Chapter 11 Legal and Ethical Issues Internet Taxation







































- Slides: 44

Chapter 11, Legal and Ethical Issues; Internet Taxation Outline 11. 1 Introduction 11. 2 Legal Issues: Privacy on the Internet 11. 2. 1 Right to Privacy 11. 2. 2 Internet and the Right to Privacy 11. 2. 3 Network Advertising Initiative 11. 2. 4 Employer and Employee 11. 2. 5 Protecting Yourself as a User 11. 2. 6 Protecting Your Business: Privacy Issues 11. 3 Legal Issues: Other Areas of Concern 11. 3. 1 Defamation 11. 3. 2 Sexually Explicit Speech 11. 3. 3 Children and the Internet 11. 3. 4 Alternative Methods of Regulation 11. 3. 5 Intellectual Property: Copyrights and Patents 11. 3. 6 Trademark and Domain Name Registration 2001 Prentice Hall, Inc. All rights reserved.

Chapter 11, Legal and Ethical Issues; Internet Taxation Outline 11. 4 11. 5 11. 3. 7 Unsolicited Commercial E-mail (Spam) 11. 3. 8 Online Auctions 11. 3. 9 Online Contracts 11. 3. 10 Online User Agreements Cybercrime Internet Taxation 2001 Prentice Hall, Inc. All rights reserved.

11. 1 Introduction • Real space – Our physical environment consisting of temporal and geographic boundaries • Cyberspace – The realm of digital transmission not limited by geography 2001 Prentice Hall, Inc. All rights reserved.

11. 2 Legal Issues: Privacy on the Internet • Difficulty of applying traditional law to the Internet • Technology and the issue of privacy 2001 Prentice Hall, Inc. All rights reserved.

11. 2. 1 Right to Privacy • Implicit in the First, Fourth, Ninth and Fourteenth Amendments • Olmstead vs. United States – Telecommunication of alcohol sales during Prohibition era – New application of the Fourth Amendment • Translation – Interpreting the Constitution to protect the greater good 2001 Prentice Hall, Inc. All rights reserved.

11. 2. 2 Internet and the Right to Privacy • Self-regulated medium – The Internet industry governs itself • Many Internet companies collect users’ personal information – Privacy advocates argue that these efforts violate individuals’ privacy rights – Online marketers and advertisers suggest that online companies can better serve their users by recording the likes and dislikes of online consumers • Financial Services Modernization Act of 1999 – Establishes a set of regulations concerning the management of consumer information 2001 Prentice Hall, Inc. All rights reserved.

11. 2. 3 Network Advertising Initiative • Network Advertising Initiative (NAI) – Approved by the FTC in July 1999 to support self regulation • NAI currently represents 90 percent of Web advertisers • Determines the proper protocols for managing a Web user’s personal information on the Internet • Prohibits the collection of consumer data from medical and financial sites • Allows the combination of Web-collected data and personal information 2001 Prentice Hall, Inc. All rights reserved.

11. 2. 3 Double. Click: Marketing with Personal Information Feature • Regulation of the Internet could limit a company’s efforts to buy and sell advertising • Double. Click – Advertising network of over 1, 500 sites and 11, 000 clients • Abacus Direct Corp – Names, addresses, telephone numbers, age, gender, income levels and a history of purchases at retail, catalog and online stores • Digital redlining – Skewing of an individual’s knowledge of available products by basing the advertisements the user sees on past behavior 2001 Prentice Hall, Inc. All rights reserved.

11. 2. 4 Employer and Employee • Keystroke cop – Registers each keystroke before it appears on the screen • Company time and company equipment vs. the rights of employees • Determining factors – Reasonable expectation of privacy – Legitimate business interests • Reasons for surveillance – Slower transmission times – Harassment suits – Low productivity 2001 Prentice Hall, Inc. All rights reserved.

11. 2. 4 Employer and Employee • Notice of Electronic Monitoring Act – Proposed in 2000 – Would require employers to notify employees of telephone, e -mail and Internet surveillance – Annual updates or when policy changes are made – The frequency of surveillance, the type of information collected and the method of collection would also be disclosed 2001 Prentice Hall, Inc. All rights reserved.

11. 2. 4 Michael A. Smyth vs. The Pillsbury Company Feature • Dismissed as regional operations manager • Questionable material in e-mail • Pennsylvania law – “An employer may discharge an employee with or without cause, at pleasure, unless restrained by some contract" • Public policy – Reprimanding an employee called for jury duty – Denial of employment as a result of previous convictions • Verdict awarded to Pillsbury – No reasonable expectation of privacy – Legitimate business interests 2001 Prentice Hall, Inc. All rights reserved.

11. 2. 5 Protecting Yourself as a User • Anonimity and pseudonimity – Privacy. X. com • Platform for Privacy Preferences Project (P 3 P) – Browser complies in accordance with users’ privacy preferences by allowing them to interact in specific ways • Privacy services and software – – – Junkbusters. com Privacy. Choices. org Center for Democracy and Technology Electronic Frontier Foundation Electronic Privacy Information Center Privacy. Rights. org 2001 Prentice Hall, Inc. All rights reserved.

11. 2. 6 Protecting Your Business: Privacy Issues • Privacy policy – The stated policy regarding the collection and use of visitor’s personal information • Privacy policy services and software – Privacy. Bot. com – TRUSTe 2001 Prentice Hall, Inc. All rights reserved.

11. 2. 6 Protecting Your Business: Privacy Issues • Core Fair Information Practices – Consumers should be made aware that personal information will be collected – The consumer should have a say in how this information will be used – The consumer should have the ability to check the information collected to ensure that it is complete and accurate – The information collected should be secured – The Web site should be responsible for seeing that these practices are followed 2001 Prentice Hall, Inc. All rights reserved.

11. 2. 6 Protecting Your Business: Privacy Issues Privacy. Bot. com. (Courtesy of Invisible Hand Software, LLC. ) 2001 Prentice Hall, Inc. All rights reserved.

11. 3 Legal Issues: Other Areas of Concern • • • Defamation Sexually explicit speech Copyright and patents Trademarks Unsolicited e-mail First Amendment – "Congress shall make no law respecting an establishment of religion, or prohibiting the free exercise thereof; or abridging the freedom of speech, or of the press; or the right of the people peaceably to assemble and to petition the Government for a redress of grievances" 2001 Prentice Hall, Inc. All rights reserved.

11. 3. 1 Defamation • Defamation – The act of injuring another’s reputation, honor or good name through false written or oral communication • Libel – Defamatory statements written or spoken in a context in which they have longevity and pervasiveness that exceed slander 2001 Prentice Hall, Inc. All rights reserved.

11. 3. 1 Defamation • Slander – Spoken defamation • Proving defamation – The statement must have been published, spoken or broadcast – There must be identification of the individual(s) through name or reasonable association – The statement must be defamatory – There must be fault – There must be evidence of injury 2001 Prentice Hall, Inc. All rights reserved.

11. 3. 1 Defamation • Good Samaritan provision, Section 230 of the Telecommunications Act – Protects ISPs from defamation lawsuits when the ISPs’ attempt to control potentially damaging postings – “Obscene, lewd, lascivious, filthy, excessively violent, harassing or otherwise objectionable" 2001 Prentice Hall, Inc. All rights reserved.

11. 3. 1 Cubby vs. Compuserve and Stratton Oakmont vs. Prodigy Feature • Cubby vs. Compuserve – Anonymous individual used a news service hosted by Compuserve to post an allegedly defamatory statement • Distributor vs. publisher – A distributor cannot be held liable for a defamatory statement unless the distributor has knowledge of the content – Compuserve was a distributor of content • Stratton Oakmont vs. Prodigy – Claimed responsibility to remove potentially defamatory or otherwise questionable material – Prodigy served as a publisher of the content 2001 Prentice Hall, Inc. All rights reserved.

11. 3. 2 Sexually Explicit Speech • Miller vs. California (1973) – The Miller Test identifies the criteria used to distinguish between obscenity and pornography – Must appeal to the prurient interest, according to contemporary community standards – When taken as a whole, lacks serious literary, artistic, political or scientific value • Challenge of community standards in cyberspace 2001 Prentice Hall, Inc. All rights reserved.

11. 3. 2 United States vs. Thomas Feature • Thomas – Internet business owner in California, owner of pornographic Web site from which merchandise could be ordered – Accessible by password – Acceptable by California community standards – Sold pornographic material to Tennessee resident (opposing community standards) • Thomas found guilty • Non-content related means – Effort to control the audience rather than controlling the material 2001 Prentice Hall, Inc. All rights reserved.

11. 3. 3 Children and the Internet • Accessibility of information • Decency Act of 1996 (CDA) and Children’s Online Protection Act of 1998 (COPA) – Designed to restrict pornography on the Internet, particularly in the interest of children – Overbroad – “Patently offensive, ” “indecent” and “harmful to minors” • Chilling effect – Limiting speech to avoid a lawsuit • Children’s Online Privacy Protection Act of 2000 (COPPA) – Prohibits Web sites from collecting personal information from children under the age of 13 2001 Prentice Hall, Inc. All rights reserved.

11. 3. 4 Alternatives Methods of Regulation • Blocking and filtering – Allows users to select what kinds of information can and cannot be received through their browsers • Blocking and filtering software and services – Surfwatch. com – Cybersitter. com – Net. Nanny. com • Infringement of First Amendment rights • Parent’s counsel – Cyber. Angels. com – Get. Net. Wise. com – Parentsoup. com 2001 Prentice Hall, Inc. All rights reserved.

11. 3. 4 Alternatives Methods of Regulation Net Nanny home page. (Courtesy of Net Nanny Software International, Inc. ) 2001 Prentice Hall, Inc. All rights reserved.

11. 3. 5 Intellectual Property: Patents and Copyright • Copyright – The protection given to the author of an original piece, including “literary, dramatic, musical, artistic and certain other intellectual works” – Whether the work has been published or not – Protects only the expression or form of an idea and not the idea itself – Provides incentive to the creators of original material – Guaranteed for the life of the author plus seventy years 2001 Prentice Hall, Inc. All rights reserved.

11. 3. 5 Intellectual Property: Patents and Copyrights • Digital Millennium Copyright Act of 1998 (DMCA) – Represents the rights of creative bodies to protect their work as well as the rights of educators and resource providers to receive access to this work – Makes it illegal to delete or otherwise alter the identifying information of the copyright owner – Prevents the circumvention of protection mechanisms and/or the sale of such circumvention mechanisms – Protects the fair use of copyrighted material 2001 Prentice Hall, Inc. All rights reserved.

11. 3. 5 Intellectual Property: Patents and Copyright • Fair use – The use of a copyrighted work for education, research, criticism – The purpose of the copyrighted work is examined – The nature of the copyrighted work is taken into account – The amount of the material that has been reproduced is reviewed – The effect is taken into consideration 2001 Prentice Hall, Inc. All rights reserved.

11. 3. 5 Intellectual Property: Patents and Copyright • Patent – Grants the creator sole rights to the use of a new discovery – Protection for 20 years • Opposing the length of a patent – Does not foster the creation of new material • Includes “methods of doing business” since 1998 – Idea must be new and not obvious to a skilled person • Amazon’s 1 -Click patent – September, 1999 – Huge advantage over competitors, as 65% of shopping carts are abandoned before purchase is complete – Barnesandnoble. com Express Lane violated patent 2001 Prentice Hall, Inc. All rights reserved.

11. 3. 5 File Sharing and the Copyright Debate Feature • Present significant challenges to the traditional treatment of copyright protection • MP 3 – A compression method used to substantially reduce the size of audio files, with no significant reduction in sound quality • Napster – Operates as a centralized service – Offers software that allows users to download MP 3 files from the hard drives of other members • Gnutella – Operates as a decentralized service – Individuals with Gnutella software installed on their computers operate as both a client and a server 2001 Prentice Hall, Inc. All rights reserved.

11. 3. 5 File Sharing and the Copyright Debate Feature • Legal issues – Freedom of exchange (enabled by technological advancements) vs. copyright infringement – Ability to voice one’s opinion and circumvent efforts of censorship – If copyrighted works are distributed over the system, creators will have less incentive to continue generating original works • Sony Betamax (1984) – Courts awarded the victory to Sony, suggesting that the Betamax provided other uses (recording for personal viewing) that justified its existence 2001 Prentice Hall, Inc. All rights reserved.

11. 3. 5 United States vs. Lamacchia Feature • Changed the face of copyright protection (1994) • Posting of copyrighted material • Not guilty under the Copyright Act of 1976 – The violation must have been conducted "willfully and for purposes of commercial advantage or private financial gain” • La. Machhia did not profit from the copyright violations • La. Macchia was not convicted for his actions 2001 Prentice Hall, Inc. All rights reserved.

11. 3. 6 Trademark and Domain Name Registration • Parasite – Selects a domain name based on common typos made when entering a popular domain name • Cybersquatter – Buys an assortment of domain names that are obvious representations of a brick-and-mortar company 2001 Prentice Hall, Inc. All rights reserved.

11. 3. 6 Trademark and Domain Name Registration • Anticybersquatting Consumer Protection Act of 1999 (ACPA) – Protects traditional trademarking in cyberspace – Protects trademarks belonging to a person or entity other than the person or entity registering or using the domain name – Persons registering domain names are protected from prosecution if they have a legitimate claim to the domain name – Domain names cannot be registered with the intention of resale to the rightful trademark owner 2001 Prentice Hall, Inc. All rights reserved.

11. 3. 7 Unsolicited Commercial mail (Spam) E- • Cost is primarily incurred by the receiver and the ISP • Organizations distributing spam – Maintain anonymity and receivers cannot request to be taken off the organization’s mailing list – Present themselves as a legitimate company and damage the legitimate company’s reputation • Unsolicited Electronic Mail Act – Mandates that the nature of the e-mail be made clear – Would require online marketers to know the policy of every ISP they encounter on the Web 2001 Prentice Hall, Inc. All rights reserved.

11. 3. 8 Online Auctions • Question of government regulation • International regulation of auctions • Copyright infringement and auction aggregation services • The Collections of Information Antipiracy Act (CIAA) – Makes it easier to prosecute any group which takes listings from one organization and, in doing so, harms the original business • Shill bidding – Sellers bid for their own items to increase the bid price 2001 Prentice Hall, Inc. All rights reserved.

11. 3. 9 Online Contracts • Electronic Signatures in Global and National Commerce Act of 2000 (E-Sign Bill) – Designed to promote online commerce by legitimizing online contractual agreements – Digital agreements will receive the same level of validity as hard-copy counterparts – Allows cooperating parties to establish their own contracts 2001 Prentice Hall, Inc. All rights reserved.

11. 3. 10 User Agreements • Requires users to agree to certain terms regarding the service or product provided by the site before entering • Shrink-wrap agreement – An agreement printed on the outside of the package holding the product that becomes binding when the consumer opens the package • Click-through agreement – A pop-up screen to which users must agree before they can continue • Depending on their presentation, these types of agreements can be considered valid by the U. S. courts 2001 Prentice Hall, Inc. All rights reserved.

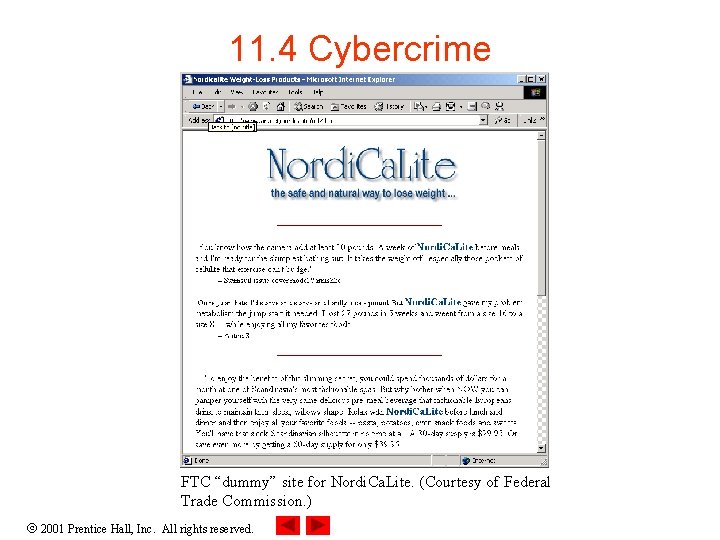
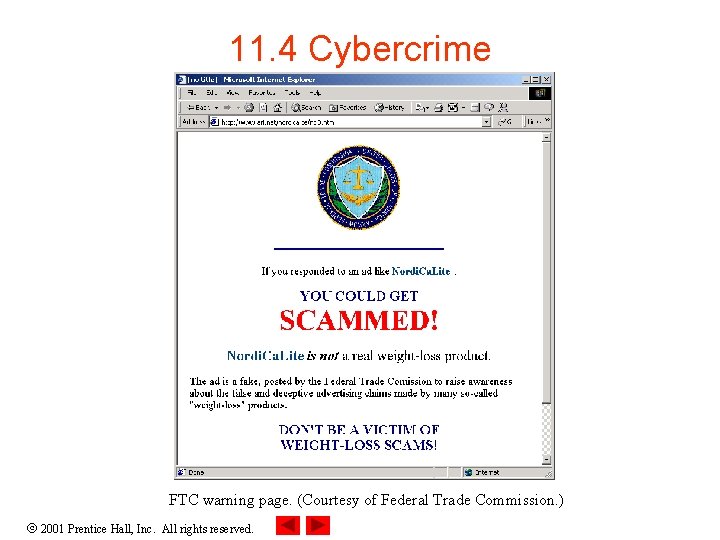
11. 4 Cybercrime • Auctions, chat rooms and bulletin boards are among the most popular forums for illegal activities • Viruses, which often lead to denial of service or a loss of stored information, are among the most common cybercrimes • Stock scams – Crimes in which individuals purchase stocks, then present false claims about the value of that stock in chat rooms or on bulletin boards to sell them back at a higher price • Web page hijacking – Web page is used as a gateway (the intermediary between one site and another) to another site 2001 Prentice Hall, Inc. All rights reserved.

11. 4 Cybercrime FTC “dummy” site for Nordi. Ca. Lite. (Courtesy of Federal Trade Commission. ) 2001 Prentice Hall, Inc. All rights reserved.

11. 4 Cybercrime FTC warning page. (Courtesy of Federal Trade Commission. ) 2001 Prentice Hall, Inc. All rights reserved.

11. 5 Internet Taxation • The opposing arguments – Permanent ban on Internet taxation – Fair taxation of Internet sales • Taxation methods – If both a vendor and a consumer are located in the same state sales tax is applied – If the vendor and the consumer are not located in the same state, then the sale is subject to a use tax – If the vendor has a physical presence, or nexus, then it is required to collect the tax; otherwise the vendor must assess the tax and pay it directly to the state 2001 Prentice Hall, Inc. All rights reserved.

11. 5 Internet Taxation • Problems with Internet taxation – The definition of physical presence (location of the ISP, the location of the server or the location of the home page) – States vary according to what transactions are subject to taxation – Sales tax revenues are the largest single source of a state’s revenue and are used to fund government-subsidized programs, including the fire department, the police and the public education systems – State and local governments further argue that removing taxation methods from their jurisdiction infringes upon state sovereignty, an element of the checks-and-balances system maintained by the United States Constitution 2001 Prentice Hall, Inc. All rights reserved.

11. 5 Internet Taxation • Problems with Internet taxation – To meet the taxation requirements of all parties in online transactions, e-businesses would be required to know and understand all these methods • Internet Tax Commission – Reviewed the issue of Internet taxation – Revision of state and local taxes to make taxing a feasible process for Internet businesses – Establish clearer definitions on the meaning of “physical presence” – Define universal taxation exemptions 2001 Prentice Hall, Inc. All rights reserved.
 Ethical issues in e-commerce
Ethical issues in e-commerce Chapter 2 ethical and legal issues
Chapter 2 ethical and legal issues Chapter 3 medical legal and ethical issues
Chapter 3 medical legal and ethical issues Chapter 3 legal and ethical issues
Chapter 3 legal and ethical issues Legal and ethical issues chapter 5
Legal and ethical issues chapter 5 Chapter 3 legal and ethical issues
Chapter 3 legal and ethical issues Chapter 6 legal and ethical issues
Chapter 6 legal and ethical issues Chapter 5 legal and ethical issues
Chapter 5 legal and ethical issues Legal and ethical aspects in nursing
Legal and ethical aspects in nursing Chapter 2 ethical and legal issues
Chapter 2 ethical and legal issues Ethical and legal issues chapter 2
Ethical and legal issues chapter 2 Ch 5 legal and ethical responsibilities
Ch 5 legal and ethical responsibilities Legal and ethical issues chapter 5
Legal and ethical issues chapter 5 Chapter 2 ethical and legal issues
Chapter 2 ethical and legal issues Chapter 6 legal and ethical issues
Chapter 6 legal and ethical issues Chapter 6 legal and ethical issues
Chapter 6 legal and ethical issues Chapter 3 legal and ethical issues
Chapter 3 legal and ethical issues Resourceful citer
Resourceful citer Legal ethical and professional aspects of security
Legal ethical and professional aspects of security Legal and ethical issues in use of ict in education
Legal and ethical issues in use of ict in education Legal and ethical issues in computer security
Legal and ethical issues in computer security Ethical and legal issues involved in practicum
Ethical and legal issues involved in practicum Attack sophistication vs intruder technical knowledge
Attack sophistication vs intruder technical knowledge Ethical and legal issues affecting the nursing assistant
Ethical and legal issues affecting the nursing assistant What is the difference between ethical and legal issues
What is the difference between ethical and legal issues Legal aspects of community health
Legal aspects of community health Legal and ethical issues in information security
Legal and ethical issues in information security Legal issues in psychiatric nursing
Legal issues in psychiatric nursing Emerging issues in taxation
Emerging issues in taxation Dho chapter 5 legal and ethical responsibilities
Dho chapter 5 legal and ethical responsibilities Health care responsibilities
Health care responsibilities Chapter 4 legal and ethical responsibilities
Chapter 4 legal and ethical responsibilities Nonmaleficence
Nonmaleficence Chapter 4 ethical and social issues in information systems
Chapter 4 ethical and social issues in information systems 4 components of an information system
4 components of an information system Ethical issues in qualitative research chapter 4
Ethical issues in qualitative research chapter 4 Chapter 4 ethical issues
Chapter 4 ethical issues Chapter 4 ethical issues
Chapter 4 ethical issues The perceived relevance or importance of an ethical issue
The perceived relevance or importance of an ethical issue Lesson 1 no taxation without representation
Lesson 1 no taxation without representation Chapter 5 lesson 1 no taxation without representation
Chapter 5 lesson 1 no taxation without representation Legal and ethical responsibilities of a coach
Legal and ethical responsibilities of a coach Legal and ethical principles in healthcare
Legal and ethical principles in healthcare Legal and ethical environment of business
Legal and ethical environment of business Beneficence
Beneficence