Chapters All Final Review Professor Rick Han University




















- Slides: 23

Chapters: All Final Review Professor Rick Han University of Colorado at Boulder rhan@cs. colorado. edu Prof. Rick Han, University of Colorado at Boulder

Announcements • • • HW #5 solutions posted on May 4 Final May 7, 4: 30 -7 pm Tuesday’s lecture now on Web Office Hours Monday: 3 -5 pm Next, final review… Prof. Rick Han, University of Colorado at Boulder

Format of Final • • 2 ½ hours Comprehensive In class Closed book Calculator OK About 5 -6 multi-part questions About 20 -25 minutes for each multi-part question Prof. Rick Han, University of Colorado at Boulder

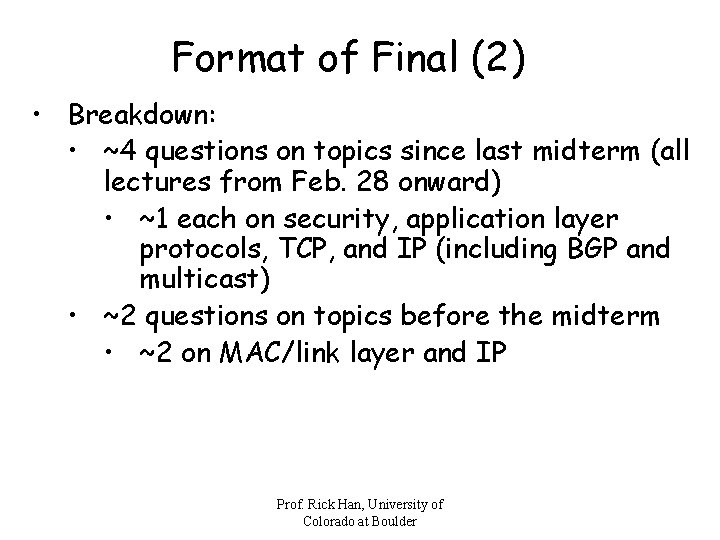
Format of Final (2) • Breakdown: • ~4 questions on topics since last midterm (all lectures from Feb. 28 onward) • ~1 each on security, application layer protocols, TCP, and IP (including BGP and multicast) • ~2 questions on topics before the midterm • ~2 on MAC/link layer and IP Prof. Rick Han, University of Colorado at Boulder

Potential Topics for Final • List is not all-inclusive; some topics may appear on final not listed here • How does ___ work? Why is it used? • Sections in textbook relevant to final: • • • Chapter 1: 1. 1 -1. 3 Chapter 2: 2. 1 -2. 8 Chapter 3: 3. 1 -3. 2 Chapter 4: 4. 1 -4. 4 Chapter 5: 5. 1 -5. 2 Chapter 6: 6. 2 -6. 4 Chapter 7: none Chapter 8: 8. 1 -8. 4 Prof. Rick Han, University of Chapter 9: 9. 1 -9. 2 Colorado at Boulder

Potential Topics for Final (2) • All topics in lecture notes are relevant to final • Relevant topics in lecture notes but not in the textbook: • • SACK TCP extensions: window scale & time stamp Wireless TCP: snoop Web caching proxies Load balancing via DNS, HTTP Redirect, NAT’s for address translation, firewalling, load balancing SMB/Samba Stream ciphers and WEP Prof. Rick Han, University of Colorado at Boulder

Potential Topics for Final (3) • All topics listed in the Midterm Review, plus the following… • IP: • • Addressing, Subnets, and CIDR BGP IP multicast • Link-state multicast • DVMRP • PIM UDP • Unreliable datagram delivery • Header, Checksum • Multiplexing/demultiplexing Prof. Rick Han, University of Colorado at Boulder

Potential Topics for Final (4) • TCP: • • Reliable Stream Delivery Header, Checksum Connection setup • How does a 3 -way handshake work and why does it work? • SYN, SYN/ACK • How does FIN and FIN/ACK exchange differ from SYN and SYN/ACK exchange? (half-closed) State machine • What states are traversed during connection setup? • In a normal termination, how does TIME_WAIT state differ Prof. from CLOSE_WAIT? Rick Han, University of Colorado at Boulder

Potential Topics for Final (5) • TCP: • Sliding window • Sequence #’s and segments • Window-based flow control • Cumulative ACK’s • Receiver window advertisements • Sender-side vs. receiver-side sliding window flow control • What is TCP Persist and why is it useful? • TCP Extensions • Timestamp address wrap-around with seq. #’s • Window scaling keeps pipe full over LFN’s Prof. Rick Han, University of Colorado at Boulder

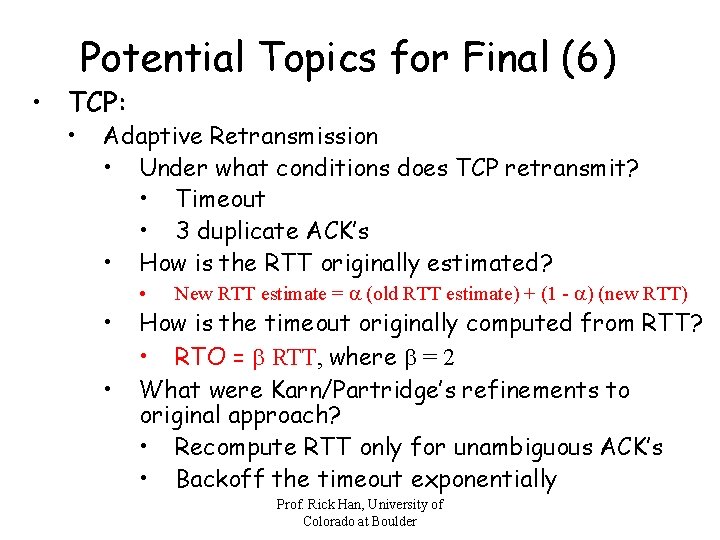
Potential Topics for Final (6) • TCP: • Adaptive Retransmission • Under what conditions does TCP retransmit? • Timeout • 3 duplicate ACK’s • How is the RTT originally estimated? • • • New RTT estimate = a (old RTT estimate) + (1 - a) (new RTT) How is the timeout originally computed from RTT? • RTO = b RTT, where b = 2 What were Karn/Partridge’s refinements to original approach? • Recompute RTT only for unambiguous ACK’s • Backoff the timeout exponentially Prof. Rick Han, University of Colorado at Boulder

Potential Topics for Final (7) • TCP: • Adaptive Retransmission • What were Jacobsen/Karels refinements to timeout algorithm? • Make the timeout a function of both the average and deviation – but why? • RTO = Smoothed Ave + 4 * Smoothed Dev Prof. Rick Han, University of Colorado at Boulder

Potential Topics for Final (8) • TCP: • Congestion Control • W = min (CW, FW) – why? • send no more packets than the network can handle without loss • Sawtooth behavior of CW – what’s the basic principle? • Probe network by expanding CW until loss, then reduce CW, then grow CW again, etc. • Slow Start is actually exponential increase • How does a sender detect that CW is too large? • A timeout occurs Prof. Rick Han, University of Colorado at Boulder

Potential Topics for Final (9) • TCP: • Congestion Control • Additive Increase/Multiplicative Decrease • After a timeout, divide CW by 2 and store in ssthresh • Slow start up to ssthresh, then add a/CW if CW packets in a RTT are safely ACK’ed • If 3 duplicate ACKs are received, then infer that one segment has been lost • Retransmit immediately, rather than wait for a timeout : called Fast Retransmit • Cancel slow start, and drop CW to half its value (approximately) rather than to one : called Fast Recovery Prof. Rick Han, University of Colorado at Boulder

Potential Topics for Final (10) • TCP: • Congestion Avoidance • Back off before there are packet losses • Informed by increasing RTT – Source-based • Informed by routers of congestion – DECbit (explicit), RED (implicit by dropped packets) • Queueing Disciplines • • What is a drop-tail policy? How do Fair Queueing and Weighted Fair Queueing enforce fairness? How are they work-conserving? Prof. Rick Han, University of Colorado at Boulder

Potential Topics for Final (11) • SACK-TCP • • Why is this an improvement over vanilla TCP? How are selective ACK’s achieved? • • What is the major problem with TCP over wireless? Solutions: • End-to-End approaches: ECN, ELN • Split connection • Link-Layer • Snoop TCP is a hybrid: TCP-aware • Retransmit locally and suppress duplicate ACK’s – all without having to terminate TCP connection • Advantages and disadvantages? • Wireless TCP Prof. Rick Han, University of Colorado at Boulder

Potential Topics for Final (12) • Application Layer: • • • DNS • Hierarchical naming • Hierarchical resolution of names: local, root & authoritative name servers with iterative/recursive resolution • Load distribution – DNS round robin HTTP • Stateless Request/Response protocol using text • Persistent HTTP 1. 1 • HTTP Caching Proxies – relevant headers? • HTTP Redirect for load balancing SMTP, MIME, and how is email relayed via SMTP mail Prof. Rick Han, University of gateways? Colorado at Boulder

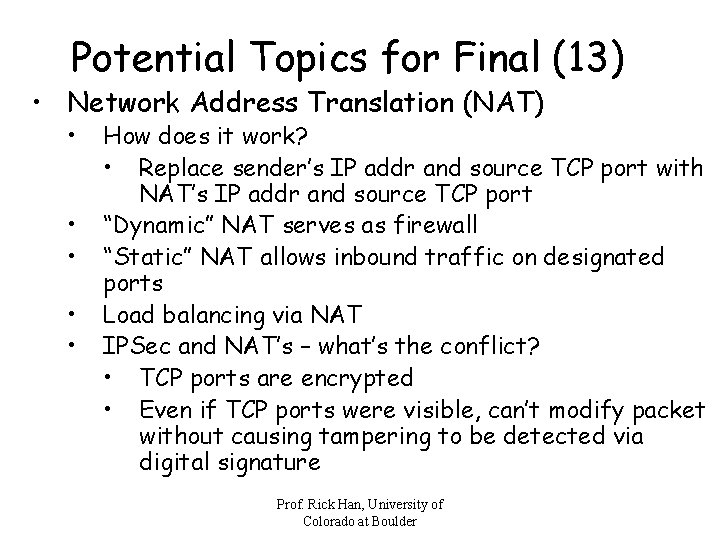
Potential Topics for Final (13) • Network Address Translation (NAT) • • • How does it work? • Replace sender’s IP addr and source TCP port with NAT’s IP addr and source TCP port “Dynamic” NAT serves as firewall “Static” NAT allows inbound traffic on designated ports Load balancing via NAT IPSec and NAT’s – what’s the conflict? • TCP ports are encrypted • Even if TCP ports were visible, can’t modify packet without causing tampering to be detected via digital signature Prof. Rick Han, University of Colorado at Boulder

Potential Topics for Final (14) • SMB/Samba • • Protocol for mapping file systems between UNIX and Windows – how does it work? What is NETBIOS and how does it relate to SMB? • Security: • • What are the six major characteristics of concern in security? • Confidentiality, Integrity, Authentication, Non. Repudiation, Availability, Authorization What are different types of cryptanalysis attacks? • Brute force, ciphertext-only, known-plaintext, chosen-plaintext, adaptive chosen-plaintext Prof. Rick Han, University of Colorado at Boulder

Potential Topics for Final (15) • Security: • Symmetric Key Cryptography • Same secret key on both endpoints • DES uses 16 stages; each employs principles of confusion and diffusion • What is a block cipher, how is it vulnerable, and how does Cipher-Block-Chaining (CBC) address this? • How do stream ciphers work? • What are various ways to securely distribute a shared secret key to both endpoints? • Diffie-Helman Key Exchange • Public key encryption of shared symmetric key • Key Distribution Center (KDC) – Kerberos Prof. Rick Han, University of Colorado at Boulder

Potential Topics for Final (16) • Security: • Public Key Cryptography • Asymmetric keys: a public key and a private key • Helps provide Confidentiality, Authentication, Integrity • Based on the difficulty of inverting one-way functions • How does RSA work? (see example) Prof. Rick Han, University of Colorado at Boulder

Potential Topics for Final (17) • Security: • • Authentication via • public-key digital signatures • 3 -way handshakes • Trusted 3 rd party • Public keys (Fig. 8. 11) How do one-way hashes provide data integrity? • What are some counterexamples? • Checksums for IP and WEP Prof. Rick Han, University of Colorado at Boulder

Potential Topics for Final (18) • Security: • • • Secure distribution of public keys • Trusted 3 rd party Certificate Authorities (CA) • What is a digital certificate and how does it certify the provider of the certificate? SSL/TLS – how is the secure connection established? IPSec • End-to-end encryption at the network layer • Impact on NAT’s • How do the two protocols AH and ESP provide confidentiality, integrity, and/or authentication? • How is a VPN created using IPSec? Prof. Rick Han, University of Colorado at Boulder

Potential Topics for Final (19) • Security: • Firewalls • Packet filters • Proxies • What are some sample policies that firewalls could implement? How are they flawed? • Good luck on the Final! Prof. Rick Han, University of Colorado at Boulder
 Ap gov review final exam review
Ap gov review final exam review Promotion from assistant to associate professor
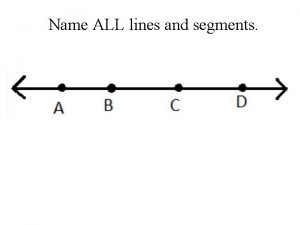
Promotion from assistant to associate professor Name three lines
Name three lines Research problem formulation
Research problem formulation Village by the sea chapter 1
Village by the sea chapter 1 Solas all chapters
Solas all chapters World history spring final exam review answers
World history spring final exam review answers World geography spring final review
World geography spring final review Spanish 1 semester 1 final exam answer key
Spanish 1 semester 1 final exam answer key Human body systems final exam
Human body systems final exam Poe practice test - materials answer key
Poe practice test - materials answer key Ied final exam review
Ied final exam review World history semester 2 final review packet
World history semester 2 final review packet World history first semester exam review
World history first semester exam review Entrepreneurship 1 final exam review
Entrepreneurship 1 final exam review Spanish 2 review packet
Spanish 2 review packet Environmental science defination
Environmental science defination World history final exam study guide
World history final exam study guide Us history semester 2 final exam
Us history semester 2 final exam Algebra 2 semester 2 final exam
Algebra 2 semester 2 final exam Geometry final review
Geometry final review English 11 semester exam
English 11 semester exam Physics 20 final exam practice
Physics 20 final exam practice Financial accounting final exam
Financial accounting final exam