Chapter 21 Trivial File Transfer Protocol TFTP Mc

- Slides: 23

Chapter 21 Trivial File Transfer Protocol (TFTP) Mc. Graw-Hill ©The Mc. Graw-Hill Companies, Inc. , 2000

CONTENTS • • Mc. Graw-Hill MESSAGES CONNECTION DATA TRANSFER UDP PORTS TFTP EXAMPLE TFTP OPTIONS SECURITY APPLICATIONS ©The Mc. Graw-Hill Companies, Inc. , 2000

TFTP uses the services of UDP on the well-known port 69. Mc. Graw-Hill ©The Mc. Graw-Hill Companies, Inc. , 2000

21. 1 MESSAGES Mc. Graw-Hill ©The Mc. Graw-Hill Companies, Inc. , 2000

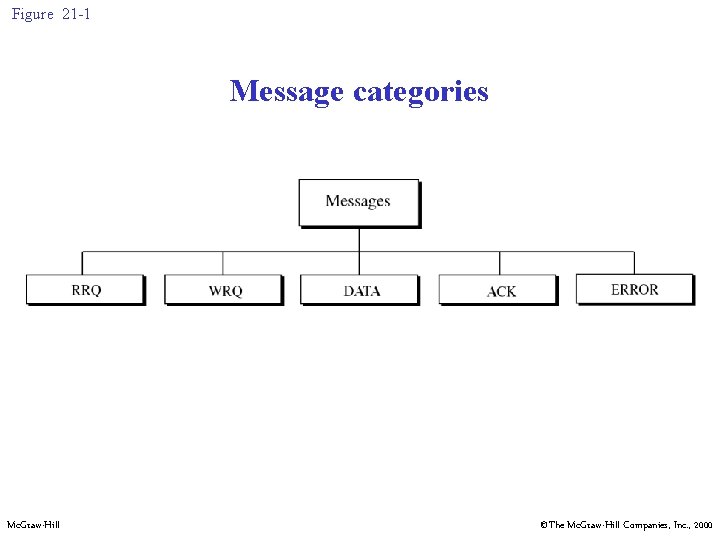
Figure 21 -1 Message categories Mc. Graw-Hill ©The Mc. Graw-Hill Companies, Inc. , 2000

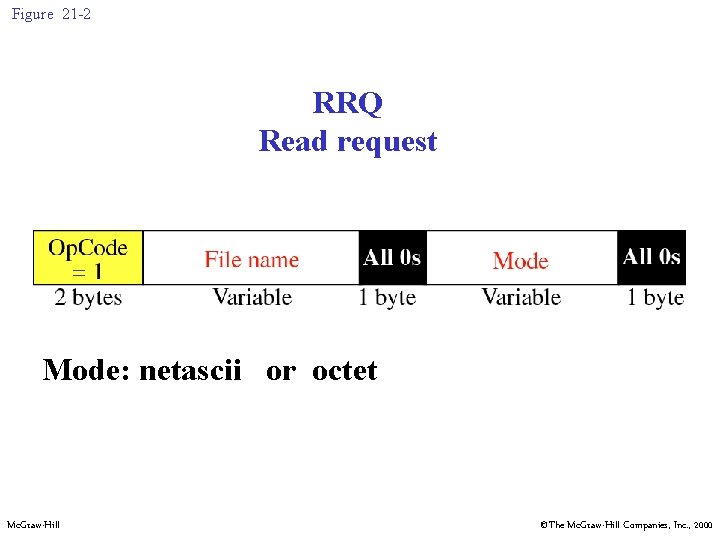
Figure 21 -2 RRQ Read request Mode: netascii or octet Mc. Graw-Hill ©The Mc. Graw-Hill Companies, Inc. , 2000

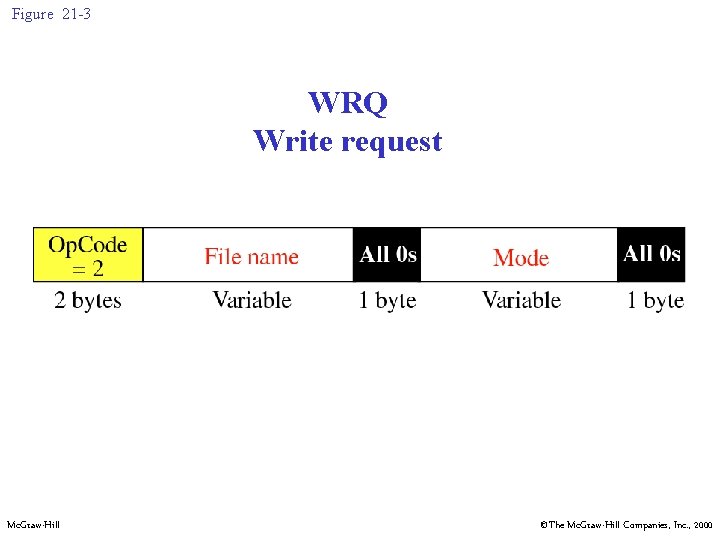
Figure 21 -3 WRQ Write request Mc. Graw-Hill ©The Mc. Graw-Hill Companies, Inc. , 2000

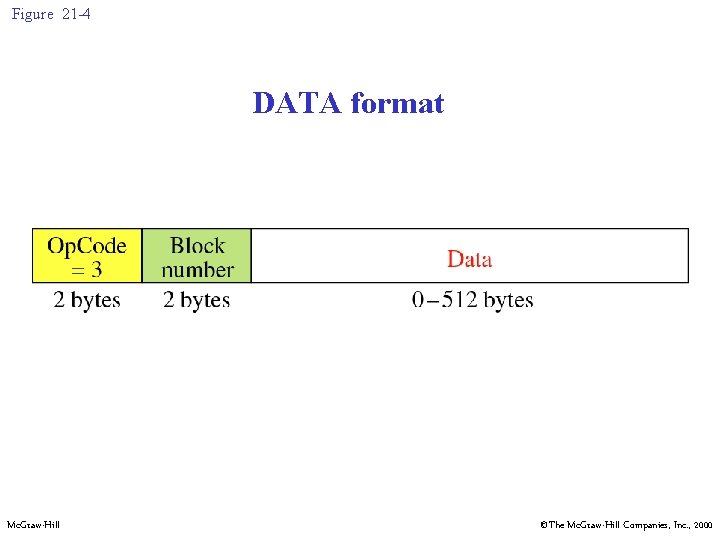
Figure 21 -4 DATA format Mc. Graw-Hill ©The Mc. Graw-Hill Companies, Inc. , 2000

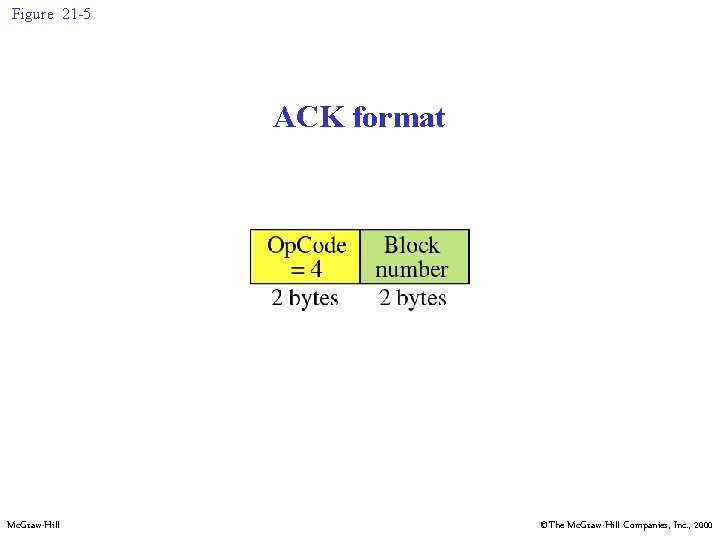
Figure 21 -5 ACK format Mc. Graw-Hill ©The Mc. Graw-Hill Companies, Inc. , 2000

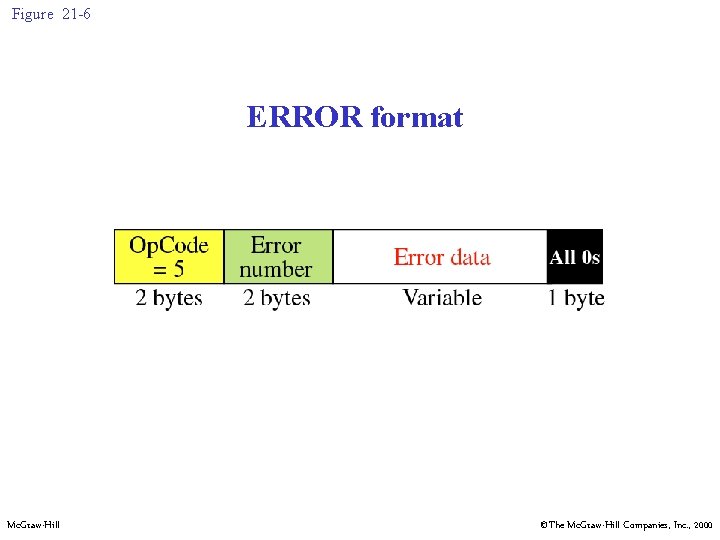
Figure 21 -6 ERROR format Mc. Graw-Hill ©The Mc. Graw-Hill Companies, Inc. , 2000

21. 2 CONNECTION Mc. Graw-Hill ©The Mc. Graw-Hill Companies, Inc. , 2000

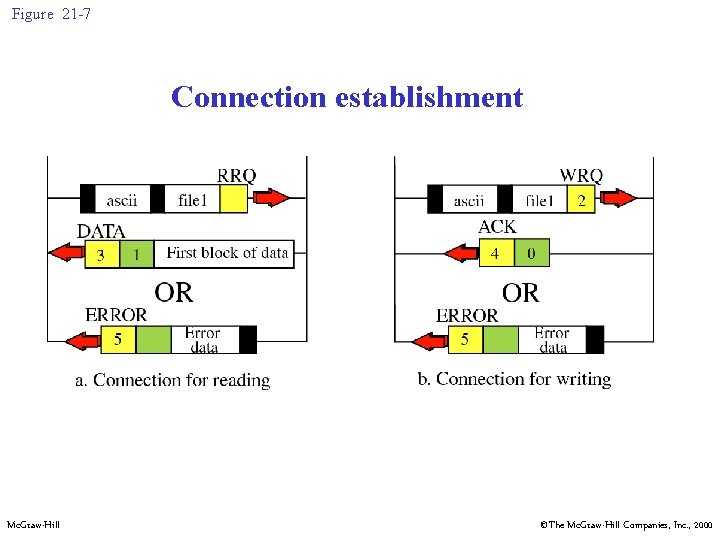
Figure 21 -7 Connection establishment Mc. Graw-Hill ©The Mc. Graw-Hill Companies, Inc. , 2000

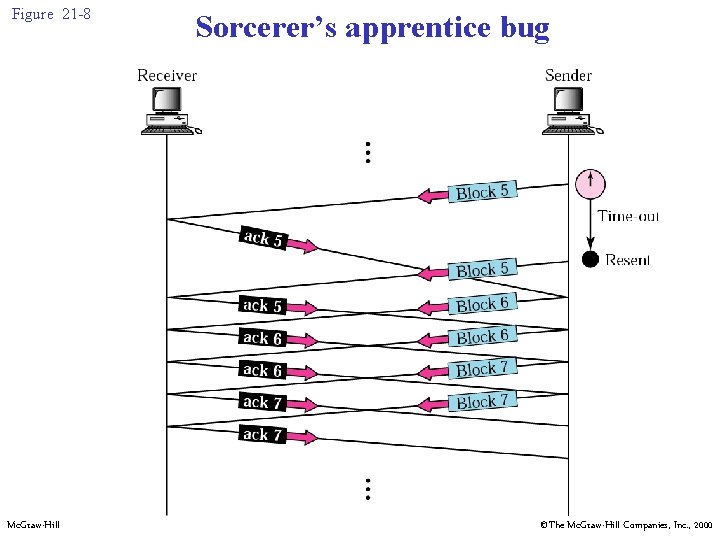
21. 3 DATA TRANSFER Mc. Graw-Hill ©The Mc. Graw-Hill Companies, Inc. , 2000

Figure 21 -8 Mc. Graw-Hill Sorcerer’s apprentice bug ©The Mc. Graw-Hill Companies, Inc. , 2000

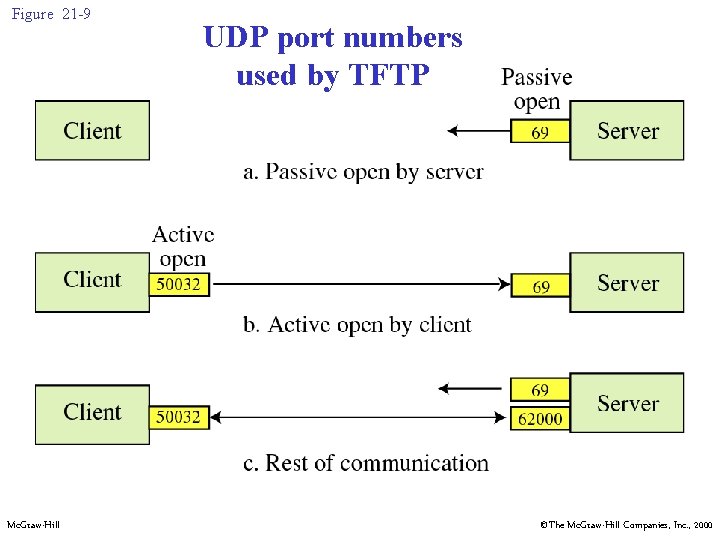
21. 4 UDP PORTS Mc. Graw-Hill ©The Mc. Graw-Hill Companies, Inc. , 2000

Figure 21 -9 Mc. Graw-Hill UDP port numbers used by TFTP ©The Mc. Graw-Hill Companies, Inc. , 2000

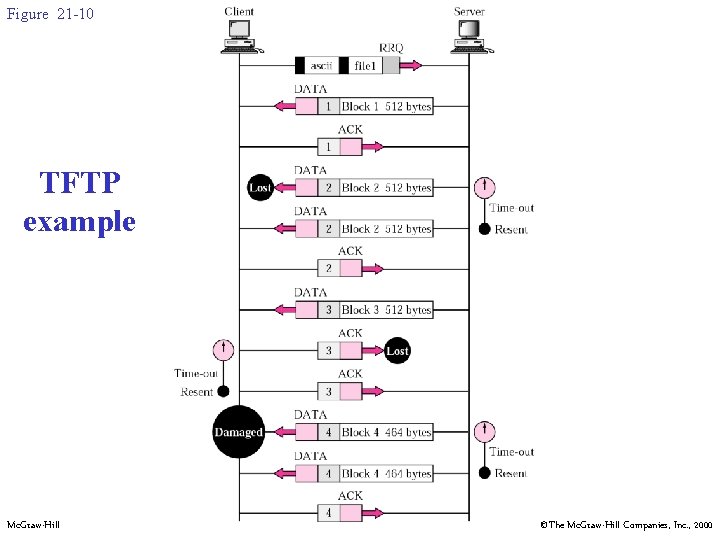
21. 5 TFTP EXAMPLE Mc. Graw-Hill ©The Mc. Graw-Hill Companies, Inc. , 2000

Figure 21 -10 TFTP example Mc. Graw-Hill ©The Mc. Graw-Hill Companies, Inc. , 2000

21. 6 TFTP OPTIONS Mc. Graw-Hill ©The Mc. Graw-Hill Companies, Inc. , 2000

21. 7 SECURITY Mc. Graw-Hill ©The Mc. Graw-Hill Companies, Inc. , 2000

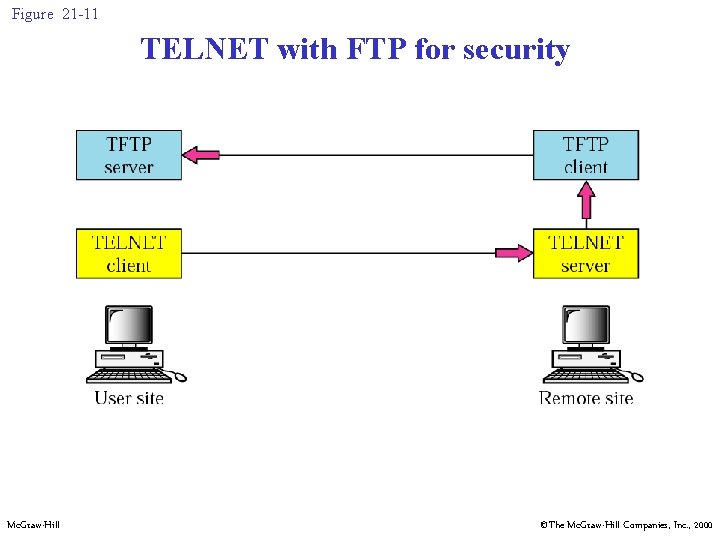
Figure 21 -11 TELNET with FTP for security Mc. Graw-Hill ©The Mc. Graw-Hill Companies, Inc. , 2000

21. 8 APPLICATIONS Mc. Graw-Hill ©The Mc. Graw-Hill Companies, Inc. , 2000

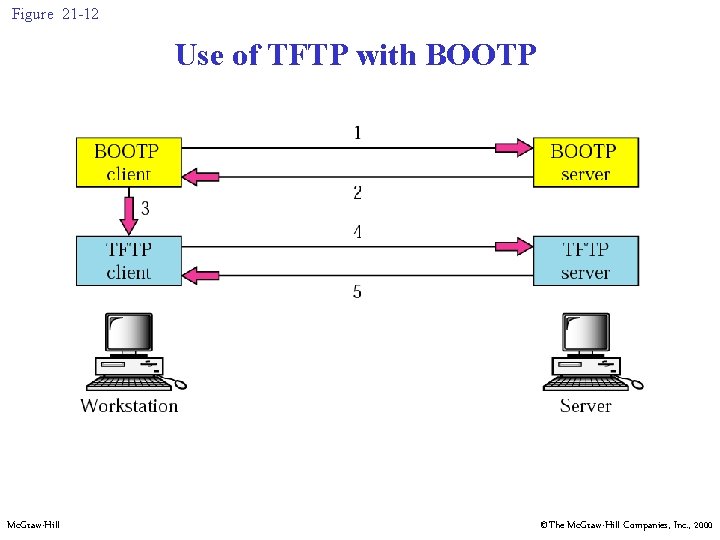
Figure 21 -12 Use of TFTP with BOOTP Mc. Graw-Hill ©The Mc. Graw-Hill Companies, Inc. , 2000