CGNAT on VSM in 5 1 1 What














- Slides: 24

CGNAT on VSM in 5. 1. 1

What is VSM? Virtualized Services Module(VSM) is virtualized platform in ASR 9 K to host multiple Service applications. This document will be focusing on CGN/CGNv 6(NAT 44) as an example.

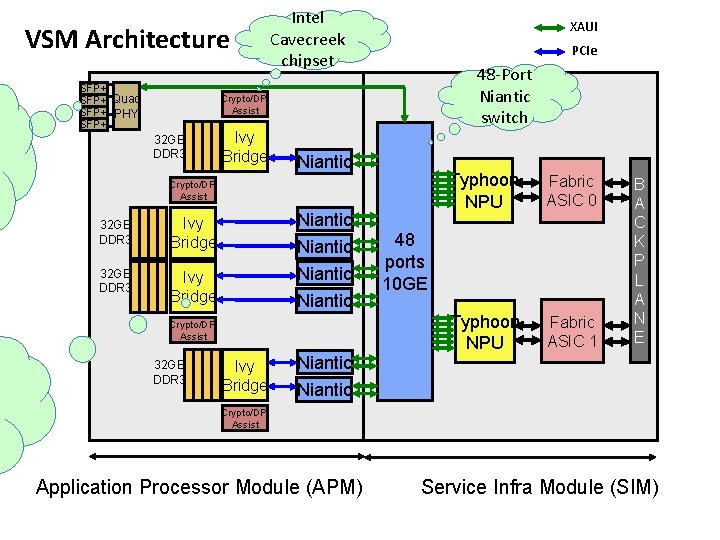
VSM Architecture SFP+ Quad SFP+ PHY SFP+ Intel Cavecreek chipset XAUI PCIe 48 -Port Niantic switch Crypto/DPI Assist 32 GB DDR 3 Ivy Bridge Niantic Niantic Crypto/DPI Assist 32 GB DDR 3 Ivy Bridge Niantic Typhoon NPU Fabric ASIC 0 Typhoon NPU Fabric ASIC 1 48 ports 10 GE B A C K P L A N E Niantic Crypto/DPI Assist Application Processor Module (APM) Service Infra Module (SIM)

VSM Hardware Intel x 86 Ivy Bridge CPU 1 Intel CPU with 10 cores Total of 4 CPU with 40 Cores. With Intel Hyper-threading technology total of 80 cores for 4 CPU; 20 cores per CPU can be achieved. • Intel Cavecreek Chipset provides Crypto/DPI assist functionality. • •

Virtualized Software Infrastructure KVM hypervisor runs on Linux. Multiple Service Applications can be hosted. Service chaining of applications can be achieved in two ways: 1) Via static route 2) Via One. PK

Interface Terminologies a) SVI Infra (identified by ‘interface Service. Infra’) –used to send SVI and CGv 6 related control/mgmt traffic between XR and Linux side b) SVI App (identified by ‘interface Service. App’) –used to send CGv 6 data traffic to/from CGv 6 applications.

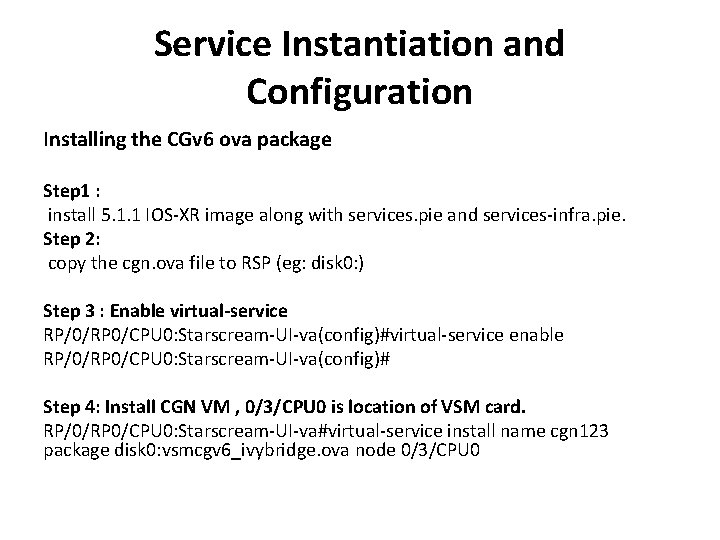
Service Instantiation and Configuration Installing the CGv 6 ova package Step 1 : install 5. 1. 1 IOS-XR image along with services. pie and services-infra. pie. Step 2: copy the cgn. ova file to RSP (eg: disk 0: ) Step 3 : Enable virtual-service RP/0/RP 0/CPU 0: Starscream-UI-va(config)#virtual-service enable RP/0/RP 0/CPU 0: Starscream-UI-va(config)# Step 4: Install CGN VM , 0/3/CPU 0 is location of VSM card. RP/0/RP 0/CPU 0: Starscream-UI-va#virtual-service install name cgn 123 package disk 0: vsmcgv 6_ivybridge. ova node 0/3/CPU 0

CGv 6 Installation status Step 5: Status of Installation RP/0/RP 0/CPU 0: Starscream-UI-va#sh virtual-service list Virtual Service List: Name Status Package Name Node Name _______________________________________ cgn 123 Installing vsmcgv 6_ivybridge. ova 0/3/CPU 0 RP/0/RP 0/CPU 0: Starscream-UI-va#sh virtual-service list Virtual Service List: Name Status Package Name Node Name _______________________________________ cgn 123 Installed vsmcgv 6_ivybridge. ova 0/3/CPU 0 RP/0/RP 0/CPU 0: Starscream-UI-va#

CGv 6 VM activate Step 6: Configure CGv 6 VM RP/0/RP 0/CPU 0: Starscream-UI-va(config)#virtual-service cgn 123 RP/0/RP 0/CPU 0: Starscream-UI-va(config-virt-service)# vnic interface Ten. Gig. E 0/3$ RP/0/RP 0/CPU 0: Starscream-UI-va(config-virt-service)# vnic interface Ten. Gig. E 0/3$ RP/0/RP 0/CPU 0: Starscream-UI-va(config-virt-service)#commit RP/0/RP 0/CPU 0: Starscream-UI-va(config-virt-service)#activate RP/0/RP 0/CPU 0: Starscream-UI-va(config-virt-service)#commit Step 7: Check the status of the CGv 6 VM RP/0/RP 0/CPU 0: Starscream-UI-va#sh virtual-service list Virtual Service List: Name Status Package Name Node Name _______________________________________ cgn 123 Activated vsmcgv 6_ivybridge. ova 0/3/CPU 0 RP/0/RP 0/CPU 0: Starscream-UI-va#

VSM-NAT 44 Basic Configuration Steps ü Install asr 9 k-services-p. pie üInstall asr 9 k-services-infra. pie Int Service. Infra 1 IPv 4: 200. 1. 1. 1/24 Ingress LC VSM Egress LC VRF “Nat-inside” VRF “Nat-outside” CGN “cgn 123/nat 44” Public IPv 4 Pool (Natinside to Nat-outside): 100. 2. 0. 0/24 Int Gige 0/6/1/13 VRF: Nat-inside IPv 4: 31. 1/24 int Service. App 1 VRF: Nat-inside IPv 4: 14. 1. 1. 1/24 Service-Type: cgn 123/nat 44 router static vrf Nat-inside address-family ipv 4 unicast 0. 0/0 Service. App 1 Int Gige 0/6/1/14 [VRF: Nat-outside] IPv 4: 41. 1/24 int Service. App 2 [VRF: Nat-outside] IPv 4: 15. 1. 1. 1/24 Service-Type: cgn 123/nat 44 router static [vrf Nat-outside] address-family ipv 4 unicast 100. 2. 0. 0/24 Service. App 2

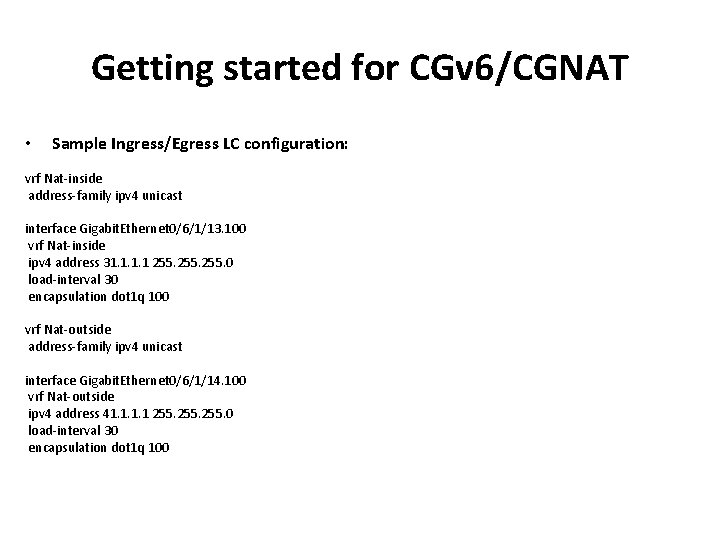
Getting started for CGv 6/CGNAT • Sample Ingress/Egress LC configuration: vrf Nat-inside address-family ipv 4 unicast interface Gigabit. Ethernet 0/6/1/13. 100 vrf Nat-inside ipv 4 address 31. 1 255. 0 load-interval 30 encapsulation dot 1 q 100 vrf Nat-outside address-family ipv 4 unicast interface Gigabit. Ethernet 0/6/1/14. 100 vrf Nat-outside ipv 4 address 41. 1 255. 0 load-interval 30 encapsulation dot 1 q 100

Service CGN and service-type **** CGN instance ******* service cgn 123 service-location preferred-active 0/3/CPU 0 *****CGNAT service-type ****** service-type nat 44 nat 123 portlimit 65535 inside-vrf Nat-inside map outside-vrf Nat-outside address-pool 100. 2. 0. 0/24 ! protocol udp session initial timeout 65535 session active timeout 65535 ! protocol tcp session initial timeout 65535 session active timeout 65535 !

Service interfaces interface Service. Infra 1 ipv 4 address 75. 1. 1. 1 255. 0 service-location 0/3/CPU 0 Service. App interfaces per vrf along with service cgn and service-type. interface Service. App 1 vrf Nat-inside ipv 4 address 14. 1. 1. 1 255. 0 service cgn 123 service-type nat 44 interface Service. App 2 vrf Nat-outside ipv 4 address 15. 1. 1. 1 255. 0 service cgn 123 service-type nat 44

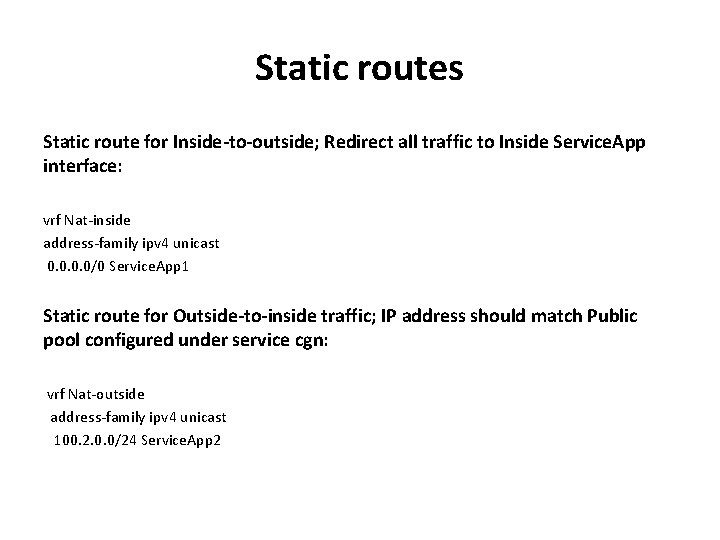
Static routes Static route for Inside-to-outside; Redirect all traffic to Inside Service. App interface: vrf Nat-inside address-family ipv 4 unicast 0. 0/0 Service. App 1 Static route for Outside-to-inside traffic; IP address should match Public pool configured under service cgn: vrf Nat-outside address-family ipv 4 unicast 100. 2. 0. 0/24 Service. App 2

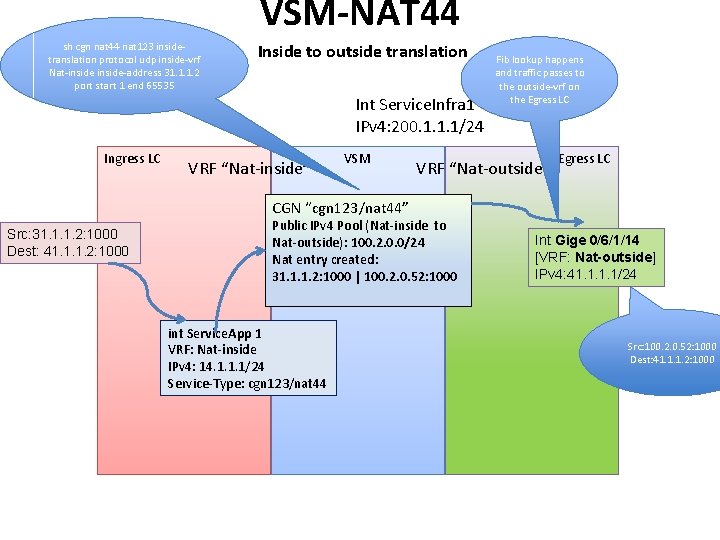
VSM-NAT 44 sh cgn nat 44 nat 123 insidetranslation protocol udp inside-vrf Nat-inside-address 31. 1. 1. 2 port start 1 end 65535 Inside to outside translation Int Service. Infra 1 IPv 4: 200. 1. 1. 1/24 Ingress LC VRF “Nat-inside” VSM Fib lookup happens and traffic passes to the outside-vrf on the Egress LC VRF “Nat-outside” Egress LC CGN “cgn 123/nat 44” Src: 31. 1. 1. 2: 1000 Dest: 41. 1. 1. 2: 1000 Public IPv 4 Pool (Nat-inside to Nat-outside): 100. 2. 0. 0/24 Nat entry created: 31. 1. 1. 2: 1000 | 100. 2. 0. 52: 1000 int Service. App 1 VRF: Nat-inside IPv 4: 14. 1. 1. 1/24 Service-Type: cgn 123/nat 44 Int Gige 0/6/1/14 [VRF: Nat-outside] IPv 4: 41. 1/24 Src: 100. 2. 0. 52: 1000 Dest: 41. 1. 1. 2: 1000

Inside-to-Outside Packet flow 1) 2) 3) 4) Inside vrf is connected to a traffic Generator Packet enters from private Inside VRF to the ingress Linecard. Static route from inside vrf redirects all traffic to Service. App 1 on VSM. CGNAT application does the NAT processing for the packet and assigns a public IP address from the public pool creating a NAT entry. 5) After the Nat translation forwarding lookup will be done for destination address in the outside vrf and packet is sent to the Egress LC interface. 6) Egress line card send the packet to the Public side connected to another traffic generator.

VSM-NAT 44 sh cgn nat 44 nat 123 outsidetranslation protocol udp outside-vrf Nat-outside-address 100. 2. 0. 52 port start 1 end 65535 Outside to Inside translation Ingress LC VSM Egress LC VRF “Nat-inside” VRF “Nat-outside” CGN “cgn 123/nat 44” Public IPv 4 Pool (Natinside to Nat-outside): 100. 2. 0. 0/24 Int Gige 0/6/1/13 VRF: Nat-inside IPv 4: 31. 1/24 Fib lookup happens and traffic passes to the inside-vrf on the Egress LC Int Gige 0/6/1/14 [VRF: Nat-outside] IPv 4: 41. 1/24 int Service. App 2 [VRF: Nat-outside] IPv 4: 15. 1. 1. 1/24 Service-Type: cgn 123/nat 44 Src: 41. 1. 1. 2: 1000 Dest: 100. 2. 0. 52: 1000

Outside to Inside Packet flow (reverse -nat) 1) Packet enters from Outside vrf - Public side 2) Based on Static route defined packet should be forwarded to the VSM card via the Service. App 2 in the outside-vrf. 3) CGNAT application does the Nat processing and looks for corresponding NAT entry if present. If not it drops the packet. If the entry is present then it replaces destination ip and port with the corresponding Private IP address. 4) After the Reverse Nat translation forwarding lookup will be done for the destination IP address in the inside vrf and packet is sent to the Egress LC interface 5) Egress line card send the packet out to the Private side/ inside vrf.

Caveats in 5. 1. 1 Ø VSM on Cluster is not supported Ø Commit replace and rollback: i) Commit replace does not have this restriction but its safer to deactivate Virtual- services in all cases. ii) Rollback: Virtual-services need to be deactivated before doing config rollback. Ø IP address configuration is not supported on the Tengig interfaces of the VSM LC. Ø 4 Front Panel SFP+ ports are not enabled and cannot be used.

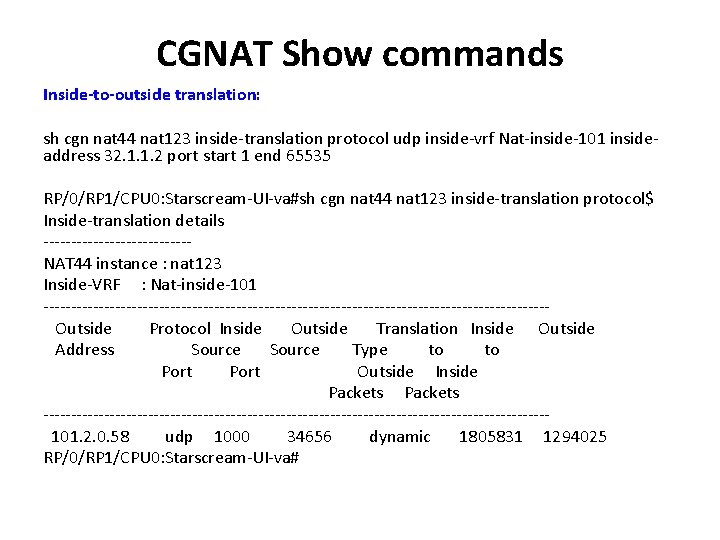
CGNAT Show commands Inside-to-outside translation: sh cgn nat 44 nat 123 inside-translation protocol udp inside-vrf Nat-inside-101 insideaddress 32. 1. 1. 2 port start 1 end 65535 RP/0/RP 1/CPU 0: Starscream-UI-va#sh cgn nat 44 nat 123 inside-translation protocol$ Inside-translation details -------------NAT 44 instance : nat 123 Inside-VRF : Nat-inside-101 ---------------------------------------------- Outside Protocol Inside Outside Translation Inside Outside Address Source Type to Port Outside Inside Packets ---------------------------------------------- 101. 2. 0. 58 udp 1000 34656 dynamic 1805831 1294025 RP/0/RP 1/CPU 0: Starscream-UI-va#

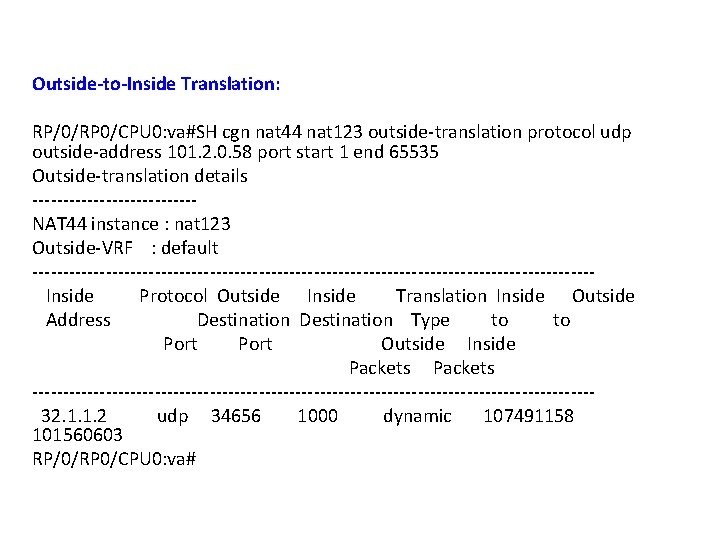
Outside-to-Inside Translation: RP/0/RP 0/CPU 0: va#SH cgn nat 44 nat 123 outside-translation protocol udp outside-address 101. 2. 0. 58 port start 1 end 65535 Outside-translation details -------------NAT 44 instance : nat 123 Outside-VRF : default ---------------------------------------------- Inside Protocol Outside Inside Translation Inside Outside Address Destination Type to Port Outside Inside Packets ---------------------------------------------- 32. 1. 1. 2 udp 34656 1000 dynamic 107491158 101560603 RP/0/RP 0/CPU 0: va#

Cef commands RP/0/RP 0/CPU 0: va#sh cef vrf Nat-inside 31. 1. 1. 2 location 0/3/CPU 0 31. 1. 1. 0/24, version 19, attached, connected, internal 0 xc 0000 c 1 0 x 0 (ptr 0 x 7 c 12 a 064) [1], 0 x 0 (0 x 7 c 071008), 0 x 0 (0 x 0) Updated Jan 22 15: 17: 43. 521 remote adjacency to Gigabit. Ethernet 0/6/1/13. 100 Prefix Len 24, traffic index 0, precedence n/a, priority 0 via Gigabit. Ethernet 0/6/1/13. 100, 2 dependencies, weight 0, class 0 [flags 0 x 8] path-idx 0 NHID 0 x 0 [0 x 7 e 1624 d 8 0 x 0] remote adjacency RP/0/RP 0/CPU 0: va#sh cef vrf Nat-outside 101. 2. 0. 58 location 0/3/CPU 0 0. 0/0, version 0, proxy default, default route handler, drop adjacency, internal 0 x 4002021 0 x 0 (ptr 0 x 7 c 1241 e 4) [1], 0 x 0 (0 x 7 c 066290), 0 x 0 (0 x 0) Updated Jan 22 15: 17: 24. 341 Prefix Len 0, traffic index 0, precedence n/a, priority 0 via point 2 point, 144 dependencies, weight 0, class 0 [flags 0 x 0] path-idx 0 NHID 0 x 0 [0 x 7 bacf 23 c 0 x 0] next hop point 2 point drop adjacency RP/0/RP 0/CPU 0: va#

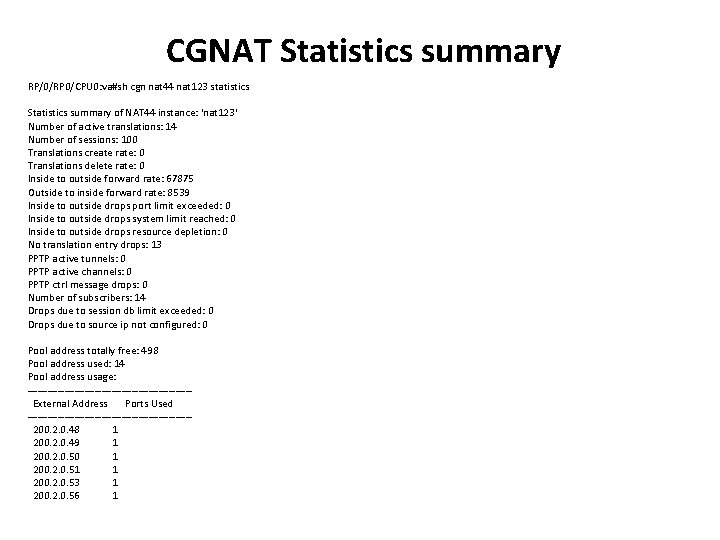
CGNAT Statistics summary RP/0/RP 0/CPU 0: va#sh cgn nat 44 nat 123 statistics Statistics summary of NAT 44 instance: 'nat 123' Number of active translations: 14 Number of sessions: 100 Translations create rate: 0 Translations delete rate: 0 Inside to outside forward rate: 67875 Outside to inside forward rate: 8539 Inside to outside drops port limit exceeded: 0 Inside to outside drops system limit reached: 0 Inside to outside drops resource depletion: 0 No translation entry drops: 13 PPTP active tunnels: 0 PPTP active channels: 0 PPTP ctrl message drops: 0 Number of subscribers: 14 Drops due to session db limit exceeded: 0 Drops due to source ip not configured: 0 Pool address totally free: 498 Pool address used: 14 Pool address usage: ------------------------ External Address Ports Used ------------------------ 200. 2. 0. 48 1 200. 2. 0. 49 1 200. 2. 0. 50 1 200. 2. 0. 51 1 200. 2. 0. 53 1 200. 2. 0. 56 1