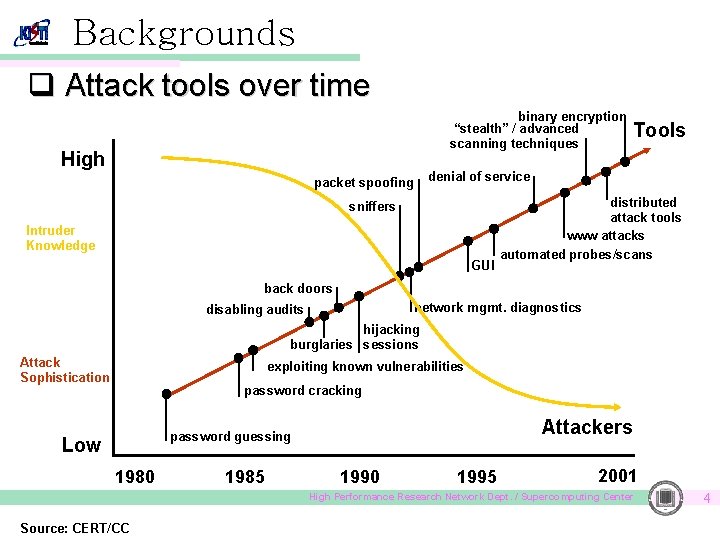
Backgrounds q Attack tools over time binary encryption “stealth” / advanced scanning techniques High Tools denial of service packet spoofing sniffers Intruder Knowledge GUI distributed attack tools www attacks automated probes/scans back doors network mgmt. diagnostics disabling audits hijacking burglaries sessions Attack Sophistication exploiting known vulnerabilities password cracking Attackers password guessing Low 1980 1985 1990 1995 2001 High Performance Research Network Dept. / Supercomputing Center Source: CERT/CC 4

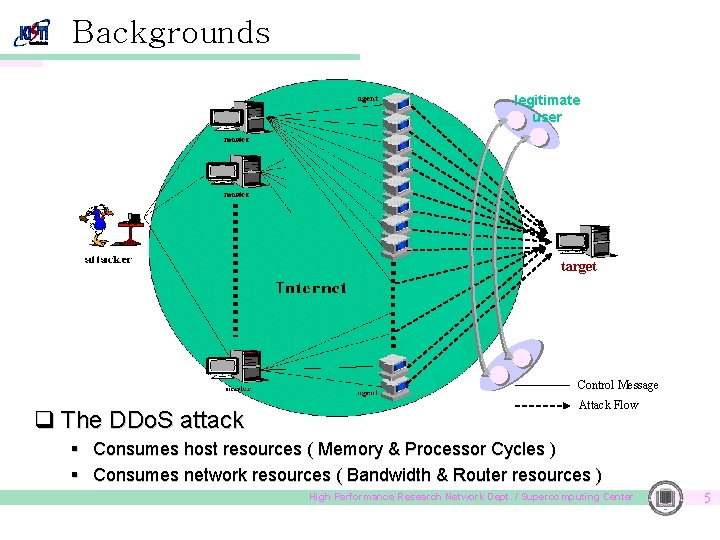
Backgrounds legitimate user target Control Message q The DDo. S attack Attack Flow § Consumes host resources ( Memory & Processor Cycles ) § Consumes network resources ( Bandwidth & Router resources ) High Performance Research Network Dept. / Supercomputing Center 5

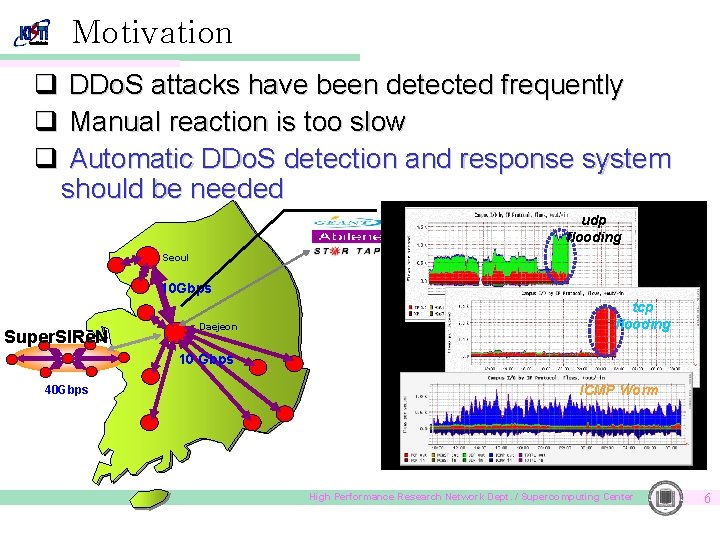
Motivation q DDo. S attacks have been detected frequently q Manual reaction is too slow q Automatic DDo. S detection and response system should be needed udp flooding Seoul 10 Gbps Super. SIRe. N Daejeon tcp flooding 10 Gbps 40 Gbps ICMP Worm High Performance Research Network Dept. / Supercomputing Center 6

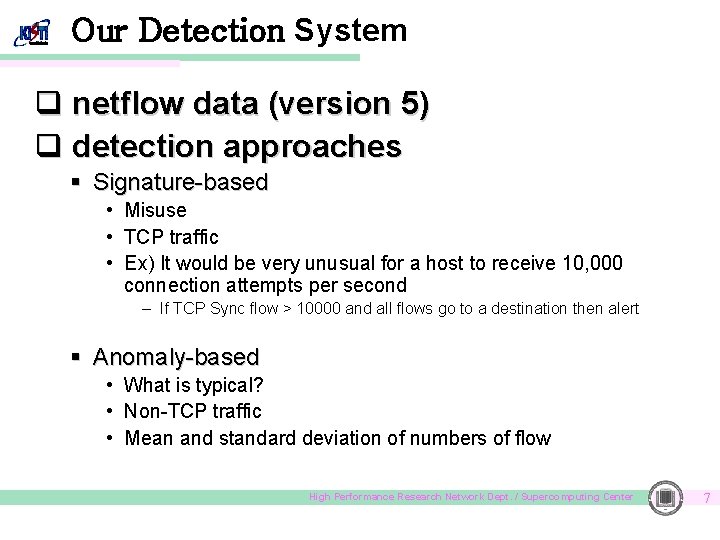
Our Detection System q netflow data (version 5) q detection approaches § Signature-based • Misuse • TCP traffic • Ex) It would be very unusual for a host to receive 10, 000 connection attempts per second – If TCP Sync flow > 10000 and all flows go to a destination then alert § Anomaly-based • What is typical? • Non-TCP traffic • Mean and standard deviation of numbers of flow High Performance Research Network Dept. / Supercomputing Center 7

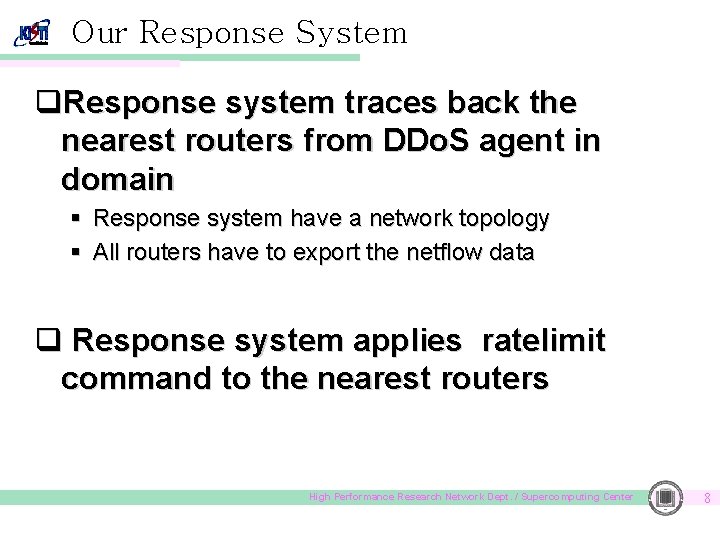
Our Response System q. Response system traces back the nearest routers from DDo. S agent in domain § Response system have a network topology § All routers have to export the netflow data q Response system applies ratelimit command to the nearest routers High Performance Research Network Dept. / Supercomputing Center 8

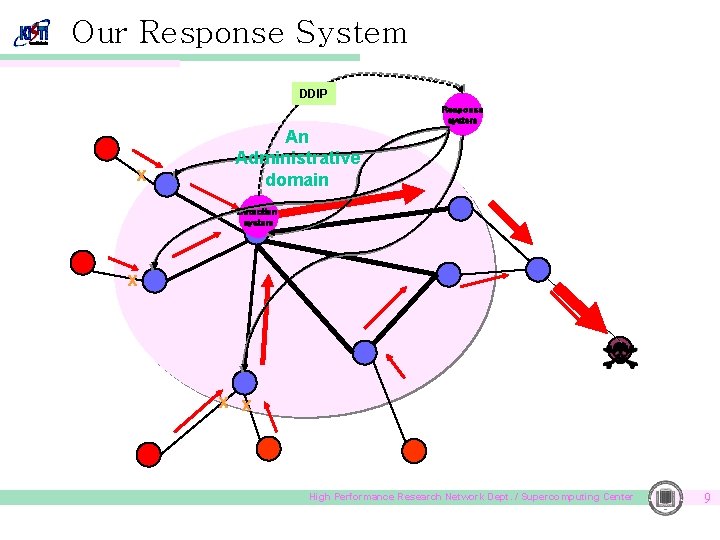
Our Response System DDIP Response system x An Administrative domain Detection system x x x High Performance Research Network Dept. / Supercomputing Center 9

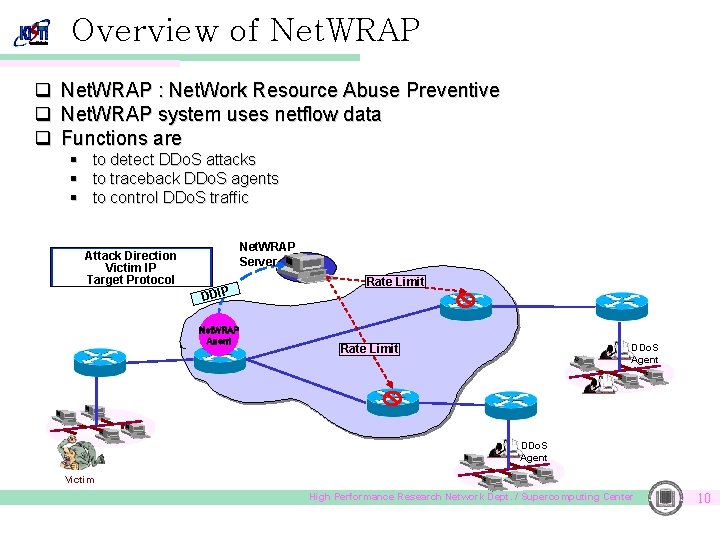
Overview of Net. WRAP q Net. WRAP : Net. Work Resource Abuse Preventive q Net. WRAP system uses netflow data q Functions are § § § to detect DDo. S attacks to traceback DDo. S agents to control DDo. S traffic Attack Direction Victim IP Target Protocol Net. WRAP Server DDIP Net. WRAP Agent Rate Limit DDo. S Agent Victim High Performance Research Network Dept. / Supercomputing Center 10

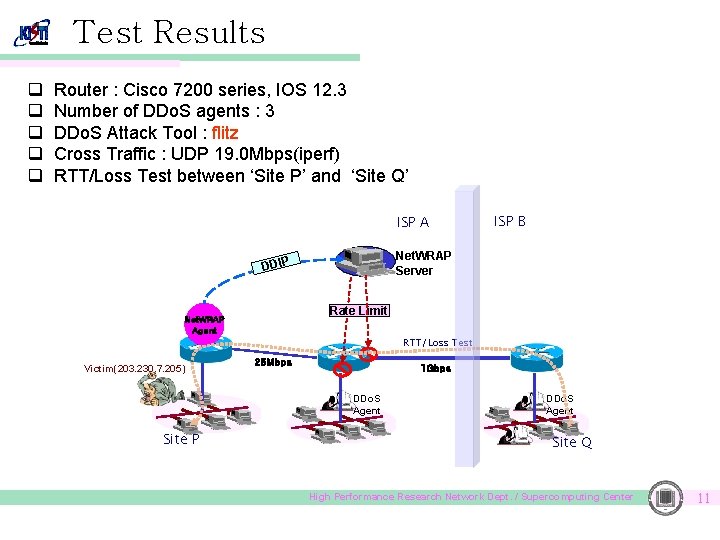
Test Results q q q Router : Cisco 7200 series, IOS 12. 3 Number of DDo. S agents : 3 DDo. S Attack Tool : flitz Cross Traffic : UDP 19. 0 Mbps(iperf) RTT/Loss Test between ‘Site P’ and ‘Site Q’ ISP A ISP B Net. WRAP Server DDIP Rate Limit Net. WRAP Agent RTT/Loss Test Victim(203. 230. 7. 205) 25 Mbps 1 Gbps DDo. S Agent Site P DDo. S Agent Site Q High Performance Research Network Dept. / Supercomputing Center 11

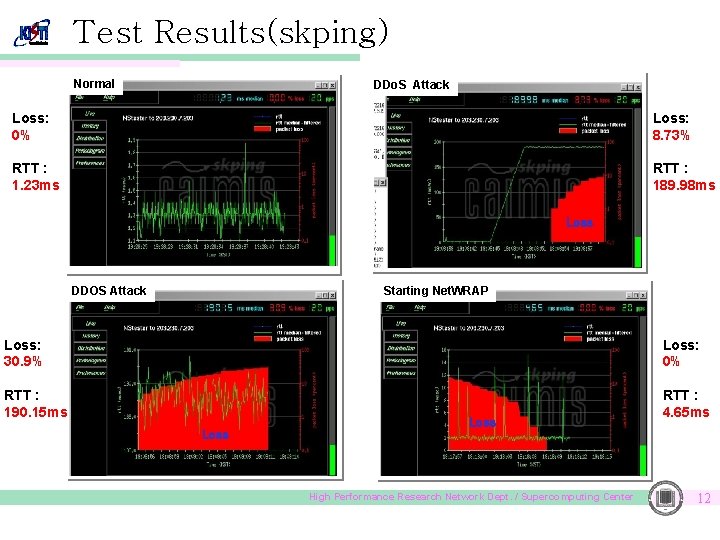
Test Results(skping) Normal DDo. S Attack Loss: 0% Loss: 8. 73% RTT : 1. 23 ms RTT : 189. 98 ms Loss DDOS Attack Starting Net. WRAP Loss: 30. 9% Loss: 0% RTT : 190. 15 ms RTT : 4. 65 ms Loss High Performance Research Network Dept. / Supercomputing Center 12

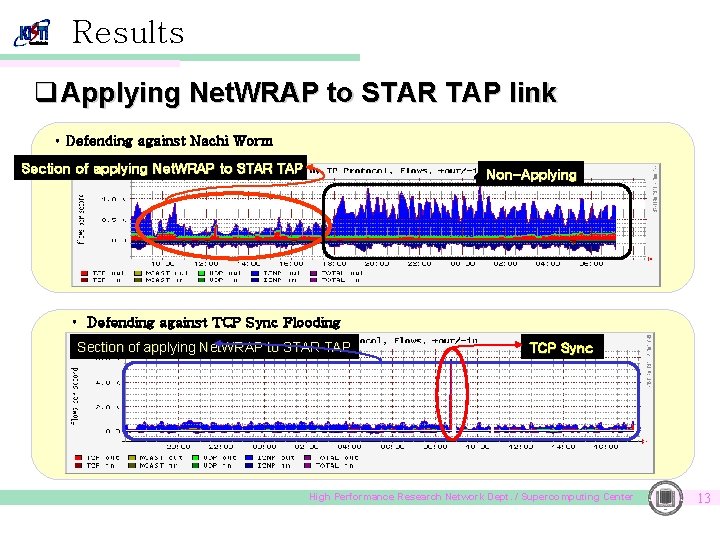
Results q Applying Net. WRAP to STAR TAP link • Defending against Nachi Worm Section of applying Net. WRAP to STAR TAP Non-Applying • Defending against TCP Sync Flooding Section of applying Net. WRAP to STAR TAP TCP Sync High Performance Research Network Dept. / Supercomputing Center 13

Summaries q DDo. S attacks are appeared continuously q We developed Net. WRAP system using netflow data q We got successful test results q We deployed Net. WRAP system to STAR TAP, international link High Performance Research Network Dept. / Supercomputing Center 14

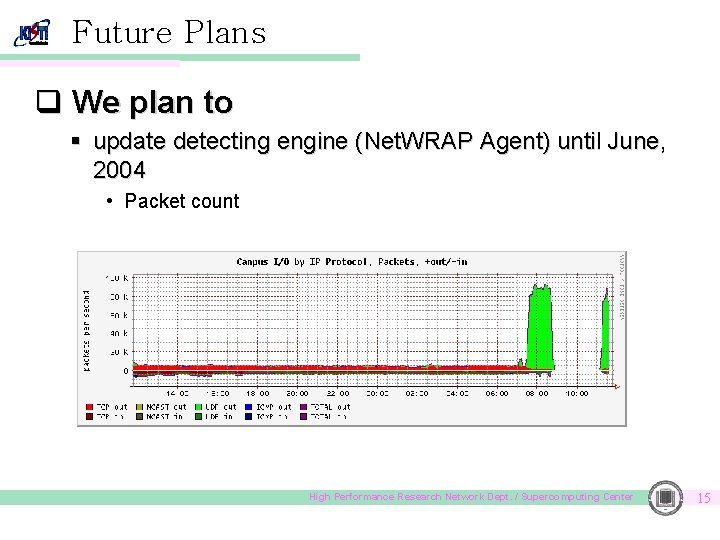
Future Plans q We plan to § update detecting engine (Net. WRAP Agent) until June, 2004 • Packet count High Performance Research Network Dept. / Supercomputing Center 15

Welcome to join us q We would like § to form a shared infrastructure capable of defending network against DDo. S attack • we are going to update our system until June • after June, we want to cooperate with other ISPs • if anyone in NOC members are interested in our system, contact me – yulli@kisti. re. kr High Performance Research Network Dept. / Supercomputing Center 16