Corresponding Auto Names for IPv 6 Addresses draftkitamuraipv







- Slides: 29

Corresponding Auto Names for IPv 6 Addresses <draft-kitamura-ipv 6 -auto-name-00. txt> Hiroshi KITAMURA NEC Corporation kitamura@da. jp. nec. com 1

Index • Introduction • Goals: What can be achieved – – – Assumed typical IPv 6 communication environment Auto Names examples Auto Name Prefix for Grouped Addresses Contribution in Regular Resolving (Name -> Address) Contribution in Reverse Resolving (Address -> Name) • Deployed Notions and Functions – Stateless Name – Scoped Name – Target IPv 6 Addresses • Design of Auto Names – Conceptual Design on Naming Rules – Address Appearance Detection and Auto Name Registration • Discussions 2

Introduction IPv 6 address is too long and complicated to remember for human. It is very nuisance or almost impossible to ‘type’ a literal IPv 6 address manually. Also, literal IPv 6 address information can be called meaningless. Because it is very difficult for human to tell which IPv 6 address is set to which actual IPv 6 node at a glance. Strong desires: • Use gentle information “Name” Name instead of literal IPv 6 Address. • Change information from almost meaningless to meaningful An idea “Corresponding Auto Names” is introduced to solve above problems and to satisfy the above desires. 3

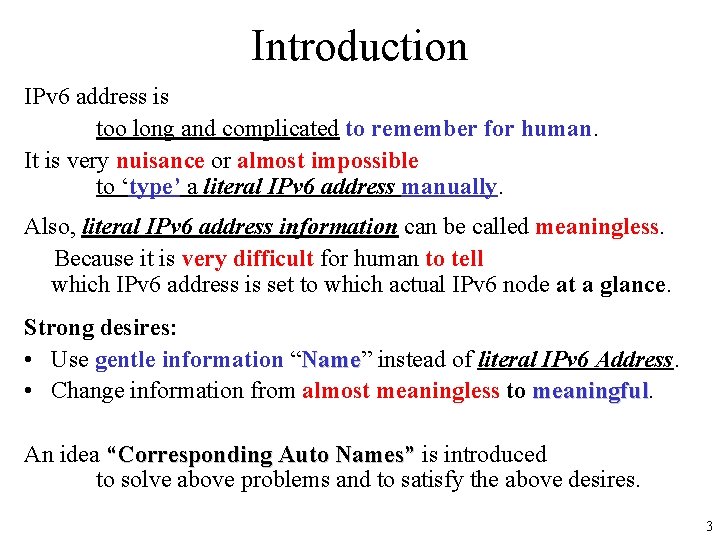
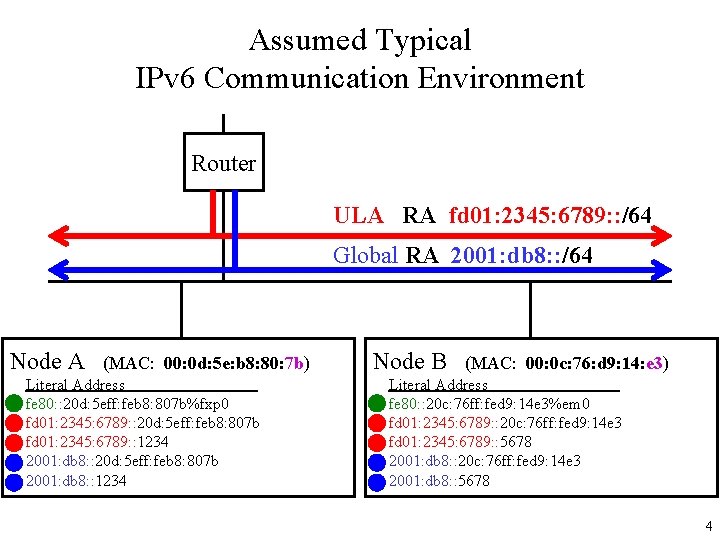
Assumed Typical IPv 6 Communication Environment Router ULA RA fd 01: 2345: 6789: : /64 Global RA 2001: db 8: : /64 Node A (MAC: 00: 0 d: 5 e: b 8: 80: 7 b) Literal Address fe 80: : 20 d: 5 eff: feb 8: 807 b%fxp 0 fd 01: 2345: 6789: : 20 d: 5 eff: feb 8: 807 b fd 01: 2345: 6789: : 1234 2001: db 8: : 20 d: 5 eff: feb 8: 807 b 2001: db 8: : 1234 Node B (MAC: 00: 0 c: 76: d 9: 14: e 3) Literal Address fe 80: : 20 c: 76 ff: fed 9: 14 e 3%em 0 fd 01: 2345: 6789: : 20 c: 76 ff: fed 9: 14 e 3 fd 01: 2345: 6789: : 5678 2001: db 8: : 20 c: 76 ff: fed 9: 14 e 3 2001: db 8: : 5678 4

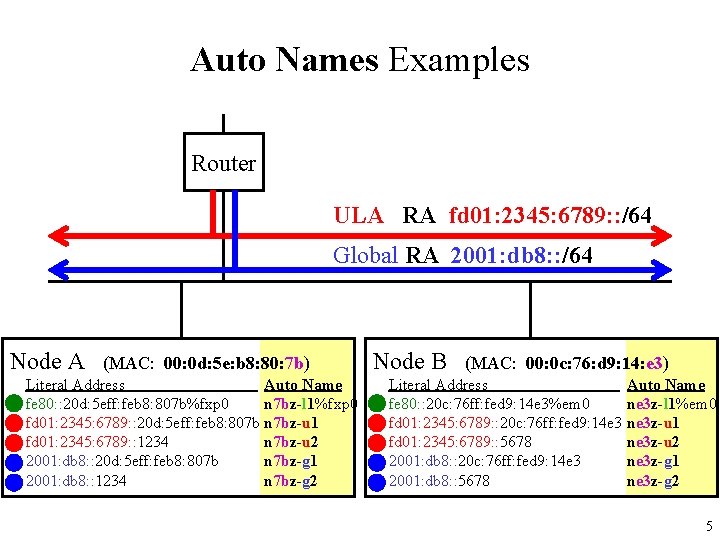
Auto Names Examples Router ULA RA fd 01: 2345: 6789: : /64 Global RA 2001: db 8: : /64 Node A (MAC: 00: 0 d: 5 e: b 8: 80: 7 b) Literal Address Auto Name fe 80: : 20 d: 5 eff: feb 8: 807 b%fxp 0 n 7 bz-l 1%fxp 0 fd 01: 2345: 6789: : 20 d: 5 eff: feb 8: 807 b n 7 bz-u 1 fd 01: 2345: 6789: : 1234 n 7 bz-u 2 2001: db 8: : 20 d: 5 eff: feb 8: 807 b n 7 bz-g 1 2001: db 8: : 1234 n 7 bz-g 2 Node B (MAC: 00: 0 c: 76: d 9: 14: e 3) Literal Address Auto Name fe 80: : 20 c: 76 ff: fed 9: 14 e 3%em 0 ne 3 z-l 1%em 0 fd 01: 2345: 6789: : 20 c: 76 ff: fed 9: 14 e 3 ne 3 z-u 1 fd 01: 2345: 6789: : 5678 ne 3 z-u 2 2001: db 8: : 20 c: 76 ff: fed 9: 14 e 3 ne 3 z-g 1 2001: db 8: : 5678 ne 3 z-g 2 5

Auto Name Prefix for Grouped Addresses In order to make Auto Names meaningful, – IPv 6 addresses are grouped. – Auto Name Prefix is used to show grouped addresses. For IPv 6 addresses that are set to the same interface (node), the same Auto Name Prefix is used for their Auto Names. As shown above example: • ‘n 7 bz-’ is used for Auto Name Prefix for Node A (00: 0 d: 5 e: b 8: 80: 7 b) • ‘ne 3 z-’ is used for Auto Name Prefix for Node B (00: 0 c: 76: d 9: 14: e 3) Naming rule of Auto Name Prefixes is based on inheriting the last octet of the node's MAC address. 6

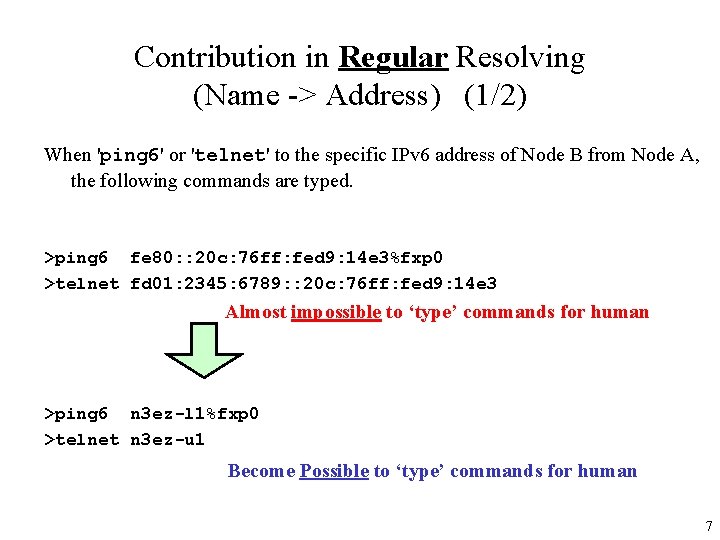
Contribution in Regular Resolving (Name -> Address) (1/2) When 'ping 6' or 'telnet' to the specific IPv 6 address of Node B from Node A, the following commands are typed. >ping 6 fe 80: : 20 c: 76 ff: fed 9: 14 e 3%fxp 0 >telnet fd 01: 2345: 6789: : 20 c: 76 ff: fed 9: 14 e 3 Almost impossible to ‘type’ commands for human >ping 6 n 3 ez-l 1%fxp 0 >telnet n 3 ez-u 1 Become Possible to ‘type’ commands for human 7

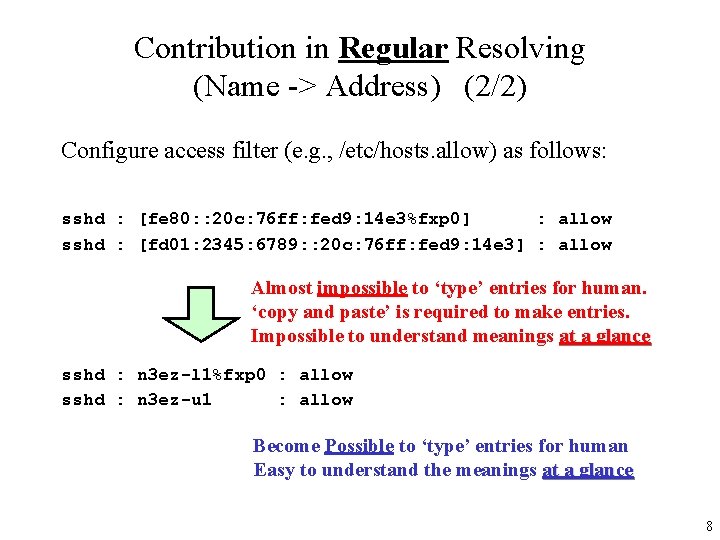
Contribution in Regular Resolving (Name -> Address) (2/2) Configure access filter (e. g. , /etc/hosts. allow) as follows: sshd : [fe 80: : 20 c: 76 ff: fed 9: 14 e 3%fxp 0] : allow sshd : [fd 01: 2345: 6789: : 20 c: 76 ff: fed 9: 14 e 3] : allow Almost impossible to ‘type’ entries for human. ‘copy and paste’ is required to make entries. Impossible to understand meanings at a glance sshd : n 3 ez-l 1%fxp 0 : allow sshd : n 3 ez-u 1 : allow Become Possible to ‘type’ entries for human Easy to understand the meanings at a glance 8

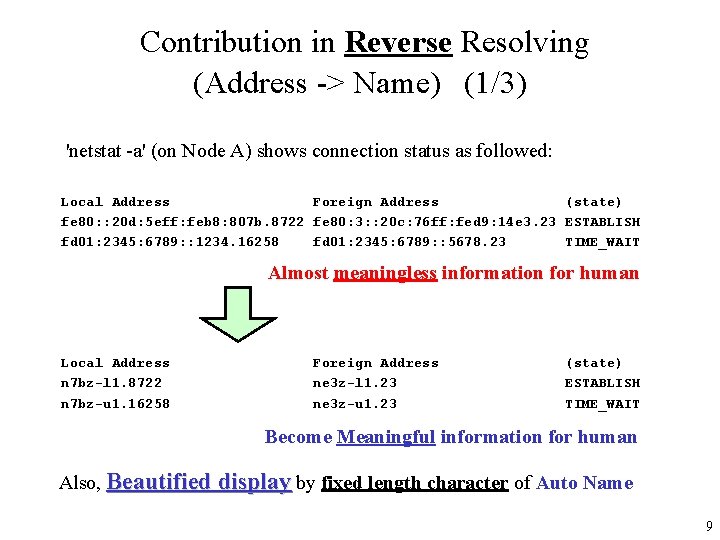
Contribution in Reverse Resolving (Address -> Name) (1/3) 'netstat -a' (on Node A) shows connection status as followed: Local Address Foreign Address (state) fe 80: : 20 d: 5 eff: feb 8: 807 b. 8722 fe 80: 3: : 20 c: 76 ff: fed 9: 14 e 3. 23 ESTABLISH fd 01: 2345: 6789: : 1234. 16258 fd 01: 2345: 6789: : 5678. 23 TIME_WAIT Almost meaningless information for human Local Address n 7 bz-l 1. 8722 n 7 bz-u 1. 16258 Foreign Address ne 3 z-l 1. 23 ne 3 z-u 1. 23 (state) ESTABLISH TIME_WAIT Become Meaningful information for human Also, Beautified display by fixed length character of Auto Name 9

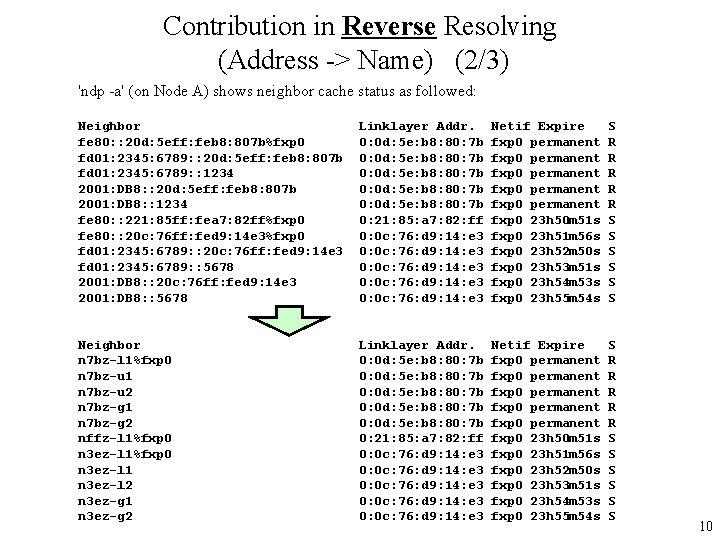
Contribution in Reverse Resolving (Address -> Name) (2/3) 'ndp -a' (on Node A) shows neighbor cache status as followed: Neighbor fe 80: : 20 d: 5 eff: feb 8: 807 b%fxp 0 fd 01: 2345: 6789: : 20 d: 5 eff: feb 8: 807 b fd 01: 2345: 6789: : 1234 2001: DB 8: : 20 d: 5 eff: feb 8: 807 b 2001: DB 8: : 1234 fe 80: : 221: 85 ff: fea 7: 82 ff%fxp 0 fe 80: : 20 c: 76 ff: fed 9: 14 e 3%fxp 0 fd 01: 2345: 6789: : 20 c: 76 ff: fed 9: 14 e 3 fd 01: 2345: 6789: : 5678 2001: DB 8: : 20 c: 76 ff: fed 9: 14 e 3 2001: DB 8: : 5678 Linklayer Addr. 0: 0 d: 5 e: b 8: 80: 7 b 0: 0 d: 5 e: b 8: 80: 7 b 0: 21: 85: a 7: 82: ff 0: 0 c: 76: d 9: 14: e 3 0: 0 c: 76: d 9: 14: e 3 Netif Expire fxp 0 permanent fxp 0 permanent fxp 0 23 h 50 m 51 s fxp 0 23 h 51 m 56 s fxp 0 23 h 52 m 50 s fxp 0 23 h 53 m 51 s fxp 0 23 h 54 m 53 s fxp 0 23 h 55 m 54 s S R R R S S S Neighbor n 7 bz-l 1%fxp 0 n 7 bz-u 1 n 7 bz-u 2 n 7 bz-g 1 n 7 bz-g 2 nffz-l 1%fxp 0 n 3 ez-l 1 n 3 ez-l 2 n 3 ez-g 1 n 3 ez-g 2 Linklayer Addr. 0: 0 d: 5 e: b 8: 80: 7 b 0: 0 d: 5 e: b 8: 80: 7 b 0: 21: 85: a 7: 82: ff 0: 0 c: 76: d 9: 14: e 3 0: 0 c: 76: d 9: 14: e 3 Netif Expire fxp 0 permanent fxp 0 permanent fxp 0 23 h 50 m 51 s fxp 0 23 h 51 m 56 s fxp 0 23 h 52 m 50 s fxp 0 23 h 53 m 51 s fxp 0 23 h 54 m 53 s fxp 0 23 h 55 m 54 s S R R R S S S 10

Contribution in Reverse Resolving (Address -> Name) (3/3) Other examples where the Auto Names can contributes: • In access log files of a server application: Accessed clients are can be recoded as meaningful Auto Names instead of (almost meaningless) literal IPv 6 address. • In packet dumping applications: Address information can be shown as meaningful Auto Names The Auto Name technique can significantly help for human to analyze and understand above information. Auto Name format is simple and easy enough for human to understand. By using the Auto Names technique, troublesome IPv 6 literal Address info. can be converted into meaningful info. and we can achieve our goals. 11

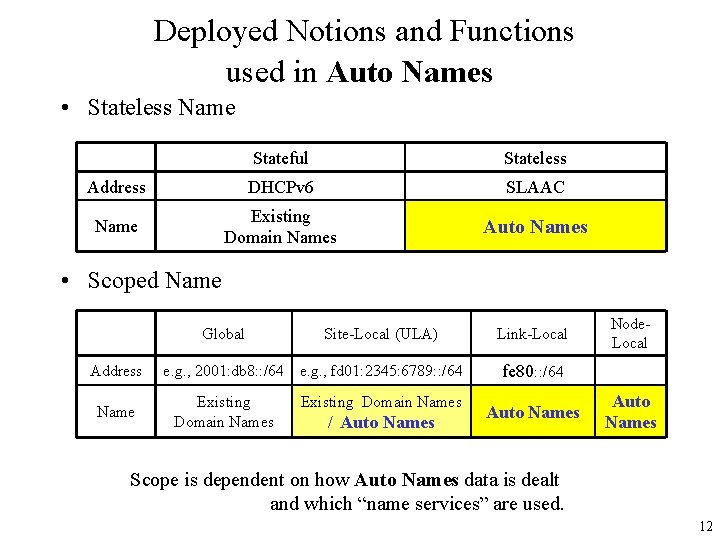
Deployed Notions and Functions used in Auto Names • Stateless Name Stateful Stateless Address DHCPv 6 SLAAC Name Existing Domain Names Auto Names • Scoped Name Global Address Name Site-Local (ULA) e. g. , 2001: db 8: : /64 e. g. , fd 01: 2345: 6789: : /64 Existing Domain Names / Auto Names Link-Local Node. Local fe 80: : /64 Auto Names Scope is dependent on how Auto Names data is dealt and which “name services” are used. 12

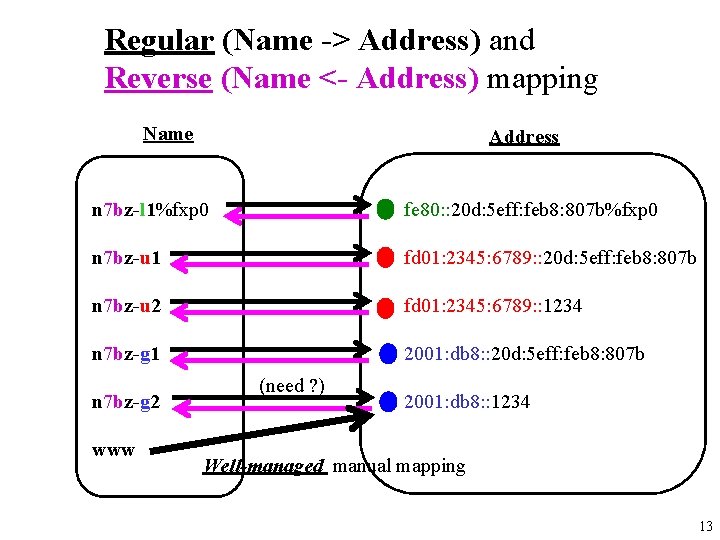
Regular (Name -> Address) and Reverse (Name <- Address) mapping Name Address n 7 bz-l 1%fxp 0 fe 80: : 20 d: 5 eff: feb 8: 807 b%fxp 0 n 7 bz-u 1 fd 01: 2345: 6789: : 20 d: 5 eff: feb 8: 807 b n 7 bz-u 2 fd 01: 2345: 6789: : 1234 n 7 bz-g 1 2001: db 8: : 20 d: 5 eff: feb 8: 807 b n 7 bz-g 2 www (need ? ) 2001: db 8: : 1234 Well-managed manual mapping 13

Target IPv 6 Addresses of Auto Names • Target of Auto Names: All unicast IPv 6 addresses (include link-local scoped addresses) are target • Exception (non-target): “Well-managed” IPv 6 addresses are basically non-target Definition of “Well-managed” addresses: Their “Domain Names” are manually (or statefully) registered into name services (such as the DNS) already. Reverse mapping entries are needed for All addresses. Regular mapping entries will not be needed for “Well-managed” addresses. (Even if Regular mapping entries exist, they will not cause problems. ) 14

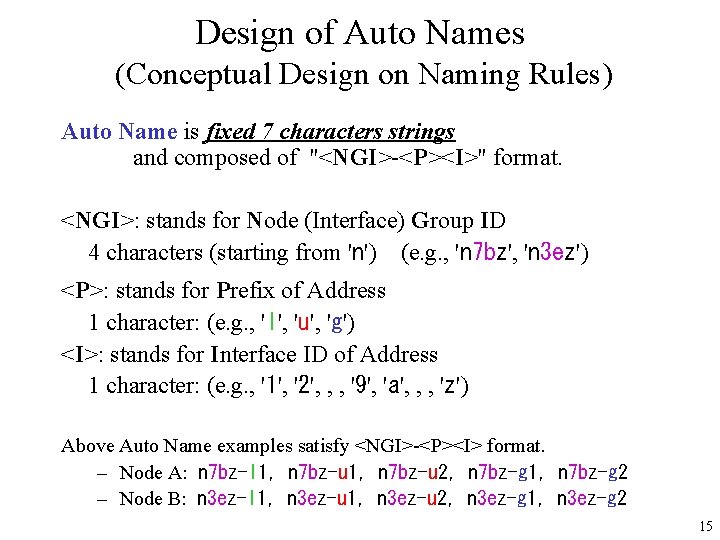
Design of Auto Names (Conceptual Design on Naming Rules) Auto Name is fixed 7 characters strings and composed of "<NGI>-<P><I>" format. <NGI>: stands for Node (Interface) Group ID 4 characters (starting from 'n') (e. g. , 'n 7 bz', 'n 3 ez') <P>: stands for Prefix of Address 1 character: (e. g. , 'l', 'u', 'g') <I>: stands for Interface ID of Address 1 character: (e. g. , '1', '2', , , '9', 'a', , , 'z') Above Auto Name examples satisfy <NGI>-<P><I> format. – Node A: n 7 bz-l 1, n 7 bz-u 2, n 7 bz-g 1, n 7 bz-g 2 – Node B: n 3 ez-l 1, n 3 ez-u 2, n 3 ez-g 1, n 3 ez-g 2 15

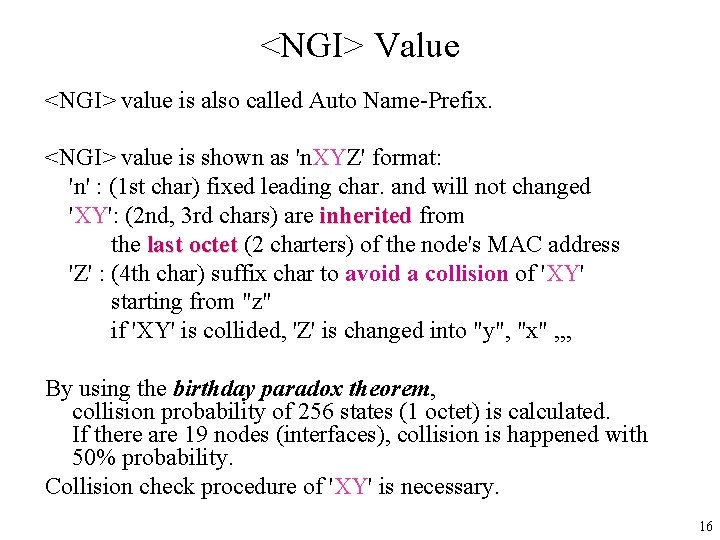
<NGI> Value <NGI> value is also called Auto Name-Prefix. <NGI> value is shown as 'n. XYZ' format: 'n' : (1 st char) fixed leading char. and will not changed 'XY': (2 nd, 3 rd chars) are inherited from the last octet (2 charters) of the node's MAC address 'Z' : (4 th char) suffix char to avoid a collision of 'XY' starting from "z" if 'XY' is collided, 'Z' is changed into "y", "x" , , , By using the birthday paradox theorem, collision probability of 256 states (1 octet) is calculated. If there are 19 nodes (interfaces), collision is happened with 50% probability. Collision check procedure of 'XY' is necessary. 16

<P> Value <P> value stands for Prefix (Scope) of Address as 1 character format. Auto Names of IPv 6 addresses whose prefixes are same use the same <P> value. Typically, following characters are used: "l": used for Link-local scoped addresses. "u": used for ULA "g": used for Global scoped address If multiple prefixes for the same scope are used, other character (such as "h", "i", , , ) can be used depending on the circumstances. 17

<I> Value <I> value stands for Interface ID of Address as 1 character format. <I> value is starting from "1". If multiple IPv 6 addresses whose <NGI> and <P> values are same are found, other <I> value (such as '2', '3', , , '9', 'a', , , 'z') is used. (9(digit)+26(alphabet)=35 states can be taken) 18

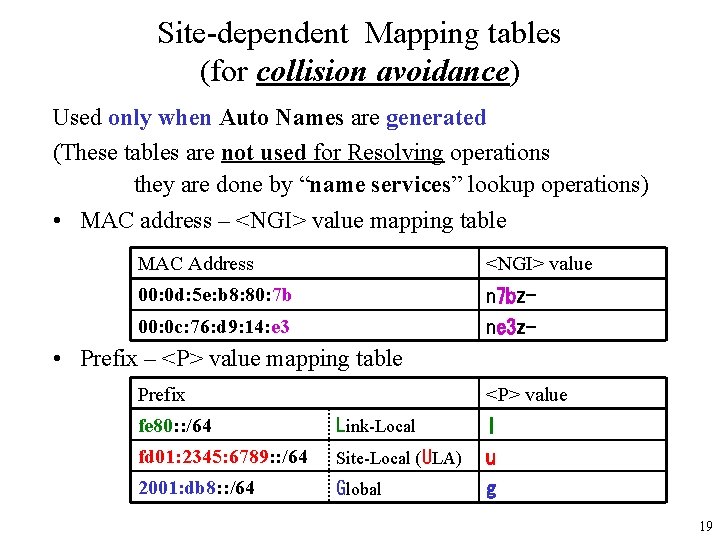
Site-dependent Mapping tables (for collision avoidance) Used only when Auto Names are generated (These tables are not used for Resolving operations they are done by “name services” lookup operations) • MAC address – <NGI> value mapping table MAC Address <NGI> value 00: 0 d: 5 e: b 8: 80: 7 b n 7 bz- 00: 0 c: 76: d 9: 14: e 3 ne 3 z- • Prefix – <P> value mapping table Prefix <P> value fe 80: : /64 Link-Local l fd 01: 2345: 6789: : /64 Site-Local (ULA) u 2001: db 8: : /64 Global g 19

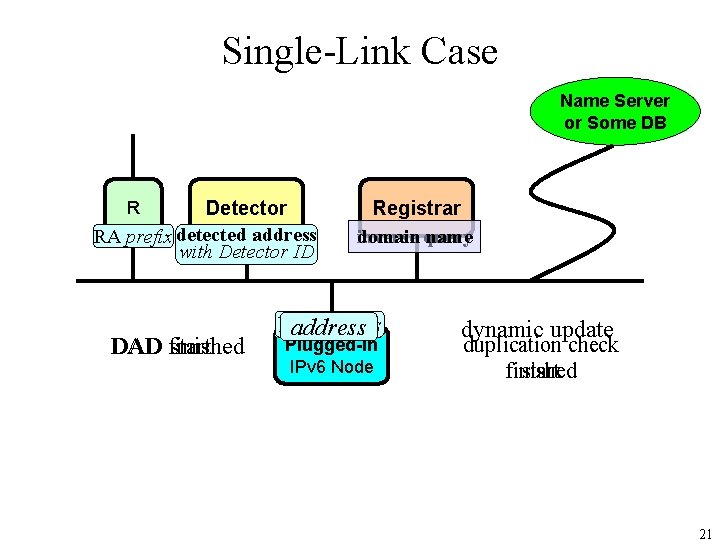
IPv 6 Address Appearance Detection mechanism In order to detect newly appeared IPv 6 address, DAD message (NS for DAD) is effectively used. DAD message has the following good capabilities: • issued only when node would like to set new IPv 6 address • issued for All types (link-local, global, temporary, , , ) • L 2 broadcast and easy to capture (without using mirror port) • distinguishable from other NS messages, because source address of the message is unspecified (": : ") and different from others • Captured DAD message includes all necessary information (such as, IPv 6 address and MAC address) Detector captures DAD messages and detects newly appeared IPv 6 addresses. Detected information is sent to Registrar. 20

Single-Link Case Name Server or Some DB Detector RA prefix detected address with Detector ID R DAD finished start Registrar domain inverse query name NS address Plugged-in IPv 6 Node dynamic update duplication check finished start 21

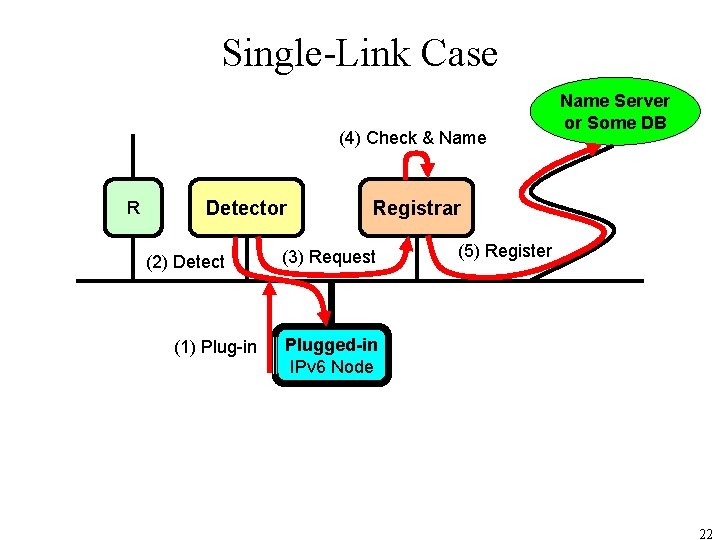
Single-Link Case (4) Check & Name R Detector (2) Detect (1) Plug-in Name Server or Some DB Registrar (3) Request (5) Register Plugged-in IPv 6 Node 22

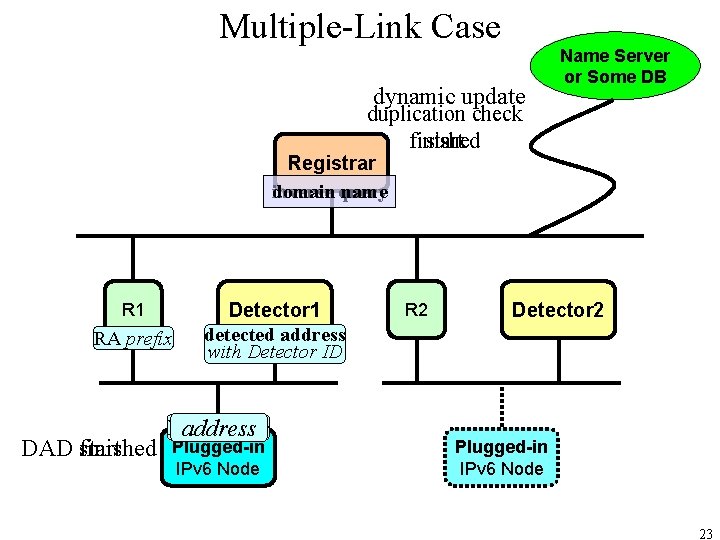
Multiple-Link Case dynamic update Name Server or Some DB duplication check finished start Registrar domain inverse query name R 1 RA prefix DAD start finished Detector 1 detected address with Detector ID NS address Plugged-in IPv 6 Node R 2 Detector 2 Plugged-in IPv 6 Node 23

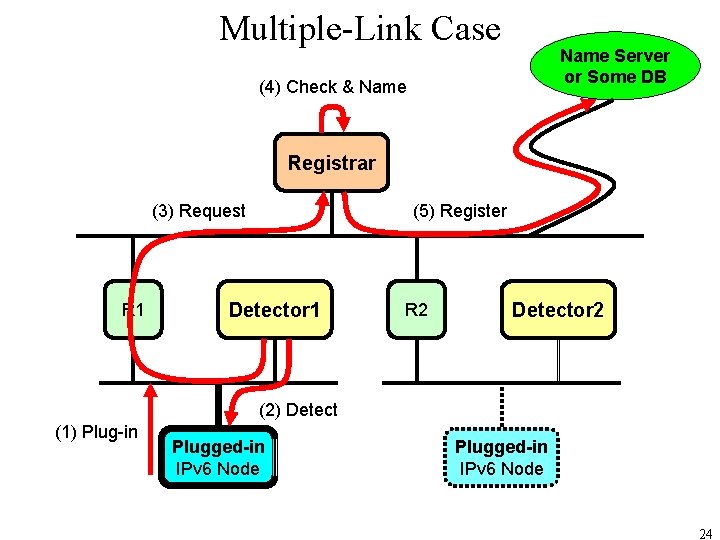
Multiple-Link Case Name Server or Some DB (4) Check & Name Registrar (3) Request R 1 (5) Register Detector 1 R 2 Detector 2 (2) Detect (1) Plug-in Plugged-in IPv 6 Node 24

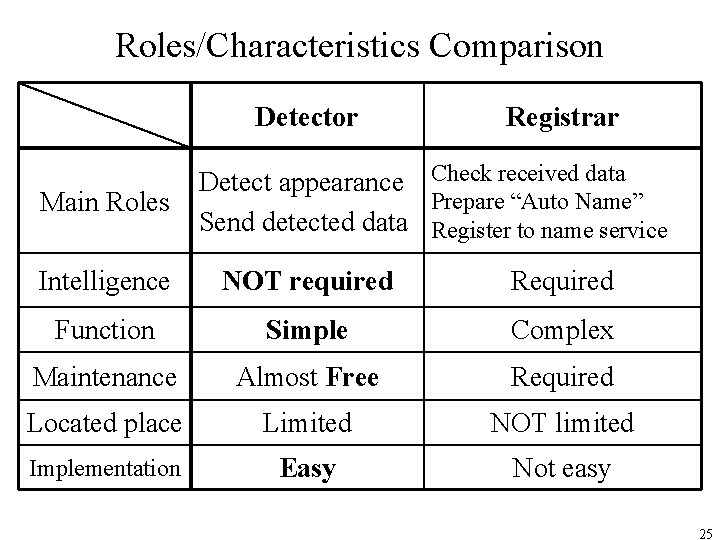
Roles/Characteristics Comparison Detector Main Roles Registrar Detect appearance Check received data Prepare “Auto Name” Send detected data Register to name service Intelligence NOT required Required Function Simple Complex Maintenance Almost Free Required Located place Limited NOT limited Implementation Easy Not easy 25

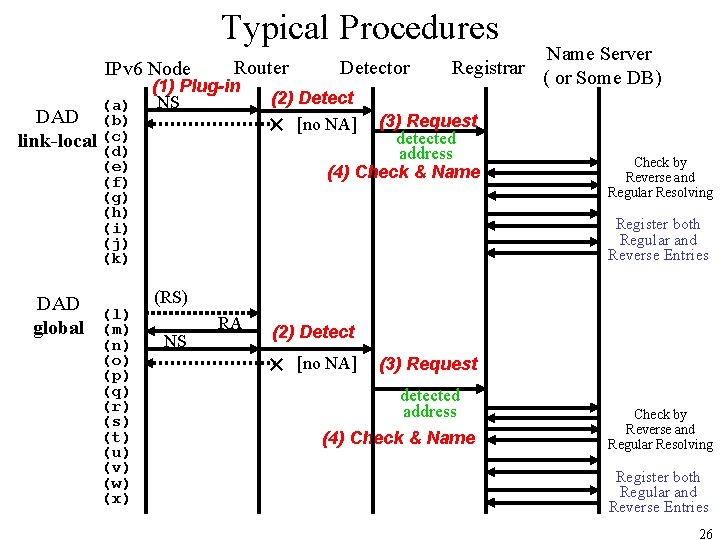
Typical Procedures IPv 6 Node (a) DAD (b) link-local (c) (d) (e) (f) (g) (h) (i) (j) (k) DAD global (l) (m) (n) (o) (p) (q) (r) (s) (t) (u) (v) (w) (x) Router (1) Plug-in NS Detector Registrar (2) Detect × [no NA] (3) Request detected address (4) Check & Name Server ( or Some DB) Check by Reverse and Regular Resolving Register both Regular and Reverse Entries (RS) NS RA (2) Detect × [no NA] (3) Request detected address (4) Check & Name Check by Reverse and Regular Resolving Register both Regular and Reverse Entries 26

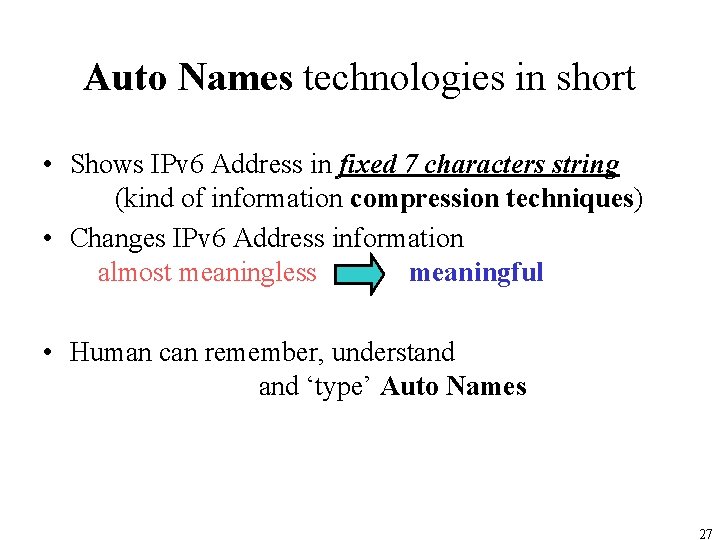
Auto Names technologies in short • Shows IPv 6 Address in fixed 7 characters string (kind of information compression techniques) • Changes IPv 6 Address information almost meaningless meaningful • Human can remember, understand ‘type’ Auto Names 27

Name Services • It is not clarified: which actual ‘name services’ is used for Auto Names. – DNS is first strong candidate for it. • All OS have DNS resolver implementations. • By using the DNS user authenticate implementation, it is easy to achieve the ‘Scoped Name’ features. 28

Discussions • Please let us know you comments. 29