Cover Up Privacy Through Forced Participation in Anonymous








- Slides: 20

Cover. Up: Privacy Through “Forced” Participation in Anonymous Communication Networks David Sommer, Aritra Dhar, Luka Malisa Esfandiar Mohammadi, Daniel Ronzani, Srdjan Capkun

Motivations: ACN •

Motivations: Deniability • Intention hiding more than deniability • Accessing classified or leaked documents • Information related to specific medic conditions • Covert Channels & steganography • Covertcast, Free. Wave, SWEET etc. • Only partial solution • Why is it important? • • Freedom of speech Whistleblowers Open journalism User profiling by governmental agencies

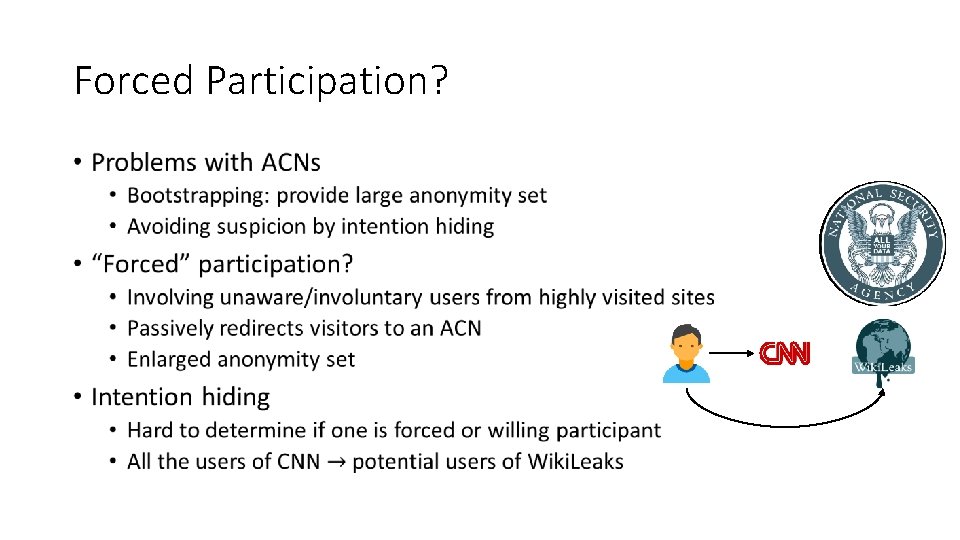
Forced Participation? •

Contributions • Uses “forced participation” • Unidirectional channel to deliver broadcast (Feed) • Bidirectional channel to implement secure chat protocol • Previous Work • Con. Script, Ad. Leaks, New covert channels in HTTP • Working Prototype • Detailed attacker model • Analysis of the attacker’s capabilities • Analysis of privacy leakage and mitigation techniques • Quantitative privacy metric

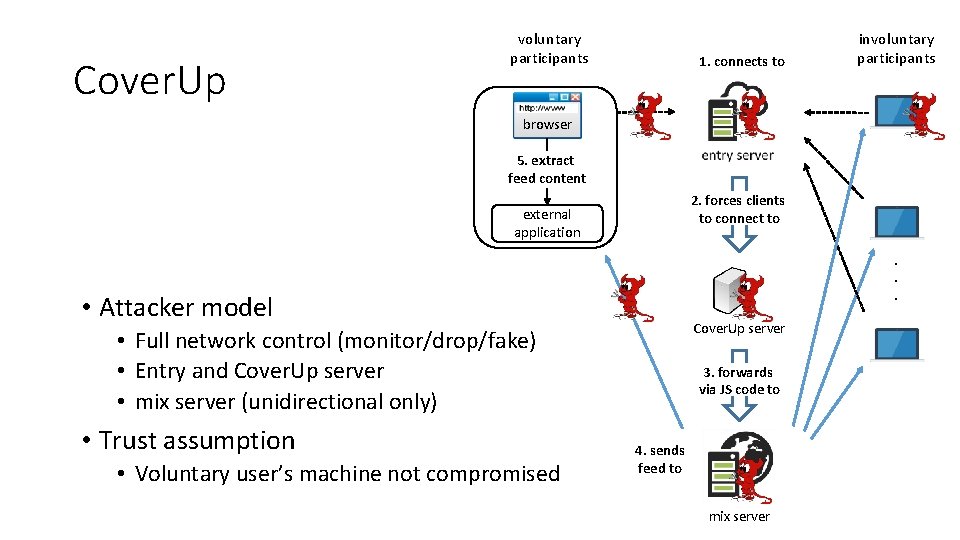
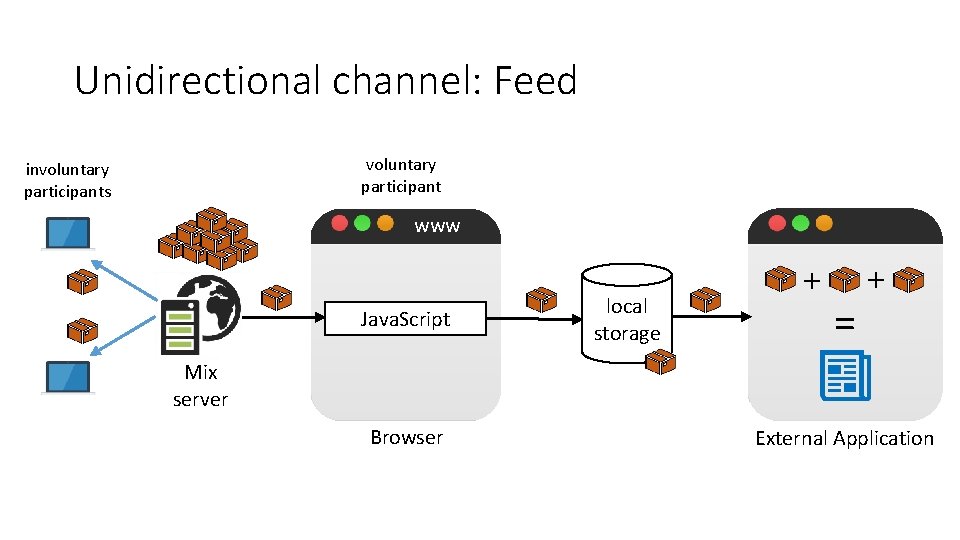
Cover. Up voluntary participants 1. connects to involuntary participants browser 5. extract feed content 2. forces clients to connect to external application . . . • Attacker model Cover. Up server • Full network control (monitor/drop/fake) • Entry and Cover. Up server • mix server (unidirectional only) • Trust assumption • Voluntary user’s machine not compromised 3. forwards via JS code to 4. sends feed to mix server

Unidirectional channel: Feed voluntary participant involuntary participants www Java. Script local storage + = + Mix server Browser External Application

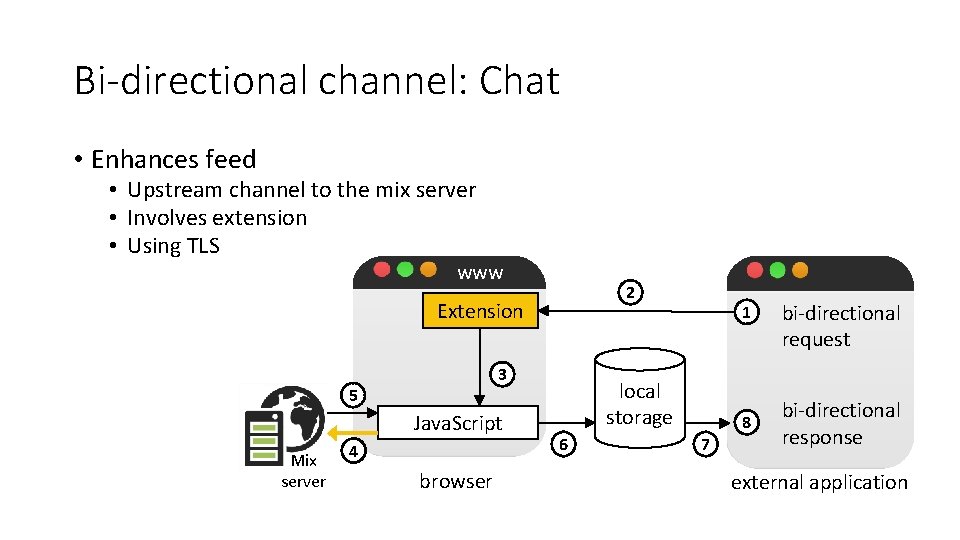
Bi-directional channel: Chat • Enhances feed • Upstream channel to the mix server • Involves extension • Using TLS www 2 Extension 3 5 Java. Script Mix server 4 browser 1 local storage 6 7 8 bi-directional request bi-directional response external application

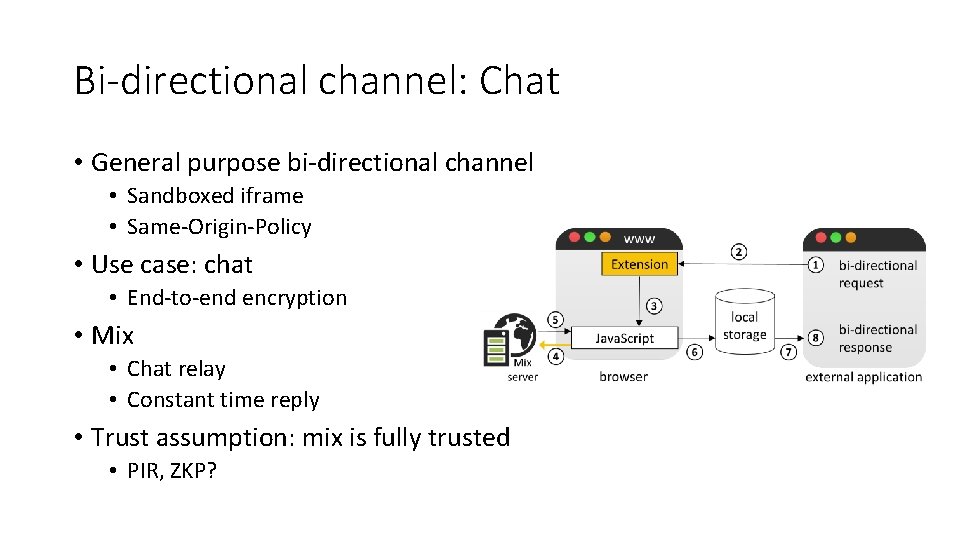
Bi-directional channel: Chat • General purpose bi-directional channel • Sandboxed iframe • Same-Origin-Policy • Use case: chat • End-to-end encryption • Mix • Chat relay • Constant time reply • Trust assumption: mix is fully trusted • PIR, ZKP?

Ethics? Liability? • User get informed about their participation • Option to opt out • User do not get harmed • Computational overhead negligible • Data overhead minimal ( 7. 5 MB / day ) • Advertisement networks / Tracking Services • Ethics committee approval

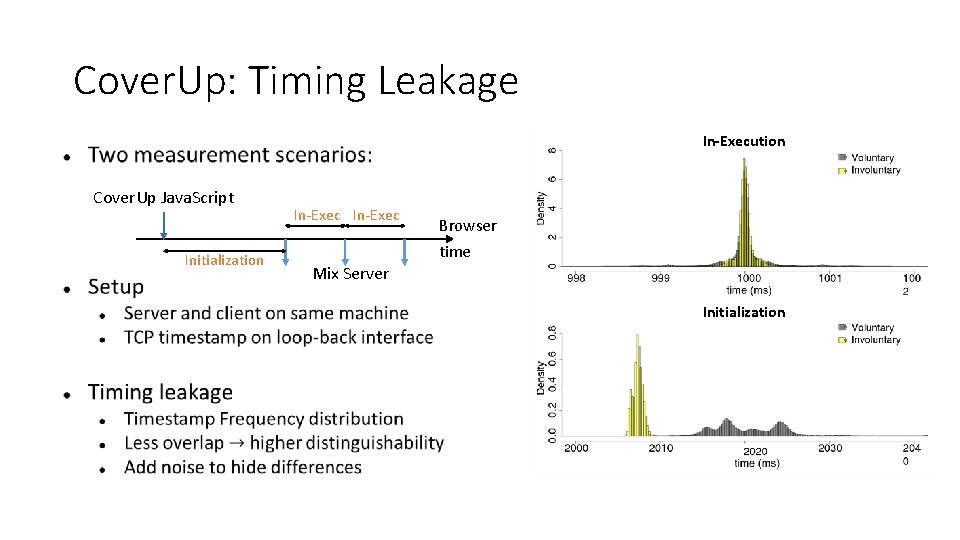
What could go wrong? • Protocol transcripts are indistinguishable • Chat and Feed look identical due to TLS • What else can attacker do? • Analyze user’s entry server visiting pattern • Measure execution time by network timestamps • We assume: • Precise knowledge of execution time distributions for voluntary and involuntary user.

Cover. Up: Timing Leakage In-Execution Cover. Up Java. Script Initialization In-Exec Browser time Mix Server Initialization

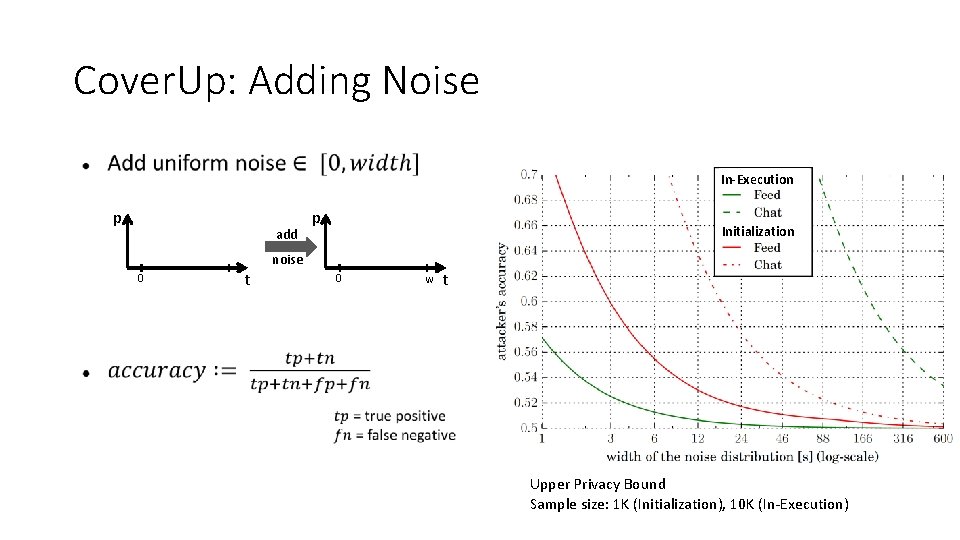
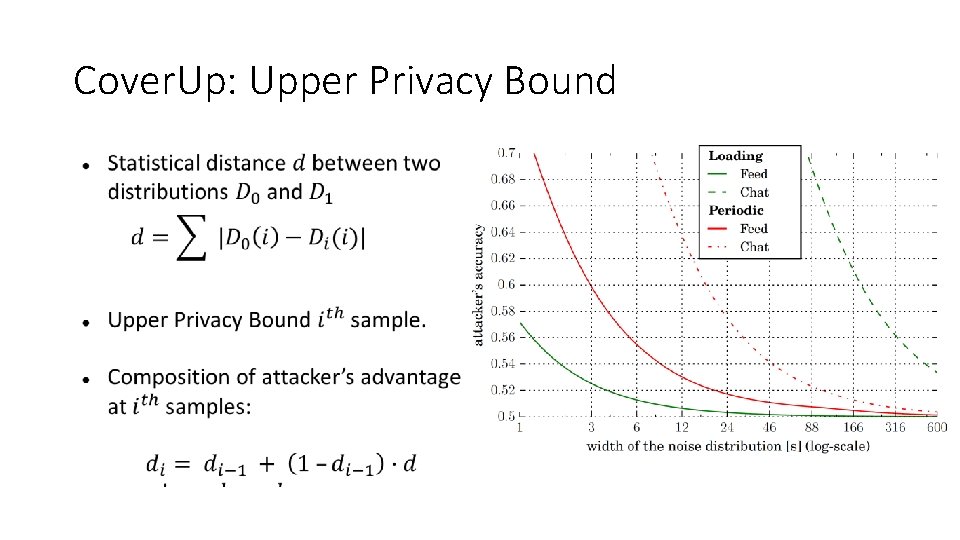
Cover. Up: Adding Noise In-Execution p add 0 t p Initialization noise 0 w t Upper Privacy Bound Sample size: 1 K (Initialization), 10 K (In-Execution)

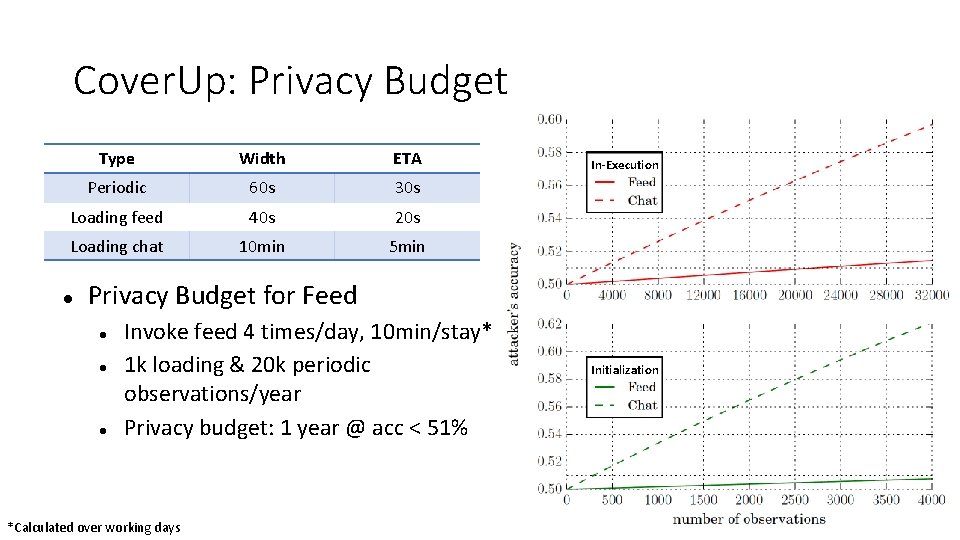
Cover. Up: Privacy Budget Type Width ETA Periodic 60 s 30 s Loading feed 40 s 20 s Loading chat 10 min 5 min In-Execution Privacy Budget for Feed Invoke feed 4 times/day, 10 min/stay* 1 k loading & 20 k periodic observations/year Privacy budget: 1 year @ acc < 51% *Calculated over working days Initialization

Cover. Up: Implementation • External application • Implemented in Java • Features: feed, chat and interactive browsing • Uses crypto APIs from whisper systems and JCA • Browser extension • Firefox extension based on Web. Extension API • Mix and Cover. Up server • Implemented using Java EE Servlet API • Hosted on Apache Tomcat webserver

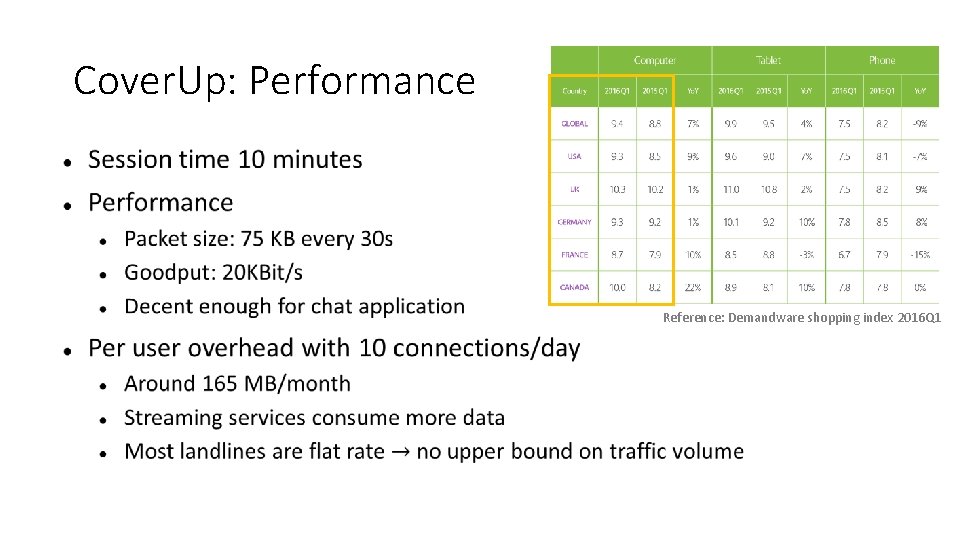
Cover. Up: Performance Reference: Demandware shopping index 2016 Q 1

Conclusions

Thank you

Cover. Up: Upper Privacy Bound

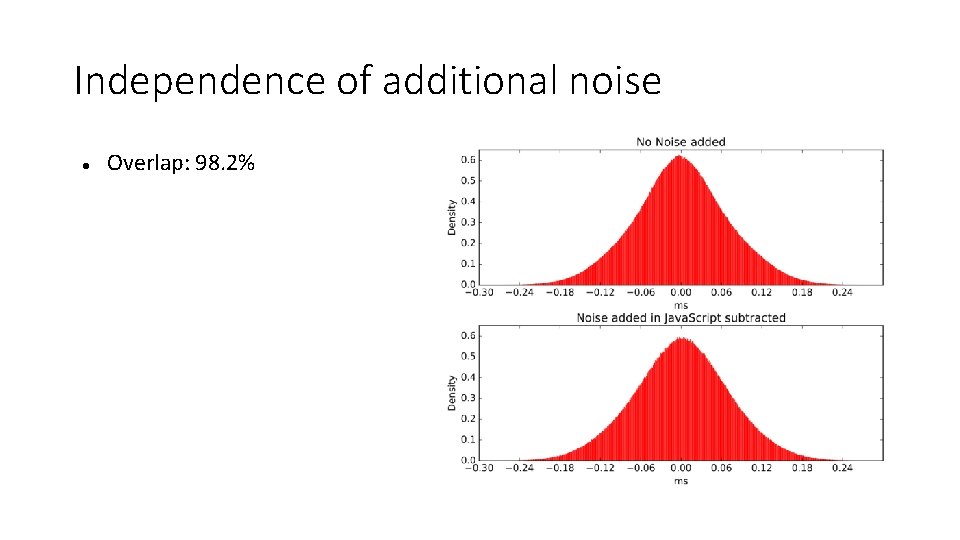
Independence of additional noise Overlap: 98. 2%
 Forced participation
Forced participation Mapping cardinality
Mapping cardinality Cvs privacy awareness and hipaa privacy training
Cvs privacy awareness and hipaa privacy training Cooperative evaluation in hci
Cooperative evaluation in hci Participation through language
Participation through language Cover uncover test vs alternating cover test
Cover uncover test vs alternating cover test Worth 4 dot test
Worth 4 dot test Cover uncover test vs alternating cover test
Cover uncover test vs alternating cover test Alcoholics anonymous warranties
Alcoholics anonymous warranties Anonymous adjective
Anonymous adjective Narcotics anonymous
Narcotics anonymous Anonymous outline
Anonymous outline Narcotics anonymous albuquerque
Narcotics anonymous albuquerque Anonymous vocabulary
Anonymous vocabulary Remote side-channel attacks on anonymous transactions
Remote side-channel attacks on anonymous transactions Zerocash decentralized anonymous payments from bitcoin
Zerocash decentralized anonymous payments from bitcoin C anonymous class
C anonymous class Hopi poem by anonymous
Hopi poem by anonymous Cs1951l brown
Cs1951l brown Remember remember the 3rd of november
Remember remember the 3rd of november Antonym anonymous
Antonym anonymous